Title Link:https://pan.baidu.com/s/1s9J89ppouArOR8XdCoG_ug
Extraction Code: 7szc
Get ready
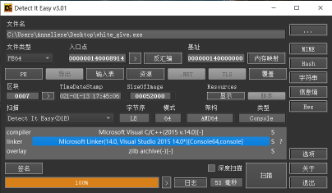
Or do you want to check the basics first?
64-bit shell-less
static analysis
Drag ida to look at the string but find many python functions
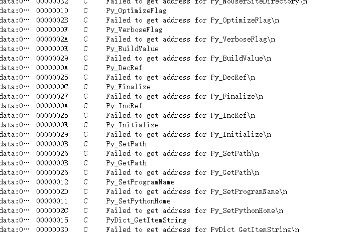
So we can guess that this is a python file
Then you need to restore the exe file to the py file
Seeing this reminds me of a previous example of Happy New Year. It looks like the two topics should have the same idea]
So it's good to do more examples
Installation Tools
Download Ming Loh's python decompile project
Links: https://github.com/countercept/python-exe-unpacker
Download the software wxmedit that edits the hexadecimal
Official website: http://wxmedit.github.io/zh_CN/downloads.html
Install uncompyle
In Terminal Input
pip install uncompyle
python-exe-unpacker-master (extracting file resources)
PyInstaller Extractor is a resource content that extracts the windows executable created by PyInstaller.
The default icons for exe made with PyInstaller are as follows:

Place the pyinstxtractor.py and exe files in the same directory
python pyinstxtractor.py xx.exe
You can also be in a different directory but add an absolute path to the file
First we found the downloaded python-exe-unpacker-master directory to run cmd
Input in terminal
pyinstxtractor.py + white_give file location
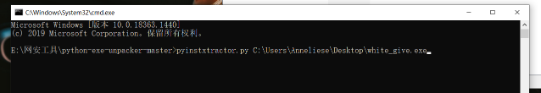
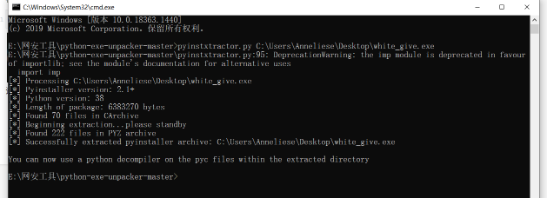
A new folder was found in the directory after running successfully
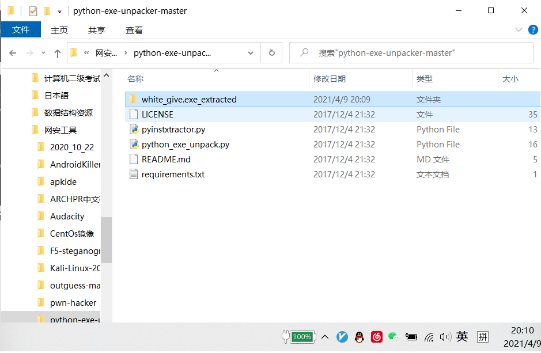
After running, the xx.exe_extracted folder is generated, into which various files are added.
Targeting some suffix-free files (usually the same as the title name) is actually a pyc file with fewer pyc headers
Go into the folder and find two files, struct and white_give (one is required to complete struct and the other is the file name of exe)
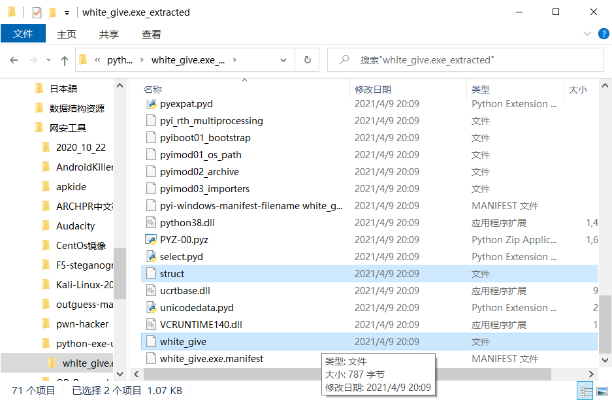
wxmedit(exe -> pyc)
Open the downloaded wxMEdit and open both files inside
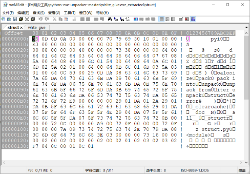
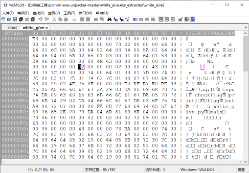
Comparing the two files found that white_give is missing a py header
So we copy the header file from the struct to white_give
When copying, note to move the mouse cursor to the position of line E3, hold down the left key, and slide to the front of line 55
Then click Copy again or it will be easy to copy errors
What it looks like after copying
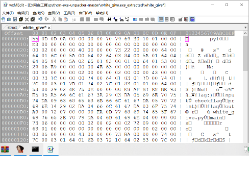
After clicking Save, go back to the directory and find white_give again and rename it white_give.pyc
Uncompyle(pyc -> py)
And run cmd input in this directory
uncompyle6 white_give.pyc
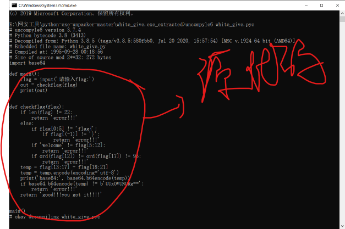
You can see the source code after running successfully
Is it not too good to see the source code only in the terminal
Let's continue converting files to py files
Current directory reruns cmd input
uncompyle6 white_give.pyc > white_give.py
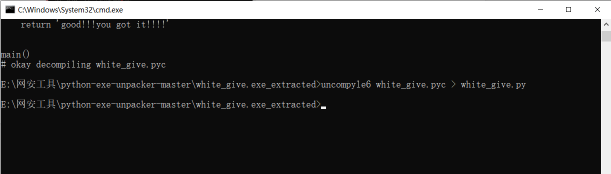
You will see that white_give.py was generated after running successfully
Open white_give.py to see the source code
Algorithmic Reverse
Next, flag can be analyzed by simply analyzing the code
# uncompyle6 version 3.7.4
# Python bytecode 3.8 (3413)
# Decompiled from: Python 3.8.5 (tags/v3.8.5:580fbb0, Jul 20 2020, 15:57:54) [MSC v.1924 64 bit (AMD64)]
# Embedded file name: white_give.py
# Compiled at: 1995-09-28 00:18:56
# Size of source mod 2**32: 272 bytes
import base64
def main():
flag = input('Please enter flag:')
out = checkflag(flag)
print(out)
def checkflag(flag):
if len(flag) != 22: //flag length is 23
return 'error!!!'
else:
if flag[0:5] != 'flag{': //The first five bits of flag are flag{
if flag[(-1)] != '}': //flag last bit is}
return 'error!!!'
if 'welcome' != flag[5:12]: //flag6 to 11 bits are welcome
return 'error!!!' //flag{welcome_****_***}
if ord(flag[12]) != ord(flag[17]) != 95: //ord() function=char() function
return 'error!!!' //The character represented by ASC II95 is''
temp = flag[13:17] + flag[18:21] //1318 bit is''
temp = temp.encode(encoding='utf-8') //temp is 14 to 18 bits of flag
print('base64:', base64.b64encode(temp)) // 19 to 22 bits and is
if base64.b64encode(temp) != b'UUxOVUNURg==': //'UUxOVUNURg=='
return 'error!!!' //base64 Decryption
return 'good!!!you got it!!!!' //'UxOVUNURg=='decrypted to QLNUCTF
// flag{welcome_QLNU_CTF}
main()
flag{welcome_QLNU_CTF}