Previously, I shared the Harbor series articles in my column Harbor dictionary.
In this issue, we will continue to share how to pull private images in Harbor in k8s's container.
We can pull public images in Harbor at will, but some private images cannot be pulled directly. We can use the Secret resource object to pull private images. The following are the detailed steps.
Harbor Address: https://192.168.2.250:443
Harbor user: admin
Harbor password: Harbor 12345
At the end of the paper, record the problems encountered and solutions!
1. Log in to Harbor
After successful login, it will be displayed in ~ / docker/config. The login information is recorded in the JSON file, and then a Secret is created based on the information. The container specifies the Secret through imagePullSecret to realize authentication, so as to pull the private image.
If you fail to log in to Harbor, please check the problem solving column.
# docker login -u admin -p Harbor12345 192.168.2.250:443
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded //Login succeeded
# cat ~/.docker/config.json
{
"auths": {
"192.168.2.250:443": {
"auth": "YWRtaW46SGFyYm9yMTIzNDU="
}
},
"HttpHeaders": {
"User-Agent": "Docker-Client/19.03.8 (linux)"
}
}2. Parsing key data with BASH64 encoding
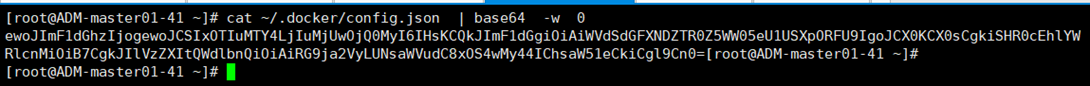
Next, you need to use the parsed results when creating a Secret- w 0 means that the generated Secret key will not be converted to a line. If the default conversion is not in the correct format, an error will occur.
# cat ~/.docker/config.json | base64 -w 0 ewoJImF1dGhzIjogewoJCSIxOTIuMTY4LjIuMjUwOjQ0MyI6IHsKCQkJImF1dGgiOiAiWVdSdGFXNDZTR0Z5WW05eU1USXpORFU9IgoJCX0KCX0sCgkiSHR0cEhlYWRlcnMiOiB7CgkJIlVzZXItQWdlbnQiOiAiRG9ja2VyLUNsaWVudC8xOS4wMy44IChsaW51eCkiCgl9Cn0=
3. Create Secret image pull voucher
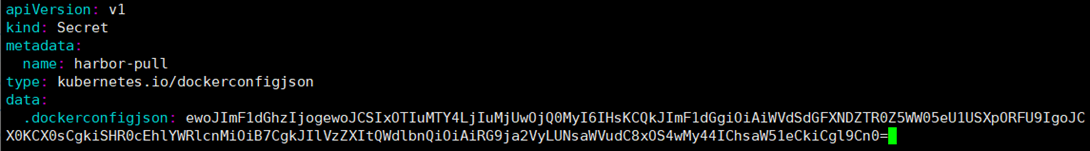
. The value of dockerconfigjson is the result of the parsing in step 2 (copy the result there)
# vim harbor-image-secret.yaml apiVersion: v1 kind: Secret metadata: name: harbor-pull type: kubernetes.io/dockerconfigjson data: .dockerconfigjson: ewoJImF1dGhzIjogewoJCSIxOTIuMTY4LjIuMjUwOjQ0MyI6IHsKCQkJImF1dGgiOiAiWVdSdGFXNDZTR0Z5WW05eU1USXpORFU9IgoJCX0KCX0sCgkiSHR0cEhlYWRlcnMiOiB7CgkJIlVzZXItQWdlbnQiOiAiRG9ja2VyLUNsaWVudC8xOS4wMy44IChsaW51eCkiCgl9Cn0= # kubectl apply -f harbor-image-secret.yaml secret/harbor-pull created # kubectl get secret NAME TYPE DATA AGE default-token-qqjxn kubernetes.io/service-account-token 3 13d harbor-pull kubernetes.io/dockerconfigjson 1 52s
For the method of creating secret on the command line, see kubectl create secret -h, which will not be described in detail here.
4. The private image is pulled by using the image pull Certificate in the container
Take the private image 192.168.2.250:443/muli/tomcat:8.5.34-jre8-alpine as an example.
# cat tomcat-pod1.yaml
kind: Pod
apiVersion: v1
metadata:
name: tomcat-v2.3.1
namespace: test
spec:
imagePullSecrets:
- name: image-secret
containers:
- name: tomcat-po
image: 192.168.2.250:443/muli/tomcat:8.5.34-jre8-alpine
imagePullPolicy: IfNotPresent
# kubectl apply -f tomcat-pod1.yaml
pod/tomcat-v2.3.1 created
# kubectl get pods
NAME READY STATUS RESTARTS AGE
tomcat-v2.3.1 1/1 Running 0 20h
5. Problems encountered
After the Pod is created, the image always fails to be pulled.
Troubleshooting:
Because the operation is performed on the master, the Pod is scheduled to the node node, but the node node has not logged in to Harbor, so the node node does not have ~ / docker/config.json file, so that the node node cannot obtain the login information when pulling the image.
terms of settlement:
To the node to which the Pod is scheduled:
# docker login -u admin -p Harbor12345 192.168.2.250:443 WARNING! Using --password via the CLI is insecure. Use --password-stdin. WARNING! Your password will be stored unencrypted in /root/.docker/config.json. Configure a credential helper to remove this warning. See https://docs.docker.com/engine/reference/commandline/login/#credentials-store Login Succeeded //Login succeeded
~ /. Will be generated automatically docker/config.json file, whose content is consistent with that generated by master.
In the production environment, the node to which the Pod will be scheduled is not known in advance, and the login operation can be performed on each node.