1, Why addressing
- We know that data is stored in memory. The CPU needs to use the data stored in memory. To use a data, we need to find the data in memory. What to find is to use the memory number, that is, the address, to find the location of the data in memory, take it out for use, or put it back to the specified location
- The above is an addressing process: there are five addressing modes, and the computer only knows these five modes to address
2, Five addressing modes
1. Addressing mode 1 [immediate]
-
Directly through [immediate], that is, directly addressing with memory address
-
Read the value of memory
MOV EAX,DWORD PTR DS:[0x13FFC4]
MOV is to put the value DWORD PTR DS:[0x13FFC4] into the 32-bit EAX register; DWORD means to read 32-bit numbers, which can be omitted but not recommended; PTR is a fixed writing method; DS is a segment register. The middle segment register of 32-bit assembly is related to the attributes of memory. If the subsequent address is directly represented by a number, use DS. If ESP or EBP is written later, write SS. If EDI is written later, use ES. Therefore, the middle register of 32-bit assembly is an identification of the following memory attributes. Therefore, the function of the whole instruction is to read out the value stored in 0x13FFC4 address in memory and put it into EAX by means of immediate addressing
-
Write data to memory
MOV DWORD PTR DS:[0x13FFC4],ebx
Read out the value in 0x13FFC4 in memory and write it into ebx register
-
Get memory number
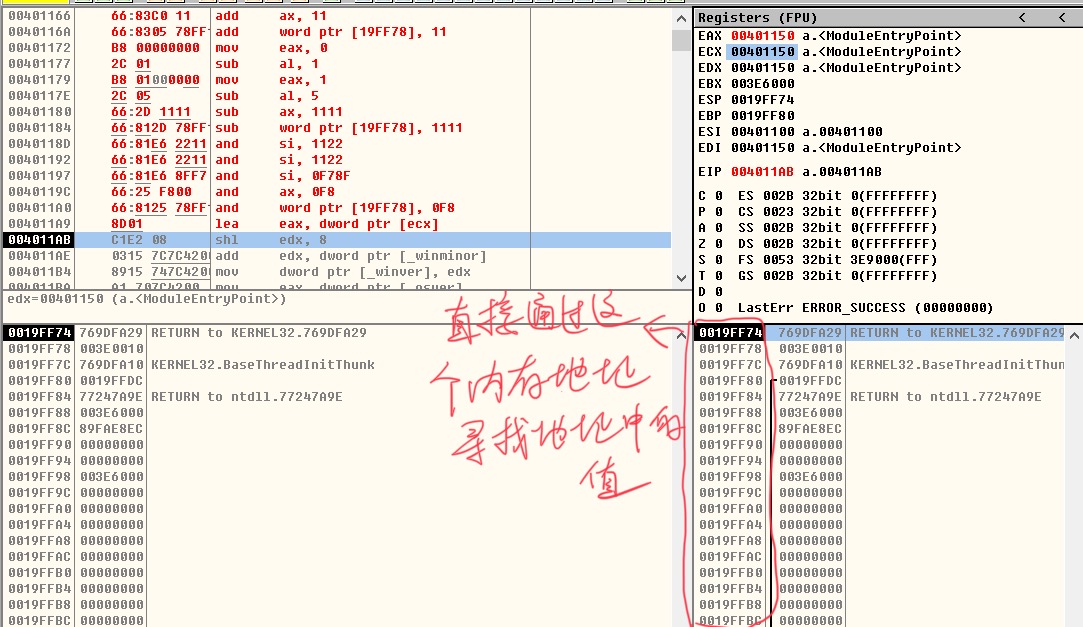
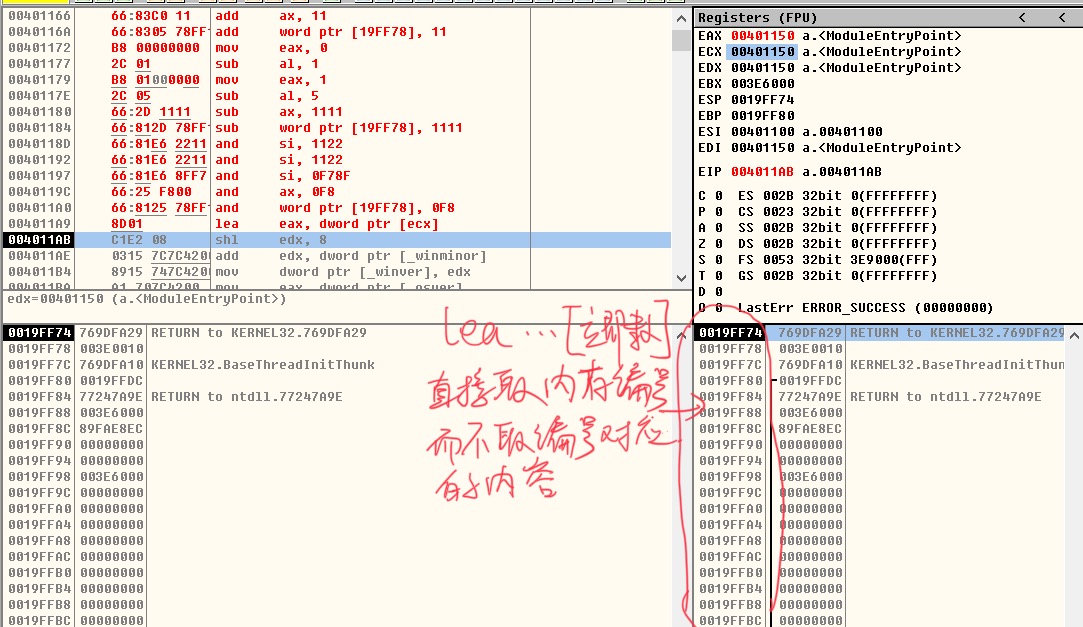
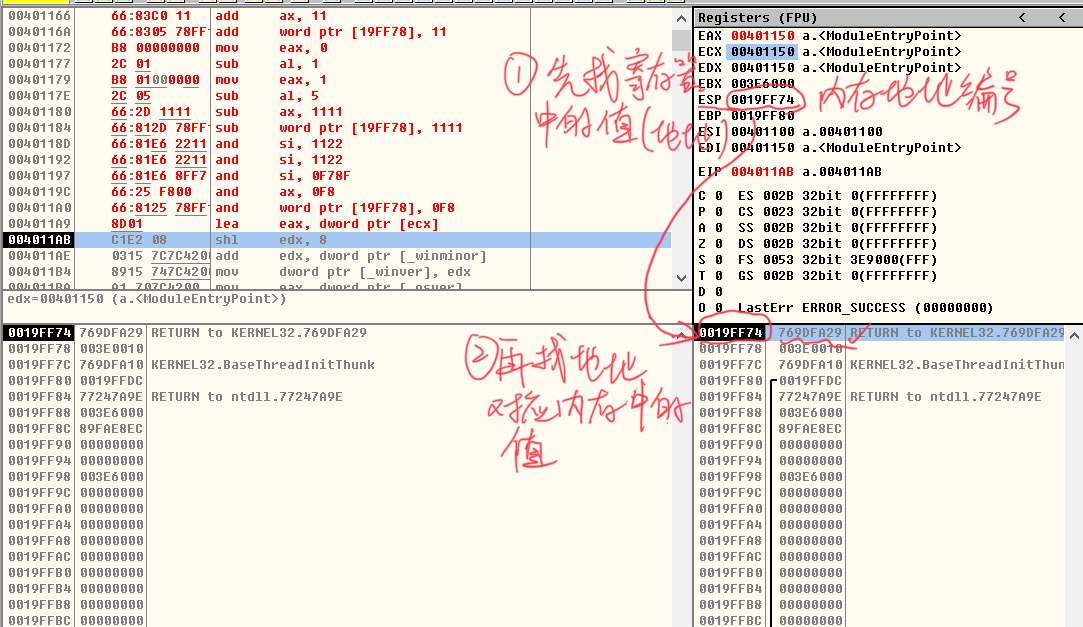
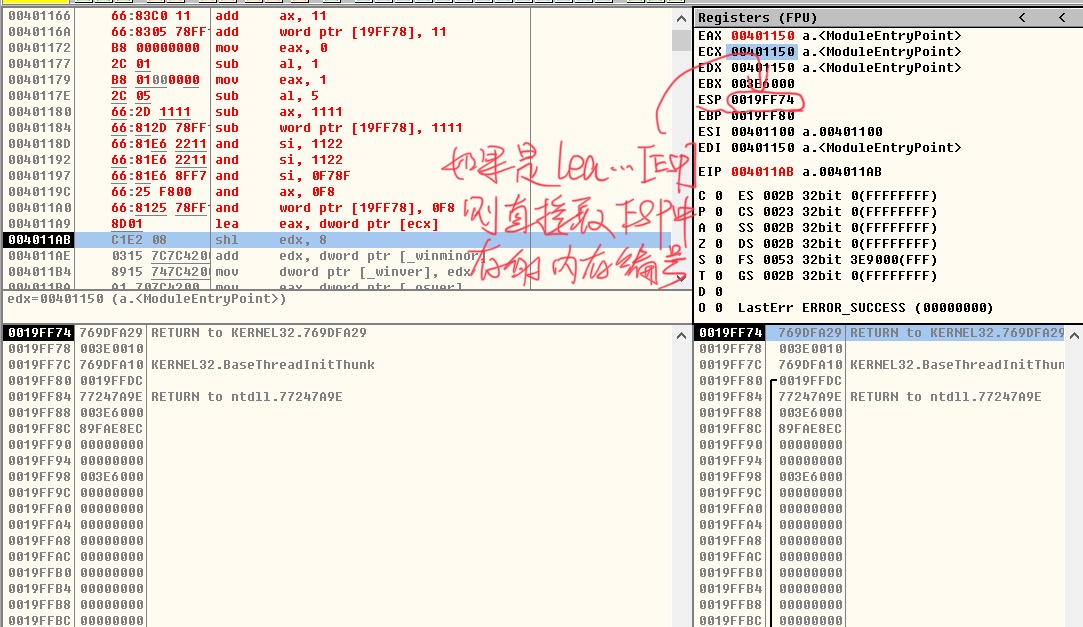
LEA EAX,DWORD PTR DS:[0x13FFC4]
The first instruction means to put the address number 0x13FFC4 in memory into EAX register
2. Addressing mode 2 [reg]
-
Addressed by [reg], reg can be any of the eight general-purpose registers. First, read the memory address number stored in the register, and then find the value in the memory through the memory address number
-
Read the value of memory
MOV ECX,0x13FFD0 #Put the address number 0x13FFD0 into ECX deposit. This address is the base address of ECX #There may be many operations on the value in ecx in the middle. As long as we find the base address of ecx, we can track ecx, and finally get what ecx is in the following statement MOV EAX,DWORD PTR DS:[ECX] #Take out the value in the address 0x13FFD0 stored in ECX register and put it into EAX
-
Write data to memory
MOV EDX,0x13FFD8 #Store 0x13FFD8 in EDX MOV DWORD PTR DS:[EDX],0x87654321
-
Get memory number
LEA EAX,DWORD PTR DS:[EDX]
3. Addressing mode 3 [reg + immediate]
-
Via [reg + immediate]
-
Read the value of memory
MOV ECX,0x13FFD0 MOV EAX,DWORD PTR DS:[ECX+4] #Take out the value in the address number 0x13FFD0+0x000004 and save it in EAX
-
Write data to memory
MOV EDX,0x13FFD0 MOV DWORD PTR DS:[EDX+0xC],0x87654321
-
Get memory number
LEA EAX,DWORD PTR DS:[EDX+4]
4. Addressing mode 4 [reg+reg*{1,2,4,8}]
-
Address through [reg+reg*1 or 2 or 4 or 8]. It can only be 1,2,4,8. Learn hard coding later
-
Read the value of memory
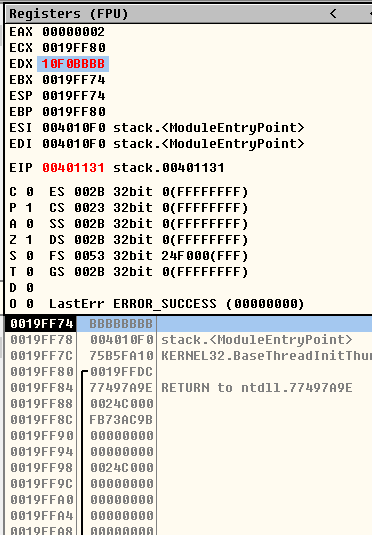
MOV EAX,0x13FFC4 MOV ECX,2 MOV EDX,DWORD PTR DS:[EAX+ECX*4] #Take out the value in the address number after 0x13FFC4+0x8 and save it to EDX
Special case: if the memory address number obtained by [reg+reg*{1,2,4,8}] is not the representative address of the stack, for example, the calculated result is 0x0019ff7A, we know that the difference between each address number in the stack is 4, because a first address 0x0019ff78 represents the four memory blocks from 0x0019ff78 to 0x0019ff7B, a total of 4 bytes, Therefore, the following value can be saved as 0xf0019ff0. In fact, the value stored in 0x0019ff7A is 0x40 (one byte), while the above command uses DWORD, which means that 4 bytes are read and stored in edx as a whole. Therefore, 4 bytes are taken from behind 0x0019ff7A, that is, the values in 0x19ff7A, 0x19ff7B, 0x19ff7C and 0x19ff7D. The final result is 0xFA100040 (remember to write from the high bit when writing)
-
Write data to memory
MOV EAX,0x13FFC4 MOV ECX,2 MOV DWORD PTR DS:[EAX+ECX*4],87654321 #Write the value 87654321 into the memory 0x13FFC4+0x8
-
Get memory number
LEA EAX,DWORD PTR DS:[EAX,ECX*4] #Only the address numbers EAX and ECX * 4 are stored in EAX
5. Addressing mode 5 [reg+reg*{1,2,4,8} + immediate]
-
By [reg + reg*1 or 2 or 4 or 8 + immediate]
-
Read the value of memory
MOV EAX,0x13FFC4 MOV ECX,2 MOV EDX,DWORD PTR DS:[EAX+ECX*4+4]
-
Write data to memory
MOV EAX,0x13FFC4 MOV ECX,2 MOV DWORD PTR DS:[EAX+ECX*4+4],87654321
-
Get memory number
LEA EAX,DWORD PTR DS:[EAX+ECX*4+2]
3, Homework
1. Memory reading and writing exercise
-
Each addressing formula realizes the reading, writing and fetching of memory address respectively
-
Addressing Formula 1: [immediate]
mov eax,dword ptr ss:[0x0019ff74] #Read memory mov dword ptr ss:[0x0019ff74],0xAAAAAAAA #Write memory lea eax,dword ptr ss:[0x0019ff74] #Fetch memory address
-
Addressing formula 2: [reg]
mov eax,dword ptr ss:[esp] mov dword ptr ss:[esp],0xBBBBBBBB lea eax,dword ptr ss:[esp]
Note that the two parameters of mov instruction cannot be registers at the same time
-
Addressing formula 3: [reg + immediate]
mov eax,dword ptr ss:[esp+4] mov dword ptr ss:[ebp-8],edx #Store the value in edx into [ebp-8] memory lea eax,dword ptr ss:[esp+8]
-
Addressing formula 4: [reg + reg * {1,2,4,8}]
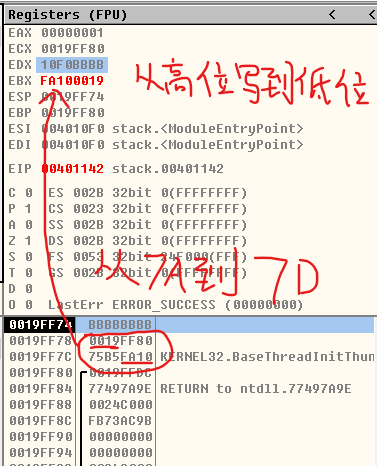
mov eax,2 lea ecx,dword ptr ss:[ebp] #Now the value stored in ecx is the bottom address number 0x19ff80 lea ebx,dword ptr ss:[esp] #Now the value stored in ebx is the stack top address number 0x19ff74 ---------------------------------- #Mov EDX, DWORD PTR ds: [ECX eax * 1] cannot be subtraction!!! mov edx,dword ptr ds:[ebx+eax*1] #The number that combines the 0x19ff76 address number and the last three address numbers to the top is stored in the In edx mov edx,dword ptr ds:[ebx+eax*2] #Copy the value in 0x19ff78 address and store it in edx ---------------------------------- mov dword ptr ds:[esp+eax*2],ecx lea eax,dword ptr ds:[esp+eax*4]
-
Addressing formula 5: [reg + reg * {1,2,4,8} + immediate]
mov eax,1 mov ebx,dword ptr ss:[esp+eax*4+0x2] #fa100019 mov dword ptr ss:[esp+eax*4+0x2],edx lea eax,dword ptr ss:[esp+eax*4+0x2]
-