Linux firewall system mainly works in the network layer. It belongs to the typical packet filtering firewall for real-time filtering and restriction of TCP/IP packets.
How does the Linux firewall check data traffic?
For the data packet entering the system, the first check is its source address:
If the source address is associated with a specific area, the rules formulated by that area are implemented.
If the source address is not associated with a particular area, the area passed into the network interface is used and the rules established by that area are enforced.
If the network interface is not associated with a specific area, the default area is used and the rules formulated by that area are enforced.
The default area is not a separate area, but points to some other area defined on the system. By default, the default area is public, but you can also change the default area. The above matching rules, according to the sequence, the first matching rules win, and network equipment ACL matching rules are similar, commonly known as matching stop.
The relevant predefined areas of firewalld:
firewalld firewall has two configurations:
1. Runtime mode: The firewall configuration running in current memory will fail when the system or firewalld service restarts or stops.
2. Permanent mode: The rule configuration when restarting or reloading the firewall is permanently stored in the configuration file.
The firewall-cmd command tool has three options related to configuration mode:
Reload: reload firewall rules and keep status information, i.e. permanent configuration application is run-time configuration;
Permanent: Commands with this option are used to set permanent rules that will only take effect if the firewall rules are restarted or reloaded; if not, they are used to set runtime rules.
runtime-to-permanent: Write the current runtime configuration into the rule configuration file so that the current rules in memory are called permanent configuration.
1. Firewall-related commands are used:
[root@localhost ~]# systemctl start firewalld #Start Firewall [root@localhost ~]# systemctl enable firewalld #Set up boot-up self-startup [root@localhost /]# firewall-cmd --reload #Heavy-duty firewall [root@localhost ~]# systemctl status firewalld #View firewall status [root@localhost ~]# systemctl stop firewalld #Stop Firewall [root@localhost ~]# systemctl disable firewalld #Setting Firewall Boot-up Not Self-Start [root@localhost ~]# firewall-cmd --get-zones #Display predefined areas block dmz drop external home internal public trusted work [root@localhost ~]# firewall-cmd --get-service #Display predefined services [root@localhost /]# firewall-cmd --list-all --zone=dmz #View the configuration of the specified area dmz target: default icmp-block-inversion: no interfaces: sources: services: ssh ports: protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules: [root@localhost ~]# firewall-cmd --get-icmptypes #Display predefined ICMP types address-unreachable bad-header communication-prohibited destination-unreachable echo-reply echo-request fragmentation-needed host-precedence-violation host-prohibited host-redirect host-unknown host-unreachable ip-header-bad neighbour-advertisement neighbour-solicitation network-prohibited network-redirect network-unknown network-unreachable no-route packet-too-big parameter-problem port-unreachable precedence-cutoff protocol-unreachable redirect required-option-missing router-advertisement router-solicitation source-quench source-route-failed time-exceeded timestamp-reply timestamp-request tos-host-redirect tos-host-unreachable tos-network-redirect tos-network-unreachable ttl-zero-during-reassembly ttl-zero-during-transit unknown-header-type unknown-option
** firewall-cmd -- The meaning of some blocking types in the result of get-icmptypes command execution is as follows:
**
destination-unreachable: destination address is unreachable; echo-reply: response; parameter-problem: parameter problem; Redirect: redirect; router-advertisement: Router notification; router-solicitation: Router search; source-quench: source-side inhibition; time-exceeded: timeout; timestamp-reply: timestamp response; timestamp-request: timestamp request;
2. Firewall Area Management Commands and Examples:
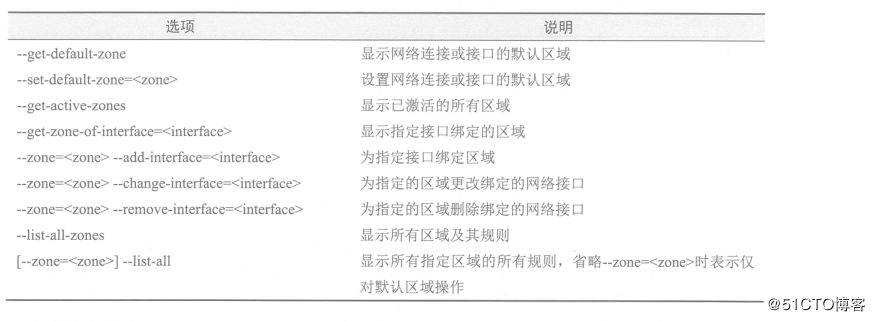
[root@localhost /]# firewall-cmd --set-default-zone=dmz #Set the default area to DMZ area [root@localhost ~]# firewall-cmd --get-default-zone #Display default areas in the current system [root@localhost ~]# firewall-cmd --list-all #Display all rules for default regions [root@localhost ~]# firewall-cmd --get-zone-of-interface=ens33 #Display the corresponding area of network interface ens33 [root@localhost ~]# firewall-cmd --get-active-zones #Display all active regions internal interfaces: ens33 #Perform the following actions to change the corresponding area of network interface ens33 to the internal area and view: [root@localhost ~]# firewall-cmd --zone=internal --change-interface=ens33 The interface is under control of NetworkManager, setting zone to 'internal'. success [root@localhost ~]# firewall-cmd --zone=internal --list-interfaces #View the list of interfaces in the internal area ens33 [root@localhost ~]# firewall-cmd --get-zone-of-interface=ens33 #View the area corresponding to interface ens33 internal
3. Commands and examples related to firewall service management:
Some examples of service management:
Set up services that are accessible for the default locale
[root@localhost services]# firewall-cmd --list-services #Displays all services allowed to be accessed in the default area ssh dhcpv6-client [root@localhost services]# firewall-cmd --add-service=http #Setting default zones to allow access to http services success [root@localhost services]# firewall-cmd --add-service=https #Setting default zones to allow access to https services success [root@localhost services]# firewall-cmd --list-services #Displays all services allowed to be accessed in the default area ssh dhcpv6-client http https
Set up accessible services for the internal region:
[root@localhost services]# firewall-cmd --zone=internal --add-service=mysql #Setting up the internal area to allow access to mysql services success [root@localhost services]# firewall-cmd --zone=internal --remove-service=samba-client #Setting up the internal area does not allow access to the Samba-client service success [root@localhost services]# firewall-cmd --zone=internal --list-services #Display all services that are allowed to be accessed in the internal area ssh mdns dhcpv6-client mysql
Port management:
When configuring a service, the predefined network service can be configured using the service name, and the ports involved in the service will be opened automatically. However, for non-predefined services, ports can only be manually added to the specified area. Examples are as follows:
[root@localhost services]# firewall-cmd --zone=internal --add-port=443/tcp #Open 443/tcp port in internal area success [root@localhost services]# firewall-cmd --zone=internal --remove-port=443/tcp #Prohibit 443/tcp port access in the internal area success
The above configurations are all temporary configurations. To save the current configuration as a permanent configuration, you can use the following commands:
[root@localhost services]# firewall-cmd --runtime-to-permanent success
Direct configuration of permanent rules with the permanent option is as follows:
[root@localhost /]# firewall-cmd --add-icmp-block=echo-request --permanent #Prohibit ping success [root@localhost /]# firewall-cmd --zone=external --add-icmp-block=echo-request --permanent #Configure external zone to ban ping success