This case is the sorting of IPsec over GRE materials on Digital China devices
It is used for personal study and record. In case of any doubt, you shall prevail. You are welcome to point out mistakes
Function introduction:
When using IPSEC static tunnel networking, it is necessary to manually configure the tunnel at both ends of each IPSEC tunnel without dynamic negotiation. However, with the increase of encryption points and tunnels, it is more difficult to configure and maintain IPSEC tunnels. Therefore, static tunnel technology is generally used in scenes with few encryption points
working principle:
IPSec VPN is divided into two negotiation stages, ISAKMP stage and IPSec stage. ISAKMP stage is mainly to negotiate the protection policies at both ends, verify the legitimacy of peers, generate encryption keys and protect the negotiation of IPSec SA in the second stage. The second stage is the IPSec stage, which mainly determines the protection strategy of IPSec SA, whether to use AH or ESP, transmission mode or tunnel mode, what is the protected data, and so on. The goal of the second stage negotiation is to generate an IPSec SA that is really used to protect IP data. The two sides of IPSec communication entities must reach an agreement on these security policies in phase I and phase II, otherwise the IPSec negotiation will not pass
Network experiment topology: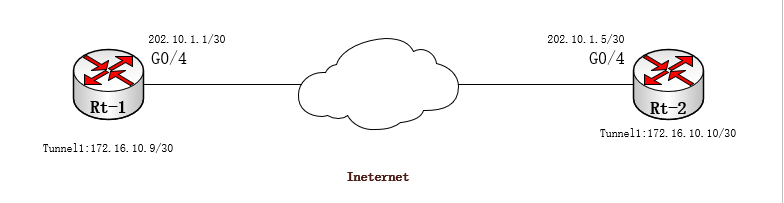
I Basic equipment configuration:
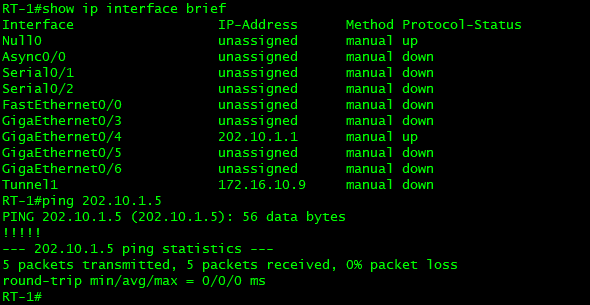
II Configure GRE tunnel:
Rt-1: interface Tunnel1 ip address 172.16.10.9 255.255.255.252 tunnel source GigaEthernet0/4 tunnel destination 202.10.1.5 tunnel mode gre ip Configure as GRE Pattern( tunnel Koumo thinks GRE)
Rt-2: interface Tunnel1 ip address 172.16.10.10 255.255.255.252 tunnel source GigaEthernet0/4 tunnel destination 202.10.1.1 tunnel mode gre ip
III IPSEC configuration:
1.ipsec configuration steps
(1) Configure ipsec streams of interest
(2) Configure isakmp policy
(3) Configure preshared key
(4) Configure ipsec encryption conversion set
(5) Configure ipsec encryption graph
(6) Apply encrypted graph to interface
2. Configure ipsec with RT-1:
RT-1_config#IP access list extended ACL configure streams of interest (Note that you must ACL Must be an extension ACL,Because standard ACL Check only the source address of the packet; extend ACL Check both the source address and destination address of the packet.) RT-1_config_ext_nacl#permit ip any any RT-1_config#
RT-1_config#Crypto ISAKMP policy 1 configure ISAKMP policy with priority of 1 RT-1_config_isakmp#Authentication pre share sets the authentication method as pre shared secret key RT-1_config_isakmp#Set the hash md5 algorithm to md5 RT-1_config_isakmp#exit
RT-1_config#Crypto ISAKMP key 123 172.16.10.10 configure pre shared secret key appoint peer 172.16.10.10 The preshared key for is“ ruijie",The opposite end must also be configured with a consistent key. If digital certificate is used/No configuration is required for envelope authentication.
RT-1_config#Crypto IPSEC transform set IPSEC configure IPSEC transform set RT-1_config_crypto_trans#Exit uses the default configuration, so you can exit directly
Default content of ipsec transform set: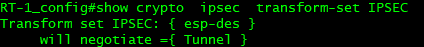
RT-1_config#Crypto map IPSec ACL 1 IPSec ISAKMP create a new encryption map named "IPSec ACL" RT-1_config_crypto_map#set peer 172.16.10.10 specify the peer address RT-1_config_crypto_map#Set transform set IPSEC specifies the encryption conversion set "IPSEC" RT-1_config_crypto_map#match address ACL configures streams of interest RT-1_config_crypto_map#exit
RT-1_config#int tunnel 1 RT-1_config_t1#Crypto map IPSec ACL application encryption map RT-1_config_t1#exit
The configuration of RT-2 is almost the same except for the peer address, which is omitted here
3. ping the opposite address with the original address in Rt-1 to activate IPSEC
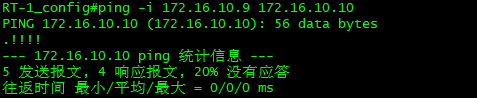
4. Check whether isakmp, IPSec and SA have been negotiated successfully on R1
RT-1_config#show crypto isakmp sa
dst src state state-id conn
172.16.10.10 172.16.10.9 <I>Q_SA_SETUP 2 10 IPSECACL 1
172.16.10.10 172.16.10.9 <I>M_SA_SETUP 1 10 IPSECACL 1
RT-1_config#show crypto ipsec sa
Interface: Tunnel1
Crypto map name:IPSECACL , local addr. 172.16.10.9 / / the name of the encryption graph running under the interface and the ip address used for isakmp/ipsec negotiation
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0) / / original address of stream of interest
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0) / / destination address of stream of interest
local crypto endpt.: 172.16.10.9, remote crypto endpt.: //172.16.10.10 end point of local encryption and remote encryption
inbound esp sas:
spi: 0x939892ee (2476249838) / / spi in the direction of IPSec SA
transform: ESP DES / / ipsec encryption conversion set to ESP des
In use settings = {tunnel} / / tunnel mode is adopted
sa timing: remaining key lifetime (k/sec): (4607999 / 3273) / / there are 4607999 kilobytes / 1324 seconds before the life cycle of the security alliance expires
Outbound ESP SAS: / / the spi in the outbound direction of ipsec sa. Only seeing the inbound spi and outbound spi indicates that ipsec sa has negotiated successfully.
spi:0xfde6f413(4259771411)
transform: esp-des
in use settings ={ Tunnel }
sa timing: remaining key lifetime (k/sec): (4607999/3273)