Five chains and four tables
Concept of chain
After iptables is enabled, the data message will pass through five checkpoints from entering the server to exiting, namely pre routing, input, output, forward and post routing
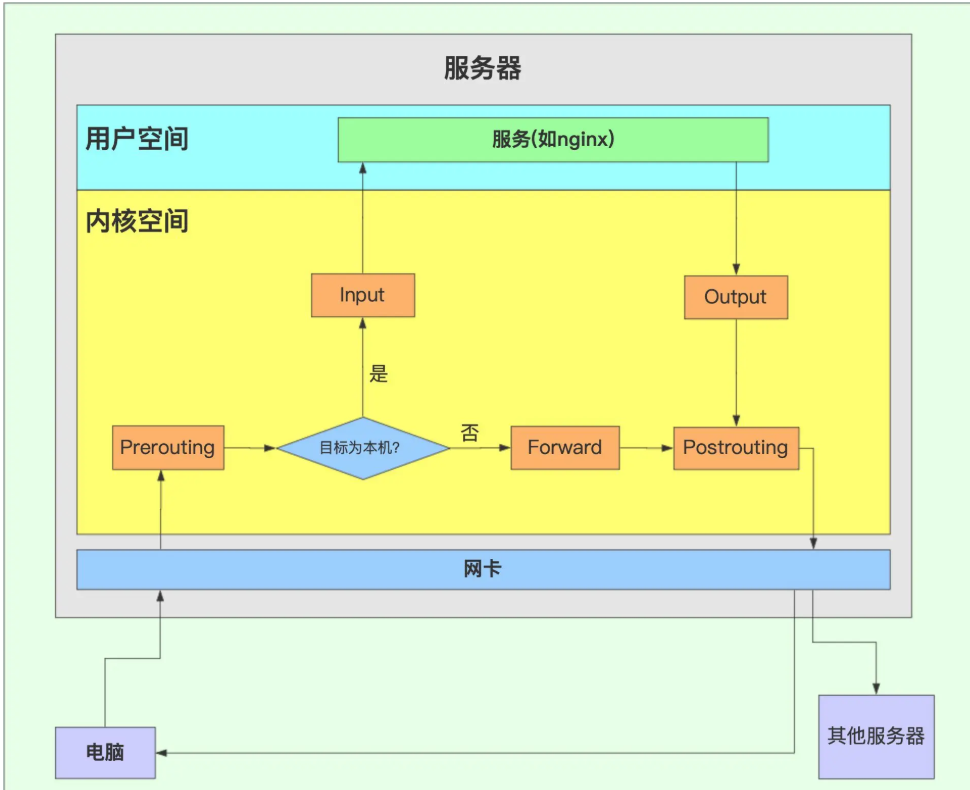
There are multiple rules in each level. Data packets must match these rules one by one in order. These rules are connected like a chain, so we call these levels "chain"
The INPUT and OUTPUT chains are more used in the "host firewall", that is, they are mainly used for the security control of the incoming and outgoing data of the server; The FORWARD, forwarding and POSTROUTING chains are more used in the "network firewall", especially when the firewall server is used as a gateway.
Concept of table
Although there are multiple rules in each chain, the functions (functions) of some rules are very similar. Multiple rules with the same functions together form a "table". iptables provides four "tables":
– filter table: it is mainly used to filter data packets and decide whether to release the data packets according to specific rules (such as DROP, ACCEPT, REJECT and LOG). The so-called firewall basically refers to the filtering rules on this table, corresponding to the kernel module iptables_filter;
– NAT table: network address translation, which is mainly used to modify the IP address, port number and other information of the packet (network address translation, such as SNAT, DNAT, MASQUERADE and REDIRECT). Packets belonging to a stream (data may be divided into multiple packets due to packet size constraints) will only pass through this table once. If the first packet is allowed to do NAT or Masqueraded, the remaining packets will automatically do the same operation, that is, the remaining packets will not pass through this table again. Corresponding kernel module iptables_nat;
– mangle table: disassemble the message, make modifications, and reseal. It is mainly used to modify the TOS(Type Of Service), TTL(Time To Live) of the packet and set the Mark mark Mark for the packet to realize Qos(Quality Of Service) adjustment, policy routing and other applications. Due to the need for corresponding routing equipment support, Therefore, it is not widely used. Corresponding kernel module iptables_mangle;
– raw table: it is a new table added to iptables since version 1.2.9. It is mainly used to determine whether data packets are processed by the state tracking mechanism. When matching data packets, the rules of raw table shall take precedence over other tables, corresponding to the kernel module iptables_raw. The firewall rules we finally define will be added to one of the four tables.
In the past practice, filter table can be used for more than 90%, while mangle table and raw table are rarely seen
Watch chain relationship
In the five chains (i.e. five levels), not all types of tables can be applied to each chain. In fact, except that the Ouptput chain can have four tables at the same time, there are only two or three tables in other chains:
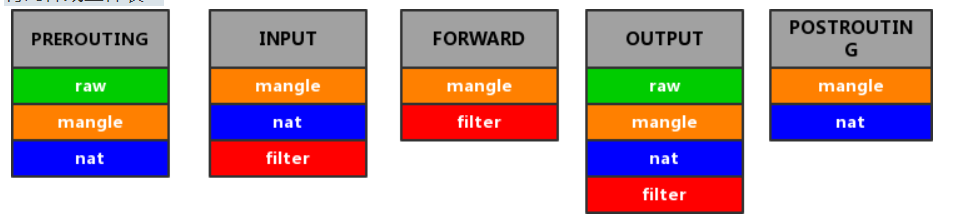
In fact, we can see from the above figure that no matter which chain, the raw table is always on the mangle table, the mangle table is always on the nat table, and the nat table is always on the filter table, which indicates that there is a matching order between the tables.
As mentioned earlier, data packets must match one rule on each chain in order, but in fact, the rules of the same class (i.e. belonging to the same table) are placed together, and the rules of different classes will not be placed cross. According to the above law, the matching order of each table on each chain is: raw → mangle → nat → filter.
Concept of rules
Matching conditions
-
S_IP: source ip
-
S_PORT: source port
-
D_IP: destination ip, destination ip
-
D_PORT: destination port
-
TCP/UDP: layer 4 (transport layer) protocol
Action of processing
-
ACCEPT: allow data packets to pass;
-
DROP: directly discard the data packet without responding to any information. The client will respond only after the link times out;
-
REJECT: REJECT the packet and send a response message to the client that the packet is discarded;
-
SNAT: S refers to Source and Source nat (Source address translation). After entering the route at the routing level and before leaving the local network stack, rewrite the Source address and keep the target address unchanged, and establish a NAT table item on the local machine. When the data is returned, rewrite the destination address data into the Source address when the data is sent out according to the NAT table and send it to the host machine. Solve the problem that private network users use the same public network IP to access the Internet;
-
MASQUERADE: it is a special form of SNAT, which is applicable to dynamic and temporary variable IP;
-
DNAT: D refers to Destination and Destination NAT, which solves the problem of private network server receiving public network requests. In contrast to SNAT, before the IP packet passes through the route, the Destination address is modified again and the source address remains unchanged. A NAT table entry is established on the local machine. When the data is returned, the source address is modified to the Destination address when the data is sent according to the NAT table and sent to the remote host. You can hide the real address of the back-end server;
-
REDIRECT: port mapping on the local machine;
-
LOG: record the LOG information in the / var/log/messages file, and then pass the packet to the next rule. Except the last LOG, after the first three rules match the packet, the packet will not continue to match, so the order of rules written is extremely critical.
-
iptables command operation
Since the servers of most domestic companies adopt CentOS system, here we take CentOS as an example.
service iptables start
Other commands
# View startup status service iptables status # Stop iptables service iptables stop # Restart iptables (restart is actually stop and then start) service iptables restart # Overloading is the rule of reloading configuration, which seems to be the same as restarting here service iptables reload
Query rules
Command format: iptables [options] [parameters]
Common options: - L: abbreviation of list. List is usually translated into list, which means to list the rules on each chain. Because multiple rules are a list, it is represented by - L- L can also be followed by one of the chain names of five chains (postoutgoing, INPUT, FORWARD, OUTPUT and postoutgoing). Note that the chain name must be in uppercase. For example, check the rules on "INPUT chain":
-
-t: Specify which table to insert into. If it is not written, it defaults to the "filter" table;
-
-1: Specify which chain to insert into, and insert (I:Input) at the front of the chain specified table (in this case, the filter table). If - A is used, insert (A:Append) at the end.
-
-s: Match source ip, s: source, source.
-
-j: jump means jump. The target of jump can be specified later, such as custom chain. Of course, it is more to jump to "action", such as ACCEPT, DROP, REJECT, etc.
-
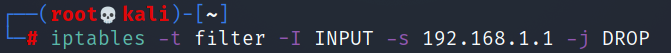
The whole meaning is to add a record to the front (- I) of the "filter" table (- t filter) of the "INPUT" chain (- I INPUT) in iptables. This record will match the request (- s 10.39.129.2) with the source address of "10.39.129.2" and discard the request (- j DROP).
Delete records in iptables
1. Delete by number: as mentioned earlier, when querying the iptables rule list, add -- line numbers, abbreviated as -- line to display the record number. Now we can delete it according to this number:
iptables -t filter -D INPUT (No.)
-t filter specifies that the operation table is the filter table, - D means delete, followed by two parameters, the first is the chain name and the second is the number of the rule to be deleted.
2. Delete according to conditions:
iptables -t filter -D INPUT -s 10.37.129.2 -j DROP
Delete the rule with the source address of "10.37.129.2" and the action of "DROP" in the filter table in the INPUT chain.
3. Empty: - F: the abbreviation of flush. Flush means "flush" and here it means empty. iptables -t filter -F INPUT means to empty all rules in the "filter" table in the "INPUT" chain. If the chain is not specified and the table is not specified, that is, iptables -F is used directly, the rules of all tables in all chains will be cleared.
iptables -F
Modify rules
In fact, it is better to describe it with "replace", because the so-called modification is actually to replace the whole rule with a new rule:
iptables -t filter -R INPUT 1 -s 10.37.129.3 -j ACCEPT
Among them, - R means replace, that is, replace. The whole sentence command means to replace the rule numbered 1 from the filter table in the INPUT chain. The - s 10.37.129.3 -j ACCEPT after number 1 is the new rule to be replaced.
Modify policy:
iptables -P FORWARD DROP
-P: policy, that is, policy. The whole meaning is to set the default rule of the FORWARD chain to DROP, iptables [-t table] -P chain target. This description means that different restrictions can be set according to different tables
iptables -t raw -P OUTPUT ACCEPT iptables -t filter -P OUTPUT DROP
Save rule
-d: Destination is used to match the destination address of the message. Multiple IPS can be specified at the same time (separated by commas, and no spaces are allowed on both sides of the commas), or ip segments can be specified:
iptables -t filter -I OUTPUT -d 192.168.1.111,192.168.1.118 -j DROP iptables -t filter -I INPUT -d 192.168.1.0/24 -j ACCEPT iptables -t filter -I INPUT ! -d 192.168.1.0/24 -j ACCEPT
-p: The protocol type used to match the message, including tcp, udp, udp, icmp, esp, ah, sctp, etc. (icmpv6 and mh are also supported in CentOS 7):
iptables -t filter -I INPUT -p tcp -s 192.168.1.146 -j ACCEPT
#Exclamation mark means "no", that is, all except those matching this condition ACCEPT, but matching this condition does not necessarily mean REJECT or DROP? It depends on whether a rule is specially written for it. If it is not written, the default policy will be used:
iptables -t filter -I INPUT ! -p udp -s 192.168.1.146 -j ACCEPT
In the figure above, use "- S 192.168.1.146 "indicates that the matching condition of - s 192.168.1.146 is reversed, and - s 192.168.1.146 indicates that the matching condition can be met if the IP address of the message source is 192.168.1.146. Use"! " Negative indicates that the condition is satisfied as long as the source IP address of the message is not 192.168.1.146. In the above example, the rule means that the message is accepted as long as the source address of the message sent to the local machine is not 192.168.1.146.
My understanding is: the message source address is ip192 168.1.146 when passing through the INPUT chain, it will be received, but there is only one rule in the INPUT chain, but the message cannot match, so he can only find the default policy. The default policy is ACCEPT, so he will be released. If the default policy is DROP, the message will be discarded
-i: It is used to match the network card interface from which the message flows into the machine. Since the matching condition is only used to match the network card into which the message flows, this option cannot be used in the OUTPUT chain and POSTROUTING chain:
iptables -t filter -I INPUT -p icmp -i eth0 -j DROP iptables -t filter -I INPUT -p icmp ! -i eth0 -j DROP
-o: It is used to match the network card interface from which the message will flow out of the machine. The matching condition is only used to match the network card from which the message will flow out. Therefore, this option cannot be used in the INPUT chain and prior chain.
iptables -t filter -I OUTPUT -p icmp -o eth0 -j DROP iptables -t filter -I OUTPUT -p icmp ! -o eth0 -j DROP
iptables extended matching conditions' – TCP flags'
–sport
It is used to match the source port of tcp protocol message. A colon can be used to specify a continuous port range
iptables -t filter -I OUTPUT -d 192.168.1.146 -p tcp -m tcp --sport 22 -j REJECT iptables -t filter -I OUTPUT -d 192.168.1.146 -p tcp -m tcp --sport 22:25 -j REJECT iptables -t filter -I OUTPUT -d 192.168.1.146 -p tcp -m tcp ! --sport 22 -j ACCEPT
–dport
It is used to match the target port of tcp protocol message. A colon can be used to specify a continuous port range
iptables -t filter -I INPUT -s 192.168.1.146 -p tcp -m tcp --dport 22:25 -j REJECT iptables -t filter -I INPUT -s 192.168.1.146 -p tcp -m tcp --dport :22 -j REJECT iptables -t filter -I INPUT -s 192.168.1.146 -p tcp -m tcp --dport 80: -j REJECT
–tcp-flags
Flag bit used to match the tcp header of the message
iptables -t filter -I INPUT -p tcp -m tcp --dport 22 --tcp-flags SYN,ACK,FIN,RST,URG,PSH SYN -j REJECT iptables -t filter -I OUTPUT -p tcp -m tcp --sport 22 --tcp-flags SYN,ACK,FIN,RST,URG,PSH SYN,ACK -j REJECT iptables -t filter -I INPUT -p tcp -m tcp --dport 22 --tcp-flags ALL SYN -j REJECT iptables -t filter -I OUTPUT -p tcp -m tcp --sport 22 --tcp-flags ALL SYN,ACK -j REJECT
–syn
The request message used to match the new tcp connection is equivalent to using "– tcp flags syn, RST, ACK, fin syn"
iptables -t filter -I INPUT -p tcp -m tcp --dport 22 --syn -j REJECT
iptables extension module
tcp extension module
-p tcp -m tcp --sport is used to match the source port of tcp protocol messages. A colon can be used to specify a continuous port range (- p protocol, - m:match, which refers to the matching module. Many people may think it is the abbreviation of module, but it is actually the abbreviation of match, - sport: source port)- p tcp -m tcp --dport is used to match the target port of tcp protocol messages. A colon can be used to specify a continuous port range (- - dport 80:88)
iptables -t filter -I OUTPUT -d 192.168.1.146 -p tcp -m tcp --sport 22 -j REJECT iptables -t filter -I INPUT -s 192.168.1.146 -p tcp -m tcp --dport 22:25 -j REJECT iptables -t filter -I INPUT -s 192.168.1.146 -p tcp -m tcp --dport :22 -j REJECT iptables -t filter -I INPUT -s 192.168.1.146 -p tcp -m tcp --dport 80: -j REJECT iptables -t filter -I OUTPUT -d 192.168.1.146 -p tcp -m tcp ! --sport 22 -j ACCEPT
In addition, the TCP extension module also has the - TCP flags option, which can be matched according to the "identification bit" of the TCP header.
multiport extension module
-p tcp -m multiport --sports is used to match the source port of the message. Multiple discrete port numbers can be specified, and the ports are separated by "comma"- p udp -m multiport --dports is used to match the target port of the message. Multiple discrete port numbers can be specified, and the ports are separated by "comma":
iptables -t filter -I OUTPUT -d 192.168.1.146 -p udp -m multiport --sports 137,138 -j REJECT iptables -t filter -I INPUT -s 192.168.1.146 -p tcp -m multiport --dports 22,80 -j REJECT iptables -t filter -I INPUT -s 192.168.1.146 -p tcp -m multiport ! --dports 22,80 -j REJECT iptables -t filter -I INPUT -s 192.168.1.146 -p tcp -m multiport --dports 80:88 -j REJECT iptables -t filter -I INPUT -s 192.168.1.146 -p tcp -m multiport --dports 22,80:88 -j REJECT iprange Extension module
iprange extension module
Using the iprange extension module, you can specify "a continuous IP address range" to match the source address or destination address of the message. There are two extension matching conditions available in the iprange extension module: – -- SRC range (matching source address range) - -- DST range (matching destination address range)
iptables -t filter -I INPUT -m iprange --src-range 192.168.1.127-192.168.1.146 -j DROP
string extension module
Suppose we're visiting“ http://192.168.1.146/index.html ”, when the "XXOO" character is included in "index.html", it will be matched by the following rules:
iptables -t filter -I INPUT -m string --algo bm --string "XXOO" -j REJECT
-m string: indicates the use of string module -- algo bm: indicates the use of bm algorithm to match index HTML string, "algo" is the abbreviation of "algorithm", and there is another algorithm called "kmp", so -- algo can specify two values, bm or kmp. It seems that bm algorithm is faster.
time extension module
We can match the message according to the time period area through the time extension module. If the arrival time of the message is within the specified time range, the matching conditions are met.
I want self-discipline. I can't see the web page from 9 a.m. to 6 p.m. every day:
iptables -t filter -I INPUT -p tcp --dport 80 -m time --timestart 09:00:00 --timestop 18:00:00 -j REJECT iptables -t filter -I INPUT -p tcp --dport 443 -m time --timestart 09:00:00 --timestop 18:00:00 -j REJECT
You can't see the web page on Saturday and Sunday:
iptables -t filter -I INPUT -p tcp --dport 80 -m time --weekdays 6,7 -j REJECT iptables -t filter -I INPUT -p tcp --dport 443 -m time --weekdays 6,7 -j REJECT
--weekdays can use 1-7 to represent 7 days of the week, and the abbreviations of the week can be used to specify the matching: Mon, Tue, Wed, Thu, Fri, Sat, Sun.
Match the 22nd and 23rd of each month:
iptables -t filter -I INPUT -p tcp --dport 80 -m time --monthdays 22,23 -j REJECT
connlimit module
Using the connlimit extension module, you can limit the number of links from each IP address to the server side at the same time. Note: we don't need to specify the IP. It defaults to "each client IP", that is, the limit on the number of concurrent connections of a single IP.
Limit the maximum number of 22 ports (ssh default port) connections to 2;
iptables -t filter -I INPUT -p tcp --dport 22 -m connlimit --connlimit-above 2 -j REJECT
limit extension module
The limit module is used for speed limiting and is used to limit the "number of incoming packets per unit time".
ping packets are released every 6 bit seconds (since 1 minute is 60 seconds, 10 packets per minute is equivalent to 1 packet every 6 seconds):
iptables -t filter -I INPUT -p icmp -m limit --limit 10/minite -j ACCEPT
--In addition to minite, the units behind limit can also be second, hour and day
udp extension module
There are only two matching conditions available in the udp extension module, namely -- sport and -- dport, that is, the source port and target port of the matching message.
Release ports 137 and 138 of samba service:
iptables -t filter -I INPUT -p udp -m udp --dport 137 -j ACCEPT iptables -t filter -I INPUT -p udp -m udp --dport 138 -j ACCEPT
icmp extension module
ping uses the icmp Protocol. It is assumed that all messages of the icmp Protocol should be prohibited from entering the machine (as mentioned earlier, we can omit the use of - m icmp to specify the icmp module, because if it is not specified, the module corresponding to the protocol specified by - p will be used by default):
iptables -t filter -I INPUT -p icmp -j REJECT