Linux-IP tables
Brief introduction
Netfilter is a Linux 2.4 kernel firewall framework proposed by Rusty Russell. The rules set by Netfilter are stored in the kernel space, while iptables is an application layer application. It modifies XXtables(Netfilter configuration table) stored in the kernel space through the interface released by Netfilter.
Five chains and four tables
Five chain
After iptables is enabled, the data message will pass through 5 checkpoints from entering the server to exiting
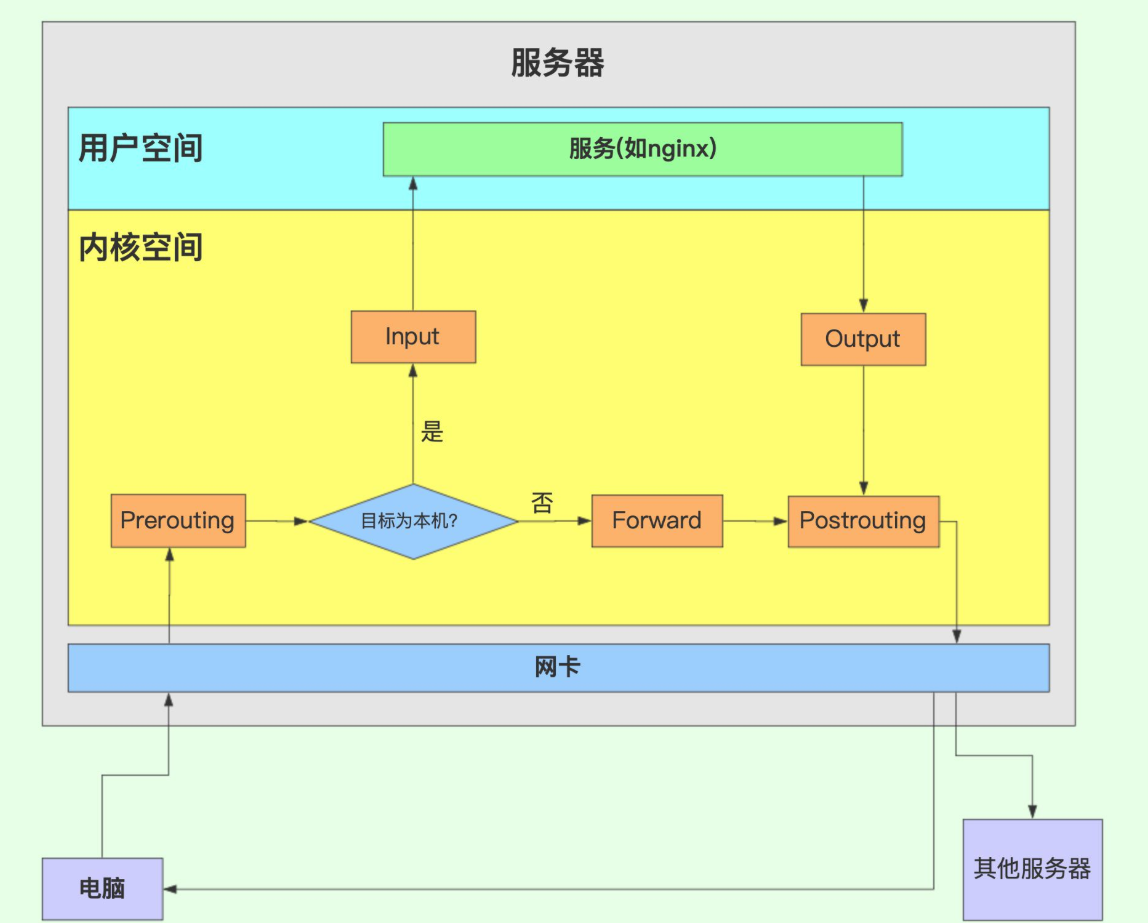
- **INPUT chain: * * when receiving packets (inbound) from the local address of the firewall, the rules in this chain shall be applied;
- **OUTPUT chain: * * the rules in this chain shall be applied when the firewall sends packets (outbound) to the outside;
- **FORWARD chain: * * when receiving a packet (forwarding) that needs to be sent to other addresses through the firewall, the rules in this chain shall be applied;
- Preouting chain: (the Internet enters the LAN) apply the rules in this chain before routing packets, such as DNAT;
- POSTROUTING chain: (LAN out of the Internet) after routing packets, apply the rules in this chain, such as SNAT.
beyond the limits of the visible world
Although there are multiple rules in each chain, the functions (functions) of some rules are very similar. Multiple rules with the same functions together form a "table". iptables provides four "tables":
- * * filter table: * * it is mainly used to filter data packets and decide whether to release the data packets according to specific rules (such as DROP, ACCEPT, REJECT and LOG). The so-called firewall basically refers to the filtering rules on this table, corresponding to the kernel module iptables_filter;
– * * NAT table: * * network address translation, the network address translation function, is mainly used to modify the IP address, port number and other information of the packet (network address translation, such as SNAT, DNAT, MASQUERADE and REDIRECT). Packets belonging to a stream (data may be divided into multiple packets due to packet size constraints) will only pass through this table once. If the first packet is allowed to do NAT or Masqueraded, the remaining packets will automatically do the same operation, that is, the remaining packets will not pass through this table again. Corresponding kernel module iptables_nat;
- * * mangle table: * * disassemble the message, modify it, and reseal it. It is mainly used to modify the TOS(Type Of Service), TTL(Time To Live) of the packet and set the Mark mark for the packet to realize Qos(Quality Of Service) adjustment, policy routing and other applications. Due to the need for corresponding routing equipment support, Therefore, it is not widely used. Corresponding kernel module iptables_mangle;
– * * * raw table: * * is a new table added to iptables since version 1.2.9. It is mainly used to determine whether data packets are processed by the state tracking mechanism. When matching data packets, the rules of raw table shall take precedence over other tables, corresponding to the kernel module iptables_raw.
The firewall rules we finally define will be added to one of the four tables.
Linked list relation
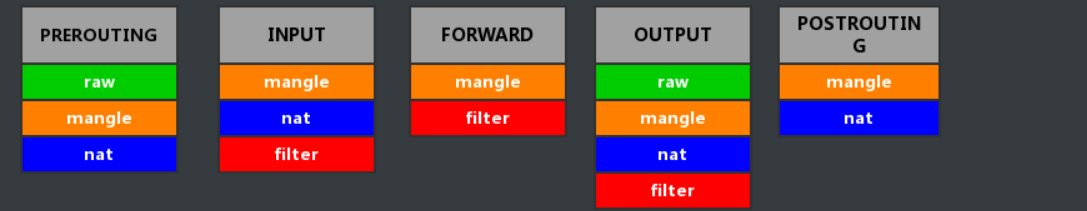
The matching order of each table in each chain is: raw → mangle → nat → filter.
Matching rules
Matching conditions
- **S_IP: * * source ip, source ip
- **S_PORT: * * source port
- D_IP: destination ip, destination ip
- D_PORT: destination port
- **TCP/UDP: * * layer 4 (transport layer) protocol
Action of processing
- **ACCEPT: * * allow data packets to pass;
- **DROP: * * directly discards the data packet and does not respond to any information. The client will respond only after the link times out;
- **REJECT: * * REJECT the packet and send a response message to the client that the packet is discarded;
- **SNAT: * * S refers to Source, Source nat (Source address translation). After entering the route at the routing level and before leaving the local network stack, rewrite the Source address and keep the target address unchanged, and establish a NAT table item on the local machine. When the data is returned, rewrite the destination address data into the Source address when the data is sent out according to the NAT table and send it to the host machine. Solve the problem that private network users use the same public network IP to access the Internet;
- **MASQUERADE: * * is a special form of SNAT, which is applicable to dynamic and temporary IP;
- **DNAT: * * D refers to Destination, Destination NAT, which solves the problem of private network server receiving public network requests. In contrast to SNAT, before the IP packet passes through the route, the Destination address is modified again and the source address remains unchanged. A NAT table entry is established on the local machine. When the data is returned, the source address is modified to the Destination address when the data is sent according to the NAT table and sent to the remote host. You can hide the real address of the back-end server;
- **REDIRECT: * * port mapping on the local machine;
- **LOG: * * record the LOG information in the / var/log/messages file, and then pass the packet to the next rule.
Except the last LOG, after the first three rules match the packet, the packet will not continue to match, so the order of rules written is extremely critical.Start iptables
# Start iptables systemctl start firewalld # View iptables status systemctl status firewalld # Stop iptables systemctl stop firewalld # Restart iptables systemctl restart firewalld # Overloaded iptables systemctl reload firewalld
Parameter options
#-L list abbreviation iptables -L INPUT #View rules on INPUT chain iptables -L #View all chain rules #-T table abbreviation iptables -t filter -L #View the rules in the filter table #-The abbreviation of N numeric, which means that the specified source and destination addresses and ports are displayed in the form of numbers / values. Otherwise, it will be displayed in the form of domain name / host name / program name by default. This option is generally used with ` - L ' #-v verbose abbreviation, that is, output more detailed information. It can be used in conjunction with - L. when used in conjunction, - L must be placed last, followed by parameters #--Line numbers displays the serial number of the list, - line can also be used #-I specifies in which chain #-s matches the source IP #-j jump jump, followed by specified actions, such as ACCEPT, DROP, REJECT, etc #-F flush empty #-R replace replace #-P policy policy iptables -t raw -P OUTPUT ACCEPT #-d destination address #-p is used to match the protocol iptables -t filter -I INPUT -p tcp -s 192.168.1.146 -j ACCEPT #-i is used to match which network card interface flows into the machine iptables -t filter -I INPUT -p icmp -i eth0 -j DROP #-o used to match which network card interface flows out of the machine
Addition, deletion, modification and query of rules
#add to iptables -t filter -I INPUT -s 192.168.198.129 -j DROP #delete iptables -t filter -D INPUT 2 #According to number iptables -t filter -D INPUT -s 192.168.198.129 -j DROP #According to conditions iptables -t filter -F INPUT #Clear the rules in the filter table on the INPUT chain #modify iptables -t filter -R INPUT 1 -s 192.168.198.129 -j ACCEPT iptables -P FORWARD DROP #Set the default rule of FORWARD chain to DROP
The file is saved in / etc/sysconfig/iptables
Scan script of defense website scanner
# log file path
logfile=/var/log/httpd/
last_minutes=1
# 1 minute before the start time (it can be modified here. If the number of attacks within a few minutes is required, it can be customized here). Time format: day, month, year, hour, minute and second
start_time=`date -d"$last_minutes minutes ago" +"%d/%m/%Y:%H:%M:%S"`
echo $start_time
# End time now
stop_time=`date +"%d/%m/%Y:%H:%M:%S"`
echo $stop_time
cur_date="`date +%d/%m/%Y`"
echo $cur_date
# Filter out the logs between companies and count the maximum ip number. Please replace it with your log path
tac $logfile/access.log | awk -v st="$start_time" -v et="$stop_time" '{t=substr($4,2);if(t>=st && t<=et){print $1}}' |sort | uniq -c | sort -nr > $logfile/log_massage
#ip_top=`cat $logfile/log_massage| head -1 | awk '{print $1}'`
# If the horizontal bar appears, use sed to remove the first line
#sed -i '1d' $logfile/log_massage
# ip with more than 200 single ip accesses per unit time [1 minute] is recorded in the mashage txt
ip=`cat $logfile/log_massage| awk '{if($1 > 100)print $2}'`
for line in $ip
do
echo $line >> $logfile/massage.txt
echo $line
iptables -I INPUT -p tcp -m multiport --dport 80,443 -s $line -j DROP
done