Linux system is a multi-user and multi task time-sharing operating system. Any user who wants to use system resources must first apply to the system administrator for an account, and then enter the system as this account.
More linux articles: Courageous steak - linux
Courageous steak official website: https://lgch.xyz/
1 Introduction
2 classification
2.1 user classification
2.1. 1 super user
| user name | UID |
|---|---|
| root | 0 (no repetition) |
2.2. 2 ordinary users
| system | UID |
|---|---|
| CentOS6- | 1~499 |
| CentOS7+ | 1~999 |
2.2. 3 login user
| system | UID |
|---|---|
| CentOS6- | 500+ |
| CentOS7+ | 1000+ |
Note: the UID of 60000 + usually requires user-defined identification.
3 name explanation
Name interpretation: the system identifies the user's name and UID.
4 document introduction
4.1 user account file passwd
Store user information, each separated by:
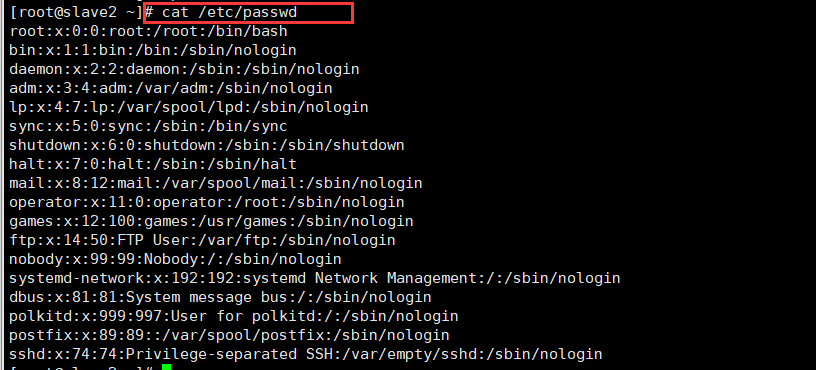
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
User name: root
x: Password, password
First 0: user
Second 0: Group
Second root: password
:: description
/root: user home directory
/bin/bash: user default Shell
- The passwd command is used to set user authentication information, including user password, password expiration time, etc.
- Only administrators can specify user names.
- General users can only change their own passwords.
Parameter introduction:
-d: Delete the password, which can only be used by the system administrator; -f: Enforcement; -k: Settings can only be updated after the password expires; -l: Lock the password and don't let you change it. -s: List the relevant information of the password, which can only be used by the system manager; -u: Unlock the locked account.
4.1. 1. User password operation
4.1. 1.1 change or create the password of test user
passwd test
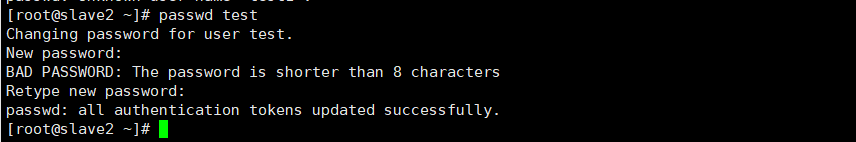
An error is reported when the user does not exist
4.1. 1.2 the current user changes his password
passwd

4.1. 1.3 prohibit test users from changing passwords
passwd -l test
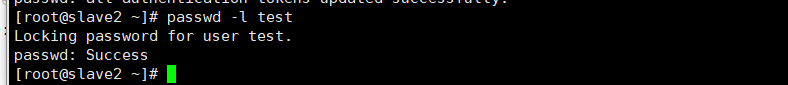
4.1. 1.4 clear test user password
passwd -d test
Note: after the password is cleared, you can log in without a password.

4.1. 1.5 query test user password
passwd -S test
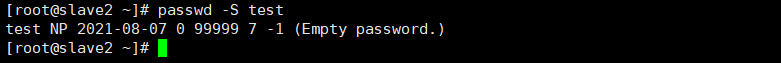
4.2 user shadow file
cat /etc/shadow
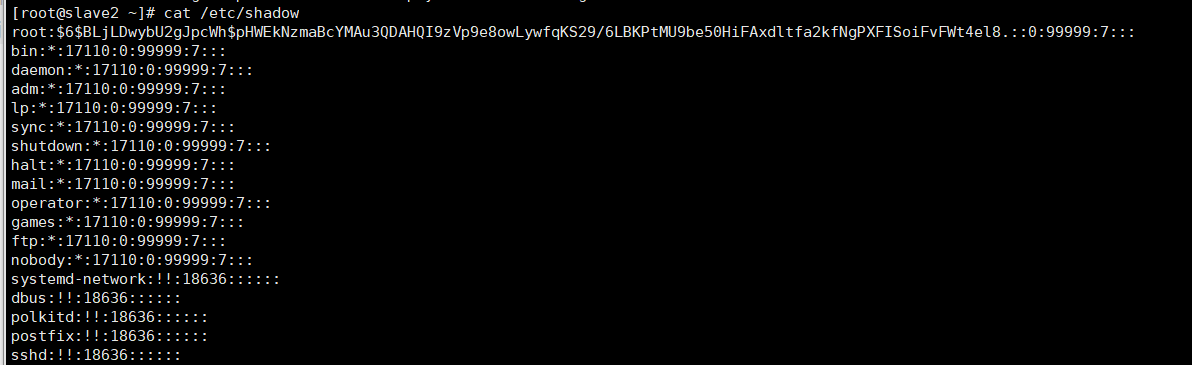
4.3 user group account files: groun d and gshadow
jack:$!$:???:13801:0:99999:7:*:*:
Group name: jack
$!$: Encrypted password
13801: number of days between the creation date and today
0: minimum number of digits of password
99999: user password
7: Reminder at 7 days
*: disable days
*: expiration days
View group files
cat /etc/group
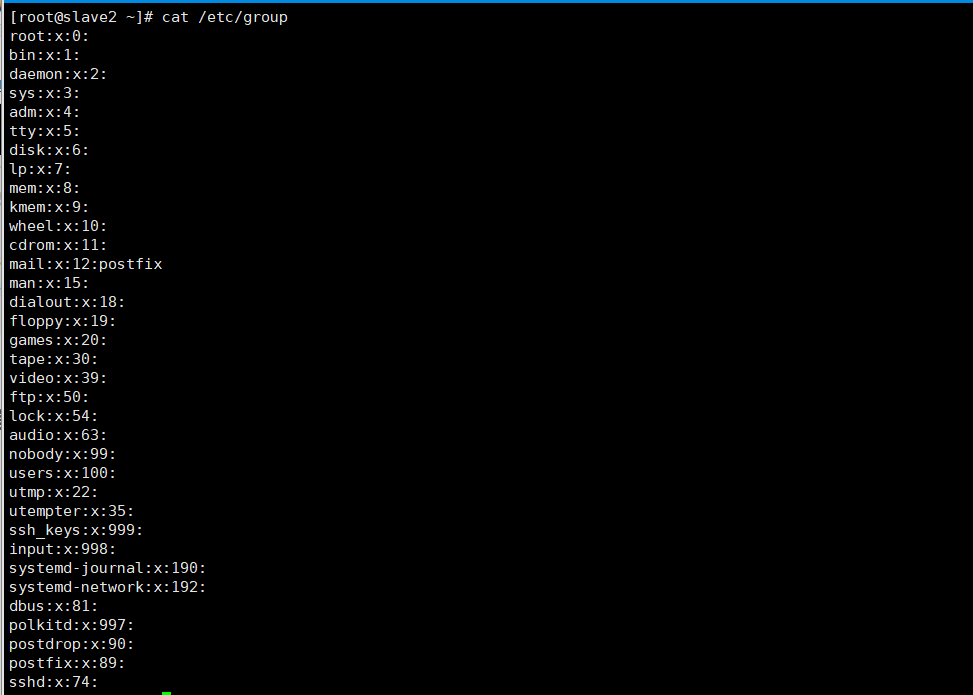
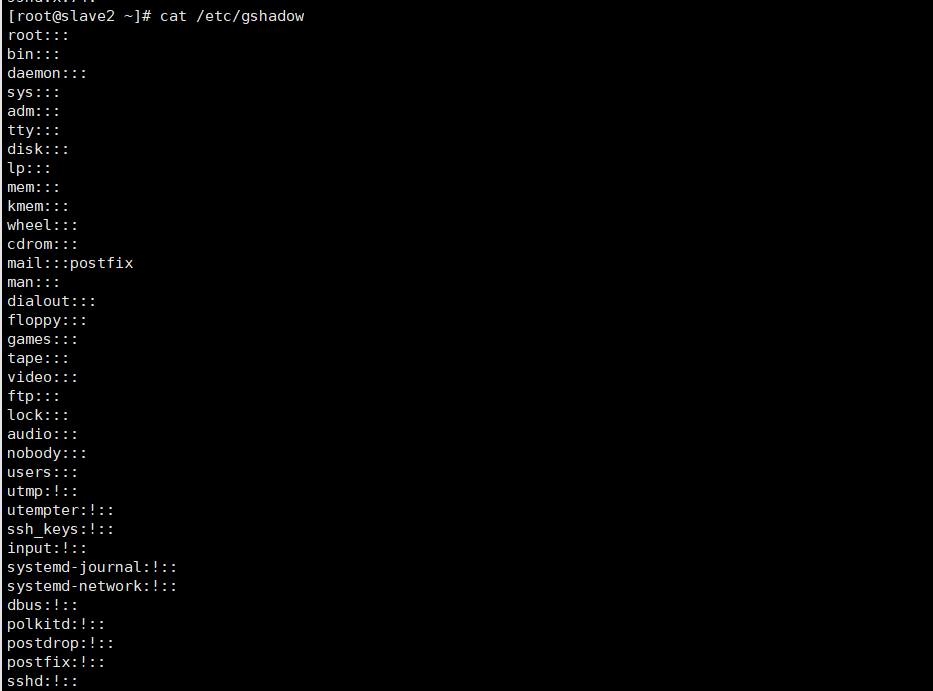
cat /etc/gshadow
5 create user useradd
The created user is saved in the / etc/passwd file
5.1 parameters
-c<remarks>: Add remarks. The note text is saved in the passwd In the remarks field of the; -d<Login directory>: Specify the start directory when the user logs in; -D: Change the preset value; -e<Term of validity>: Specify the validity period of the account number; -f<Buffer days>: Specify how many days after the password expires to close the account; -g<group >: Specify the group to which the user belongs; -G<group >: Specify the additional group to which the user belongs; -m: Automatically establish user login directory; -M: Do not automatically create user login directory; -n: Cancel the establishment of a group named by the user name; -r: Establish system account; -s<shell>: Specifies the password to use after the user logs in shell; -u<uid>: Designated user
5.2 actual combat drill
5.2. 1 create users and join groups
Insert the code slice here
5.2. 2 create user and set ID
useradd charles -u 520
Note: when setting the ID value, try to be greater than 500 to avoid conflict, because some special users will be established after linux Installation. Generally, the value between 0 and 499 is reserved for system accounts such as bin and mail.
5.3 examples
Create a user tom, set the uid to 556 and the home directory to / usr/tom, belonging to the users group:
useradd -u 544 -d /usr/tom -g users -m tom
-m: If the home directory does not exist, it is created automatically
6. Modify user information usermod
-c<remarks>: Modify the remarks of the user account; -d<Login directory>: Modify the directory when the user logs in; -e<Term of validity>: Modify the validity period of the account number; -f<Buffer days>: Modify the number of days after the password expires to close the account; -g<group >: Modify the group to which the user belongs; -G<group >;Modify the additional group to which the user belongs; -l<Account name >: Modify the user account name; -L: Lock the user password to make it invalid; -s<shell>: Modify the password used after the user logs in shell; -u<uid>: Modify user ID; -U:Unlock password.
6.1 add tom user to staff
usermod -G staff tom
6.2 modify the tom user name to tom1
usermod -l tom1 tom
6.3 lock account 1
usermod -L tom1
6.3 unlock tom1 user
usermod -U tom1
7 delete user userdel
-f: Forcibly delete the user, even if the user is currently logged in; -r: Delete all files related to the user while deleting the user.
7.1 deleting users without deleting directories and files
userdel linuxde
7.2 delete user directory files together
Remember to back up in advance
userdel -r linuxde
It's OK to delete it in / etc/passwd, but be careful not to make mistakes (not recommended).
Reference article:
https://www.cnblogs.com/ruanni/p/13922064.html
https://blog.csdn.net/thq0201/article/details/7195152
https://www.huaweicloud.com/articles/116bf3e57ee2a75bd74b121f146b5337.html
https://www.runoob.com/linux/linux-user-manage.html