preface
frp is an open source project, which can be used as a high-performance reverse proxy application for intranet penetration. It supports TCP and UDP protocols, provides additional capabilities for http and https application protocols, and tentatively supports point-to-point penetration.
frp can expose the internal network host to the Internet through the server with public network IP, so as to directly access the internal network host through the external network; frp has a server and a client. The server needs to be installed on the server with public IP, and the client needs to be installed on the intranet host.
prepare
- Public network server or public network IP (I use centos7 of Tencent cloud)
- Intranet computer (I use win10)
- Download frp at: https://github.com/fatedier/frp/releases (the client and server versions must be the same. I use v0.38.0 here)
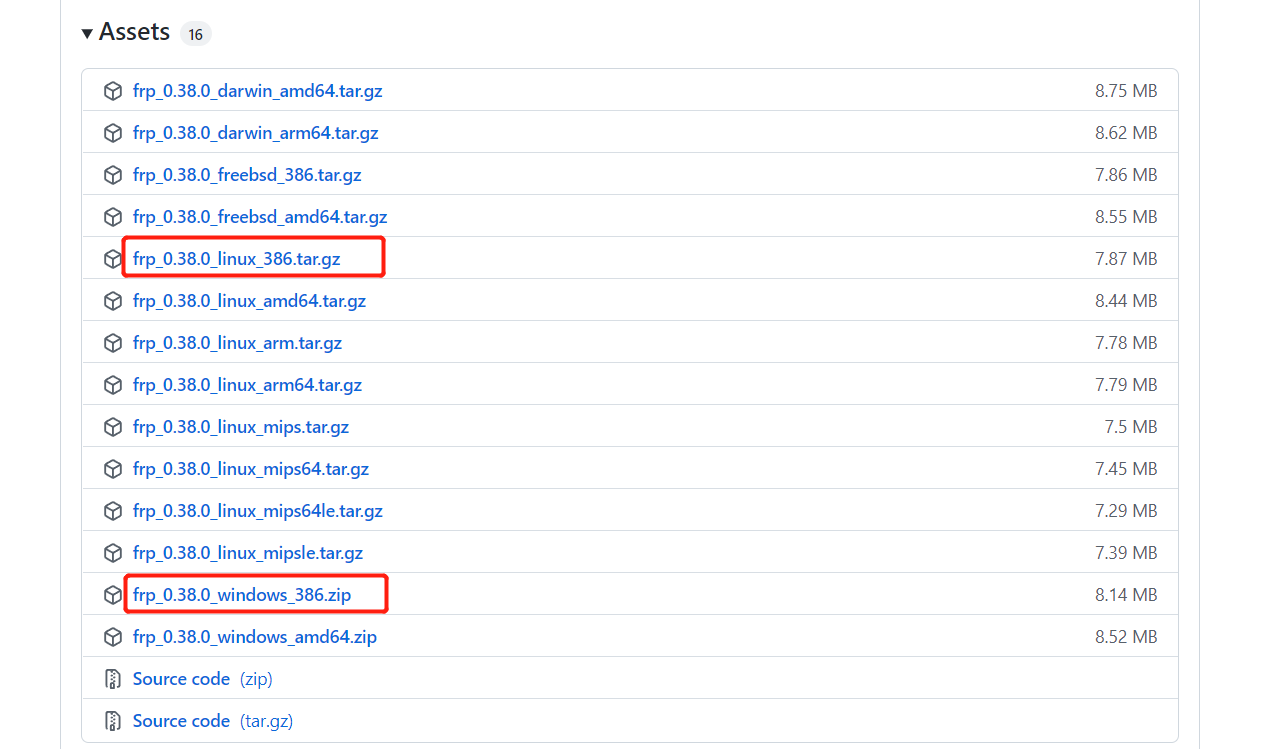
Because my server uses linux and my client uses windows. Therefore, two packages need to be downloaded:
explain
The client files are FRPC (execution file), FRPC Ini (configuration file)
The server files are FRPs (execution file) and FRPs Ini (configuration file)
In fact, c is the client and S is the server. It's good to divide and remember
configure server
- Install package frp_0.38.0_linux_386.tar.gz to server
- To the directory of the installation package:
tar -zxvf frp_0.38.0_linux_386.tar.gz cd frp_0.38.0_linux_386 mv frp_0.38.0_linux_386 /usr/local/frp
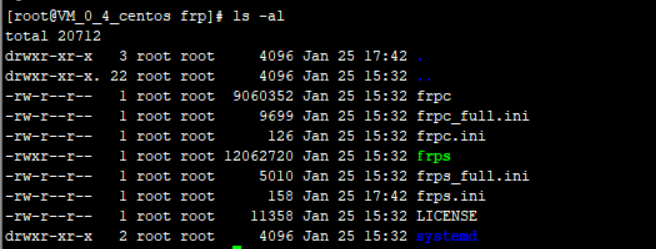
3. Modify the configuration file of the server
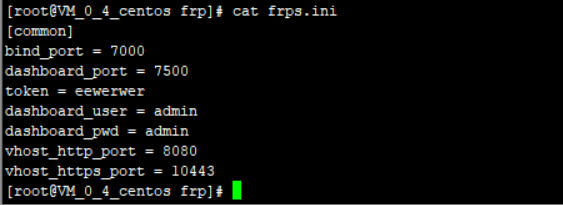
The following values can be customized, but pay attention to whether they conflict with the ports of other services
bind_port = 7000 #Binding port is the port when the client connects to the server token = eewerwer #token is the authentication when the client connects to the server dashboard_port = 7500 #Port to access the server end panel dashboard_user = admin #Account for accessing the service end panel dashboard_pwd = admin #Password to access the server side panel vhost_http_port = 8080 http Penetration port vhost_https_port = 10443 https Penetration port
After configuration, you can start:
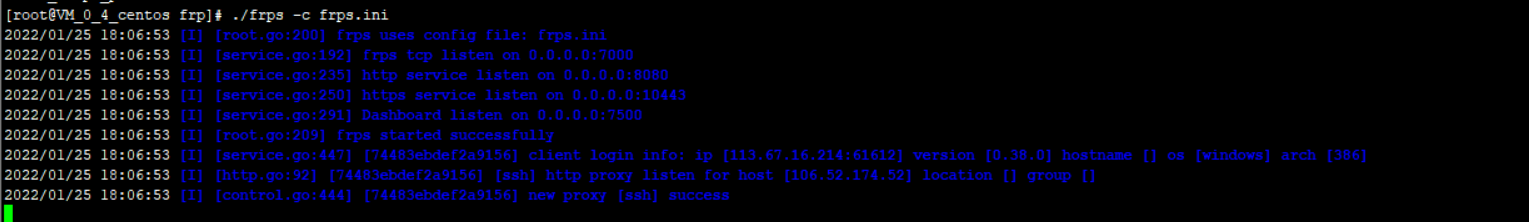
Access the service end panel and input the ip port of the public network; The port here is the configuration file dashboard_port value (I have logged in)
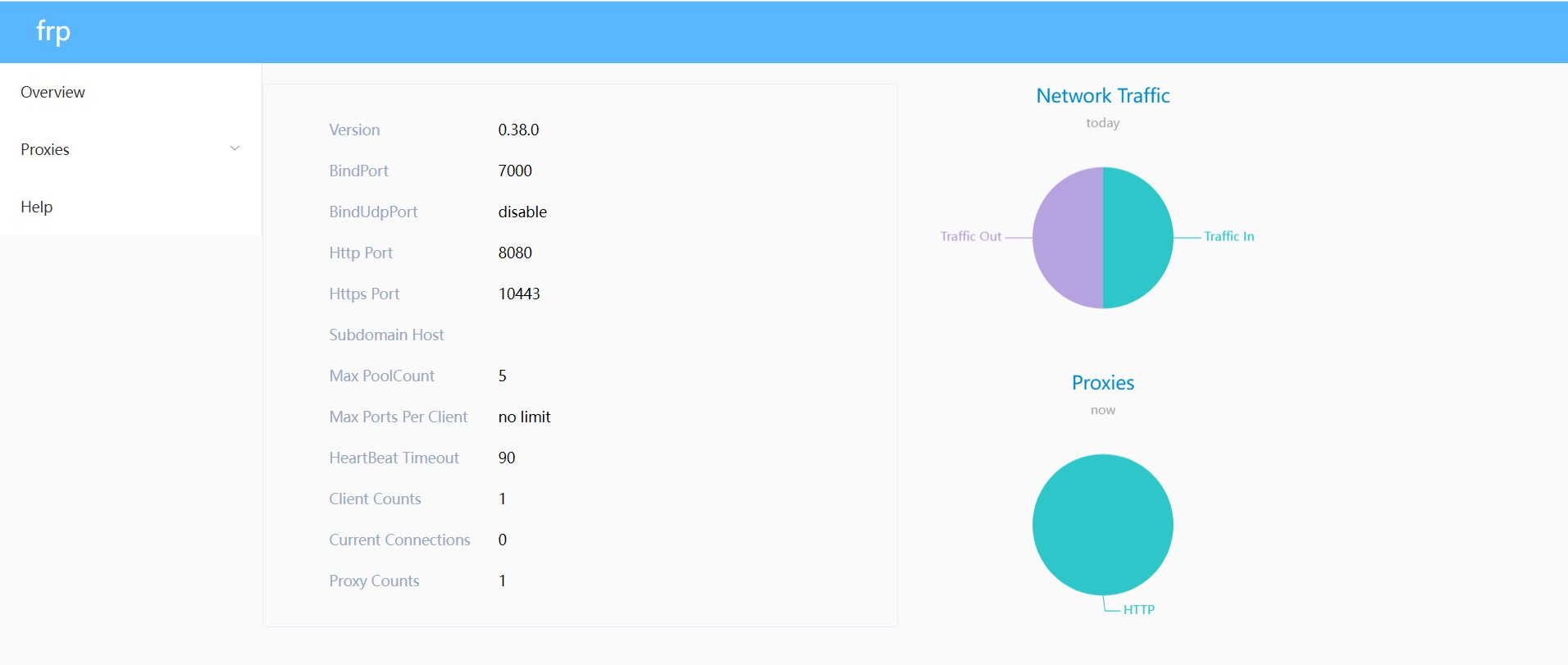
So far, the server has been configured
Configure client
- Install package FRP_ 0.38.0_ windows_ Unzip 386.zip and enter the directory
- Configuration profile
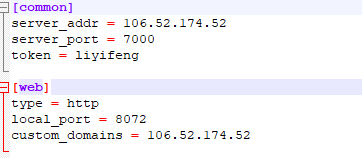
[common] server_addr = 106.5X.XX.XXX #This is the ip address of the public network server server_port = 7000 #This is the server configuration file bind_ Value of port token = eewerwer #token of the corresponding server [web] #Agent name, optional type = http #The protocol type is http, and tcp,udp, etc. can also be configured local_port = 8072 #The local port of the agent is the port when you access the local project custom_domains = 106.5X.XX.XXX #The public network can also be a domain name
Start client
Access method
Using custom_ The address or domain name specified by domains, and the port is Vhost of the server_ http_ The port specified by port is 8080 here. After accessing, it is equivalent to accessing the local port 8072
Here is: XXX xxx. xxx. xxx:8080
The agency method is equivalent to: XXX xxx. xxx. xxx:8080 --> 127.0.0.1:8072
Establish multiple reverse proxies
The server and client here are one-to-one, so you need to re-establish the server and specify different frp ports and http ports
Trample pit
At the beginning of the visit, the web page returns ERR_UNSAFE_PORT
The reason is that some ports are configured, such as Vhost at the beginning_ http_ Port = 10080, when accessing, the browser will recognize it as an insecure port and cannot access it; For example, some of the following ports:
1, // tcpmux 7, // echo 9, // discard 11, // systat 13, // daytime 15, // netstat 17, // qotd 19, // chargen 20, // ftp data 21, // ftp access 22, // ssh 23, // telnet 25, // smtp 37, // time 42, // name 43, // nicname 53, // domain 77, // priv-rjs 79, // finger 87, // ttylink 95, // supdup 101, // hostriame 102, // iso-tsap 103, // gppitnp 104, // acr-nema 109, // pop2 110, // pop3 111, // sunrpc 113, // auth 115, // sftp 117, // uucp-path 119, // nntp 123, // NTP 135, // loc-srv /epmap 139, // netbios 143, // imap2 179, // BGP 389, // ldap 465, // smtp+ssl 512, // print / exec 513, // login 514, // shell 515, // printer 526, // tempo 530, // courier 531, // chat 532, // netnews 540, // uucp 556, // remotefs 563, // nntp+ssl 587, // stmp? 601, // ?? 636, // ldap+ssl 993, // ldap+ssl 995, // pop3+ssl 2049, // nfs 3659, // apple-sasl / PasswordServer 4045, // lockd 6000, // X11 6665, // Alternate IRC [Apple addition] 6666, // Alternate IRC [Apple addition] 6667, // Standard IRC [Apple addition] 6668, // Alternate IRC [Apple addition] 6669, // Alternate IRC [Apple addition]