1: HTTPS encryption certificate process
- brief introduction
- 1. The browser initiates a request to port 443 of the server, which carries the encryption algorithm and hash algorithm supported by the browser.
- 2. The server receives the request and selects the encryption algorithm and hash algorithm supported by the browser.
- 3. The server returns the digital certificate to the browser. The digital certificate here can be applied to a reliable institution or self-made.
4,The browser enters the digital certificate authentication link, which is built in the browser TLS Completed:
4.1 First, the browser will index from the built-in certificate list to find the organization corresponding to the certificate issued by the server. If it is not found, the user will be prompted whether the certificate is issued by an authoritative organization and is untrusted. If the corresponding organization is found, take out the public key issued by the organization.
4.2 Decrypt the certificate public key of the organization to obtain the content and signature of the certificate, including the website URL, the website public key, the validity period of the certificate, etc. The browser will first verify the validity of the certificate signature (the verification process is similar to the above) Bob and Susan Communication). After the signature is passed, the browser verifies whether the web address recorded in the certificate is consistent with the current web address. If it is inconsistent, the user will be prompted. If the web address is consistent, the validity of the certificate will be checked, and the user will be prompted if the certificate expires. When these are authenticated, the browser can safely use the website public key in the certificate.
4.3 The browser generates a random number R,And use the website public key pair R Encrypt.
- 5. The browser transmits the encrypted R to the server.
- 6. The server decrypts R with its own private key.
- 7. The server uses R as the key, uses the symmetric encryption algorithm to encrypt the web content and transmit it to the browser.
- 8. The browser takes R as the key and uses the previously agreed decryption algorithm to obtain the web content.
2: Certificate comparison
| contrast |
Domain name DV |
Enterprise OV |
Enhanced EV |
| Green address bar |
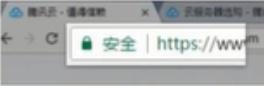 Small lock mark + https Small lock mark + https |
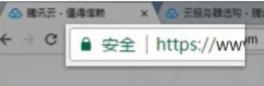 Small lock mark + https Small lock mark + https |
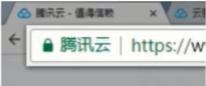 Small lock mark + enterprise name + https Small lock mark + enterprise name + https |
| General purpose |
Personal sites and applications; Simple https encryption requirements |
E-commerce sites and applications; SME site |
Large financial platform; Large enterprise and government agency sites |
| Audit content |
Domain name ownership verification |
Comprehensive enterprise authentication; Domain name ownership verification |
The highest level of enterprise authentication; Domain name ownership verification |
| Issuance duration |
10 minutes - 24 hours |
3-5 working days |
5-7 working days |
| Single application period |
1 year |
1-2 years |
1-2 years |
| Compensation guarantee fund |
- |
$1.25-1.75 million |
$1.5-1.75 million |
3: Self signed certificate
- Use the openssl command as the CA authority to create a certificate (the production does not use this method to generate a certificate, and the black door certificate is not recognized by the Internet)
1.(lb server load balancing agent)
1.Switch directory
cd /etc/nginx
2.Create certificate directory
mkdir ssl
3.Switch to certificate directory
cd ssl
2. (create CA certificate and password)
[root@lb01 ssl]# openssl genrsa -idea -out server.key 2048
Generating RSA private key, 2048 bit long modulus
...............................+++
........+++
e is 65537 (0x10001)
Enter pass phrase for server.key: 123456
Verifying - Enter pass phrase for server.key: 123456
[root@web01 ssl_key]# ll
total 4
-rw-r--r--. 1 root root 1739 Dec 9 11:27 server.key
3. Generate a self signed certificate (public key) and remove the password of the private key (Enter)
[root@web01 ssl_key]# openssl req -days 36500 -x509 -sha256 -nodes -newkey rsa:2048 -keyout server.key -out server.crt
Generating a 2048 bit RSA private key
.....................................+++
............+++
writing new private key to 'server.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:china
string is too long, it needs to be less than 2 bytes long
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:meiguo
Locality Name (eg, city) [Default City]:riben
Organization Name (eg, company) [Default Company Ltd]:heishoudang
Organizational Unit Name (eg, section) []:oldboy
Common Name (eg, your name or your server's hostname) []:oldboy
Email Address []:123@qq.com
4: Certificate content analysis description
# Req -- > used to create a new certificate
# New -- > indicates that a new certificate is created
# X509 -- > indicates that the format of the defined certificate is standard format
# Key -- > indicates the private key file information called
# Out -- > indicates the output certificate file information
# Days -- > indicates the validity period of the certificate
# Sha256 -- > encryption method
#1. Open certificate
Syntax: ssl on | off;
Default: ssl off;
Context: http, server
#2. Specify the certificate file
Syntax: ssl_certificate file;
Default: —
Context: http, server
#3. Specify the private key file
Syntax: ssl_certificate_key file;
Default: —
Context: http, server
5: Configure certificate URL module file
1.Switch path
cd /etc/nginx/conf.d
1. Prepare the website module configuration file
[root@lb01 ~]# vim /etc/nginx/conf.d/https.conf
server {
listen 443 ssl;
server_name _;
ssl_certificate /etc/nginx/ssl/server.crt;
ssl_certificate_key /etc/nginx/ssl/server.key;
location / {
proxy_pass http://ssl;
proxy_next_upstream error timeout invalid_header http_500 http_502 http_503 http_404;
include /etc/nginx/proxy_params;
}
location ~ \.(jpg|png|gif|js|css|woff|woff2|ttf)$ {
root /opt/static;
}
}
server {
listen 80;
server_name _;
rewrite (.*) https://192.168.15.5 permanent;
}
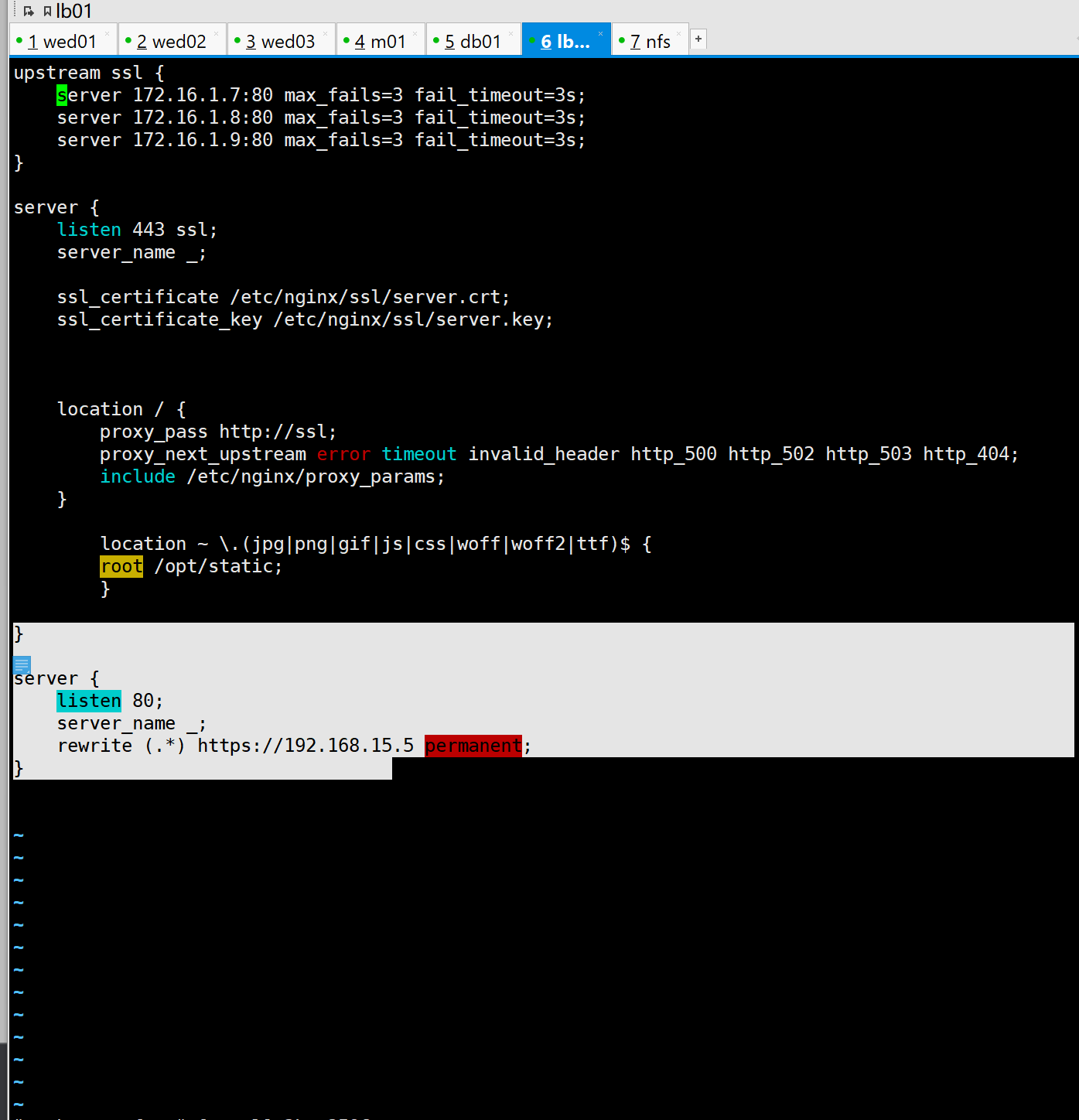
2. Website test
192.168.15.5
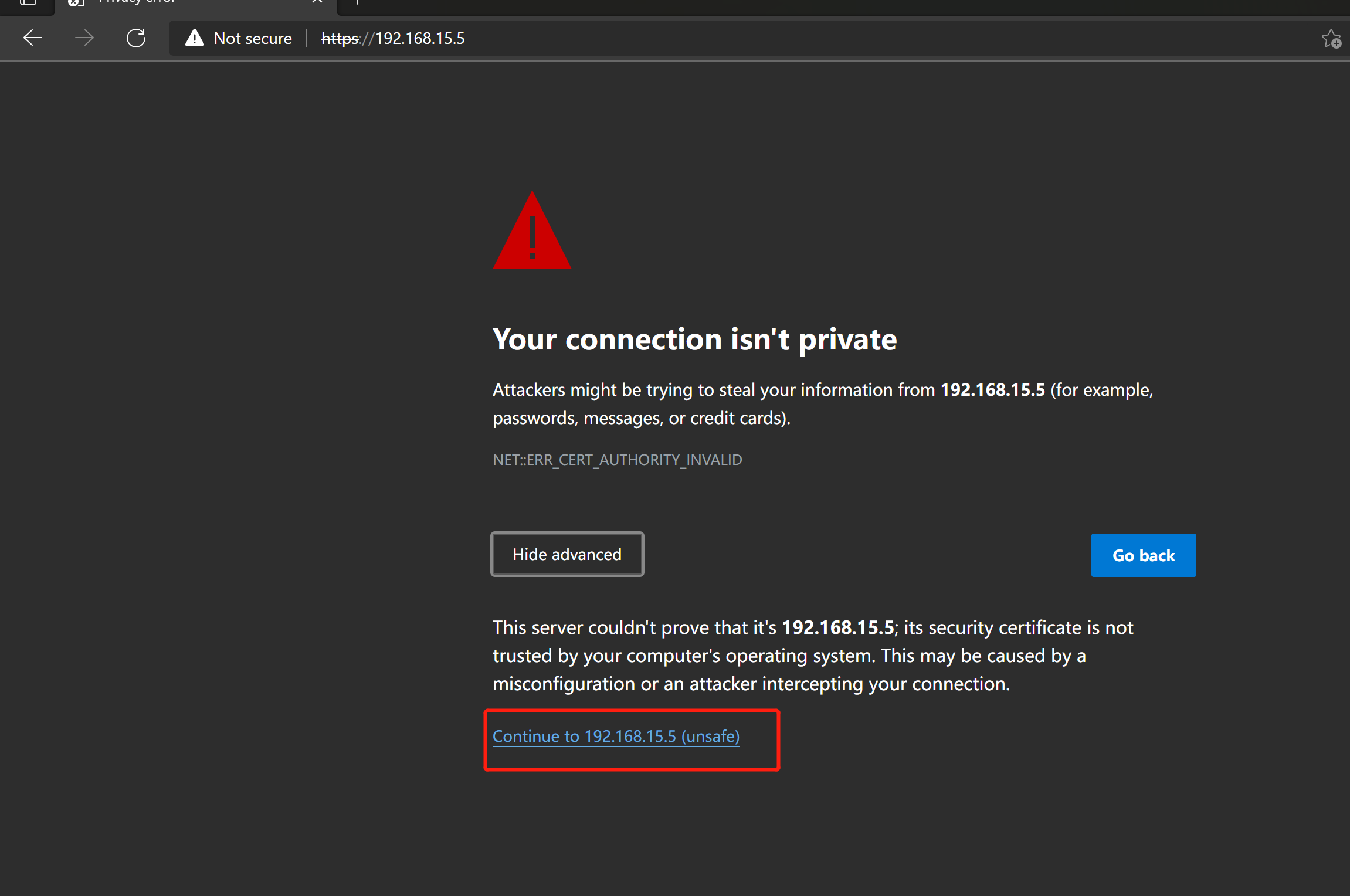
Test successful
Certificate created successfully
 Small lock mark + https
Small lock mark + https Small lock mark + https
Small lock mark + https Small lock mark + enterprise name + https
Small lock mark + enterprise name + https

