At present, it is found that the online CFS three-tier intranet shooting range is basically built by using VM virtual machine. I want to try whether I can use docker to combine the existing vulnerability environments and build them directly through docker compose. The docker environments used are from vulnhub
First, try to build containers that can communicate with each other. This involves the creation and use of docker network. The environment is Windows for Docker
First, we start two containers, Tomcat and Shiro, and docker network ls. Docker compose generates two independent virtual bridge devices
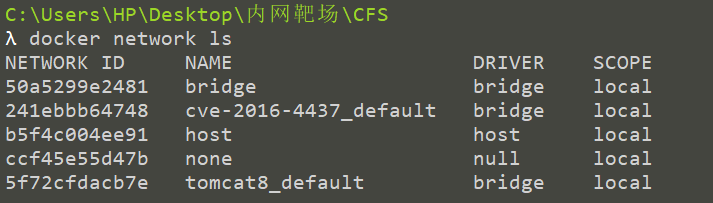
Shiro's container
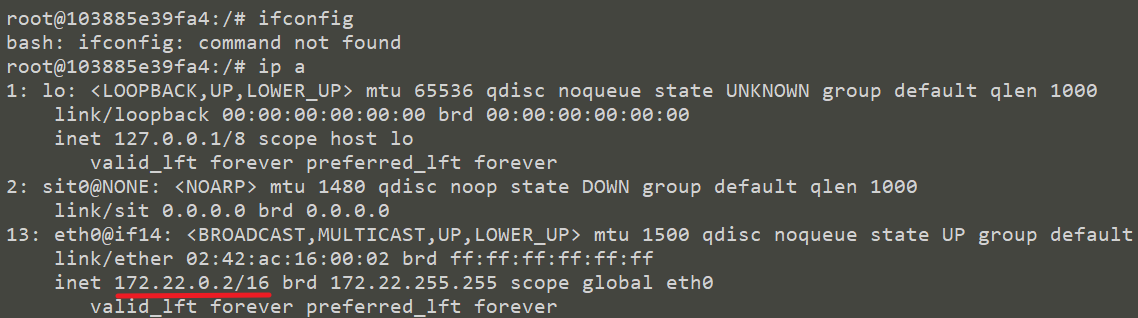
Tomcat container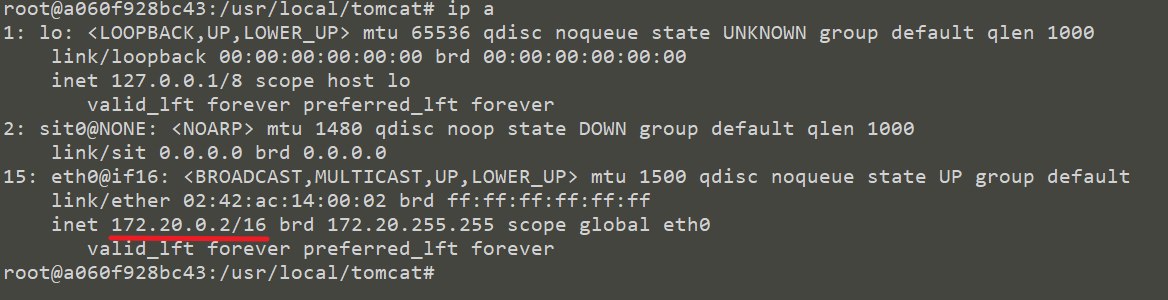
Now the two docker containers are in different network segments and cannot communicate with each other. We need to create a new docker network to connect both containers to this network
Set the desired network segment and create the network through docker network create. You can also specify the subnet and ip range
docker network create --driver bridge --subnet 192.168.12.0/16 --gateway 192.168.12.1 --ip-range 192.168.12.0/24 ****CFS
Then docker network connect connects the container to the network card device and specifies the ip address
docker network connect --ip 192.168.12.10 CFS 07c6f6b5c207 docker network connect --ip 192.168.12.100 CFS 4456375e7f25
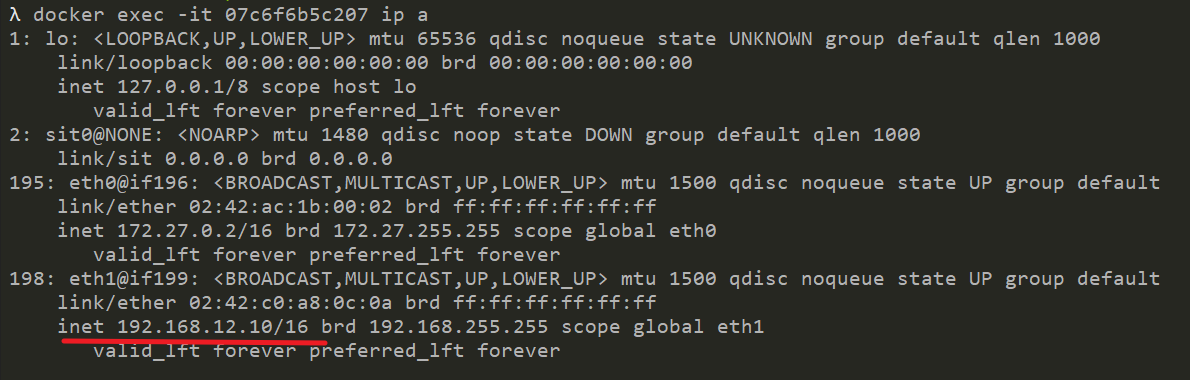
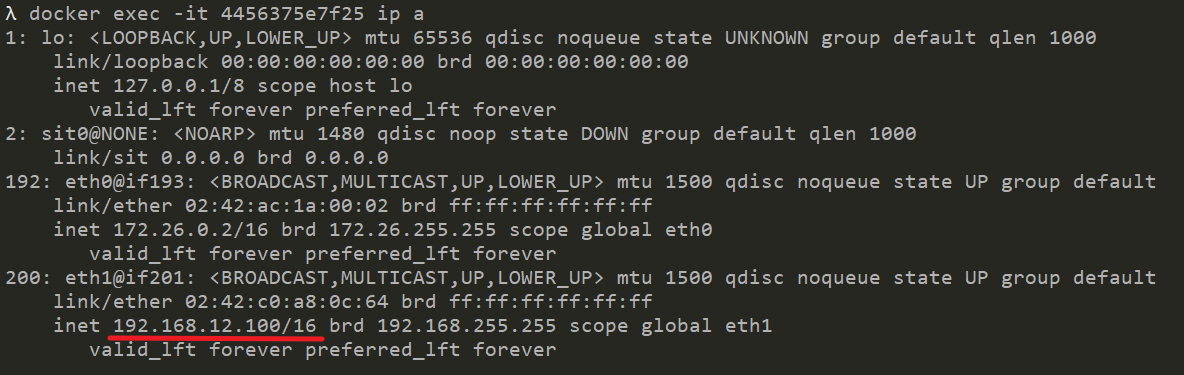
In this way, the two containers can communicate with each other
I checked the description of networks in the docker compose document again. You can create networks in compose and add multiple networks in a container service, so that you can create an intranet environment
Network configuration of compose in the document:
https://deepzz.com/post/docker-compose-file.html#toc_31
ipv4_address
Specify a static IP address for the container of this service when joining the network.
The corresponding network configuration in the top-level network section must have an ipam block containing the subnet and gateway configuration of each static address.
ipam
Specify custom IPAM configuration. This is an object with multiple attributes, each of which is optional:
- Driver: customize IPAM driver instead of default.
- config: a list with zero or more configuration blocks, each containing any of the following keys:
- Subnet: indicates the subnet in CIDR format of the network segment
- ip_range: IP range from which to allocate container IPs
- Gateway: IPv4 or IPv6 gateway of the primary subnet
- aux_addresses: the secondary IPv4 or IPv6 address used by the network driver as the mapping from host name to IP address
- Options: drive specific options as key value mapping.
Combined with the official example, we can use docker compose YML, which directly creates different network segment services without adding port mapping, can realize an intranet accessible environment
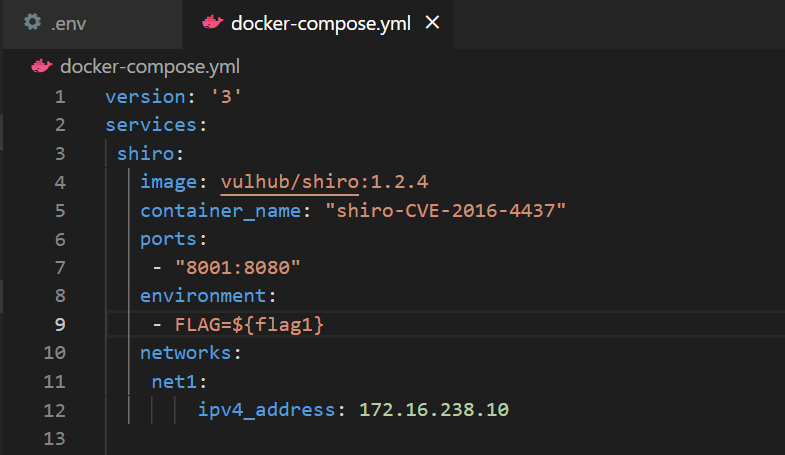
docker-compose.yml
version: '3'
services:
shiro:
image: vulhub/shiro:1.2.4
container_name: "shiro-CVE-2016-4437"
ports:
- "8001:8080"
environment:
- FLAG=${flag1}
restart: always
networks:
net1:
ipv4_address: 172.16.238.10
tomcat:
image: vulhub/tomcat:8.0
container_name: "tomcat8-weakpassword"
volumes:
- ./tomcat8/tomcat-users.xml:/usr/local/tomcat/conf/tomcat-users.xml
- ./tomcat8/context.xml:/usr/local/tomcat/webapps/manager/META-INF/context.xml
- ./tomcat8/context.xml:/usr/local/tomcat/webapps/host-manager/META-INF/context.xml
#Without port mapping, you can only access it on the intranet
expose:
- "8080"
environment:
- FLAG=${flag2}
restart: always
networks:
net1:
ipv4_address: 172.16.238.81
net2:
ipv4_address: 10.10.5.6
weblogic:
image: vulhub/weblogic:10.3.6.0-2017
container_name: "weblogic-weakpassword"
volumes:
- ./weblogic/web:/root/Oracle/Middleware/user_projects/domains/base_domain/autodeploy
expose:
- "7001"
- "5556"
environment:
- FLAG=${flag3}
restart: always
networks:
net2:
ipv4_address: 10.10.5.88
net3:
ipv4_address: 172.42.66.10
jboss:
image: vulhub/jboss:as-6.1.0
container_name: "jboss-CVE-2017-12149"
expose:
- "9990"
- "8080"
environment:
- FLAG=${flag4}
restart: always
networks:
net3:
ipv4_address: 172.42.66.77
networks:
net1:
ipam:
config:
- subnet: "172.16.0.0/16"
#ip_range: "172.16.238.0/24"
net2:
ipam:
config:
- subnet: "10.10.5.0/24"
net3:
ipam:
config:
- subnet: "172.42.66.0/24"
The link of the complete Docker configuration file is as follows:
https://github.com/yanshu-smile/CFS-Docker
Set flag
Because the image built by vulnhub is used, it is not convenient to modify the command executed by the portal to generate a flag
So write env file
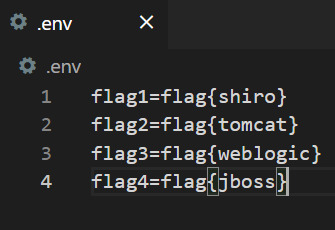
Write flag to container environment variable