- "a"
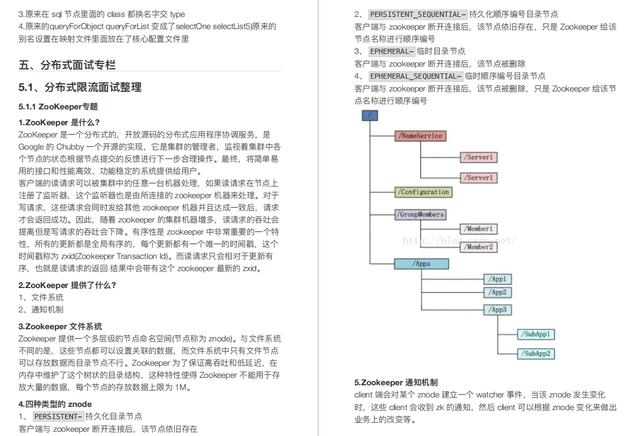
- "b"
127.0.0.1:6379> lset list1 0 v
OK
127.0.0.1:6379> lrange list1 0 -1 - "v"
- "b"
- lrm : Delete an element and return the number of deleted elements ```java 127.0.0.1:6379> lrange list1 0 -1 1) "b" 2) "b" 3) "a" 4) "b" 127.0.0.1:6379> lrange list1 0 -1 1) "a" 2) "b"
- lindex: returns the element at the specified position in the list
- Len: returns the number of elements in the list
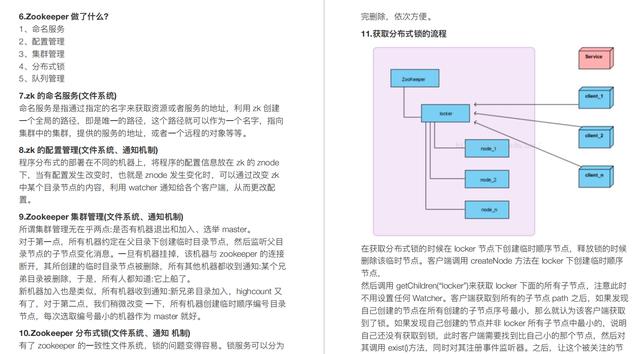
Implement data structure
- Stack
- LPUSH+LPOP
- Queue
- LPUSH + RPOP
- Blocking MQ (blocking queue)
- LPUSH+BRPOP
Application scenario
- Implement simple message queuing
- Use LRANGE command to realize Redis based paging function
3)set
The collection object set is an unordered collection of string type (integers will also be converted to string type for storage). Note the difference between a collection and a list: the elements in the collection are unordered, so they cannot be manipulated by index; the elements in the collection cannot be duplicated.
code
- The code of the collection object can be intset or hashtable
- The set object encoded by intset uses the integer set as the underlying implementation, and all elements contained in the set object are saved in the integer set.
- The hashtable encoded collection object uses the dictionary as the underlying implementation. Each key of the dictionary is a string object. Each string object here is an element in a collection, and all the values of the dictionary are SET to null. When HT coding is used, the SET in Redis is equivalent to the HashSet in Java, and the internal key value pairs are unordered and unique. The internal implementation is equivalent to a special dictionary. All values in the dictionary are null.
- Code conversion
- intset encoding is used when the set meets the following two conditions:
- All elements in the collection object are integers
- The number of all elements of the collection object does not exceed 512
- intset encoding is used when the set meets the following two conditions:
Common commands
- sadd: add elements to the collection (set does not allow duplicate elements)
- smembers: view elements in a collection
127.0.0.1:6379> sadd set1 aaa (integer) 1 127.0.0.1:6379> sadd set1 bbb (integer) 1 127.0.0.1:6379> sadd set1 ccc (integer) 1 127.0.0.1:6379> smembers set1 1) "aaa" 2) "ccc" 3) "bbb"
- srem: delete collection elements
- spop: randomly return deleted key s
- sdiff: returns the different elements of two sets (which set is based on which set before)
127.0.0.1:6379> smembers set1 1) "ccc" 2) "bbb" 127.0.0.1:6379> smembers set2 1) "fff" 2) "rrr" 3) "bbb" 127.0.0.1:6379> sdiff set1 set2 1) "ccc" 127.0.0.1:6379> sdiff set2 set1 1) "fff" 2) "rrr"
- sinter: returns the intersection of two sets
- sinterstore: returns the intersection result and stores it in the target set
127.0.0.1:6379> sinterstore set3 set1 set2 (integer) 1 127.0.0.1:6379> smembers set3 1) "bbb"
- sunion: take the union of two sets
- sunionstore: take the union of two sets and store it in the target set
- smove: move elements from one collection to another
- Scar: returns the number of elements in the collection
- sismember: judge whether an element exists in a set. 0 means no and 1 means yes
- srandmember: returns an element at random
127.0.0.1:6379> srandmember set1 1 1) "bbb" 127.0.0.1:6379> srandmember set1 2 1) "ccc" 2) "bbb"
Application scenario
- For the set data type, because the bottom layer is implemented by the dictionary, it is very fast to find elements. In addition, the set data type is not allowed to be repeated. Using these two characteristics, we can carry out global de duplication, such as judging whether the user name is registered in the user registration module; Wechat praise, wechat lucky draw applet
- In addition, using intersection, union, difference and other operations, you can calculate common preferences, all preferences, your own unique preferences, people you may know and other functions.
4)zset
Compared with collection objects, ordered collection objects are ordered. Unlike the list that uses the index table below as the sorting basis, the ordered set sets a score for each element as the sorting basis.
code
- The encoding of ordered sets can make ziplost or skiplist
- The ziplost encoded ordered collection object uses the compressed list as the underlying implementation. Each collection element is saved by two compressed list nodes next to each other. The first node saves the members of the element and the second node saves the score of the element. And the set elements in the compressed list are arranged in the order of score from small to large. The small ones are placed near the header and the large ones are placed near the footer.
- The sequential collection object encoded by skiplist uses zset structure as the underlying implementation. A zset structure contains both a dictionary and a jump table
typedef struct zset{
//Jump table
zskiplist *zsl;
//Dictionaries
dict *dice;
}
zset
The key of the dictionary saves the value of the element, the value of the dictionary saves the score of the element, and the value of the jump table node object Attribute to save the members of the element and jump the table nodes score Attribute holds the score of the element. These two data structures will share the members and scores of the same element through pointers, so there will be no duplicate members and scores, resulting in a waste of memory.
- Code conversion
- When the ordered combined object satisfies the following two conditions at the same time, the object is encoded with ziplist; otherwise, it is encoded with skiplist
- The number of saved elements is less than 128
- All saved elements are less than 64 bytes in length
- When the ordered combined object satisfies the following two conditions at the same time, the object is encoded with ziplist; otherwise, it is encoded with skiplist
Common commands
- zrem: delete the element member named key in the collection
- zincrby: automatically increment with the specified value
- zcard: view the number of element sets
- zcount: returns the number of score s in a given interval
127.0.0.1:6379> zrange zset 0 -1 1) "one" 2) "three" 3) "two" 4) "four" 5) "five" 6) "six" 127.0.0.1:6379> zcard zset (integer) 6 127.0.0.1:6379> zcount zset 1 4 (integer) 4
- zrangebyscore: find the data within the specified range and return it
127.0.0.1:6379> zrangebyscore zset 0 4 withscores 1) "one" 2) "1" 3) "three" 4) "2" 5) "two" 6) "2" 7) "four" 8) "4"
- zremrangebyrank zset from to: deletes an index
127.0.0.1:6379> zrange zset 0 -1 1) "one" 2) "three" 3) "two" 4) "four" 5) "five" 6) "six" 127.0.0.1:6379> zremrangebyrank zset 1 3 (integer) 3 127.0.0.1:6379> zrange zset 0 -1 1) "one" 2) "five" 3) "six"
- zremrangebyscore zset from to: deletes the specified sequence number
127.0.0.1:6379> zrange zset 0 -1 withscores 1) "one" 2) "1" 3) "five" 4) "5" 5) "six" 6) "6" 127.0.0.1:6379> zremrangebyscore zset 3 6 (integer) 2 127.0.0.1:6379> zrange zset 0 -1 withscores 1) "one" 2) "1"
- zrank: return sort index (find index after ascending)
- zrevrank: return sort index (find index after descending)
Application scenario
- For zset data type and ordered collection, you can do range search, leaderboard application, TOP N operation, etc.
5)hash
The key of a hash object is a string type, and the value is a collection of key value pairs
code
- The encoding of hash object can be ziplost or hashtable
- When ziplost, that is, compressed list, is used as the underlying implementation, the new key value is saved to the end of the compressed list.
- The underlying hash table object encoded by hashtable uses dictionary data structure, and each key value pair in the hash object uses a dictionary key value pair. The dictionary in Redis is equivalent to the HashMap in Java, and its internal implementation is almost similar. It solves hash conflicts through the chain address method of "array + linked list". This structure absorbs the advantages of two different data structures.
- Code conversion
- When the following two conditions are met at the same time, zip list encoding is used; otherwise, hashtable encoding is used
- The number of elements saved in the list is less than 512
- The length of each element is less than 64 bytes
- When the following two conditions are met at the same time, zip list encoding is used; otherwise, hashtable encoding is used
- hash is a mapping table between field and value of String type
- Hash is especially suitable for storing objects
- When the number of stored members is small, the data is stored as zipmap. When the number of members increases, it will be automatically converted to a real HashMap. At this time, encoding is ht
- Detailed explanation of Hash command
- hset/hget
- hset hashname hashkey hashvalue
- hget hashname hashkey
- hset/hget
127.0.0.1:6379> hset user id 1 (integer) 1 127.0.0.1:6379> hset user name z3 (integer) 1 127.0.0.1:6379> hset user add shanxi (integer) 1 127.0.0.1:6379> hget user id "1" 127.0.0.1:6379> hget user name "z3" 127.0.0.1:6379> hget user add "shanxi"
- hmset/hmget
- hmset hashname hashkey1hashvalue1 hashkey2 hashvalue2 hashkey3 hashvalue3
- hget hashname hashkey1 hashkey2 hashkey3
127.0.0.1:6379> hmset user id 1 name z3 add shanxi OK 127.0.0.1:6379> hmget user id name add 1) "1" 2) "z3" 3) "shanxi"
- hsetnx/hgetnx
- hincrby/hdecrby
127.0.0.1:6379> hincrby user2 id 3 (integer) 6 127.0.0.1:6379> hget user2 id "6"
- hexist determines whether a key exists. If it does not exist, it returns 0
127.0.0.1:6379> hget user2 id "6"
- hlen returns the number of all key values in the hash set
127.0.0.1:6379> hmset user3 id 3 name w5 OK 127.0.0.1:6379> hlen user3 (integer) 2
- hdel: deletes the key of the specified hash
- hkeys returns all fields in the hash
- hvals returns all value s in the hash
- hgetall: returns all key s and value s in the hash set
127.0.0.1:6379> hgetall user3 1) "id" 2) "3" 3) "name" 4) "w3" 5) "add" 6) "beijing"
advantage
- Similar data are classified, integrated and stored to facilitate data management. For example, all goods of a single user are placed in a hash table.
- It consumes less memory and cpu than string operation
shortcoming
- The storage consumption of hash structure is higher than that of single string
- The expiration function cannot be used on a field, but only on a key
- redis cluster architecture is not suitable for large-scale use
Application scenario
- For hash data types, value stores key value pairs. For example, single sign on can be used to store user information.
- Store commodity information and realize shopping cart
3. Memory recycling and memory sharing
typedef struct redisObject{
//type
unsigned type:4;
//code
unsigned encoding:4;
//Pointer to the underlying data structure
void *ptr;
//Reference count
int refcount;
//Record the time of the last access by the program
unsigned lru:22;
}robj
last
It's not my style to give only interview questions but no answers. There are only a few interview questions here, and the answers will greatly increase the length of the article and reduce the readability of the article, so they are only displayed in screenshots, You can click here for free!
Java interview dictionary version 2021


Analysis of the most common Java interview questions (2021 latest version)

2021 selected enterprise Java interview questions
ps://codechina.csdn.net/m0_60958482/java-p7)**
Java interview dictionary version 2021
[external chain picture transferring... (img-4m5DreGp-1630221864532)]
[external chain picture transferring... (img-sWVvN0FY-1630221864534)]
Analysis of the most common Java interview questions (2021 latest version)
[external chain picture transferring... (img-wwg5l3ka-1630221864535)]
[external chain picture transferring... (img-oh6VIfO8-1630221864537)]
2021 selected enterprise Java interview questions
[external chain picture transferring... (img-5zoI9Jwd-1630221864538)]