0x01 Preface
This paper introduces the environment preparation for firmware analysis, mainly for the Firmadyne tool environment, and finally build the router firmware using Netgear for testing.
Firmadyne is an open source software that automates the security analysis of embedded Linux systems, developed by Daming D. Chen of Carnegie Mellon University.It supports batch detection, including crawling of firmware, extraction of root file system, QEMU simulation execution, and vulnerability mining.
Experimental environment and required tools:
- System: Ubuntu 14.04
- There were strange problems with the latest Kali version and Ubuntu 16.04LTS, and the author was later found in issue in Ubuntu 14.04
- Download: http://mirrors.ustc.edu.cn/ubuntu-releases/14.04/
- Tools:
- Firmadyne
- Project address: https://github.com/firmadyne/firmadyne
- Detailed configuration and installation steps in README.md
-
Firmware Analysis Toolkit
- Project address: https://github.com/attify/firmware-analysis-toolkit
- This toolset contains the necessary tools such as binwalk, Firmadyne, and so on.Here we just need to clone the repository locally
-
qemu
- You can install it directly with apt-get, only partially
- You can also compile and install all modules from github's repository
- Firmadyne
0x02 Environment Configuration
2.1 Cloning the Firmware Analysis Toolkit toolset repository
# 1. Installation Dependency sudo apt-get install busybox-static fakeroot git dmsetup kpartx netcat-openbsd nmap python-psycopg2 python3-psycopg2 snmp uml-utilities util-linux vlan # 2. clone git clone --recursive https://github.com/attify/firmware-analysis-toolkit.git
2.2 Install binwalk
# 1. Installation dependencies and binwalk cd firmware-analysis-toolkit/binwalk sudo ./deps.sh sudo python setup.py install # 2. For python2.x, you also need to install the following Libraries sudo -H pip install git+https://github.com/ahupp/python-magic sudo -H pip install git+https://github.com/sviehb/jefferson
Test for successful installation:
hzy@ubuntu:~$ binwalk Binwalk v2.1.2-c036535 Craig Heffner, ReFirmLabs https://github.com/ReFirmLabs/binwalk Usage: binwalk [OPTIONS] [FILE1] [FILE2] [FILE3] ... Disassembly Scan Options: -Y, --disasm Identify the CPU architecture of a file using the capstone disassembler ... ... -s, --status=<int> Enable the status server on the specified port hzy@ubuntu:~$
2.3 Install Firmadyne
- Enter the Firmadyne directory, then open firmadyne.config, modify the FIRMWARE_DIR path to the absolute path of the current Firmadyne directory
cd firmware-analysis-toolkit/firmadyne vim firmadyne.config # Here's what's in firmadyne.config #!/bin/sh # uncomment and specify full path to FIRMADYNE repository FIRMWARE_DIR=/home/hzy/firmware-analysis-toolkit/firmadyne/ # specify full paths to other directories BINARY_DIR=${FIRMWARE_DIR}/binaries/ TARBALL_DIR=${FIRMWARE_DIR}/images/ SCRATCH_DIR=${FIRMWARE_DIR}/scratch/ SCRIPT_DIR=${FIRMWARE_DIR}/scripts/ # functions to safely compute other paths ... ...
- Install Firmadyne
sh ./download.sh
2.4 Install the postgresql database
sudo apt-get install postgresql # The user's password is set to firmadyne sudo -u postgres createuser -P firmadyne, with password firmadyne sudo -u postgres createdb -O firmadyne firmware # Note that the database file is in the firmadyne/directory, that is, the command is executed in the root firmware-analysis-toolkit/directory sudo -u postgres psql -d firmware < ./firmadyne/database/schema
Start the postgresql database to confirm that it is running.
- Here, during the kali test, if the database is not started first, the command to add users will fail.
- I also encountered a problem, clearly the database service is running, but the error that I always reported when adding users is also the error that the service is not running. In this case, I directly reinstalled postgresql
- Specific errors you can search for solutions online.Generally, there are ready-made methods.
sudo service postgresql start sudo service postgresql status
2.5 Install qemu
QEMU is an analog processor written by Fabrice Bellard that distributes source code under a GPL license and is widely used on GNU/Linux platforms.
There are two ways to install:
- Install directly from apt-get
sudo apt-get install qemu-system-arm qemu-system-mips qemu-system-x86 qemu-utils
- Compile Installation
git clone git://git.qemu.org/qemu.git cd qemu git submodule init git submodule update --recursivesudo apt install libglib2.0 libglib2.0-devsudo apt install autoconf automake libtoolcd qemu && ./configuremakesudo make install
0x03 Test Run
- Move fat.py and reset.py from firmware-analysis-toolkit/directory to firmadyne/directory:
mv fat.py ./firmadyne mv reset.py ./firmadyne
- Modify the execute permissions in fat.py, firmadyne's path firmadyne_path, and root_pass password
chmod +x fat.py vim fat.py # Here's what's in fat.py #!/usr/bin/env python2.7 import os import pexpect import sys # Put this script in the firmadyne path downloadable from # https://github.com/firmadyne/firmadyne #Configurations - change this according to your system firmadyne_path = "/home/hzy/firmware-analysis-toolkit/firmadyne" binwalk_path = "/usr/local/bin/binwalk" root_pass = "123456" firmadyne_pass = "firmadyne" ... ...
- Download router firmware to emulate
-
The router to be simulated is: WNAP320
-
Download the firmware file at https://www.netgear.com/support/product/WNAP320.aspx#Firmware%20Version%203.7.11.4
-
Suppose I rename the firmware file netgear.zip here and place it in the / home/hzy/firmware/directory
- test run
hzy@ubuntu:~/firmware-analysis-toolkit/firmadyne$ sudo ./fat.py [sudo] password for hzy: __ _ / _| | | | |_ __ _ | |_ | _| / _` | | __| | | | (_| | | |_ |_| \__,_| \__| Welcome to the Firmware Analysis Toolkit - v0.2 Offensive IoT Exploitation Training - http://offensiveiotexploitation.com By Attify - https://attify.com | @attifyme [?] Enter the name or absolute path of the firmware you want to analyse : /home/hzy/firmware/netgear.zip [?] Enter the brand of the firmware : Netgear [+] Now going to extract the firmware. Hold on.. [+] Firmware : /home/hzy/firmware/netgear.zip [+] Brand : Netgear [+] Database image ID : 2 [+] Identifying architecture [+] Architecture : mipseb [+] Storing filesystem in database [!] Filesystem already exists [+] Building QEMU disk image [+] Setting up the network connection, please standby [+] Network interfaces : [('brtrunk', '192.168.0.100')] [+] Running the firmware finally [+] command line : sudo /home/hzy/firmware-analysis-toolkit/firmadyne/scratch/2/run.sh [*] Press ENTER to run the firmware...
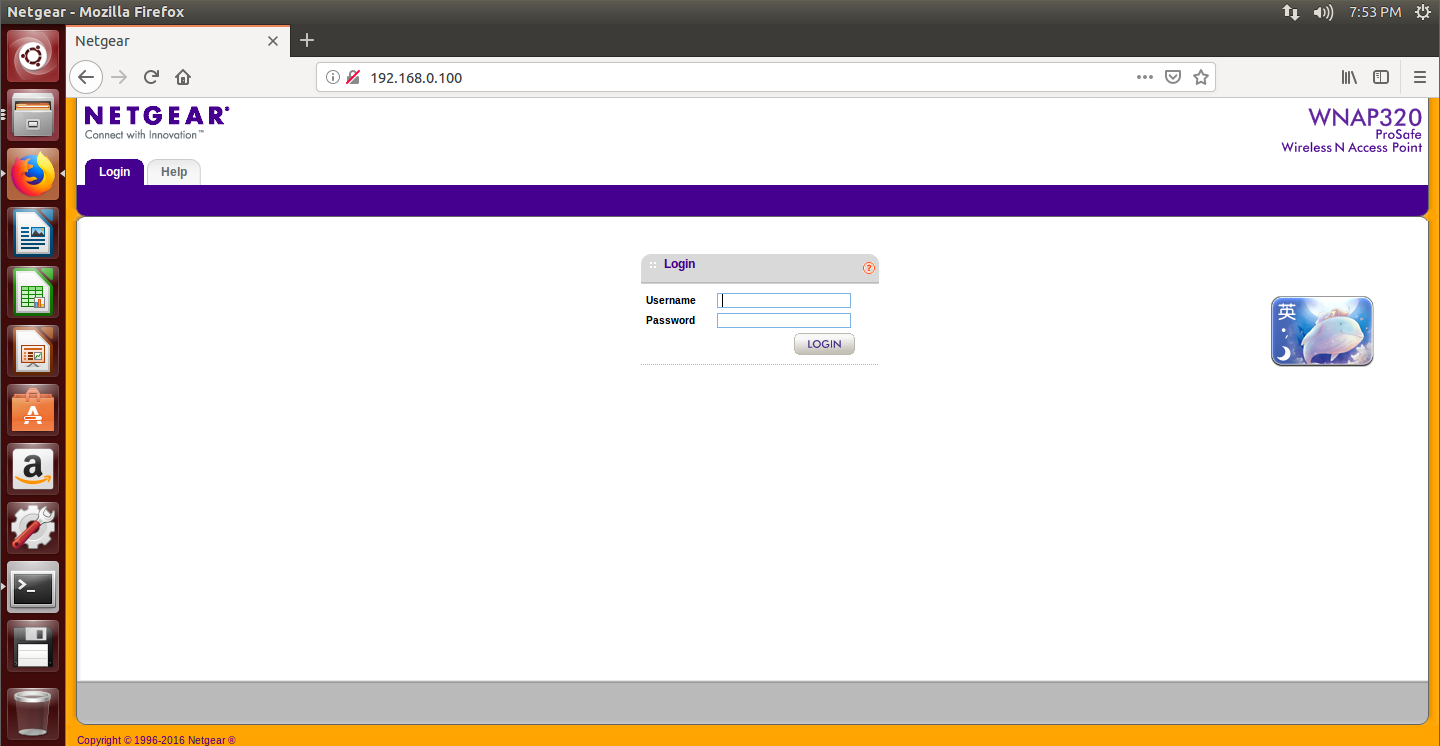
As you can see from [+] Network interfaces: [('brtrunk','192.168.0.100')], a service is started and is accessible through 192.168.0.100
Next, press Enter to run the firmware, and then you can access it from your browser:
Summary of 0x04
Reference 1 is the main reference, but there are many holes in the middle, you can refer to Reference 3.
There are other uses for this firmadyne, which can be found in Reference 2.This article is over.
To install this analysis environment, three virtual machines are tossed around.Installing software and matching environment is my lifetime enemy!!(Qi_Qi)
By:hzy