Istio 1.6.3 released. Istio is an open source project jointly developed by Google, IBM and Lyft, aiming to provide a unified way of microservice connection, security, management and monitoring. Specifically, istio is an open source services grid platform, which ensures that microservices are interconnected in a specified way when they handle failures.
Update content
- Fixed a problem that the operator could not recreate after the monitoring resource was deleted
- Fixed Istio crash due to message: proto.Message is * client.QuotaSpecBinding , not * client.QuotaSpecBinding
- Added to k8s.v1 cni.cncf.io/networks Support for annotations
- SidecarInjectionSpec updated from Values.global Read imagePullSecret
- Updated horizontal split to skip gateway resolving hostname
- Fixed istioctl experimental metrics, marking error response code as erros only
- Updated istioctl analyze to sort output formats
- Updated gateway to use proxyMetadata
- Prometheus Sidecar updated to use proxyMetadata
- Enable gateway.runAsRoot Invalid configuration removed from PodSecurityContext on
Upgrade update
- Update Description: https://istio.io/latest/news/releases/1.6.x/announcing-1.6.3/
- Upgrade instructions: https://istio.io/latest/news/releases/1.6.x/announcing-1.6/upgrade-notes/
express setup
Download:
$ curl -L https://istio.io/downloadIstio | sh - $ cd istio-1.6.3 # Add to ~/.profile or .bash... $ export PATH=$PWD/bin:$PATH
Installation:
$ istioctl install --set profile=demo ✔ Istio core installed ✔ Istiod installed ✔ Egress gateways installed ✔ Ingress gateways installed ✔ Addons installed ✔ Installation complete # Enable auto-injection $ kubectl label namespace default istio-injection=enabled namespace/default labeled
Deployment Demo:
$ kubectl apply -f samples/bookinfo/platform/kube/bookinfo.yaml
Check operation status:
$ kubectl exec -it $(kubectl get pod -l app=ratings -o jsonpath='{.items[0].metadata.name}') -c ratings -- curl productpage:9080/productpage | grep -o "<title>.*</title>" <title>Simple Bookstore App</title>
Publish service to external access:
$ kubectl apply -f samples/bookinfo/networking/bookinfo-gateway.yaml gateway.networking.istio.io/bookinfo-gateway created virtualservice.networking.istio.io/bookinfo created
Determine the IP and port of Igress:
$ kubectl get svc istio-ingressgateway -n istio-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE istio-ingressgateway LoadBalancer 172.21.109.129 130.211.10.121 80:31380/TCP,443:31390/TCP,31400:31400/TCP 17h
Set environment:
$ export INGRESS_HOST=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.status.loadBalancer.ingress[0].ip}') $ export INGRESS_PORT=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports[?(@.name=="http2")].port}') $ export SECURE_INGRESS_PORT=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports[?(@.name=="https")].port}') $ export GATEWAY_URL=$INGRESS_HOST:$INGRESS_PORT $ echo $GATEWAY_URL 192.168.99.100:32194
Visit the demonstration service:
$ echo http://$GATEWAY_URL/productpage
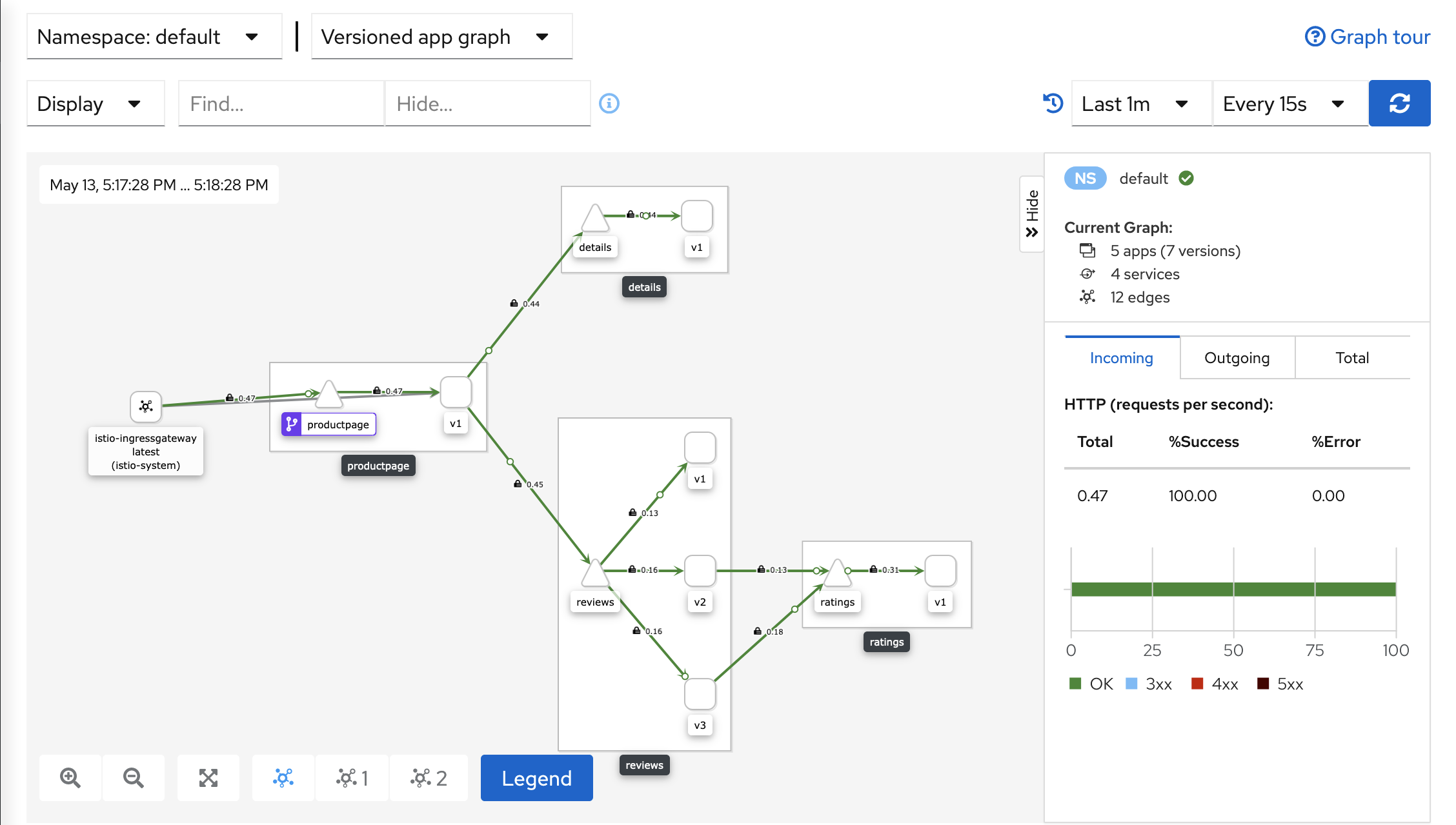
Open the Kiali panel. Both the account and password are admin.
$ istioctl dashboard kiali
As follows:
Related links
- Istio website, Click to view
- Istio download, Click download
- Istio resources, https://my.oschina.net/u/2306127?q=istio