Hello, I'm Zhang Anzhong, a researcher of Microsoft MVP laboratory in this issue. Today, I will introduce you how to use ASP Net core and Java projects integrate Azure Key Vault functions.
Microsoft MVP lab researcher
Thinking analysis
In software development, project security is the top priority, especially in multi department or open source projects. How to save our keys without affecting local development is a problem that our developers need to consider. Here is a brief list of our solutions in normal development:
-
The local is directly developed in the form of localhost. Whether DB, ES/Redis/MQ, or others, they all use local parameters. When deploying to K8s, they are mounted in the form of Configmap. It is also a scheme, but it will make the isolation between dev and prod more severe
-
Use the remote configuration center to uniformly process local and production direct data. For example, Apollo, Azure's Key Vault technology and so on are common. Recommended way
-
Manually modify every time you go online. This is obviously unreasonable
PS: This paper adopts azure.com of 21vianet Cn.
Preliminary preparation account
First, you need to register an Azure account.
Secondly, you need to register an application. When registering, fill in the Client password. The password should be well saved and will be used many times in the future.
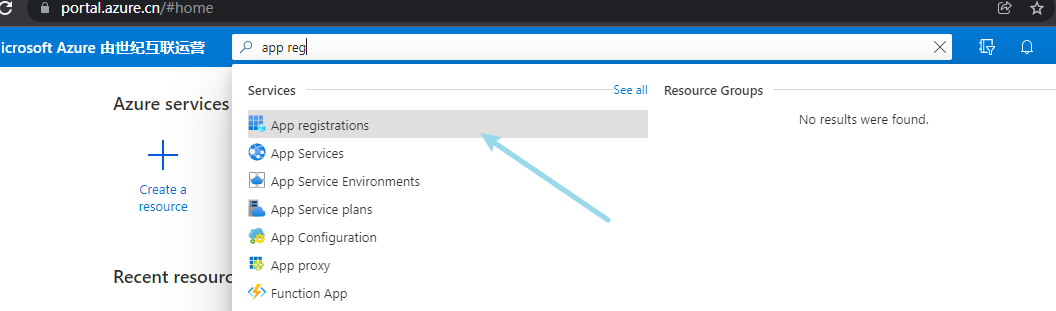
Search app registration and register an account:
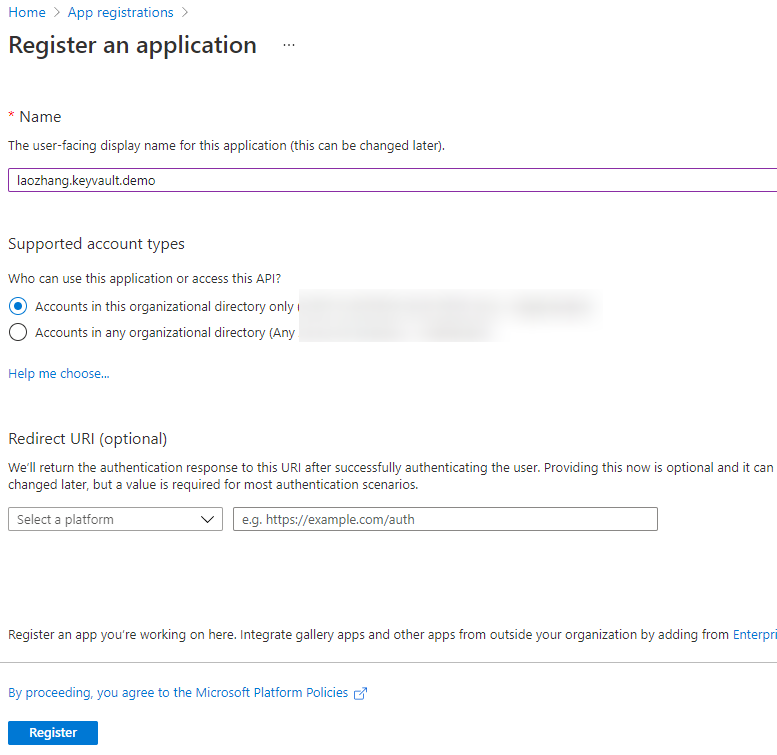
Enter the name of the application, and the others can be used by default:
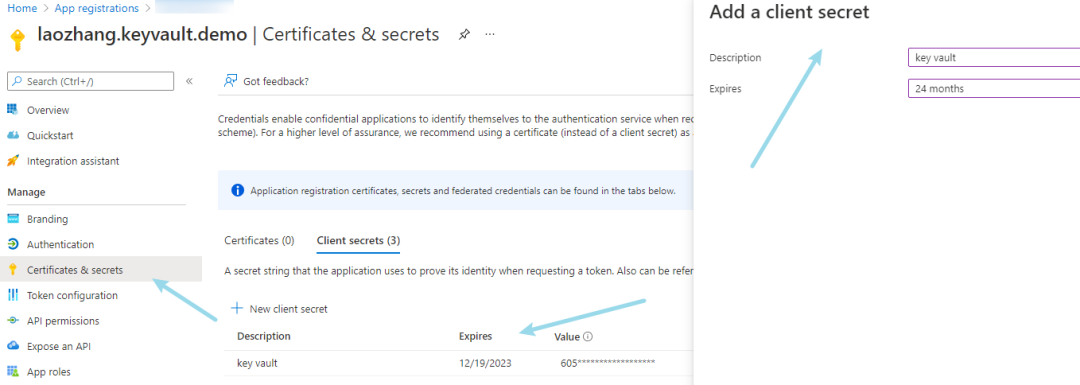
Next, in certificates & secrets, add Client secrets:
With the application, you can set the key in the application.
At this time, we already have two parameters, ClientId and ClientSecret.
Configure key vault
Step 1 - add the Key vault service
Continue searching for the Key vault keyword at the top:
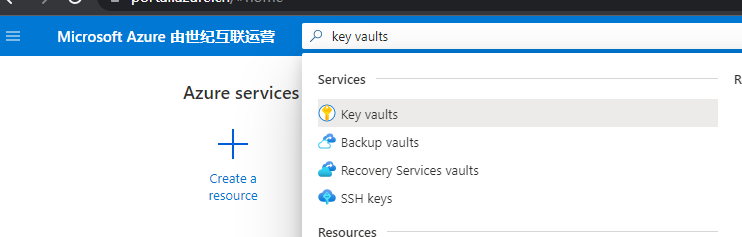
Create a new key vault service, select your own subscription and resource group, and set the following name:
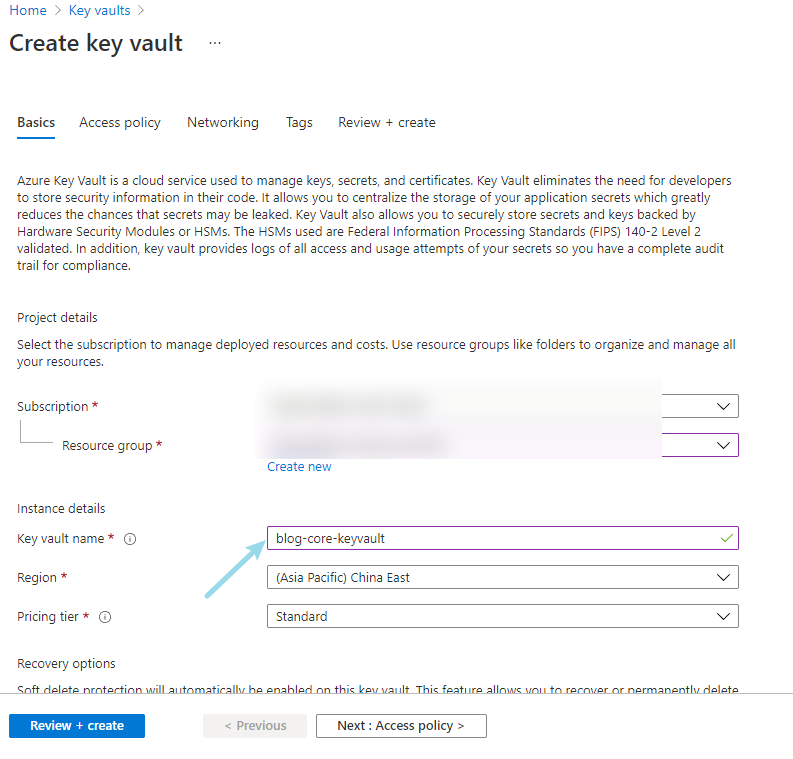
After creation, you can see two other parameters on the overview page of the key vault:
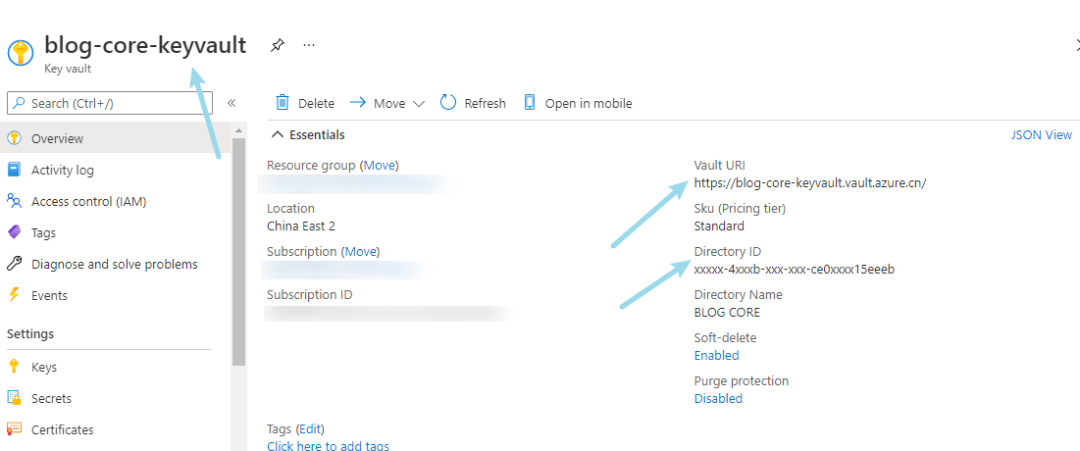
The other two parameters, the uri of vault and tenantid, are also ready.
So far, all four parameters are ready.
Step 2 - parameter setting
Click the secrets option under settings to create or import configurations:
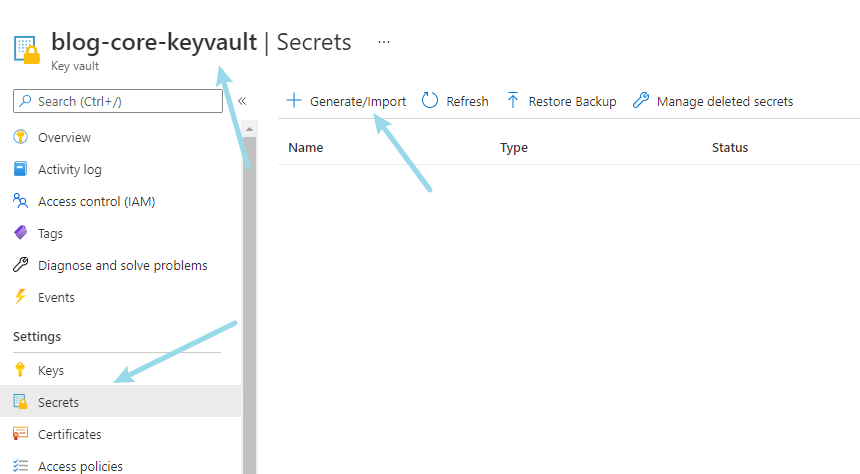
In the pop-up new page, select Manual mode, enter name and value, and configure the user name of the database:
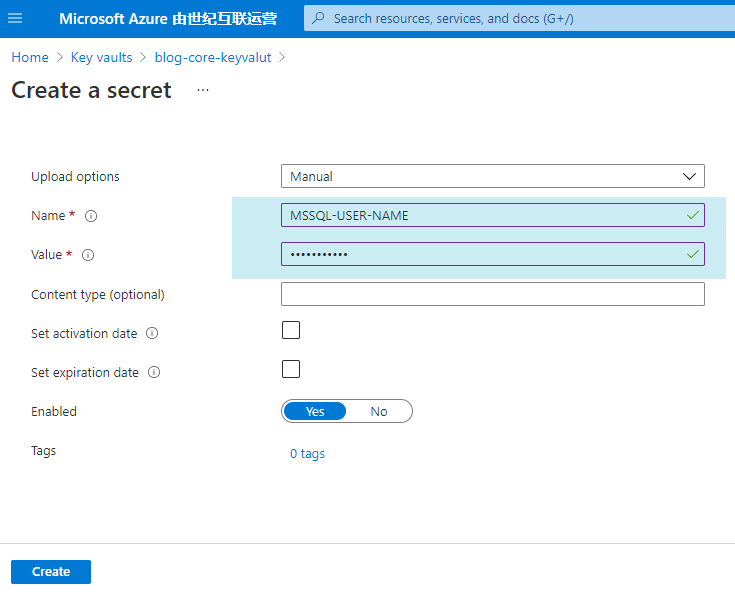
Then the creation is completed. You can configure the password of sqlserver as follows:
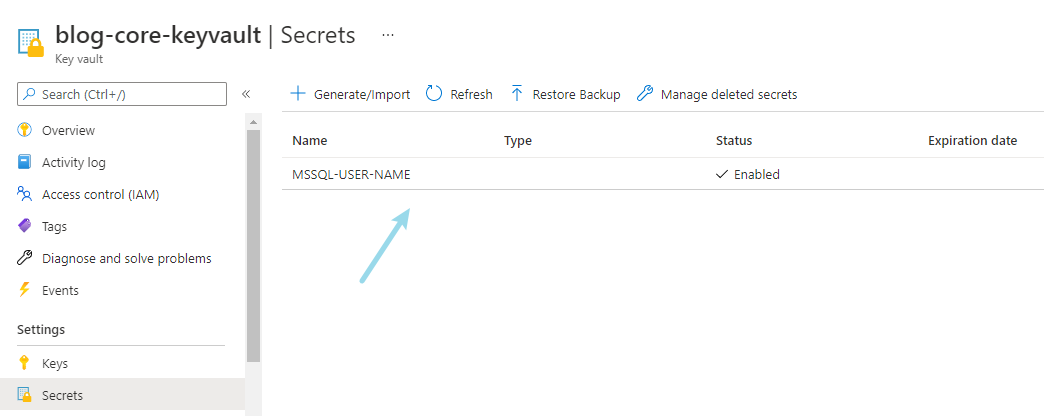
Step 3 - access policy settings
After creation, click go to the resource to configure Access policies, "Settings =" Access policies ", and click" Add Access Policy "to create a new access policy.
First select Configure from template (optional): "Secret Management".
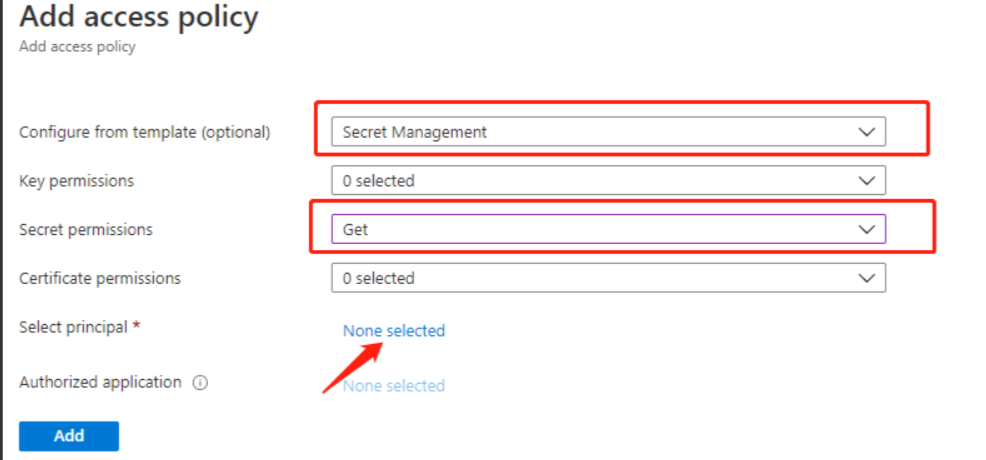
Click "no Select" to Select the service subject first, and enter "your own service account name", such as Laozhang keyvault. Demo, Select, click "Select" and save.
Here, the Azure related configuration has been completed. Start writing code.
Create a new Core project

Step 1 - create an ASP Net Core5. 0 API project
The process is very simple. I won't say more. After creation, add the nuget package:
<PackageReference Include="Microsoft.Extensions.Configuration.AzureKeyVault" Version="3.1.21" /> <PackageReference Include="Microsoft.VisualStudio.Azure.Containers.Tools.Targets" Version="1.10.9" />
Then, put the above four variables into the environment variables, and local development can be done in launchsettings JSON:
"IIS Express": { "commandName": "IISExpress", "launchBrowser": true, "launchUrl": "swagger", "environmentVariables": { "ASPNETCORE_ENVIRONMENT": "Development", "AZURE_TENANT_ID": "Yours tenantid", "AZURE_CLIENT_ID": "Your client id", "AZURE_CLIENT_SECRET": "Your client key", "AZURE_KEY_VAULT_URI": "https://blog-core-keyvault.vault.azure.cn/" } }
Step 2 - configure the Program and connect to the configuration center
In program Configuration in CS:
Host.CreateDefaultBuilder(args)
.ConfigureAppConfiguration((hostingContext, config) =>
{
var env = hostingContext.HostingEnvironment;
var tenantId = Environment.GetEnvironmentVariable("AZURE_TENANT_ID");
var clientId = Environment.GetEnvironmentVariable("AZURE_CLIENT_ID");
var clientSecret = Environment.GetEnvironmentVariable("AZURE_CLIENT_SECRET");
config
.AddJsonFile("appsettings.json", true)
.AddJsonFile($"appsettings.{env.EnvironmentName}.json", true)
.AddEnvironmentVariables();
string vaultUri = "https://blog-core-keyvault.vault.azure.cn/";
config.AddAzureKeyVault(vaultUri, clientId, clientSecret);
})
.ConfigureWebHostDefaults(webBuilder =>
{
webBuilder.UseStartup<Startup>();
});If there is no error in starting the application at this time, congratulations. The connection has been successful. The next step is to obtain the specified parameters.
Step 3 - get the value of the Key Vault anywhere
The method used here is the same as the ordinary Appsettings JSON as like as two peas, and configuration.
_configuration.GetValue<string>("MSSQL-USER-PASSWORD");Well, in ASP Net core application, you have finished connecting to Azure Key Vault. Let's see how Java operates.
Create a new Java project
Step 1 - create a Sring Boot project
The process is also very simple. You can use Idea or the official template to create it. I won't say much. After creating it, add a pom package:
<dependency> <groupId>com.azure.spring</groupId> <artifactId>azure-spring-boot-starter-keyvault-secrets</artifactId></dependency
Then, put the above four variables into the configuration file
azure.keyvault.enabled=trueazure.keyvault.uri=https://blog-core-keyvault. vault. azure. cn/azure. keyvault. Client id = your app idazure keyvault. Client key = your app key azure keyvault. Tenant id = your tenant dazure keyvault. authority-host= https://login.chinacloudapi.cn
Note that the last configuration is very important. You need to specify the host address, because the default is azure COM, if you are azure Com does not need to be specified.
Step 2 - get the value of the Key Vault anywhere
The method used here as like as two peas in yml is the same, and the configuration variables are marked with @value annotation.
@SpringBootApplication
public class KeyvaultApplication implements CommandLineRunner {
@Value("${MSSQL-USER-NAME}")
private String mySecretProperty;
public static void main(String[] args) {
SpringApplication.run(KeyvaultApplication.class, args);
}
@Override
public void run(String... args) {
System.out.println("property your-property-name value is: " + mySecretProperty);
}
}Well, in the Java application, the connection to Azure Key Vault is finished. You can try to contact it.
summary
This paper takes ASP Net core and Java as examples to explain how to connect Key Vault configuration in Azure. The overall process is simple and convenient, and the documents are particularly clear. Once again, we cheer for Microsoft Docs documents.
-
Source Link:
-
https://github.com/Azure/azure-sdk-for-java/tree/master/sdk/spring/azure-spring-boot-starter-keyvault-secrets
-
https://devblogs.microsoft.com/dotnet/category/net-core/?WT.mc_id=DOP-MVP-5003704
-
Github:
-
https://github.com/anjoy8/Blog.Core/
Microsoft MVP

Microsoft's most valuable expert is a global award awarded by Microsoft to third-party technology professionals. Over the past 28 years, technology community leaders around the world have won this award for sharing expertise and experience in their online and offline technology communities.
MVP is a strictly selected expert team. They represent the most skilled and intelligent people. They are experts who are enthusiastic and helpful to the community. MVP is committed to helping others through lectures, forum Q & A, creating websites, writing blogs, sharing videos, open source projects, organizing meetings, and helping users in the Microsoft technology community use Microsoft technology to the greatest extent.
For more details, please visit the official website:
https://mvp.microsoft.com/zh-cn