Iptables firewall is used to manage packet filtering and NAT rules. Iptables comes with all Linux distributions. Understanding how to set up and configure iptables will help you manage your Linux firewall effectively.
Iptables tool is used to manage Linux firewall rules. At first glance, iptables can look complex (or even confusing). However, once you understand the basic knowledge of iptables working principle and its structure, it will be easy to read and write iptables firewall rules.
This article is part of an ongoing iptables tutorial series. This is the first article in the series.
This article explains the structure of iptables and explains the basics of iptables tables, chains, and rules.
Multiple tables may be included on a high-level iptables. A table may contain multiple chains. Chains can be built-in or user-defined. The chain may contain multiple rules. Rules are defined for packets.
Therefore, the structure is iptables - > tables - > chains - > rules. This is defined in the following figure.
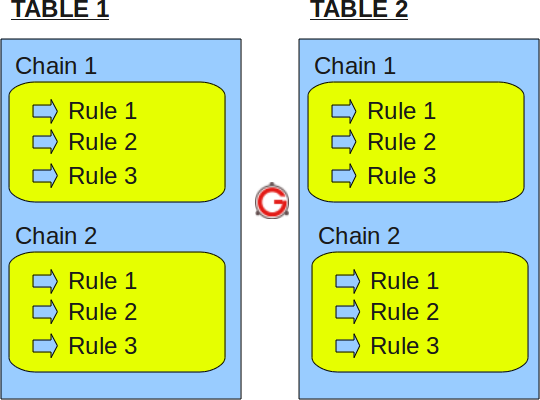
Figure: IPTables table, chain, and rule structure
Again, a table is a pile of chains, and a chain is a pile of firewall rules.
1. Iptables tables and chains
IPTables has the following four built-in tables.
1. Filter table
Filters are the default table for iptables. So if you don't define your own table, you will use the filter table. Iptables filter tables have the following built-in chains.
- INPUT chain – incoming firewall. Packets used to reach the local server.
- OUTPUT chain – outgoing from firewall. Packets that are generated locally and leave the local server.
- FORWARD chain – packets from another NIC on the local server. For packets routed through the local server.
2. NAT table
iptable's NAT table has the following built-in chains.
- Routing chain – changes packets before routing. That is, packet conversion occurs immediately after the packet arrives at the system (and before routing). This helps to translate the destination IP address of the packet into something that matches the route on the local server. This is for DNAT (target NAT).
- POSTROUTING chain – changes packets after routing. That is, packet conversion occurs when the packet leaves the system. This helps to translate the source IP address of the packet into something that may match the route on the target server. This is for SNAT (source NAT).
- OUTPUT chain – NAT of locally generated packets on the firewall.
3. Mangle table
The Mangle table of iptables is used for specialized packet changes. This changes the QOS bit in the TCP header. The Mangle table has the following built-in chains.
- Pre routing chain
- Output chain
- Forward chain
- Input chain
- POSTROUTING chain
4. Original table
The Raw table of Iptable is used to configure exceptions. The original table has the following built-in chains.
- Pre routing chain
- Output chain
The following figure shows three important tables in iptables.
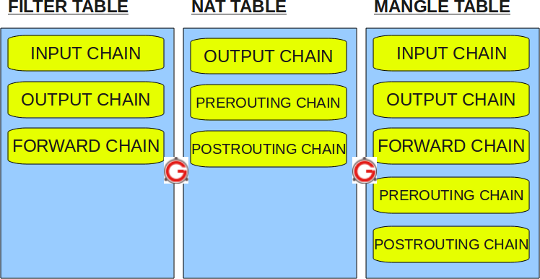
Figure: IPTables built-in table
2, IPTABLES rule
Here are the key points to remember about iptables rules.
- The rule contains a standard and a goal.
- If the conditions match, go to the rule specified in the target (or) execute the special value mentioned in the target.
- If the conditions do not match, proceed to the next rule.
target value
The following are possible special values that you can specify in the target.
- ACCEPT – the firewall will ACCEPT packets.
- DROP – the firewall will DROP packets.
- QUEUE – the firewall delivers packets to user space.
- RETURN – the firewall will stop executing the next set of rules in the current chain for this packet. Control is returned to the call chain.
If you execute iptables – list (or) service iptables status, you will see all available firewall rules on the system. The following iptable example shows that there are no firewall rules defined on this system. As you can see, it displays a default input table with default input chains, forward chains, and output chains.
# iptables -t filter --list Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination
Do the following to view the mangle table.
# iptables -t mangle --list
Do the following to view the nat table.
# iptables -t nat --list
Do the following to view the original table.
# iptables -t raw --list
Note: if you do not specify the - t option, it displays the default filter table. Therefore, the following two commands are the same.
# iptables -t filter --list (or) # iptables --list
The following iptable example shows some rules defined in the input, forward, and output chains of the filter table.
# iptables --list Chain INPUT (policy ACCEPT) num target prot opt source destination 1 RH-Firewall-1-INPUT all -- 0.0.0.0/0 0.0.0.0/0 Chain FORWARD (policy ACCEPT) num target prot opt source destination 1 RH-Firewall-1-INPUT all -- 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT) num target prot opt source destination Chain RH-Firewall-1-INPUT (2 references) num target prot opt source destination 1 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 2 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmp type 255 3 ACCEPT esp -- 0.0.0.0/0 0.0.0.0/0 4 ACCEPT ah -- 0.0.0.0/0 0.0.0.0/0 5 ACCEPT udp -- 0.0.0.0/0 224.0.0.251 udp dpt:5353 6 ACCEPT udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:631 7 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:631 8 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 9 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 10 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
The rules in the iptables – list command output contain the following fields:
- num - number of rules in a specific chain
- Target – the special target variable we discussed above
- prot - Protocol. tcp, udp, icmp, etc,
- opt – special options for this particular rule.
- Source – the source IP address of the packet
- Destination - the destination IP address of the packet