Summary
The access control process of API Server in Kuberntes is illustrated as follows:
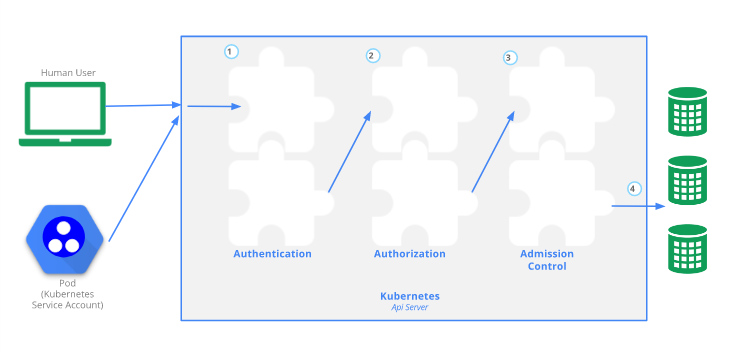
In Kubernetes, authorization is a step after authentication. Authorization is to determine whether a user (ordinary user or Service Account) has the right to request the Kubernetes API to do something.
Previously, the authorization strategy in Kubernetes was mainly ABAC(Attribute-Based Access Control). For ABAC, Kubernetes is difficult to implement, and requires SSH and root file system access rights of Master Node. API Server needs to be restarted after the authorization policy changes.
In Kubernetes 1.6, RBAC(Role-Based Access Control) entered the Beta phase of role-based access control. RBAC access control policies can be configured using kubectl or Kubernetes API. Using RBAC, users can be authorized directly to have authorization management rights, so that they no longer need to touch Master Node directly. RBAC is mapped to API resources and operations in Kubernetes.
Resource object of RBAC API
In Kubernetes 1.6, RBAC is enabled for API Server by starting parameter - authorization-mode=RBAC.API Overview.
The 1.6 version of Kubernetes cluster initialized with kubeadm has opened RBAC by default for API Server. You can view the static Pod definition file of API Server on Master Node:
cat /etc/kubernetes/manifests/kube-apiserver.yaml | grep RBAC- --authorization-mode=RBAC
The RBAC API defines four resource objects to describe the connection privileges between users and resources in RBAC:
- Role
- ClusterRole
- RoleBinding
- ClusterRoleBinding
Role and Cluster Role
Role is a collection of permissions. Role is a resource defined under a Namespace and used under this specific Namespace. Cluster Role is similar to Role, but Cluster Role is used throughout the cluster.
Let's use kubectl to print Role and CulturRole in the Kubernetes cluster:
kubectl get roles --all-namespacesNAMESPACE NAME AGEkube-public system:bootstrap-signer-clusterinfo 6dkube-public system:controller:bootstrap-signer 6dkube-system extension-apiserver-authentication-reader 6dkube-system system:controller:bootstrap-signer 6dkube-system system:controller:token-cleaner 6d
kubectl get ClusterRolesNAME AGEadmin 6dcluster-admin 6dedit 6dflannel 5dsystem:auth-delegator 6dsystem:basic-user 6dsystem:controller:attachdetach-controller 6d......system:kube-aggregator 6dsystem:kube-controller-manager 6dsystem:kube-dns 6dsystem:kube-scheduler 6dsystem:node 6dsystem:node-bootstrapper 6dsystem:node-problem-detector 6dsystem:node-proxier 6dsystem:persistent-volume-provisioner 6dview 6d
You can see that many Roles and Cluster Roles have been built in or created in the Kubernetes cluster created previously.
Next, create a Role named pod-reader in the default namespace. The role-pord-reader.yaml file is as follows:
kind: RoleapiVersion: rbac.authorization.k8s.io/v1beta1metadata:namespace: defaultname: pod-readerrules:- apiGroups: [""] # "" indicates the core API groupresources: ["pods"]verbs: ["get", "watch", "list"]
kubectl create -f role-pord-reader.yamlrole "pod-reader" createdkubectl get rolesNAME AGEpod-reader 1m
Note that RBAC is still in Beta phase in Kubernetes 1.6, so the API belongs to rbac.authorization.k8s.io, and the apiVersion above is rbac.authorization.k8s.io/v1beta1.
Here's another definition file for ClusterRole:
kind: ClusterRoleapiVersion: rbac.authorization.k8s.io/v1beta1metadata:# "namespace" omitted since ClusterRoles are not namespacedname: secret-readerrules:- apiGroups: [""]resources: ["secrets"]verbs: ["get", "watch", "list"]
Role Binding and Cluster Role Binding
RoleBinding binds Role to Subject, the main body of the account, so that Subject inherits Role's permissions under namespace. Cluster Role Binding binds Cluster Role to Subject, allowing Subject to integrate the privileges of Cluster Role across the cluster.
Account Subject is still called "user" here, including group, user and Service Account.
kubectl get rolebinding --all-namespacesNAMESPACE NAME AGEkube-public kubeadm:bootstrap-signer-clusterinfo 6dkube-public system:controller:bootstrap-signer 6dkube-system system:controller:bootstrap-signer 6dkube-system system:controller:token-cleaner 6d
kubectl get clusterrolebindingNAME AGEcluster-admin 6dflannel 6dkubeadm:kubelet-bootstrap 6dkubeadm:node-proxier 6dsystem:basic-user 6dsystem:controller:attachdetach-controller 6dsystem:controller:certificate-controller 6d......system:controller:ttl-controller 6dsystem:discovery 6dsystem:kube-controller-manager 6dsystem:kube-dns 6dsystem:kube-scheduler 6dsystem:node 6dsystem:node-proxier 6d
In fact, a RoleBinding can refer to either a role under the same namespace or a Cluster Role, and when RoleBinding refers to Cluster Role, the user's inherited rights are limited to the namespace where RoleBinding resides.
kind: RoleBindingapiVersion: rbac.authorization.k8s.io/v1beta1metadata:name: read-podsnamespace: defaultsubjects:- kind: Username: janeapiGroup: rbac.authorization.k8s.ioroleRef:kind: Rolename: pod-readerapiGroup: rbac.authorization.k8s.io
kind: RoleBindingapiVersion: rbac.authorization.k8s.io/v1beta1metadata:name: read-secretsnamespace: development # This only grants permissions within the "development" namespace.subjects:- kind: Username: daveapiGroup: rbac.authorization.k8s.ioroleRef:kind: ClusterRolename: secret-readerapiGroup: rbac.authorization.k8s.io
Default Role and Role Binding in Kubernetes
API Server has created a series of Cluster Roles and Cluster Role Binding. The names in these resource objects begin with system: to indicate that the resource object belongs to the Kubernetes system infrastructure. That is to say, the default cluster role of RBAC has been covered enough so that the cluster can be completely in place. RBAC runs under management. Modifying these resource objects may have unknown consequences, such as defining the permissions of the kubelet process for the system:node ClusterRole, which may cause the kubelet to fail to work if the role is modified.
You can use the label kubernetes.io/bootstrapping=rbac-defaults to view the default Cluster Role and Cluster Role Binding:
kubectl get clusterrole -l kubernetes.io/bootstrapping=rbac-defaultsNAME AGEadmin 6dcluster-admin 6dedit 6dsystem:auth-delegator 6dsystem:basic-user 6dsystem:controller:attachdetach-controller 6dsystem:controller:certificate-controller 6d......system:node-problem-detector 6dsystem:node-proxier 6dsystem:persistent-volume-provisioner 6dview 6d
kubectl get clusterrolebinding -l kubernetes.io/bootstrapping=rbac-defaultsNAME AGEcluster-admin 6dsystem:basic-user 6dsystem:controller:attachdetach-controller 6dsystem:controller:certificate-controller 6dsystem:controller:cronjob-controller 6dsystem:controller:daemon-set-controller 6dsystem:controller:deployment-controller 6d......system:discovery 6dsystem:kube-controller-manager 6dsystem:kube-dns 6dsystem:kube-scheduler 6dsystem:node 6dsystem:node-proxier 6d
Detailed privilege information about these roles can be viewed Default Roles and Role Bindings
Original text http://blog.frognew.com/2017/04/kubernetes-1.6-rbac.html