1. url: https://weibo.com/
2. target: Login
3. Analysis. Due to the need to fill in the verification code, this article only analyzes the part of cracking the user name and password encryption, without verification code identification.
3.1 according to the old rule, F12, enter an account password and click login to see what requests have been initiated. Find the post request (usually the login is post request). After finding the login request, let's see what parameters are needed. The encrypted parameters are basically as follows:
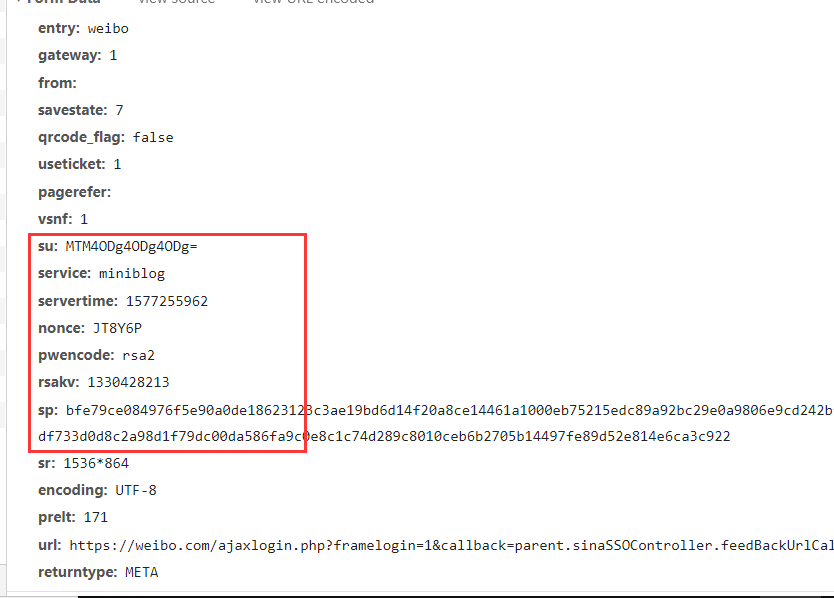
The parameters su, servertime, nonce, rsakv, sp are encrypted. And servertime is the timestamp, over. Both nonce and rsakv can be found in the response of the previous request. Only su and sp are left. Guess an account and a password. Let's break sp first.
3.2 it must be inconvenient to search sp directly. If the target is too large, search the parameter pwencode which looks relevant and has strong uniqueness. It's also known that the name is related to the password code, so search it.
Soon they found the following:
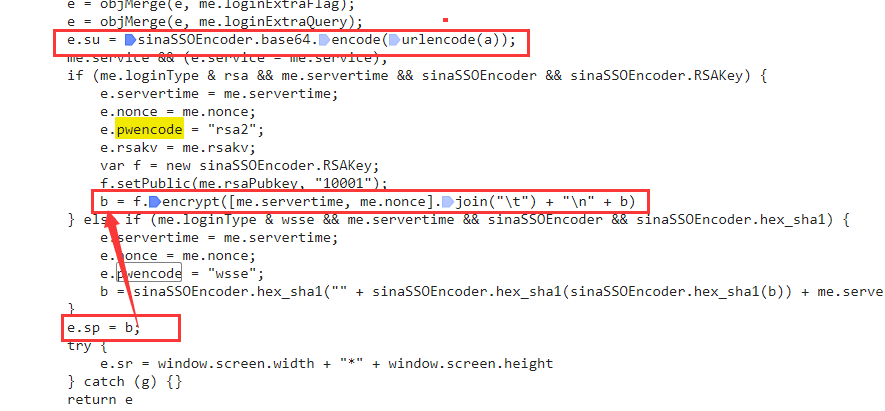
3.3 interrupt point debugging. su is su, and b is sp.
3.4 deduct js code process, omitted. Just one function at a time.
4. python code:
from afterWork.config import proxies, userAgent import requests import json import execjs import time import re import random def getJsCode(): with open('jsCode.js', 'r') as f: jsCode = f.read() return jsCode def getSu(ctx, account): su = ctx.call('getUser', account) # print(su) return su def getServerTimeNoncePubkey(su): # print('1577263612028') ts = re.sub(r'\.', '', str(time.time())) ts = ts[:13] data = { 'entry': 'weibo', 'callback': 'sinaSSOController.preloginCallBack', 'su': su, 'rsakt': 'mod', 'checkpin': '1', 'client': 'ssologin.js(v1.4.15)', '_': ts } res = requests.get(url='https://login.sina.com.cn/sso/prelogin.php', params=data) # print(res.text) # print(json.loads(res.text.lstrip('sinaSSOController.preloginCallBack(').strip(')'))) nonce = json.loads(res.text.lstrip('sinaSSOController.preloginCallBack(').strip(')'))['nonce'] pubkey = json.loads(res.text.lstrip('sinaSSOController.preloginCallBack(').strip(')'))['pubkey'] servertime = json.loads(res.text.lstrip('sinaSSOController.preloginCallBack(').strip(')'))['servertime'] rsakv = json.loads(res.text.lstrip('sinaSSOController.preloginCallBack(').strip(')'))['rsakv'] pcid = json.loads(res.text.lstrip('sinaSSOController.preloginCallBack(').strip(')'))['pcid'] return servertime, pubkey, nonce, rsakv, ts, pcid def getLoginData(su, serverTime, nonce, rsakv, sp, ts): # print('1577263612028') ts = re.sub(r'\.', '', str(time.time()))[:-4] # url='https://login.sina.com.cn/sso/login.php?client=ssologin.js(v1.4.15)&_={}'.format(ts) headers = { 'User-Agent': 'Opera/9.80 (Windows NT 6.0) Presto/2.12.388 Version/12.14', 'Host': 'login.sina.com.cn', 'Referer': 'https://www.weibo.com/login.php', } data = { 'entry': 'sso', 'gateway': '1', 'from': 'null', 'savestate': '30', 'useticket': '0', 'pagerefer': 'https://login.sina.com.cn/sso/login.php?client=ssologin.js(v1.4.19)', 'vsnf': '1', 'su': su, 'service': 'sso', 'servertime': serverTime, 'nonce': nonce, 'pwencode': 'rsa2', 'rsakv': rsakv, 'sp': sp, 'sr': '1536*864', 'encoding': 'UTF-8', 'cdult': '3', 'domain': 'sina.com.cn', 'prelt': '113', 'returntype': 'TEXT', } res = requests.post(url='https://login.sina.com.cn/sso/login.php?client=ssologin.js(v1.4.15)&_={}'.format(ts), data=data, headers=headers, timeout=10) res.encoding = 'GBK' # print(res.text) loginResult = json.loads(res.text) print(loginResult) return def getSp(ctx, pw, serverTime, nonce, pubKey): sp = ctx.call('getPw', pw, serverTime, nonce, pubKey) # print(sp) return sp def mainFun(): account = 'Your account number' pw = 'Your password' ctx = execjs.compile(getJsCode()) su = getSu(ctx, account) serverTime, pubKey, nonce, rsakv, ts, pcid = getServerTimeNoncePubkey(su) sp = getSp(ctx, pw, serverTime, nonce, pubKey) getLoginData(su, serverTime, nonce, rsakv, sp, ts) # login(account, sp, pcid, serverTime, nonce) if __name__ == '__main__': mainFun()
Result:
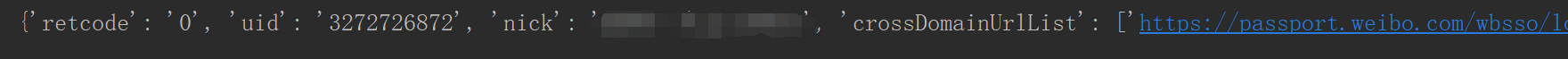
At this point, the login has been completed. You can use session session to carry cookie s to access some information that requires login.
Learn to communicate, not for other purposes.