Hyperledger Fabric (HF) provides fabric-ca tools for end users to use their own CAs.However, root CAs should be as secure as possible in production environments, such as offline root CAs, and certificate issuance agents in Hyperledger Fabric environments should be given to the middle
CA.In this article, we will describe how to use third-party CAs as root CAs, fabric-ca as intermediate CAs, and how to integrate third-party CAs with fabric-ca in the CA trust chain.
1. Preparations
To demonstrate the use of external and intermediate CAs, we will deploy a root CA, which will only issue certificates for intermediate CAs.This intermediate CA uses a Fabric CA, which is responsible for issuing user and node certificates.For simplicity, in this tutorial, we'll make OpenSSL.
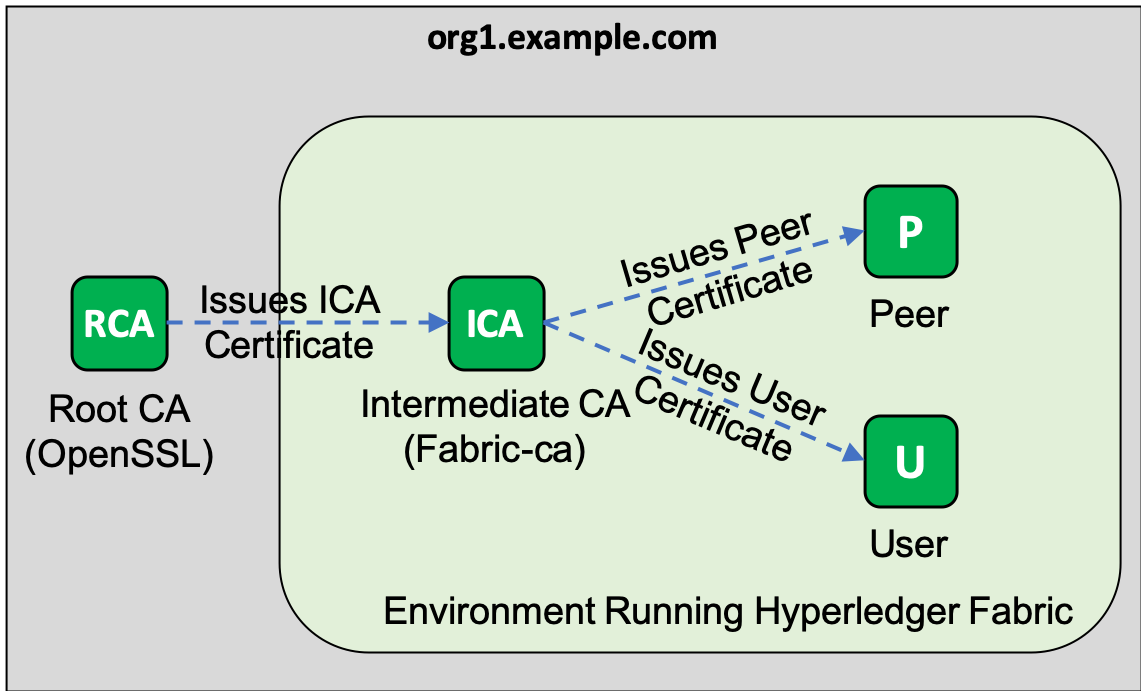
Before you begin, consult the appropriate documentation to complete the deployment and knowledge preparation of the following pre-links:
- Install docker, docker-compose, git, and curl
- Hyperledger Fabric and bash/sheel scripting Basics
- PKI Basics
Cloning this tutorial demonstrates the code repository, which contains all the scripts used:
git clone https://github.com/aldredb/external-ca cd external-ca
Download the Hyperledger Fabric precompiler and delete unnecessary files.We only use cryptogen, fabric-ca-client, and configtx.
curl -sSL http://bit.ly/2ysbOFE | bash -s -- 1.4.1 -d -s rm -f config/configtx.yaml config/core.yaml config/orderer.yaml
Use cryptogen to generate certificates and keys for the Sort Node Authority:
export PATH=$PWD/bin:$PATH
export FABRIC_CFG_PATH=${PWD}
cryptogen generate --config=./crypto-config.yaml
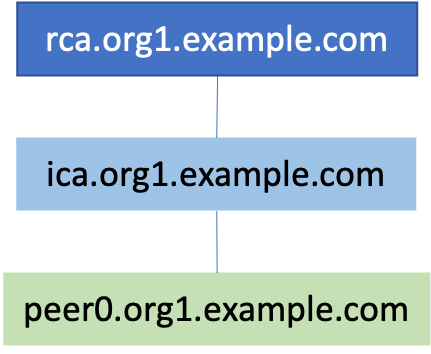
Create a directory structure to hold the certificates and keys of the peer node institution org1.example.com.As shown below, the organization contains a node, peer0.org1.example.com, and two users: admin and Admin@org1.example.com.The certificate and key of the intermediate CA are saved in the Ca folder.
ORG_DIR=$PWD/crypto-config/peerOrganizations/org1.example.com PEER_DIR=$ORG_DIR/peers/peer0.org1.example.com REGISTRAR_DIR=$ORG_DIR/users/admin ADMIN_DIR=$ORG_DIR/users/Admin@org1.example.com mkdir -p $ORG_DIR/ca $ORG_DIR/msp $PEER_DIR $REGISTRAR_DIR $ADMIN_DIR
2. Create intermediate CA
Generate private key and certificate signature request/CSR.Note that the values of the mechanism are the same as the root CA.
openssl ecparam -name prime256v1 -genkey -noout -out \ $ORG_DIR/ca/ica.org1.example.com.key.pem openssl req -new -sha256 -key $ORG_DIR/ca/ica.org1.example.com.key.pem \ -out $ORG_DIR/ca/ica.org1.example.com.csr \ -subj "/C=SG/ST=Singapore/L=Singapore/O=org1.example.com/OU=/CN=ica.org1.example.com"
The root CA is responsible for signing the CSR of the intermediate CA and Issuing the certificate, which has half the validity of the root CA certificate.Notice that we use the v3_intermediate_ca extension.
openssl ca -batch -config openssl_root.cnf -extensions v3_intermediate_ca \ -days 1825 -notext -md sha256 -in $ORG_DIR/ca/ica.org1.example.com.csr \ -out $ORG_DIR/ca/ica.org1.example.com.crt.pem
Now let's take a look at the certificates we get:
openssl x509 -in $ORG_DIR/ca/ica.org1.example.com.crt.pem -text -noout
As shown below, you can see that the issuing authority of the certificate is rca.org1.example.com:
Issuer: C=SG, ST=Singapore, L=Singapore, O=org1.example.com, CN=rca.org1.example.com
Validity
Not Before: May 3 10:16:44 2019 GMT
Not After : Apr 30 10:16:44 2029 GMT
Subject: C=SG, ST=Singapore, O=org1.example.com, CN=ica.org1.example.com
Once we have issued a certificate for the intermediate CA, the root CA is no longer needed unless you need to create another intermediate CA or recycle the certificate for the intermediate CA.
Now create a CA chain file that contains the certificates for the intermediate CA and genCA:
cat $ORG_DIR/ca/ica.org1.example.com.crt.pem \ $PWD/rca/certs/rca.org1.example.com.crt.pem > \ $ORG_DIR/ca/chain.org1.example.com.crt.pem
Finally, the intermediate CA is started, and its configuration file points to the certificates, keys, and CA chains we created earlier.
You can refer to the ca-config/fabric-ca-server-config.yaml file:
docker-compose up -d ica.org1.example.com
3. Issue peer node certificates and user certificates
With the intermediate CA ready, we can now issue user certificates and peer node certificates.
First join the (enroll) admin user, who has the right to register other users:
export FABRIC_CA_CLIENT_HOME=$REGISTRAR_DIR fabric-ca-client enroll --csr.names C=SG,ST=Singapore,L=Singapore,O=org1.example.com \ -m admin -u http://admin:adminpw@localhost:7054
Now use Admin@org1.example.com, the administrator of admin registry org1.example.com, and peer node peer0.org1.example.com:
fabric-ca-client register --id.name Admin@org1.example.com \ --id.secret mysecret --id.type client --id.affiliation org1 \ -u http://localhost:7054fabric-ca-client register \ --id.name peer0.org1.example.com --id.secret mysecret \ --id.type peer --id.affiliation org1 -u http://localhost:7054
Join Admin@org1.example.com:
export FABRIC_CA_CLIENT_HOME=$ADMIN_DIR fabric-ca-client enroll \ --csr.names C=SG,ST=Singapore,L=Singapore,O=org1.example.com \ -m Admin@org1.example.com \ -u http://Admin@org1.example.com:mysecret@localhost:7054 mkdir -p $ADMIN_DIR/msp/admincerts && \ cp $ADMIN_DIR/msp/signcerts/*.pem $ADMIN_DIR/msp/admincerts/
Join peer0.org1.example.com:
export FABRIC_CA_CLIENT_HOME=$PEER_DIRfabric-ca-client enroll \ --csr.names C=SG,ST=Singapore,L=Singapore,O=org1.example.com \ -m peer0.org1.example.com \ -u http://peer0.org1.example.com:mysecret@localhost:7054 mkdir -p $PEER_DIR/msp/admincerts && \ cp $ADMIN_DIR/msp/signcerts/*.pem $PEER_DIR/msp/admincerts/
Now let's look at one of these certificates, such as peer0.org1.example.com:
openssl x509 -in $PEER_DIR/msp/signcerts/cert.pem -text -noout
The issuer of the certificate should be ica.org1.example.com:
Issuer: C=SG, ST=Singapore, O=org1.example.com, CN=ica.org1.example.com
Validity
Not Before: May 3 10:27:59 2019 GMT
Not After : May 2 10:28:00 2020 GMT
Subject: C=SG, ST=Singapore, L=Singapore, O=org1.example.com, OU=peer, OU=org1, CN=peer0.org1.example.com
Congratulations!We have completed the integration of third party CA and Fabric CA!
Original Link: Tutorials and Source Code for Using Third Party CA s in Hyperledger Fabric-Wizard

