
About Forbidden
Forbidden is a network security tool based on PycURL, which can help researchers easily bypass 4xx HTTP response status code.
Forbidden uses multithreading mechanism and implements its function based on brute force cracking, so the tool may have some false positives. In addition, the script also supports color highlight output.
The tool processing results can be arranged in ascending order of HTTP response status code, descending order of content length and ascending order of ID.
If you need to filter false positives, manually check the length of each content using the cURL command provided by the project. If the processing result indicates that 4xx HTTP response status code bypass is not implemented, you only need to directly ignore all other results with the same content length.
Note: the tool is currently available in Kali Linux V2021 4 (64 bit) platform has been tested.
Tool download
Researchers can use the following commands to clone the source code of the project locally:
git clone https://github.com/ivan-sincek/forbidden.git
Tool running
Open the familiar terminal window, switch to the / src / directory of the project, and then run the following related commands.
Dependent tools required for installation:
apt-get install -y curl
Code packages required for installation:
pip3 install -r requirements.txt
Run the tool script:
python3 forbidden.py
Note: considering the access frequency limit, if you only want to test for the same domain name and expect better results, please give more time interval when running the script.
Some websites may need to set up a user agent Header. You can download a list of user agents.
Automatic use of tools
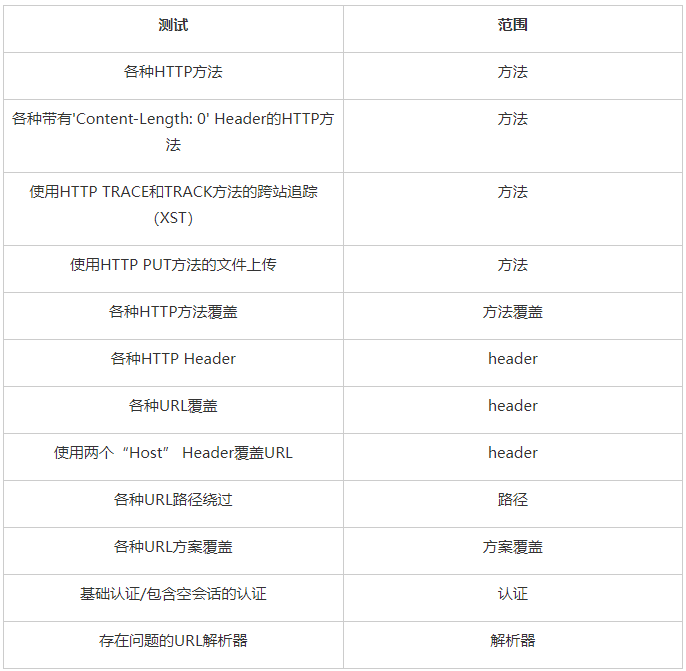
Bypass "403 Forbidden" HTTP response status code:
count=0; for subdomain in $(cat subdomains_403.txt); do count=$((count+1)); echo "#${count} | ${subdomain}"; python3 forbidden.py -u "${subdomain}" -t method,method-override,header,path,scheme-override -f GET -o "forbidden_403_results_${count}.json"; doneBypass "401 Unauthorized" HTTP response status code:
count=0; for subdomain in $(cat subdomains_401.txt); do count=$((count+1)); echo "#${count} | ${subdomain}"; python3 forbidden.py -u "${subdomain}" -t auth -f GET -o "forbidden_401_results_${count}.json"; doneCheck the problematic URL parser:
count=0; for subdomain in $(cat subdomains_live_long.txt); do count=$((count+1)); echo "#${count} | ${subdomain}"; python3 forbidden.py -u "${subdomain}" -t parser -f GET -o "forbidden_parser_results_${count}.json"; doneSupported HTTP methods
ACL ARBITRARY BASELINE-CONTROL BIND CHECKIN CHECKOUT CONNECT COPY DELETE GET HEAD INDEX LABEL LINK LOCK MERGE MKACTIVITY MKCALENDAR MKCOL MKREDIRECTREF MKWORKSPACE MOVE OPTIONS ORDERPATCH PATCH POST PRI PROPFIND PROPPATCH PUT REBIND REPORT SEARCH SHOWMETHOD SPACEJUMP TEXTSEARCH TRACE TRACK UNBIND UNCHECKOUT UNLINK UNLOCK UPDATE UPDATEREDIRECTREF VERSION-CONTROL
Supported HTTP headers
Overwrite HTTP Header:
X-HTTP-Method X-HTTP-Method-Override X-Method-Override
HTTP Header:
Client-IP Cluster-Client-IP Connection Contact Forwarded Forwarded-For Forwarded-For-Ip From Host Origin Referer Stuff True-Client-IP X-Client-IP X-Custom-IP-Authorization X-Forward X-Forwarded X-Forwarded-By X-Forwarded-For X-Forwarded-For-Original X-Forwarded-Host X-Forwarded-Server X-Forward-For X-Forwared-Host X-Host X-HTTP-Host-Override X-Original-URL X-Originating-IP X-Override-URL X-ProxyUser-IP X-Real-IP X-Remote-Addr X-Remote-IP X-Rewrite-URL X-Wap-Profile X-Server-IP X-Target
HTTP Header scheme coverage:
X-Forwarded-Proto X-Forwarded-Protocol X-Forwarded-Scheme X-Url-Scheme X-URLSCHEME
URL path
Inject before, after, and before and after the URL path with and without slashes:
/ // %09 %20 %2e . .. ; .; ..; ;foo=bar;
Inject at the end of the URL path:
~ ~~ ~~random * ** **random # ## ##random ? ?? ??random
Inject at the end of the URL path (if the URL path does not end with "/):
.php .jsp .jspa .jspx .jhtml .html .sht .shtml .xhtml .asp .aspx .esp
Processing result data sample
[
{
"id":501,
"url":"http://example.com:80/admin",
"method":"GET",
"headers":[
"Host: 127.0.0.1"
],
"agent":"Forbidden/5.4",
"proxy":null,
"data":null,
"command":"curl -m 5 --connect-timeout 5 -i -s -k -L --path-as-is -H 'Host: 127.0.0.1' -H 'User-Agent: Forbidden/5.4' -X 'GET' 'http://example.com:80/admin'",
"code":200,
"length":255408
},
{
"id":541,
"url":"http://example.com:80/admin",
"method":"GET",
"headers":[
"Host: 127.0.0.1:80"
],
"agent":"Forbidden/5.4",
"proxy":null,
"data":null,
"command":"curl -m 5 --connect-timeout 5 -i -s -k -L --path-as-is -H 'Host: 127.0.0.1:80' -H 'User-Agent: Forbidden/5.4' -X 'GET' 'http://example.com:80/admin'",
"code":200,
"length":255408
}
]Screenshot of tool operation
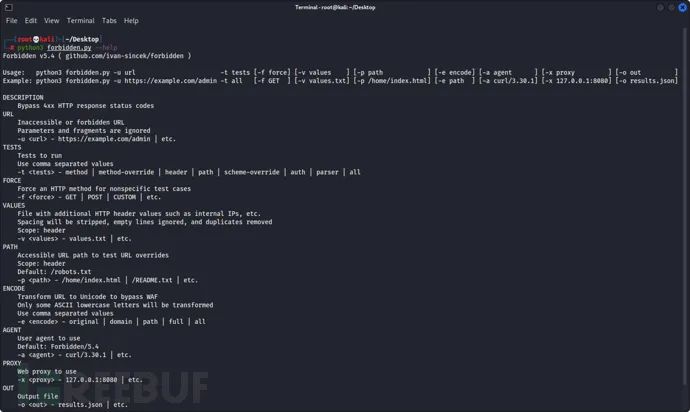
Project address
https://github.com/ivan-sincek/forbidden