Wazuh consists of three parts: Agent side, Server side and ES side
The following figure is the official overall structure diagram:
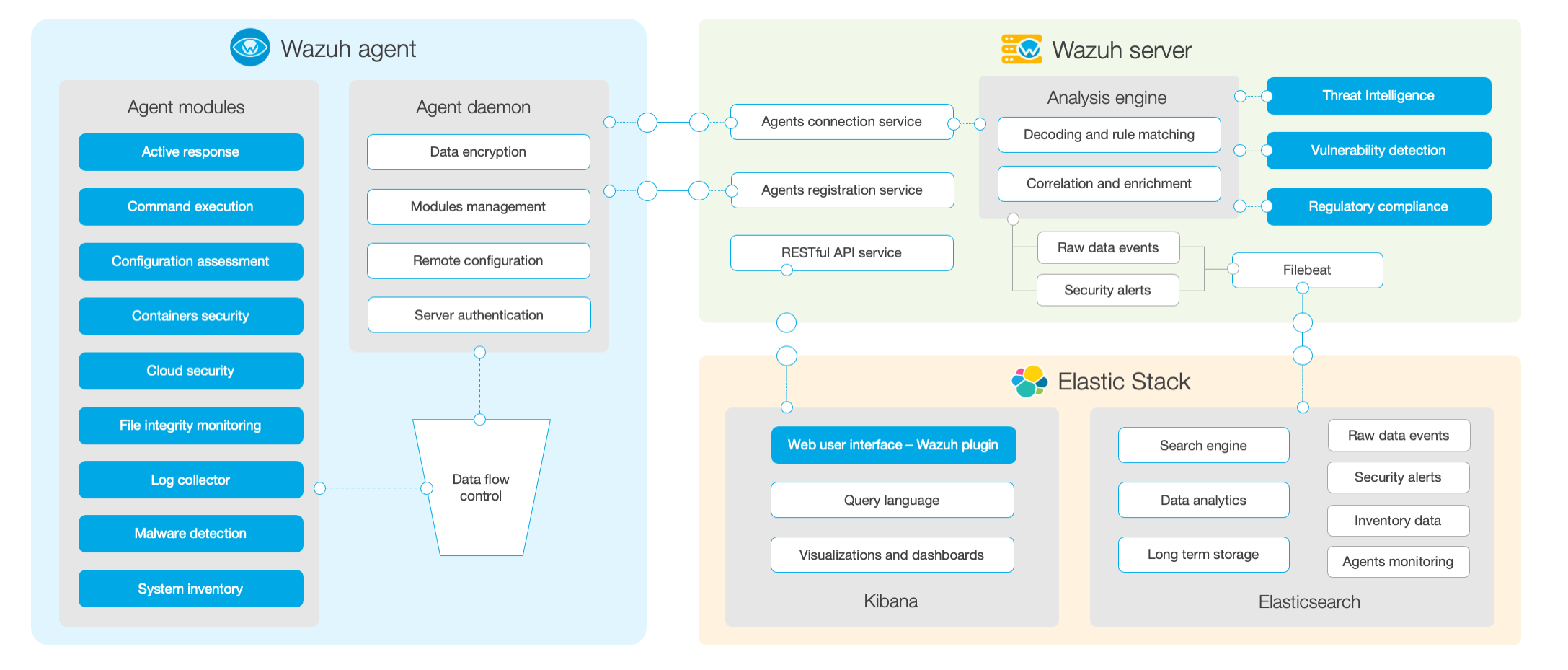
Agent
The agent side is responsible for information collection, threat prevention, detection and response. Continue to watch in detail~~
The following figure shows the official detailed architecture of the Agent side:
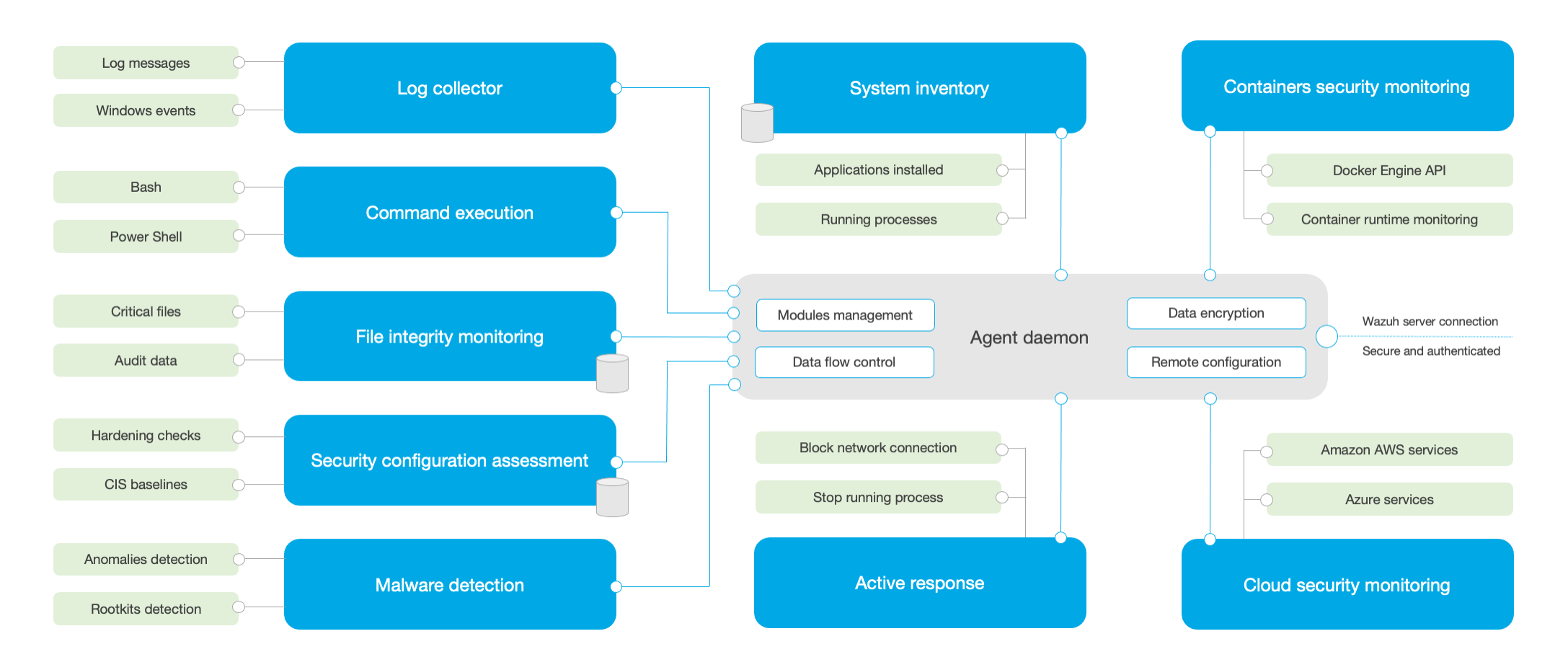
Here are some of his functions~~
Log collector
This module can read log information and Windows events
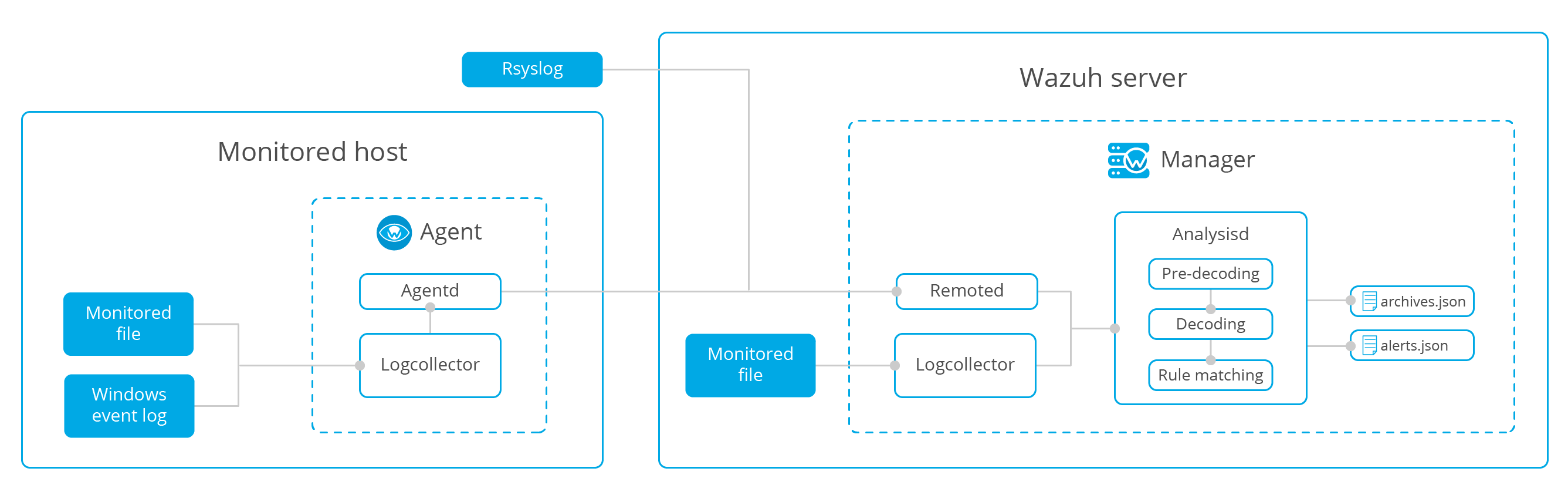
The included logcollector module collects information and sends the data to the server for analysis
Here, the remote receiving system log is realized: (the user-defined port is accepted and stored in a plain text file)
<ossec_config>
<remote>
<connection>syslog</connection>
<port>513</port>
<protocol>tcp</protocol>
<allowed-ips>192.168.2.0/24</allowed-ips>
</remote>
</ossec_config>
The code that implements the custom port indicates
- The manager will receive the system log information from the network
- Define wazuh the port that needs to listen and retrieve logs as idle port 513
- Defines the transport protocol
- Define log source IP
File integrity monitoring
The module scans regularly, compares the monitored files with the previous ones for modification, deletion and addition, and then synchronizes the results to the database and transmits them to the manager. If there is a difference, an alarm is generated.
Visualization results can be seen in kibana in real time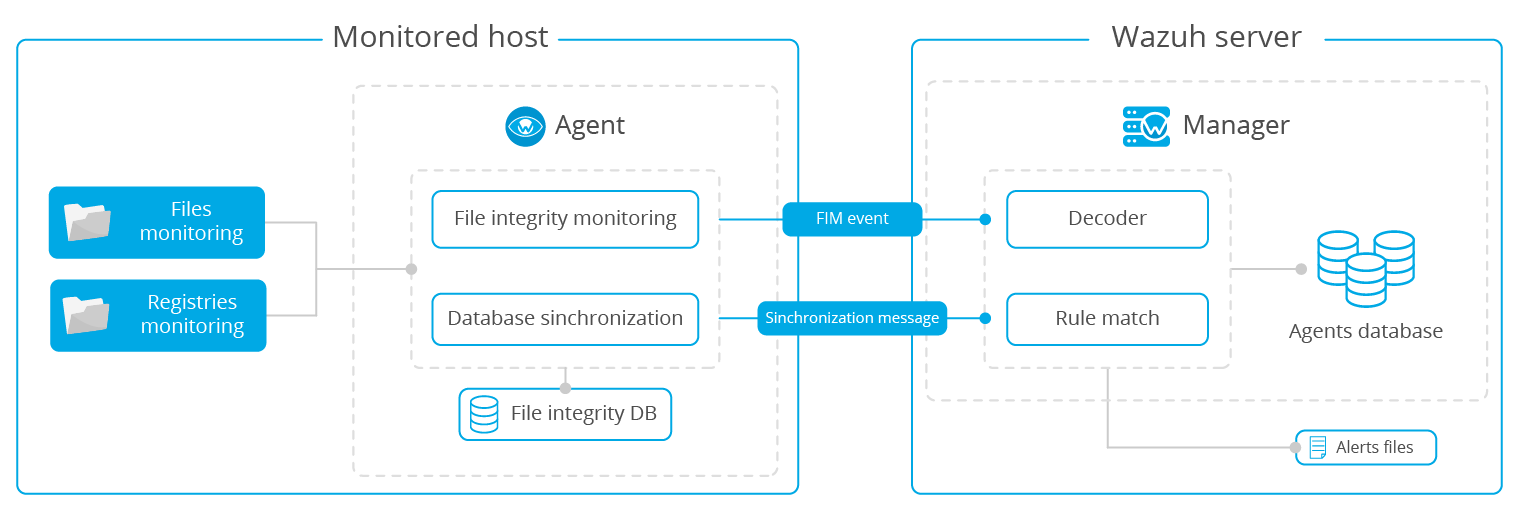
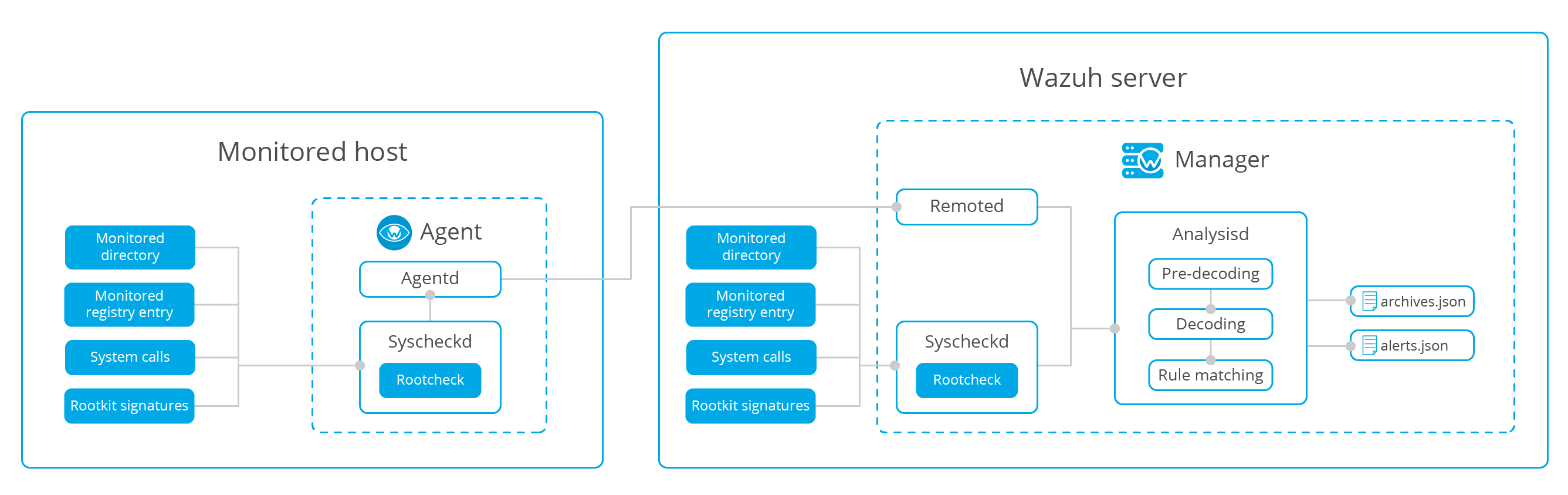
Anomaly and malware detection
This module mainly includes the following functions:
File monitoring
Monitor registry
system call
Signature rootkit
Security Configuration Assessment
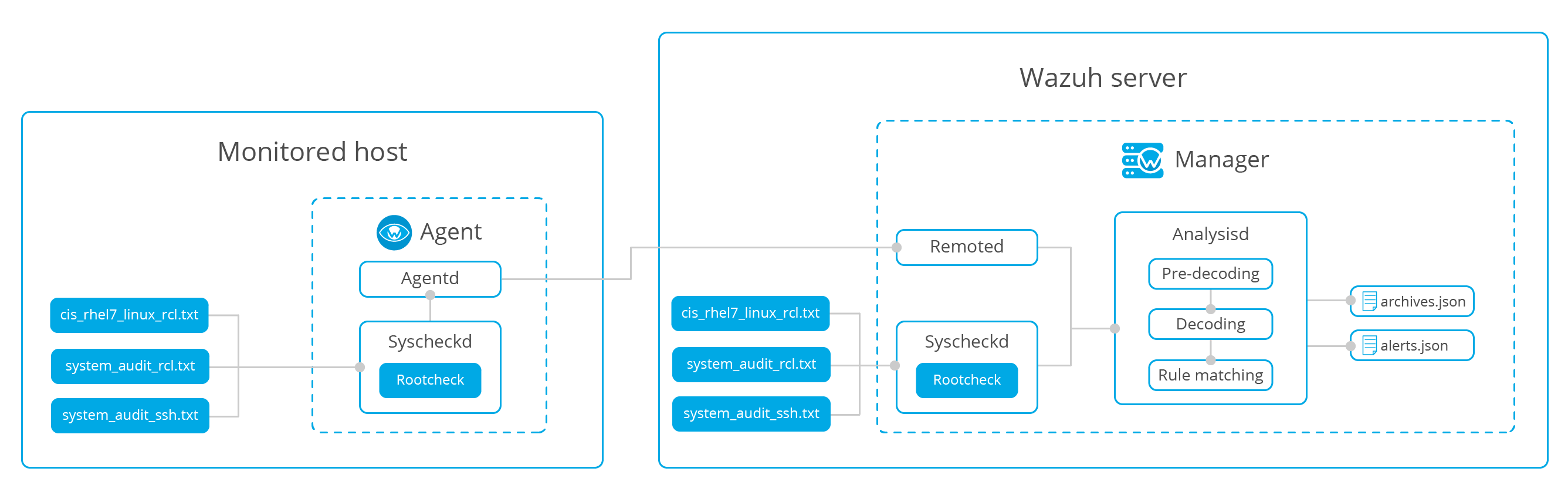
Security configuration assessment (SCA), which evaluates whether the host is secure by scanning the policy file

Monitoring security policies->Rootcheck
View through root check engine:
- Check if the process is running
- Check whether the file exists
- Check whether the contents of the file contain patterns, or whether the Windows registry key contains strings or exists only.
Monitoring system calls
It is a service provided by the Linux system. Match the tracked security event information with the rules to check whether it violates the settings of the security policy.
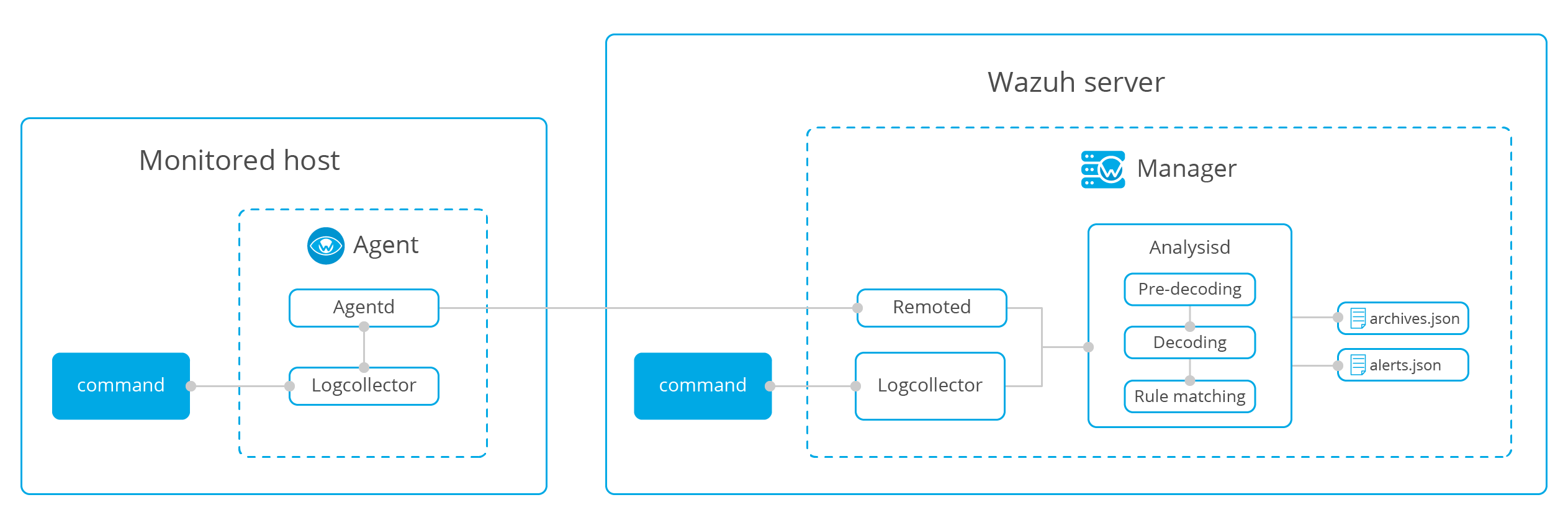
Command monitoring
wazuh will collect the specific commands to be monitored on the Agent side and send them to the server in the form of logs. You can monitor running Windows processes, disk space utilization, check whether the output changes, average load and USB storage
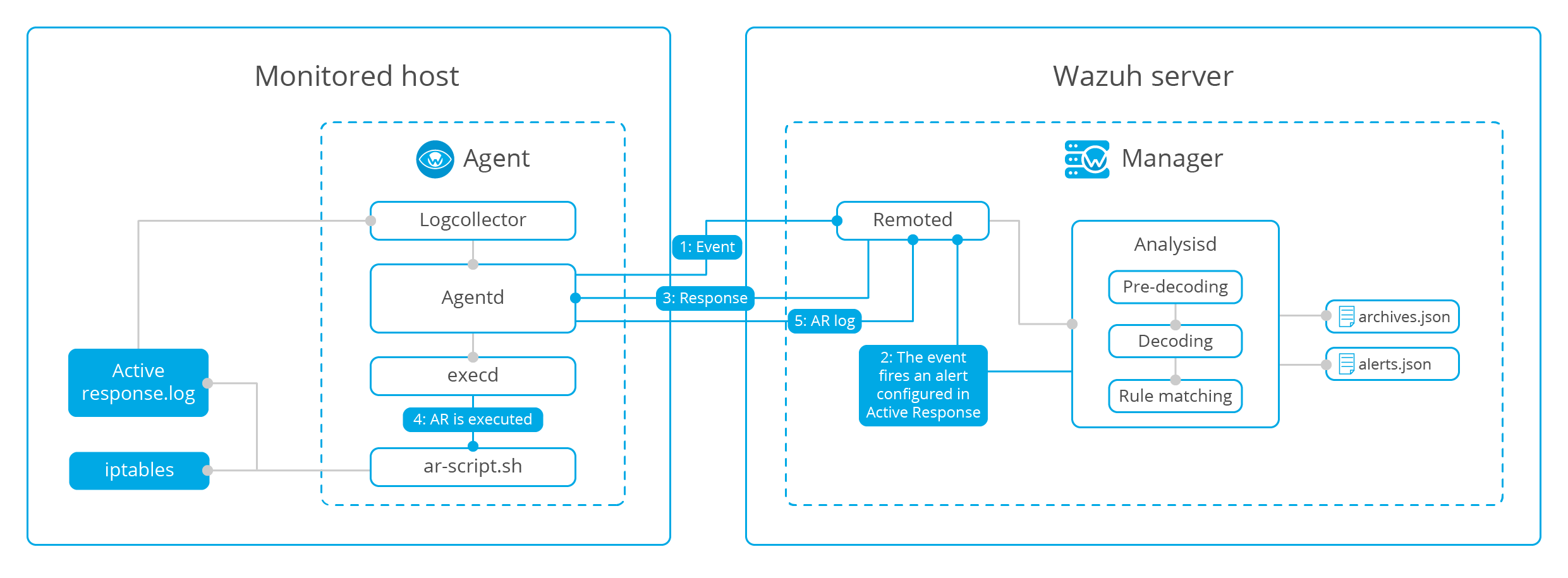
Active Response
When a rule is used to trigger an alarm, automatic countermeasures will be taken to execute the corresponding script
Agent Labels
Classify different agent groups, and the grouping will be displayed in the output of JSON format, for example!
{
"timestamp": "2017-03-07T13:31:41-0800",
"rule": {
"level": 7,
"description": "Integrity checksum changed.",
"id": "550",
"firedtimes": 1,
"groups": [
"ossec",
"syscheck"
],
"pci_dss": [
"11.5"
]
},
"agent": {
"id": "001",
"name": "92603de31548",
"ip": "192.168.66.1",
"labels": {
"aws": {
"instance-id": "i-052a1838c",
"sec-group": "sg-1103"
},
"network": {
"ip": "172.17.0.0",
"mac": "02:42:ac:11:00:02"
}
}
},
"manager": {
"name": "ubuntu"
},
"full_log": "Integrity checksum changed for: '/var/ossec/etc/ossec.conf' Size changed from '3663' to '3664' Old md5sum was: '98b351df146410f174a967d726f9965e' New md5sum is : '7f4f5846dcaa0013a91bd6d3ac4a1915' Old sha1sum was: 'c6368b866a835b15baf20976ae5ea7ea2788a30e' New sha1sum is : 'c959321244bdcec824ff0a32cad6d4f1246f53e9'",
"syscheck": {
"path": "/var/ossec/etc/ossec.conf",
"size_before": "3663",
"size_after": "3664",
"perm_after": "100640",
"uid_after": "0",
"gid_after": "999",
"md5_before": "98b351df146410f174a967d726f9965e",
"md5_after": "7f4f5846dcaa0013a91bd6d3ac4a1915",
"sha1_before": "c6368b866a835b15baf20976ae5ea7ea2788a30e",
"sha1_after": "c959321244bdcec824ff0a32cad6d4f1246f53e9",
"event": "modified"
},
"decoder": {
"name": "syscheck_integrity_changed"
},
"location": "syscheck"
}
Or in the form of e-mail:!!
Wazuh Notification. 2017 Mar 07 13:31:41 Received From: (92603de31548) 192.168.66.1->syscheck Rule: 550 fired (level 7) -> "Integrity checksum changed." Portion of the log(s): aws.instance-id: i-052a1838c aws.sec-group: sg-1103 network.ip: 172.17.0.0 network.mac: 02:42:ac:11:00:02 Integrity checksum changed for: '/var/ossec/etc/ossec.conf' Old md5sum was: '98b351df146410f174a967d726f9965e' New md5sum is : '7f4f5846dcaa0013a91bd6d3ac4a1915' Old sha1sum was: 'c6368b866a835b15baf20976ae5ea7ea2788a30e' New sha1sum is : 'c959321244bdcec824ff0a32cad6d4f1246f53e9'
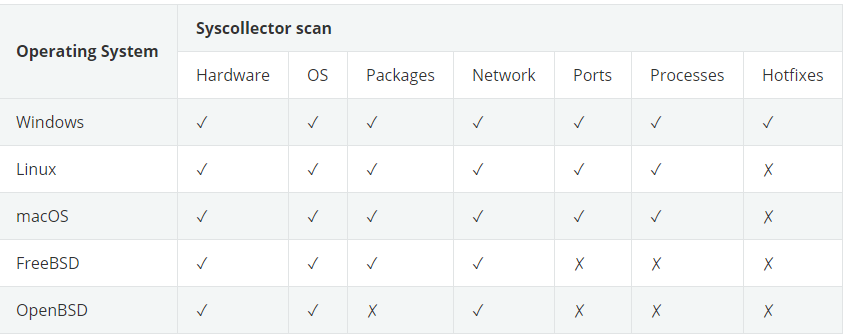
System inventory
In this module, syskellector is used to collect information, such as basic information of system hardware components, basic information of operating system, etc
The applicable operating system and scanning module are given below:
Vulnerability detection
It can detect whether the installed application on the agent side has vulnerabilities and send it to the server side regularly
VirusTotal integration
From version 3.0.0, wazuh can integrate VirusTotal to scan whether the file contains malicious content (virus, worm, Trojan horse)
Osquery
Starting with version 3.5.0, you can set the Osquery configuration and collect the information generated by Osquery to send it to the manager, and generate corresponding alerts if necessary.
eg:
{
"timestamp": "2018-07-30T13:54:46.476+0000",
"rule": {
"level": 3,
"description": "osquery data grouped",
"id": "24010",
"firedtimes": 207,
"mail": false,
"groups": [
"osquery"
]
},
"agent": {
"id": "000",
"name": "manager"
},
"manager": {
"name": "manager"
},
"id": "1532958886.437707",
"full_log": "{\"name\":\"system_info\",\"hostIdentifier\":\"manager\",\"calendarTime\":\"Mon Jul 30 13:54:45 2018 UTC\",\"unixTime\":1532958885,\"epoch\":0,\"counter\":461,\"columns\":{\"cgroup_namespace\":\"4026531835\",\"cmdline\":\"\",\"cwd\":\"/\",\"disk_bytes_read\":\"0\",\"disk_bytes_written\":\"0\",\"egid\":\"0\",\"euid\":\"0\",\"gid\":\"0\",\"ipc_namespace\":\"4026531839\",\"mnt_namespace\":\"4026531840\",\"name\":\"migration/0\",\"net_namespace\":\"4026531957\",\"nice\":\"0\",\"on_disk\":\"-1\",\"parent\":\"2\",\"path\":\"\",\"pgroup\":\"0\",\"pid\":\"9\",\"pid_namespace\":\"4026531836\",\"resident_size\":\"\",\"root\":\"/\",\"sgid\":\"0\",\"start_time\":\"0\",\"state\":\"S\",\"suid\":\"0\",\"system_time\":\"2\",\"threads\":\"1\",\"total_size\":\"\",\"uid\":\"0\",\"user_namespace\":\"4026531837\",\"user_time\":\"0\",\"uts_namespace\":\"4026531838\",\"wired_size\":\"0\"},\"action\":\"added\"}",
"decoder": {
"name": "json"
},
"data": {
"action": "added",
"name": "system_info",
"hostIdentifier": "manager",
"calendarTime": "Mon Jul 30 13:54:45 2018 UTC",
"unixTime": "1532958885",
"epoch": "0",
"counter": "461",
"columns": {
"cgroup_namespace": "4026531835",
"cmdline": "",
"cwd": "/",
"disk_bytes_read": "0",
"disk_bytes_written": "0",
"egid": "0",
"euid": "0",
"gid": "0",
"ipc_namespace": "4026531839",
"mnt_namespace": "4026531840",
"name": "migration/0",
"net_namespace": "4026531957",
"nice": "0",
"on_disk": "-1",
"parent": "2",
"path": "",
"pgroup": "0",
"pid": "9",
"pid_namespace": "4026531836",
"resident_size": "",
"root": "/",
"sgid": "0",
"start_time": "0",
"state": "S",
"suid": "0",
"system_time": "2",
"threads": "1",
"total_size": "",
"uid": "0",
"user_namespace": "4026531837",
"user_time": "0",
"uts_namespace": "4026531838",
"wired_size": "0"
}
},
"predecoder": {
"hostname": "manager"
},
"location": "osquery"
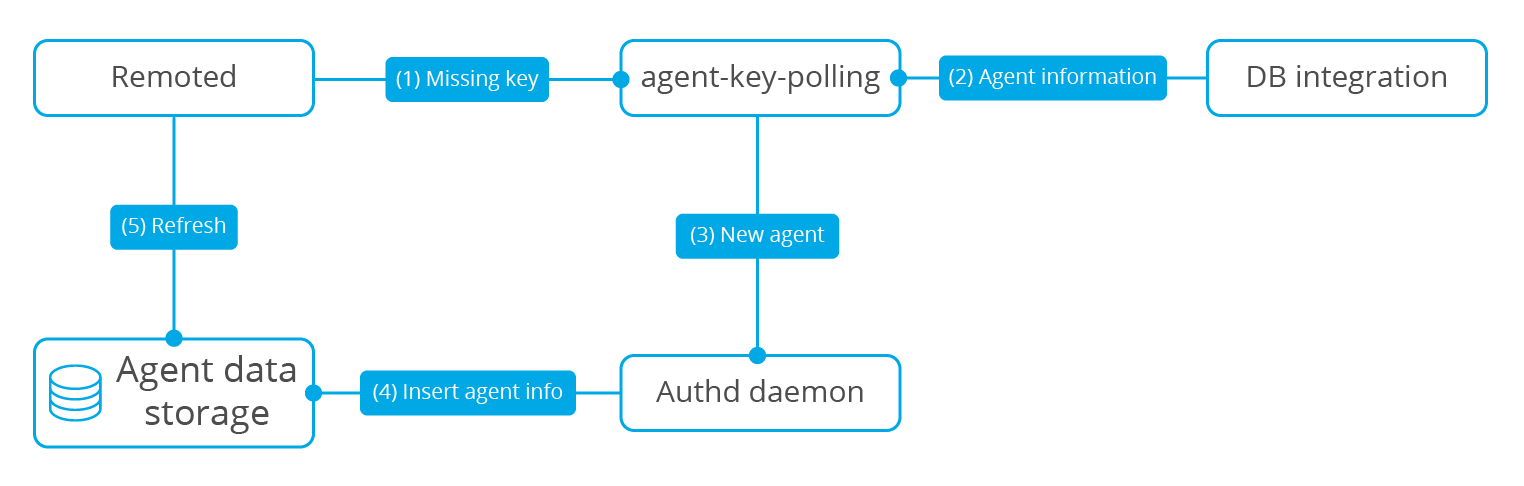
Agent key polling
polling: polling: the CPU sends out inquiries regularly and asks each peripheral device whether it needs its service in order. If so, it will give the service. After the service is finished, it will ask the next peripheral, and then continue to repeat
This module obtains the user key stored in the external database