DVWA platform is an effective way for beginners of network security to understand the ten vulnerabilities. This platform collects the ten most common vulnerabilities threatening network security, and provides a shooting range experimental environment for beginners. We can use this platform to carry out various attack experiments, so as to enrich our understanding of Web security.
This article mainly introduces one of the high-risk vulnerabilities in DVWA platform: the test of SQL injection vulnerability and the PHP source code analysis of SQL Injection on DVWA platform.
Before the attack, we should first understand the principle of SQL injection attack. In the process of Web program running, the database is an indispensable part. When we use the Web program, the program will query the data in the database according to our operation, and the SQL injection vulnerability exists in this query process. The attacker uses some malicious script statements to embed these malicious statements into the database query statements, so as to destroy the original functions of the query statements and achieve the purpose of the attacker to obtain information illegally.
In the DVWA platform, each vulnerability is divided into four levels: low, medium, high and impossible. Next, I will start from low, gradually analyze the PHP source code of SQL injection vulnerability, and conduct relevant tests.
(1) low level
From the security level in the lower left corner, you can see the low level. Then start analyzing the low level code:
<?php
if( isset( $_REQUEST[ 'Submit' ] ) ) {
// Get input
$id = $_REQUEST[ 'id' ];
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
$result = mysql_query( $query ) or die( '<pre>' . mysql_error() . '</pre>' );
// Get results
$num = mysql_numrows( $result );
$i = 0;
while( $i < $num ) {
// Get values
$first = mysql_result( $result, $i, "first_name" );
$last = mysql_result( $result, $i, "last_name" );
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
// Increase loop count
$i++;
}
mysql_close();
}
?>From the PHP code, we can first judge that this page uses$_ REQUEST variable. When we click the Submit button, the program will insert the characters we entered into the query statement to query the database. In the low level, because$_ The REQUEST variable allows us to enter freely in the text box, and there is no defense means in the code, so there is character injection in this Web program. Next is the test process:
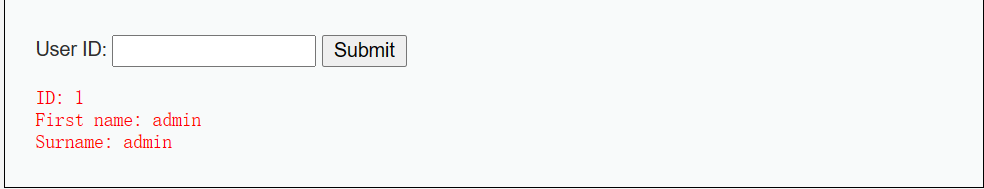
When I enter id=1, the program will query the user information with ID 1 in the database and echo it.
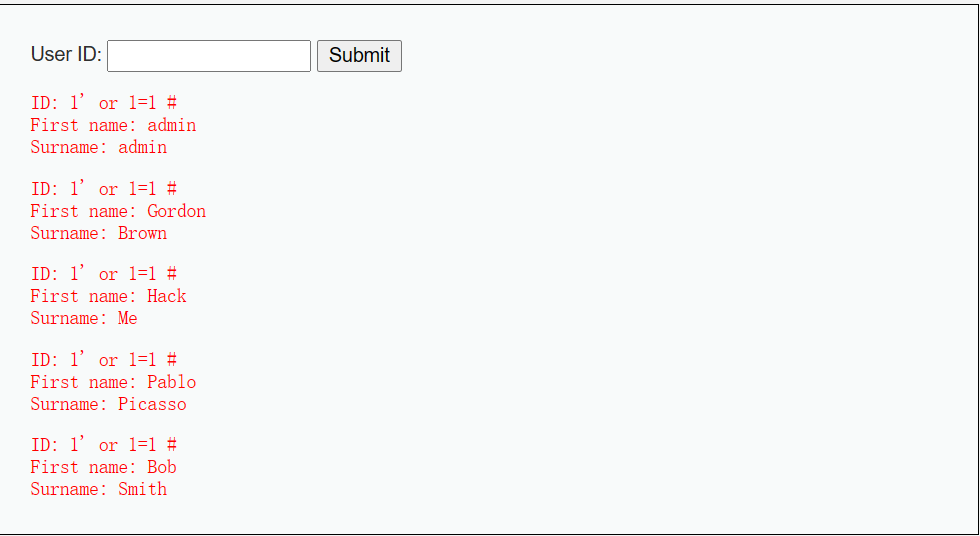
At this time, I enter 1 'or 1 = 1 #, and the echo result is like this. We can see that in the database query statement, it judges the id and user we entered_ Whether the IDs are the same. If they are consistent, assign the query results to the $result variable, and then use mysql_ num_ The rows() (mysql_num_rows() method returns the number of rows in the result set) method assigns the number of rows in the result set to $num and outputs the result through a loop. The 1 'or 1 = 1 # script we entered will cause the query statement to compare id and user_ Whether the IDs are consistent remains true, so all user information in the database is output.
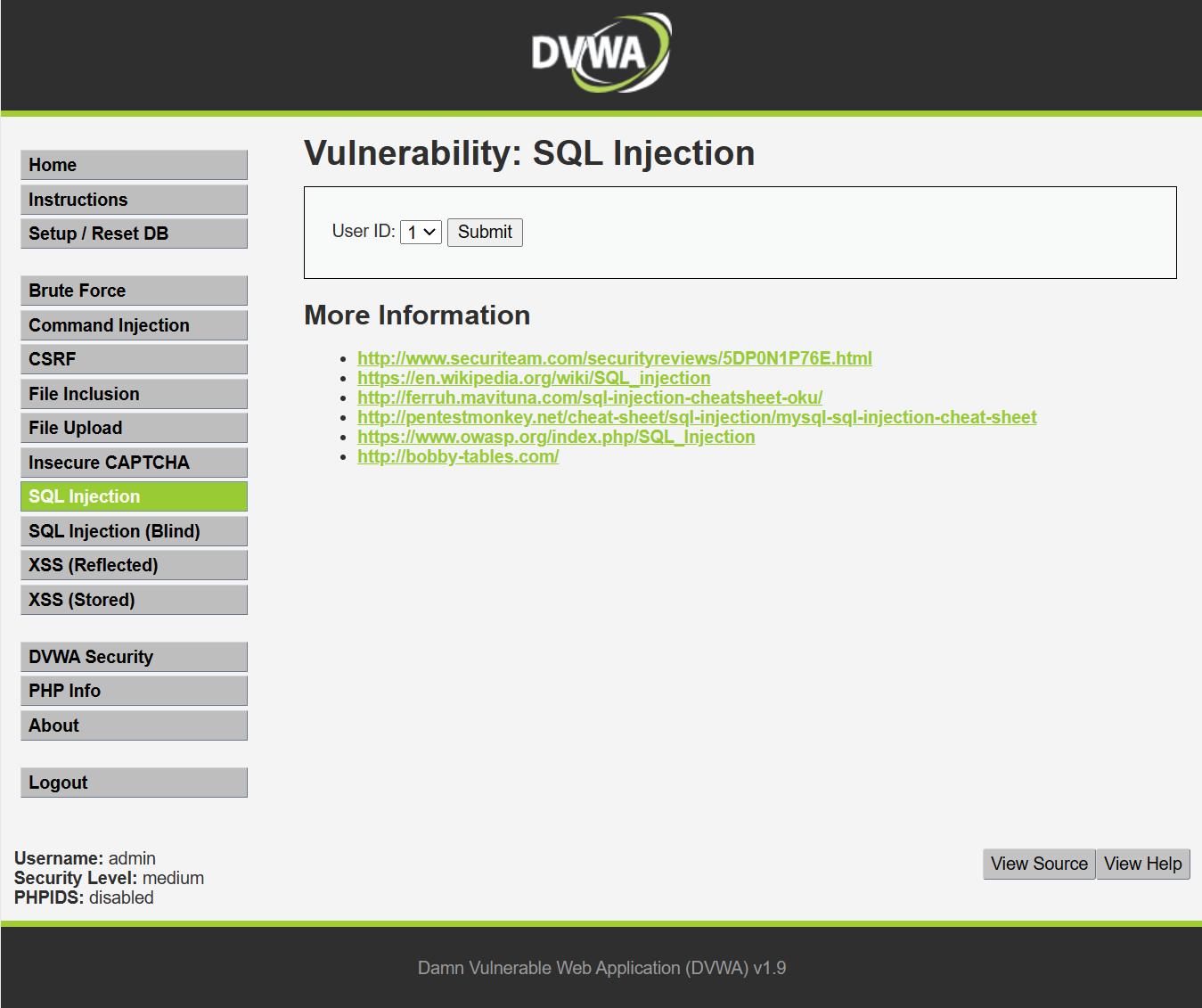
(2) medium level
<?php
if( isset( $_POST[ 'Submit' ] ) ) {
// Get input
$id = $_POST[ 'id' ];
$id = mysql_real_escape_string( $id );
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = $id;";
$result = mysql_query( $query ) or die( '<pre>' . mysql_error() . '</pre>' );
// Get results
$num = mysql_numrows( $result );
$i = 0;
while( $i < $num ) {
// Display values
$first = mysql_result( $result, $i, "first_name" );
$last = mysql_result( $result, $i, "last_name" );
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
// Increase loop count
$i++;
}
//mysql_close();
}
?> From the lower left corner of the page, we can see that it has been adjusted to the medium level. At this time, some changes have taken place on the page. The original text box has been replaced with a drop-down box. This is because the original $request variable has been changed to $POST variable in PHP code. Because the text box disappears, we cannot directly inject characters into the code, We also escaped the id value we entered, so we need to use the burp suite tool at this time. I encountered a problem in this step. After I started burpsuite and successfully set up the agent, I couldn't grab the traffic package of dvwa, but other web pages can still grab it, which is very strange
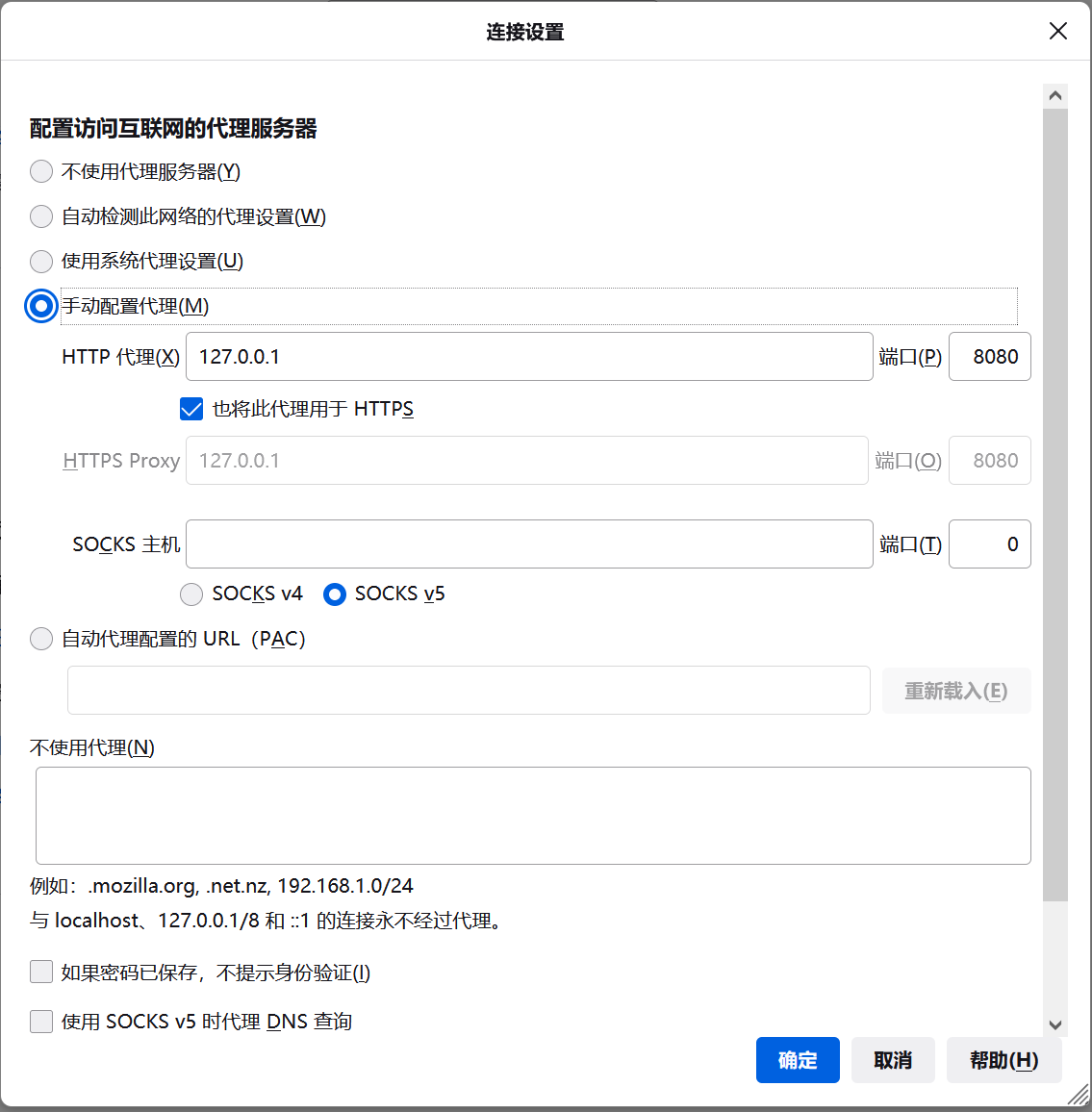
In Firefox's proxy settings, 127.0.0.1 is not added to the do not use proxy. After Baidu, I found that one method is to log in to dvwa directly using the local IP instead of using 127.0.0.1 dedicated to php. So I went to see my own IP, entered cmd in win+r, entered ipconfig in the command line, and then logged in to dvwa with my own IP address, Although I don't know what the reason is, I hope my little partner with the same problem can take fewer detours.
Back to the point, next, use burpsuite to attack SQL injection:
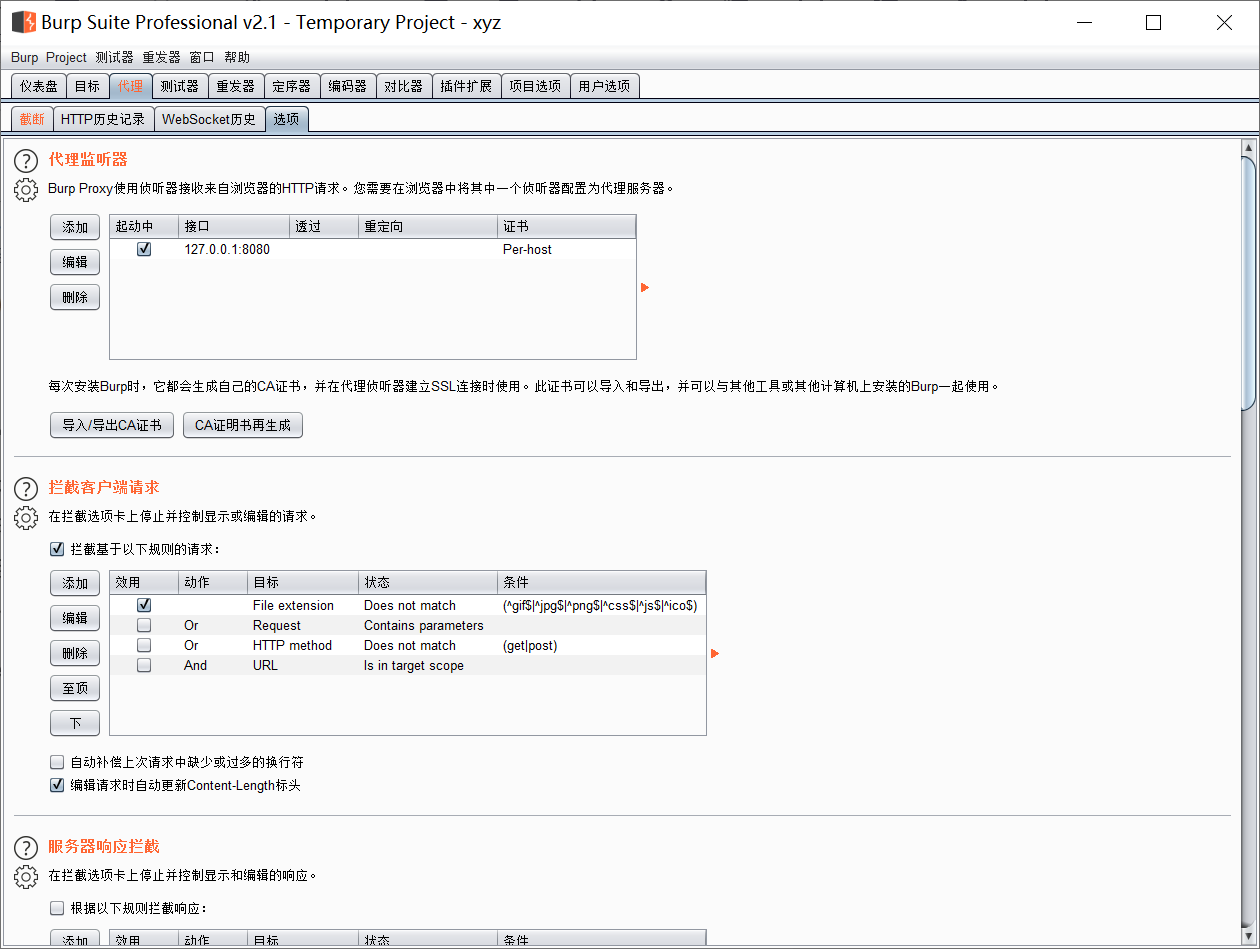
First, click the proxy in the upper left corner. I made a Chinese package. The original version should be proxy. Add port 8080 and local host in setting, and then click truncate. The original version is intercept to view the intercepted html requests.
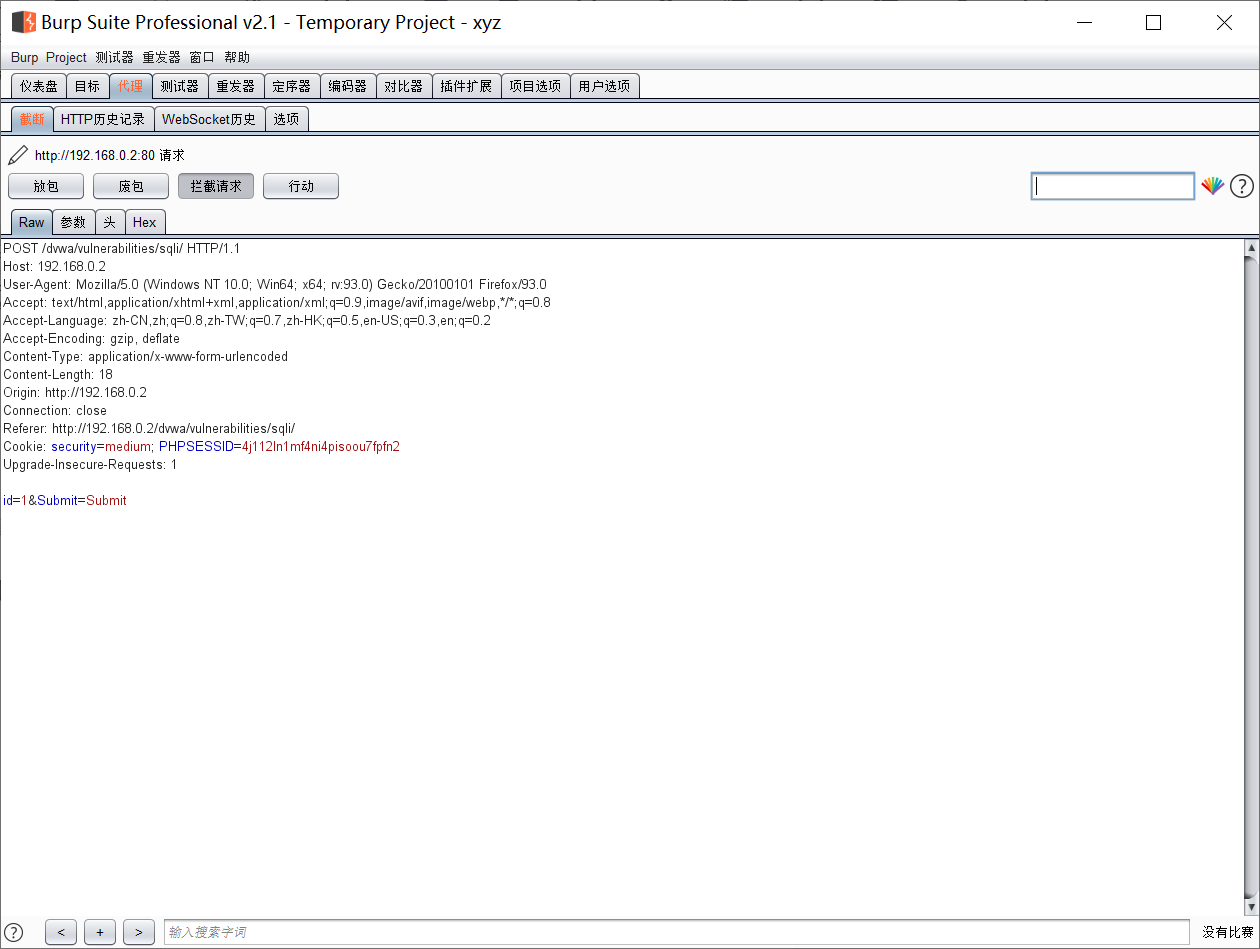
The last line of the intercepted traffic packet is the instruction we chose to enter at that time. At this time, the data after modifying the id is changed to 1'or1=1, which we used above. The injection is successful. From the php source code, we can see that the code has escaped characters, but the number has not escaped, so there is still digital injection, so the injection is successful.
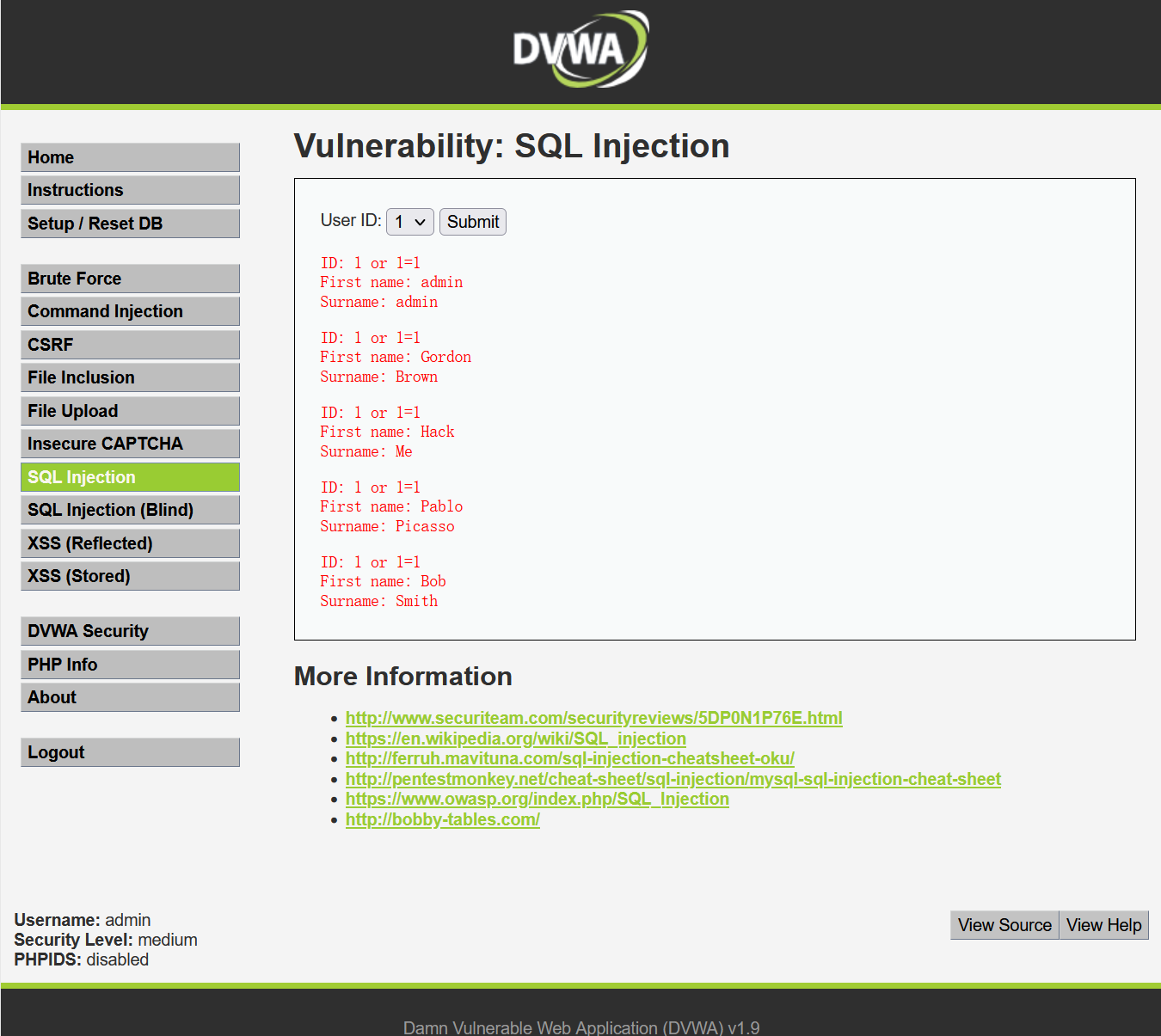
(3) high level
<?php
if( isset( $_SESSION [ 'id' ] ) ) {
// Get input
$id = $_SESSION[ 'id' ];
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
$result = mysql_query( $query ) or die( '<pre>Something went wrong.</pre>' );
// Get results
$num = mysql_numrows( $result );
$i = 0;
while( $i < $num ) {
// Get values
$first = mysql_result( $result, $i, "first_name" );
$last = mysql_result( $result, $i, "last_name" );
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
// Increase loop count
$i++;
}
mysql_close();
}
?> At this time, the security level is changed to high level. It is found that this time there is no drop-down box, and it directly becomes a pop-up command... Check the code and find that it is because the code is changed to$_ session variable, but there is no escape of characters in the code. What effect will it have if we directly click and inject and enter 1 'or 1 = 1#,
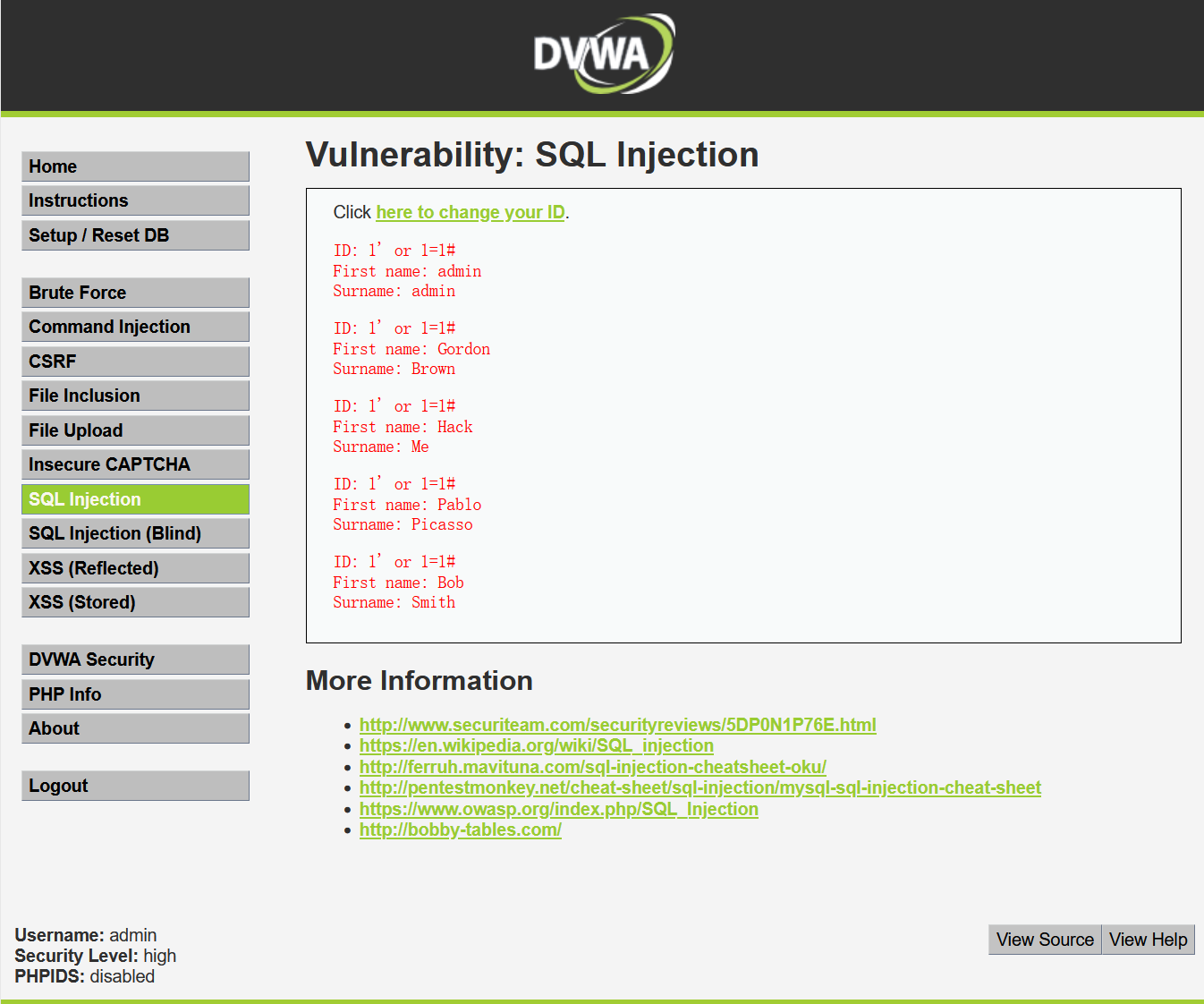
Unexpectedly, this direct injection succeeded. This high level doesn't feel as good as medium, but there is a pit in this code, that is, there is a limit 1 behind it. The function of this sentence is to return only one line of data. If the amount of returned data is greater than one line or the statement you enter is judged to be false, an error will be reported, Then you can't get into the high level of SQL injection. You can only go back in after restarting, so pay attention to the writing specification when entering payload, and remember to add spaces, otherwise it will be tears...
This is my personal understanding of the SQL injection part of DVWA. Welcome to communicate.