Active information collection features:
- Direct interactive communication with the target system can not avoid leaving traces of access
- Be prepared to be blocked:
- Detection using a controlled third-party computer
- Using agents or controlled hosts
- Use noise to confuse the target and drown the real detection flow
- Scanning: send different probes and judge the target state according to the returned results
- Generally, active information collection is divided into two-layer scanning, three-layer scanning, four-layer scanning, port scanning and service scanning
1 discovery
1.1 layer 2 detection: Discovery Based on data link layer
- The data unit of data link layer is frame, which is mainly divided into logical link control (LLC) and medium access control (MAC)
- The main protocol is ARP protocol, which is the address resolution protocol. It is a TCP/IP protocol that obtains the MAC address according to the IP address. It resolves 32-bit IP address into 48 bit Ethernet address. It should be noted that ARP protocol corresponds to layer-2 broadcast packet, and broadcast packet cannot access external address through route or gateway
- Principle: send ARP packets to all hosts in the network segment, and judge whether the host is alive by whether there is a packet return
Second floor detection features:
- Advantages: fast scanning speed and reliability
- Disadvantages: non routable
1.1.1 arping
arping 192.168.100.1 -c 1
# Select only the surviving host IP
arping 192.168.100.1 -c 1 | grep 'bytes from' | cut -d ' ' -f 5 | cut -d '(' -f 2 | cut -d ')' -f 1
arping_int.sh
#!/bin/bash
# arping query interface IP network segment
if [ "$#" -ne 1 ]
then
echo "Usage : ./arping_int.sh [Interface] \r\n eg: ./arping_int.sh eth1"
exit
fi
interface=$1
prefix=$(ifconfig $interface | grep 'inet '| cut -d 't' -f 2 | cut -d ' ' -f 2 | cut -d '.' -f 1-3)
for addr in $(seq 1 254)
do
echo $addr
arping -c 1 $prefix.$addr | grep "bytes from" | cut -d " " -f 5 | cut -d "(" -f 2 | cut -d ")" -f 1
done
#In code if In the statement $#Represents the input parameter, - ne means not equal to, that is, the statement means that when the number of input parameters is not 1, the output prompts the correct input method; Then assign the input interface value to the interface variable; The prefix variable is the prefix, in which the ifconfig command is given to the interface variable first, and then the whole information is filtered to only the prefix through the pipeline and cut command, such as 10.10.10; Then there is the for loop statement. The addr variable is traversed gradually from 1 to 254. The arping command is executed in it. The address is prefix and addr is suffix to traverse the whole network segment. Then, the IP conforming to the grep command (here, only the address that returns "bytes from" is the surviving address) is filtered out through the pipe symbol and cut command.
arping_file.sh
#!/bin/bash
# arping queries whether the IP host in the document is online
if [ "$#" -ne 1 ]
then
echo "Usage : ./arping_file.sh [filename]\r\neg: ./arping_file.sh ipaddr.txt"
exit
fi
file=$1
for addr in $(cat $file)
do
echo $addr
arping -c 1 $addr | grep "bytes from" | cut -d " " -f 5 | cut -d "(" -f 2 | cut -d ")" -f 1
done
1.1.2 netdiscover
-
Dedicated to layer 2 Discovery
-
It can be used in wireless and switched network environment
-
Active and passive detection
- Active: easy to trigger alarm
netdiscover ‐i eth0 ‐r 192.168.1.0/24 - Passive:
netdiscover ‐p ‐i eth0 ‐r 192.168.1.0/24- Discover the host by monitoring arp packets in the network environment
- Active: easy to trigger alarm
1.1.3 SCAPY constructs ARP probe packet
- It can be called as a Python library or used as a separate tool
- Functions: capturing packets, analyzing, creating, modifying and injecting network traffic
# View current ARP packet information
>>> ARP().display()
###[ ARP ]###
hwtype= 0x1
ptype= IPv4
hwlen= None
plen= None
op= who-has
hwsrc= 00:50:56:2b:0a:85
psrc= 172.30.54.33
hwdst= 00:00:00:00:00:00
pdst= 0.0.0.0
>>> arp=ARP()
# Modify ARP packet information
>>> arp.pdst='172.30.0.2'
>>> arp.display()
###[ ARP ]###
hwtype= 0x1
ptype= IPv4
hwlen= None
plen= None
op= who-has
hwsrc= 00:50:56:2b:0a:85
psrc= 172.30.54.33
hwdst= 00:00:00:00:00:00
pdst= 172.30.0.2
# Send modified packet
>>> sr1(arp)
Begin emission:
Finished sending 1 packets.
*
Received 1 packets, got 1 answers, remaining 0 packets
<ARP hwtype=0x1 ptype=IPv4 hwlen=6 plen=4 op=is-at hwsrc=80:05:88:41:de:c1 psrc=172.30.0.2 hwdst=00:50:56:2b:0a:85 pdst=172.30.54.33 |<Padding load='\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00' |>>
>>>
# Save received data
>>> recv=sr1(arp)
Begin emission:
Finished sending 1 packets.
*
Received 1 packets, got 1 answers, remaining 0 packets
# Print saved data
>>> recv
<ARP hwtype=0x1 ptype=IPv4 hwlen=6 plen=4 op=is-at hwsrc=80:05:88:41:de:c1 psrc=172.30.0.2 hwdst=00:50:56:2b:0a:85 pdst=172.30.54.33 |<Padding load='\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00' |>>
# View packet return information
>>> recv.display()
###[ ARP ]###
hwtype= 0x1
ptype= IPv4
hwlen= 6
plen= 4
op= is-at
hwsrc= 80:05:88:41:de:c1
psrc= 172.30.0.2
hwdst= 00:50:56:2b:0a:85
pdst= 172.30.54.33
###[ Padding ]###
load= '\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00'
# Query directly through ARP()
>>> sr1(ARP(pdst='172.30.0.1'),timeout=1,verbose=0)
<ARP hwtype=0x1 ptype=IPv4 hwlen=6 plen=4 op=is-at hwsrc=00:74:9c:fd:7a:73 psrc=172.30.0.1 hwdst=00:50:56:2b:0a:85 pdst=172.30.54.33 |<Padding load='\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00' |>>
>>>
1.2 three layer detection: Discovery Based on network layer
- Use IP and ICMP protocols to detect whether the host exists
- Advantages: routable
- Disadvantages: it may be filtered by the firewall
1.2.1 ping
ping 8.8.8.8 ping -c 1 8.8.8.8 | grep 'bytes from' | cut -d ' ' -f 4 | cut -d ':' -f1 # ping must output the result before processing the data
ping.sh
#!/bin/bash
# Batch PING
if [ "$#" -ne 1 ]
then
echo "Usage : ./pinger.sh [/24 network address]"
exit
fi
prefix=$(echo $1 | cut -d '.' -f 1-3)
for addr in $(seq 1 254)
do
ping -c 1 $prefix.$addr | grep "bytes from" | cut -d " " -f 4 | cut -d ":" -f 1
done
# The key code is to pass the ping command, and then pipeline to grep "bytes from". Only the host containing the string is the surviving host. Finally, filter it out through the pipeline and cut command.
ping.py
#!/usr/bin/python
import logging
import subprocess
logging.getLogger("scapy.runtime").setLevel(logging.ERROR)
from scapy.all import *
if len(sys.argv)!= 2:
print("Usage - ./ping1.py [/24 network address]")
print("Example - ./ping1.py 128.38.28.3")
sys.exit()
address = str(sys.argv[1])
prefix = address.split(".")[0]+'.'+address.split(".")[1]+'.'+address.split(".")[2]+"."
for addr in range(1, 254):
a=sr1(IP(dst=prefix+str(addr))/ICMP(),timeout=0.1,verbose=0)
if a == None:
pass
else:
print(prefix+str(addr))
1.2.2 NMAP
# -sn: Ping Scan nmap -v -sn 172.30.0.1-5 | grep -v 'host down' nmap -v -sn 172.30.0.0/24 | grep -v 'host down' nmap -iL iplist.txt -sn
1.2.3 fping
Fping is a program similar to ping. Unlike ping, you can specify multiple targets to ping at the same time. After sending the ping packet, fping does not wait for a response, but continues to the next target
fping 172.30.0.1 -c 1 fping -g 172.30.0.1 172.30.0.2 fping -g 172.30.0/24 fping -f iplist.txt
1.2.4 Hping
- Hping is a command line oriented open source tool for generating and parsing TCP/IP protocol packet assembly / analysis. The latest version is hping3, which supports TCP, UDP, ICMP and RAW-IP protocols, has tracking routing mode, can send files between covered channels and many other functions.
- hping is a standard tool for security audit and firewall testing.
- The advantage of hping is that it can customize each part of the packet, so users can flexibly detect the target machine in detail.
hping3 -1 172.30.0.1
default mode TCP
-0 --rawip RAW IP mode
-1 --icmp ICMP mode
-2 --udp UDP mode
-8 --scan SCAN mode.
Example: hping --scan 1-30,70-90 -S www.target.host
-9 --listen listen mode
1.3 four layer detection: Discovery Based on transport layer
- Advantages: routable, reliable results, unlikely to be filtered by the firewall
- Disadvantages: the firewall based on state filtering may filter scanning, and the speed of full port scanning is slow
- Principle:
- TCP: ACK, RST. Set the flag bit of the TCP packet header to ACK, and then send it to a target / port. Finally, judge whether the rst response packet is received, so as to determine whether the target exists!. SYN, SYN/ACK and RST are complete
- UDP: if it exists, the ICMP port is unreachable; if it does not exist, there is no packet return.
1.3.1 Scapy constructs four layer TCP probe packets
>>> ip=IP()
>>> tcp=TCP()
>>> send=(ip/tcp)
>>> send[IP].dst='172.30.26.130' #Set destination Ip address
>>> send[TCP].flags='A' #Set TCPflags to "ACK"“
>>> send.display()
###[ IP ]###
version= 4
ihl= None
tos= 0x0
len= None
id= 1
flags=
frag= 0
ttl= 64
proto= tcp
chksum= None
src= 172.30.54.33
dst= 172.30.26.130
\options\
###[ TCP ]###
sport= ftp_data
dport= http # TCP port 80 is detected by default
seq= 0
ack= 0
dataofs= None
reserved= 0
flags= A
window= 8192
chksum= None
urgptr= 0
options= []
>>> recv=sr1(send)
# Packet return information query
>>> recv.display()
###[ IP ]###
version= 4
ihl= 5
tos= 0x0
len= 40
id= 0
flags= DF
frag= 0
ttl= 64
proto= tcp
chksum= 0x91f0
src= 172.30.26.130
dst= 172.30.54.33
\options\
###[ TCP ]###
sport= http
dport= ftp_data
seq= 0
ack= 0
dataofs= 5
reserved= 0
flags= R # flags bit is R
window= 0
chksum= 0x69d
urgptr= 0
options= []
###[ Padding ]###
load= '\x00\x00\x00\x00\x00\x00'
>>> recv
<IP version=4 ihl=5 tos=0x0 len=40 id=0 flags=DF frag=0 ttl=64 proto=tcp chksum=0x91f0 src=172.30.26.130 dst=172.30.54.33 |<TCP sport=http dport=ftp_data seq=0 ack=0 dataofs=5 reserved=0 flags=R window=0 chksum=0x69d urgptr=0 |<Padding load='\x00\x00\x00\x00\x00\x00' |>>>
# Use a statement
recv=sr1(IP(dst="172.30.26.130")/TCP(flags='A'),timeout=1,verbose=0)
Process:
-
Send the packet with "A" flag in TCP first. If the integer of TCP flag bit in the received packet is 4, the target host will survive and output IP. As for why the integer value of flags bit should be 4, here you can use Wireshark to capture packets:
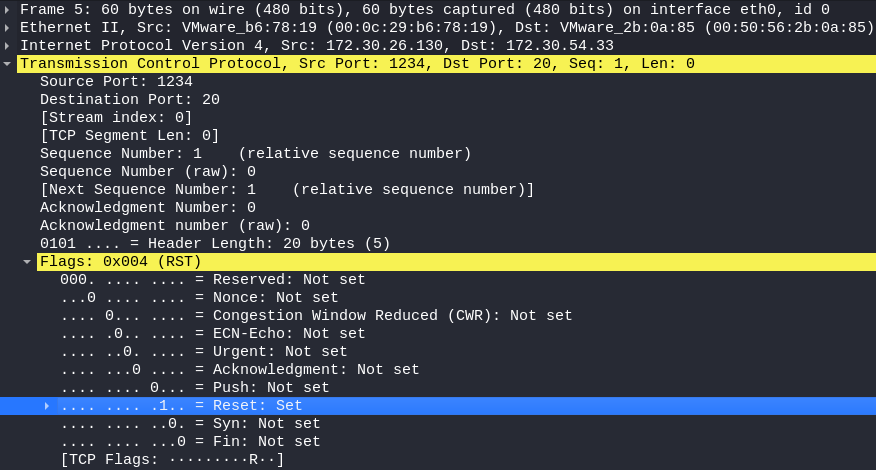
Python script implements TCP layer 4 Detection
#!/usr/bin/python
import logging
logging.getLogger("scapy.runtime").setLevel(logging.ERROR)
from scapy.all import *
if len(sys.argv) != 2:
print("Usage : ./tcp_ping.py [/24 network address]")
sys.exit()
address = str(sys.argv[1])
prefix = address.split('.')[0] + '.' + address.split('.')[1] + '.' + address.split('.')[2] + '.'
for addr in range(130, 131):
response = sr1(IP(dst=prefix + str(addr)) / TCP(dport=1234, flags='A'), timeout=0.1, verbose=0)
try:
if int(response[TCP].flags) == 4:
print(prefix + str(addr))
except:
pass
1.3.2 construction of four layer UDP probe packet by scapy
Note: UDP discovery is unreliable
>>> ip=IP()
>>> udp=UDP()
>>> send=(ip/udp)
>>> send[IP].dst='172.30.0.1'
>>> send.display()
###[ IP ]###
version= 4
ihl= None
tos= 0x0
len= None
id= 1
flags=
frag= 0
ttl= 64
proto= udp
chksum= None
src= 172.30.54.33
dst= 172.30.0.1
\options\
###[ UDP ]###
sport= domain
dport= domain
len= None
chksum= None
>>> recv=sr1(send,timeout=1,verbose=1)
Begin emission:
Finished sending 1 packets.
Received 2 packets, got 1 answers, remaining 0 packets
>>> recv.display()
###[ IP ]###
version= 4
ihl= 5
tos= 0xc0
len= 56
id= 58443
flags=
frag= 0
ttl= 64
proto= icmp # The protocol is ICMP
chksum= 0x75b
src= 172.30.0.1
dst= 172.30.54.33
\options\
###[ ICMP ]###
type= dest-unreach
code= port-unreachable
chksum= 0x8b75
reserved= 0
length= 0
nexthopmtu= 0
###[ IP in ICMP ]###
version= 4
ihl= 5
tos= 0x0
len= 28
id= 1
flags=
frag= 0
ttl= 64
proto= udp
chksum= 0xec71
src= 172.30.54.33
dst= 172.30.0.1
\options\
###[ UDP in ICMP ]###
sport= domain
dport= domain
len= 8
chksum= 0x7115
# Use a statement
recv=sr1(IP(dst="192.168.0.1")/UDP(dport=53),timeout=1,verbose=1)
Python script implements UDP four layer detection
#!/usr/bin/python
import logging
logging.getLogger("scapy.runtime").setLevel(logging.ERROR)
from scapy.all import *
if len(sys.argv) != 2:
print("Usage - ./ping1.py [/24 network address]")
print("Example - ./ping1.py 128.38.28.3")
sys.exit()
address = str(sys.argv[1])
prefix = address.split(".")[0] + '.' + address.split(".")[1] + '.' + address.split(".")[2] + '.'
for addr in range(1, 254):
response = sr1(IP(dst=prefix + str(addr)) / UDP(dport=7634), timeout=0.1, verbose=0)
try:
if int(response[IP].proto) == 1: # Why is protoco=1,
# It can be found through wireshark packet capture
# The ip layer has a protocol field, which points to its upper layer protocol. TCP is 6,ICMP is 1 and ijmp is 1
# Is 2, UDP is 17,
# From this, we can know that the ip upper layer protocol is not necessarily tcp, but udp,
# There can also be many other types of protocols. Here we send a udp package to
# Target, we judge whether the ip survives by whether we receive the icmp packet from the target
print(prefix + str(addr))
except:
pass
1.3.3 NMAP
# UDP probe nmap -sn -PU1234 172.30.26.130 # TCP probe nmap -sn -PA80 172.30.26.130 nmap -sn -PA80 -iL iplist.txt
1.3.4 hping
# Default hping3 hping3 -c 1 172.30.26.130 # Set hping3 to UDP probe hping3 -2 -c 1 172.30.26.130
TCP host discovery through shell script
#!/bin/bash
if [ "$#" -ne 1 ]
then
echo "Usage : ./TCP_hping.sh [/24 network address]"
exit
fi
prefix=$(echo $1 | cut -d'.' -f 1-3)
for addr in $(seq 1 254)
do
hping3 -c 1 $prefix.$addr>> r.txt;
done
grep ^len r.txt | cut -d " " -f 2 | cut -d "=" -f 2 >> TCP_hping.txt
rm r.txt
UDP host discovery through shell script
#!/bin/bash
if [ "$#" -ne 1 ]
then
echo "Usage : ./UDP_hping.sh [/24 network address]"
exit
fi
prefix=$(echo $1 | cut -d'.' -f 1-3)
for addr in $(seq 1 254)
do
hping3 -2 -c 1 $prefix.$addr>> r.txt;
done
grep Unreachable r.txt | cut -d " " -f 5 | cut -d "=" -f 2 >> UDP_hping.txt
rm r.txt