summary
compatibility: https://kuboard.cn/install/v3/install.html#kuboard-v3-x-version description
Official website address: https://kuboard.cn/
Feature introduction
- Multiple authentication methods
Kuboard can use the built-in user library, gitlab / github single sign on or LDAP user library for authentication to avoid the trouble caused by the administrator distributing the Token of ServiceAccount to ordinary users. When using the built-in user library, the administrator can configure the user's password policy, password expiration time and other security settings. - Multi cluster management
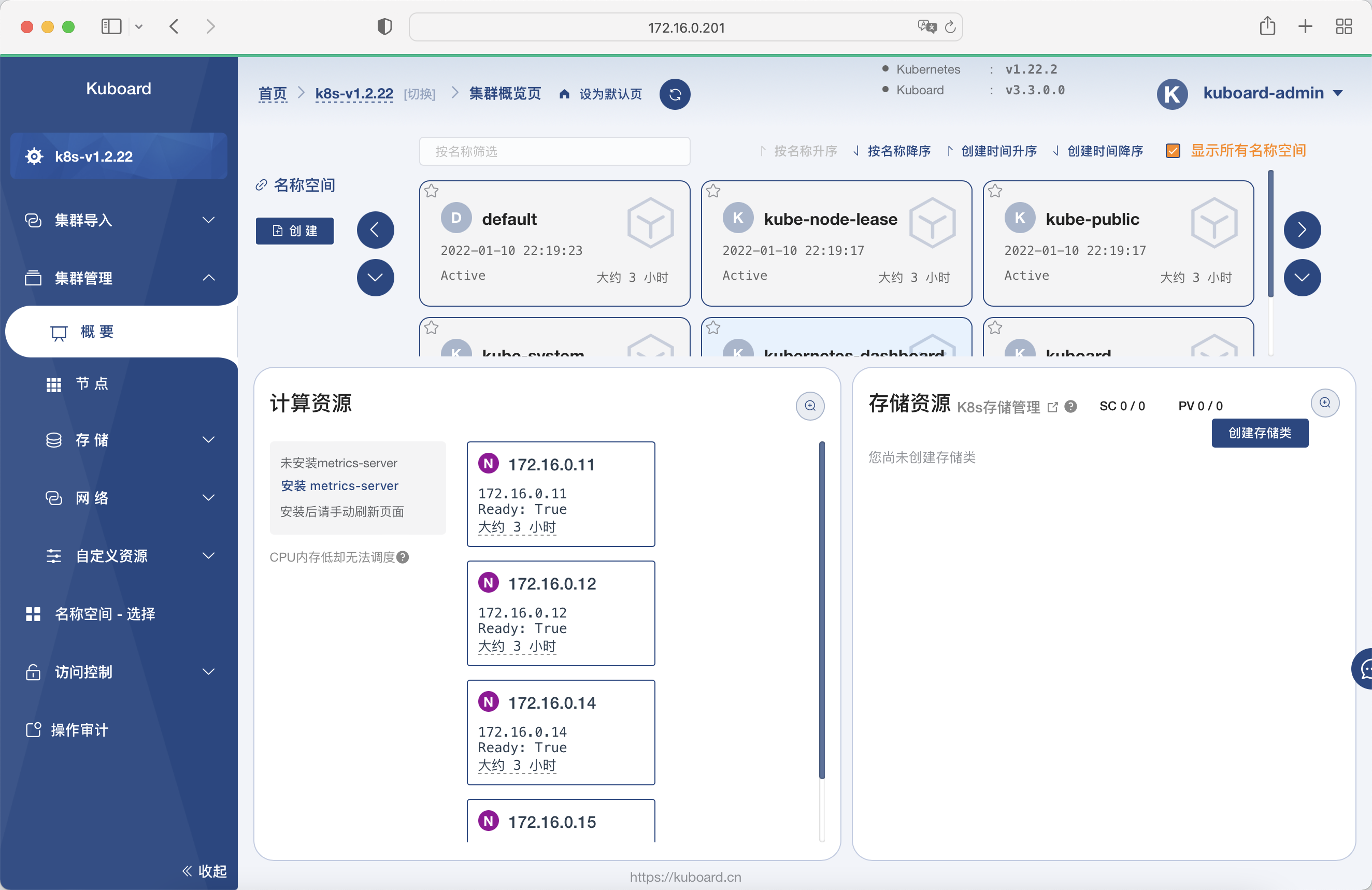
Administrators can import multiple Kubernetes clusters into Kuboard, and assign permissions of different clusters / namespaces to specified users or user groups through permission control. - Micro service layered display
In the namespace summary page of Kuboard, the workload is divided into different layers in the classic micro service layering method, which more intuitively shows the structure of the micro service architecture, and the namespace layout can be customized for each namespace. - Visual presentation of workload
Kuboard reasonably organizes the historical version of Deployment, the Pod list, Pod related events and container information in the same page, which can help users diagnose problems and perform various related operations most quickly. - Workload editing
Kuboard provides a graphical workload editing interface. Users can easily complete the task of arranging containers without falling into cumbersome YAML file details. Kubernetes object types supported include: Node, Namespace, Deployment, StatefulSet, DaemonSet, Secret, ConfigMap, Service, progress, StorageClass, PersistentVolumeClaim, LimitRange, ResourceQuota, ServiceAccount, Role, RoleBinding, ClusterRole, ClusterRoleBinding, CustomResourceDefinition Various common kubernetes objects such as CustomResource, - Storage type support
In Kuboard, you can easily connect common storage types such as NFS and CephFS, and support capacity expansion and snapshot operations on CephFS type storage volume declarations. - Rich interoperability
It can provide many interoperability means that are usually only provided in the kubectl command line interface, such as:- Top Nodes / Top Pods
- Container logs, terminals
- File browser of container (supports downloading files from container and uploading files to container)
- KuboardProxy (the function of kubectl proxy can be provided in the browser)
- Suite extension
Kuboard provides the necessary suite library, so that users can expand the management capability of the cluster according to their own needs. Currently available kits are:- The resource layer monitoring suite provides the monitoring capability of K8S cluster based on Prometheus / Grafana, which can monitor the usage of CPU, memory, network, disk and other resources of objects at all levels such as cluster, node, workload and container group;
- Log aggregation suite, which realizes log aggregation based on Grafana / Loki / Promtail;
- Storage volume browser to view and operate the contents in the storage volume;
- Alarm configuration
You can directly configure the resource layer monitoring suite to send alarm messages through the interface:- Support sending alarm messages by email and wechat;
- Support alarm routing configuration;
- Support alarm rule configuration, etc;
- Operational audit
Kuboard supports the functions of operation audit:- Audit the operations performed by users through Kuboard interface and Kuboard API;
- User defined audit rules;
docker deployment
You can also use mirror SWR cn-east-2. myhuaweicloud. COM / kuboard / kuboard: V3, you can complete the image download faster.
KUBOARD_ENDPOINT = login address
Kuboard does not need to be in the same network segment as K8S. Kuboard Agent can even access Kuboard Server through agent
Parameter interpretation
It is recommended that you save this command as a shell script, such as start Kuboard Sh. when upgrading or restoring Kuboard later, you need to know the parameters used when installing Kuboard initially through this command;
In line 4, map Kuboard Web port 80 to port 80 of the host (you can select other ports of the host according to your own situation);
In line 5, map the port 10081/tcp of the Kuboard Agent Server to the port 10081 of the host (you can select other ports of the host according to your situation);
Line 6, specify KUBOARD_ENDPOINT is http: / / Intranet IP , if you modify this parameter later, you need to delete the imported Kubernetes cluster from Kuboard and import it again;
Line 7, specify kuboard_ AGENT_ The port of server is 10081. This parameter should be consistent with the host port in line 5. Modifying this parameter will not change the port 10081 listening in the container. For example, if line 5 is - p 30081:10081/tcp, line 7 should be modified to - e KUBOARD_AGENT_SERVER_TCP_PORT="30081";
In line 8, map the persistent data / data directory to the / root / kuboard data path of the host. Please adjust the host path according to your own situation;
sudo docker run -d \ --restart=unless-stopped \ --name=kuboard \ -p 80:80/tcp \ -p 10081:10081/tcp \ -e KUBOARD_ENDPOINT="http://172.16.0.201:80" \ -e KUBOARD_AGENT_SERVER_TCP_PORT="10081" \ -v /data/kuboard-data:/data \ eipwork/kuboard:v3
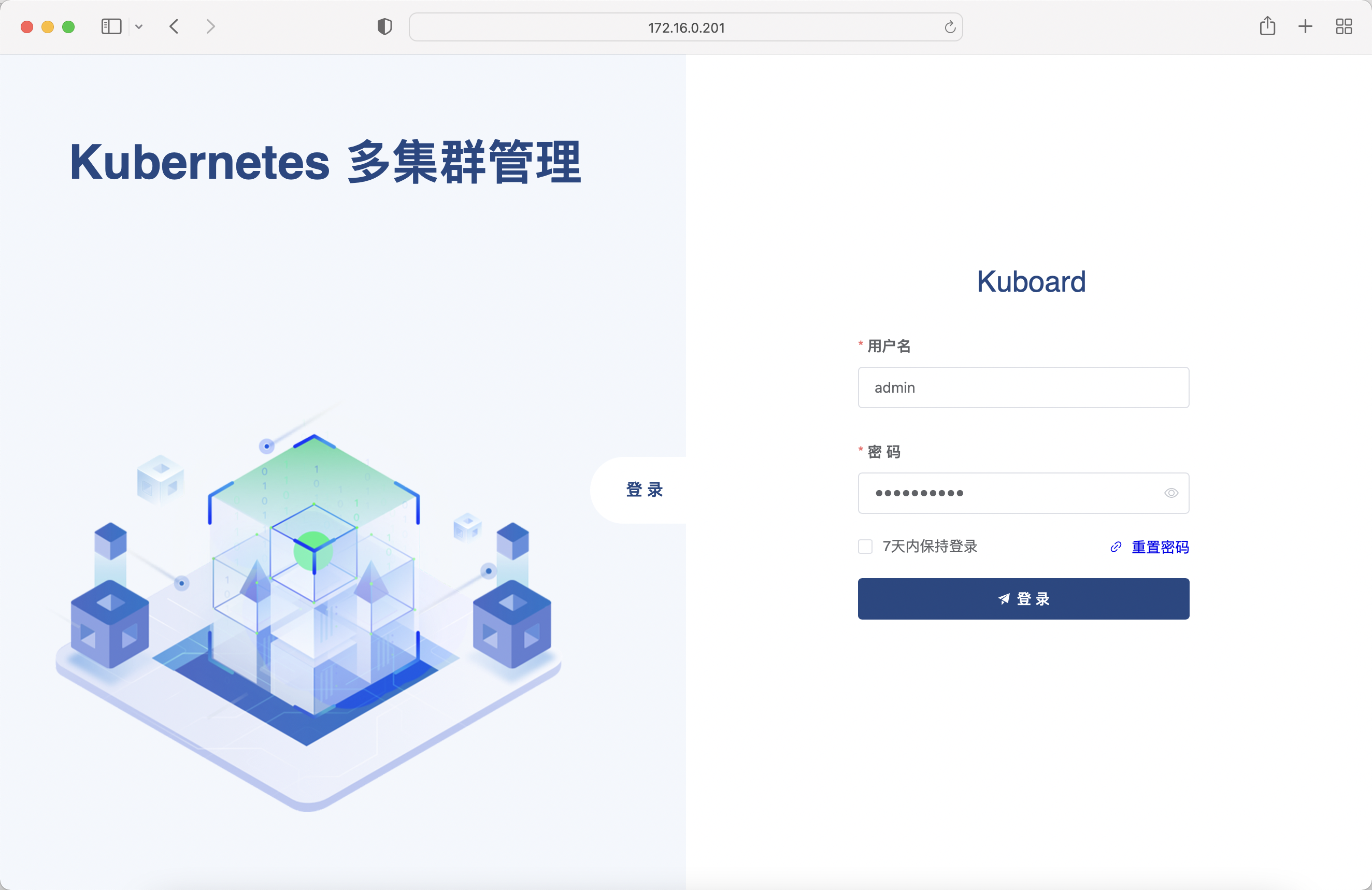
Login verification
Default user name: admin
Default password: Kuboard123
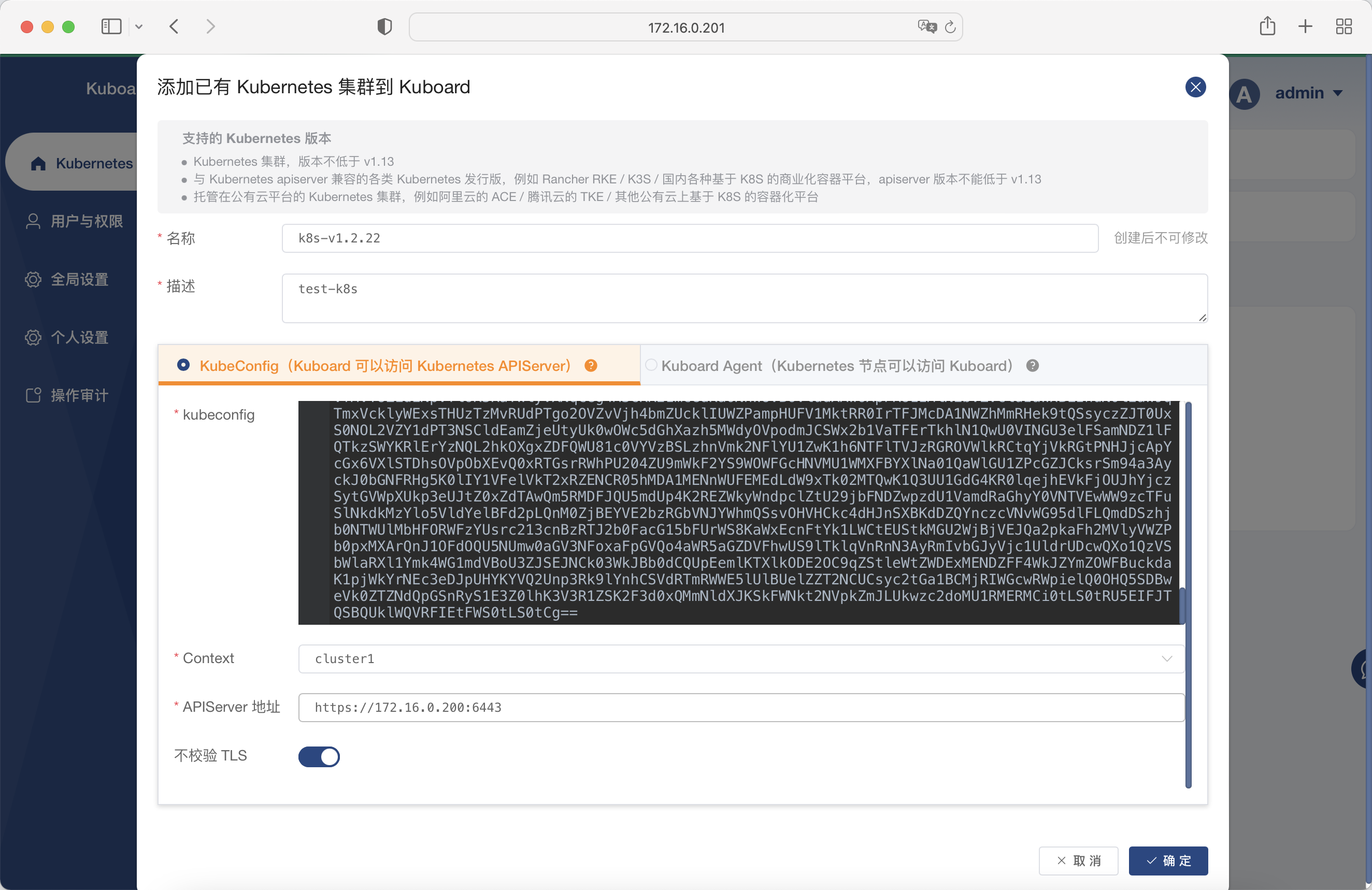
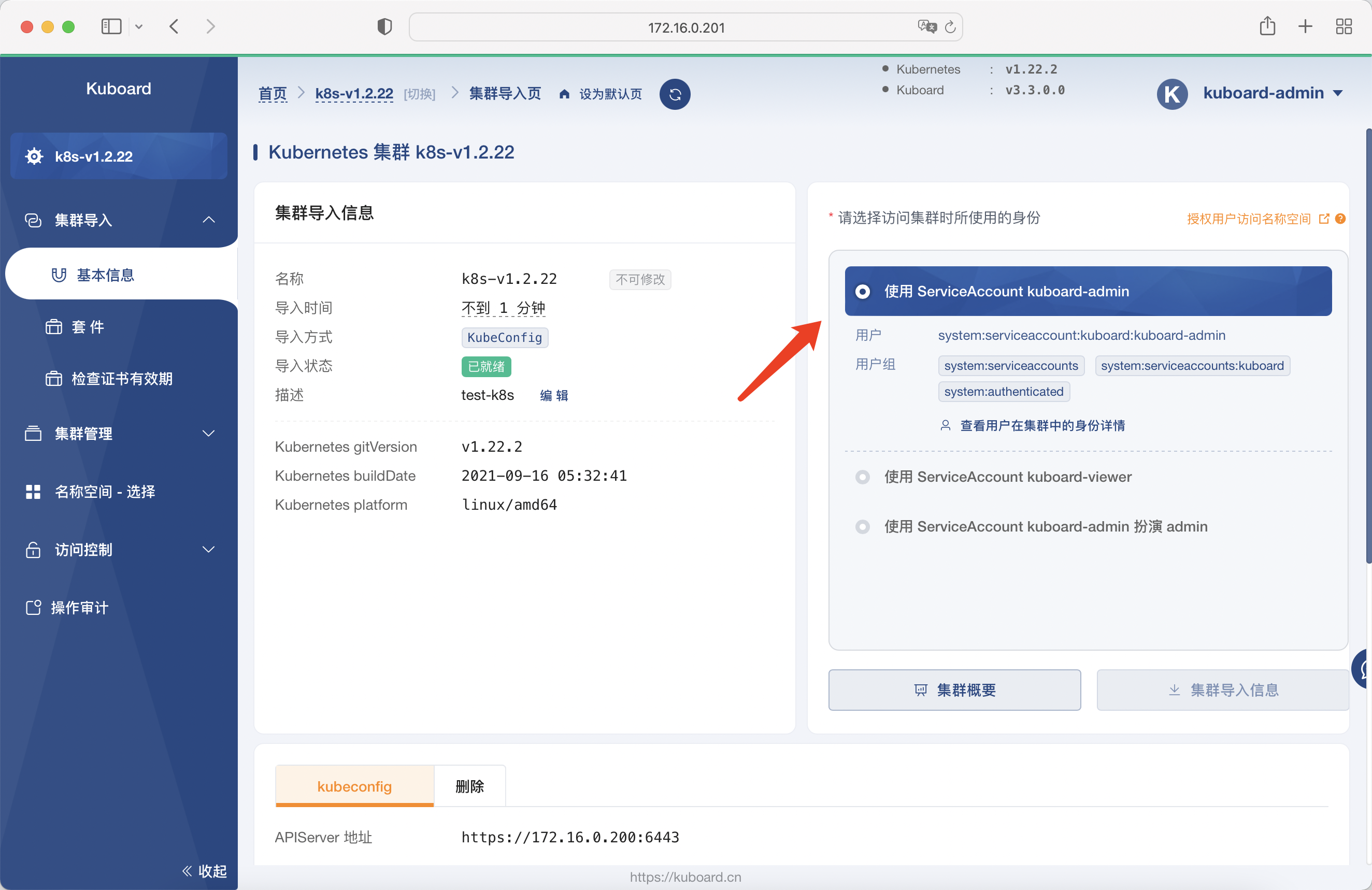
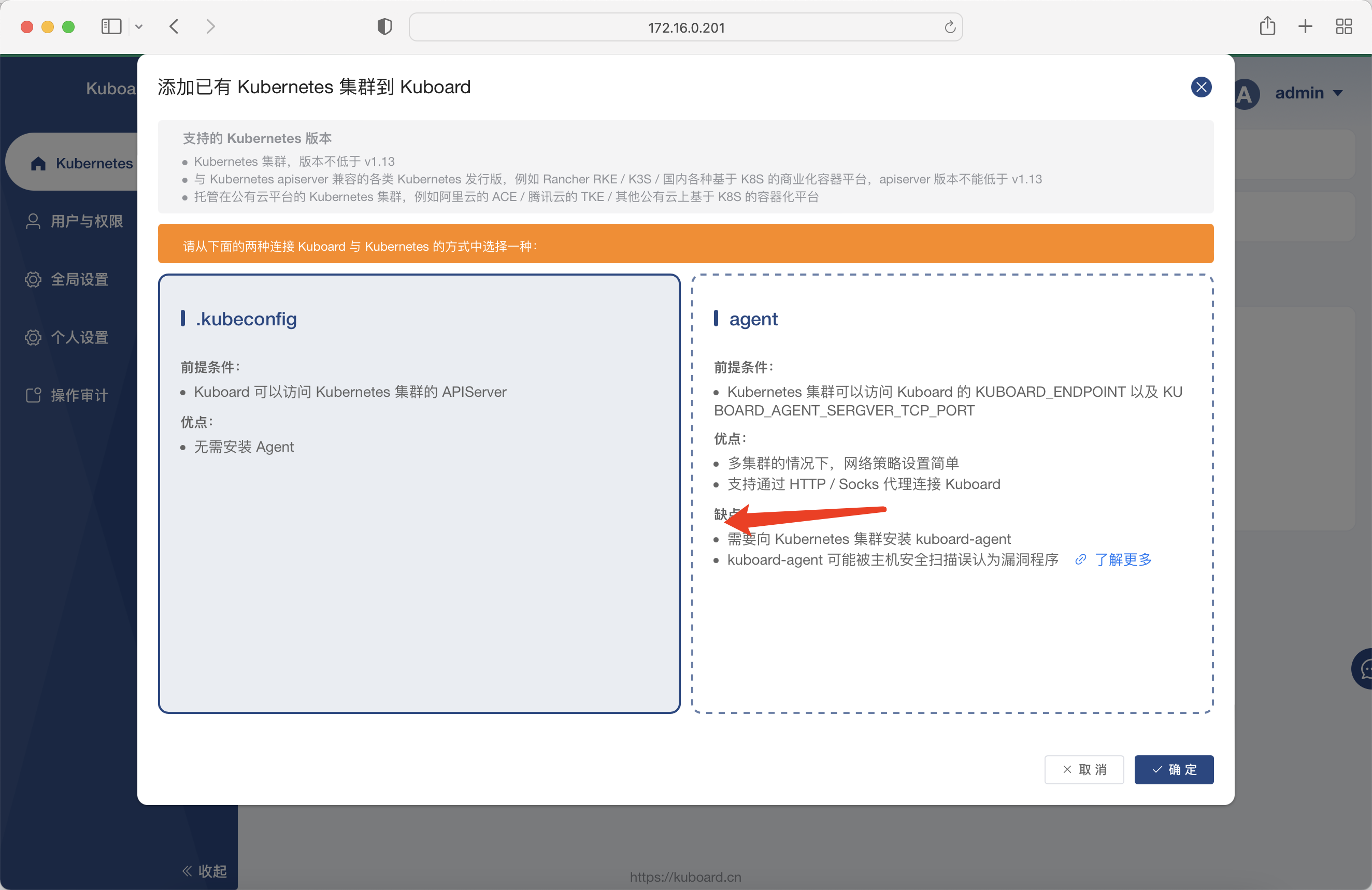
New cluster
View kubeconfig
root@k8smaster-11:~# cat .kube/config
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUR1RENDQXFDZ0F3SUJBZ0lVTVZmenYyZm9CMnl4RjBHZWZzS3krbnd5eVl3d0RRWUpLb1pJaHZjTkFRRUwKQlFBd1lURUxNQWtHQTFVRUJoTUNRMDR4RVRBUEJnTlZCQWdUQ0VoaGJtZGFhRzkxTVFzd0NRWURWUVFIRXdKWQpVekVNTUFvR0ExVUVDaE1EYXpoek1ROHdEUVlEVlFRTEV3WlRlWE4wWlcweEV6QVJCZ05WQkFNVENtdDFZbVZ5CmJtVjBaWE13SUJjTk1qSXdNVEV3TVRReE1qQXdXaGdQTWpFeU1URXlNVGN4TkRFeU1EQmFNR0V4Q3pBSkJnTlYKQkFZVEFrTk9NUkV3RHdZRFZRUUlFd2hJWVc1bldtaHZkVEVMTUFrR0ExVUVCeE1DV0ZNeEREQUtCZ05WQkFvVApBMnM0Y3pFUE1BMEdBMVVFQ3hNR1UzbHpkR1Z0TVJNd0VRWURWUVFERXdwcmRXSmxjbTVsZEdWek1JSUJJakFOCkJna3Foa2lHOXcwQkFRRUZBQU9DQVE4QU1JSUJDZ0tDQVFFQTE1elI5Q0dVaENMZEo0aXpKSmJ6dkMvbU5hQ0gKTHFUME0vdGFkeEt0clF1NFZZTDhyZVI2cWR3cm9MWjdzSlBXWjFaNzh2eHlRQlVuWGxrOThoVk5TUGFuNWVTSgpWUW9mNE9Cd3duZDRMbCtUSm9yRnUyK1FPUUxHaGRDd0hRcklmN24zUW54eGFobWVBNmh5T0xKU0tNVitKQnk3CkRTRVVCZVJwek1raDQ0ZFlmb0s2d0RqMUxqMk9wQ1JwY20ra3Z6VVdITkRlOUJKR3VibDFGdmhCTTJUTDV3T0kKOWJ6QkE2aFozNHBYcFJMeTRVWXJ3cHJ0akVScEF4bDFtUXIxRDJLNThlbThtUFIzblp2SjdiaEdRRGhNaEJ3RwprZWh3YS83SjE5L2dCb3hxNVM3eG0zV1RhK3l3Vm40UlorYlFmTHRFWmZPNk42SkNCWEg3OTlWQW1RSURBUUFCCm8yWXdaREFPQmdOVkhROEJBZjhFQkFNQ0FRWXdFZ1lEVlIwVEFRSC9CQWd3QmdFQi93SUJBakFkQmdOVkhRNEUKRmdRVWlBY0VwZ2JFYm5nN1BmYVNVMklOTWVJUnlHZ3dId1lEVlIwakJCZ3dGb0FVaUFjRXBnYkVibmc3UGZhUwpVMklOTWVJUnlHZ3dEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBS2szTC9IM096UUU2STFBZjM4SEszUmFCWlNsCnJvMDdNdklGZ0lUaXRpcUlyb3lxREp1RzNTSFhONXFVaC9ta2lVUlpPOTc0eUVKYmFxNmpoa3RPOFE0dXlYZDcKeXk3WjRMcWFjV21xbjladUpXY2VXM2dKTHN2My9NSU9NM3lCZ1Qyd05ieUJLblFLUnR2ajVuQ1Fvak1lcXgxawozeWN4VGtxUXdycFlpQmQxeHZRZ1ZweUVsbm42bThYdzA5Z3ZRNzZmTXM4WkgycFN0MFc1YjN4a0RJeGViM0RWCllBNU5OMTl2eFdaUjkrcXVxVjBLME5rRnZuYmFXSklCTWlKNFJ5WlorYVZneUgvcml1Tko0Q1pXOXJjdWdremQKTnY2RHY2dWJaR1Y0U1BCTnBpc1BpZHM0TDhWMlFVMmttMzhyektrcXU2NlpNWDVOZFN4SEtHNjF3QnM9Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
server: https://127.0.0.1:6443
name: cluster1
contexts:
- context:
cluster: cluster1
user: admin
name: context-cluster1
current-context: context-cluster1
kind: Config
preferences: {}
users:
- name: admin
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUQxekNDQXIrZ0F3SUJBZ0lVT1RLdTlLaXZjSVladHdBbllOVGtXc1plZ2J3d0RRWUpLb1pJaHZjTkFRRUwKQlFBd1lURUxNQWtHQTFVRUJoTUNRMDR4RVRBUEJnTlZCQWdUQ0VoaGJtZGFhRzkxTVFzd0NRWURWUVFIRXdKWQpVekVNTUFvR0ExVUVDaE1EYXpoek1ROHdEUVlEVlFRTEV3WlRlWE4wWlcweEV6QVJCZ05WQkFNVENtdDFZbVZ5CmJtVjBaWE13SUJjTk1qSXdNVEV3TVRReE1qQXdXaGdQTWpBM01URXlNamt4TkRFeU1EQmFNR2N4Q3pBSkJnTlYKQkFZVEFrTk9NUkV3RHdZRFZRUUlFd2hJWVc1bldtaHZkVEVMTUFrR0ExVUVCeE1DV0ZNeEZ6QVZCZ05WQkFvVApEbk41YzNSbGJUcHRZWE4wWlhKek1ROHdEUVlEVlFRTEV3WlRlWE4wWlcweERqQU1CZ05WQkFNVEJXRmtiV2x1Ck1JSUJJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBN1ZXS2Y1dFp4VWV5OGN0ajhiV2EKUkNMeEZiR1pldytVRjJqM0Vhcm81TjNiWEliM1VyUlVrL3B4anZaQTBHaERTMUVGYWRSWDU4UlBReURhRDNRbApHSHpuMnJ4ZVIvY2J6QUxIRWhhSUZ4cWJsNlE3QnpGeEhEVHJzU2hIdG9VVFVXUkVKOGRPeXpSeklQcjdGTjV6CitnSGNYMWpud3BKWUxqeXN2QUVMK3lIY2xDZzZHNU9xN2phOVhKaFdycVBSMXRCMU55aWFwWkpVRTdHdWNEeXMKNjZ3dlA4Z1ZZY0pOK3o3Y05SQmhKQUtWc3BReGFqdHlBb3gwajB0dVRKU09oTW95QU05bzV6SUtWUjdKaTRPaApHaElGbkp1Rmc4OWRsRkJycHZMRjJvbDBiVnZia1llRCtSWm9DRUFRWjFvd2hzQ2l5Um1RekxlQnNvbk56a1prCnV3SURBUUFCbzM4d2ZUQU9CZ05WSFE4QkFmOEVCQU1DQmFBd0hRWURWUjBsQkJZd0ZBWUlLd1lCQlFVSEF3RUcKQ0NzR0FRVUZCd01DTUF3R0ExVWRFd0VCL3dRQ01BQXdIUVlEVlIwT0JCWUVGRUVRUE9wZ1ZXMFE4Yll6cUdhVApxRmx5RmtBU01COEdBMVVkSXdRWU1CYUFGSWdIQktZR3hHNTRPejMya2xOaURUSGlFY2hvTUEwR0NTcUdTSWIzCkRRRUJDd1VBQTRJQkFRQkN6bjVvY3dCWlovYlY4YWRZcm9rbmptMFAySkk1djZvb2dmam1iVFpsZ3luTS96YWsKM0U5U0crV29rQ2dnN013bW1xcWFlTzdxUVpTUUFjbmluN21OSEo5TmVKWnVBZGhlTnRITG5lR2x1cTNDUXBiUQpuNG4zRVJkSnNjUisyVW1tRjMzNjlqWUZHZ09ORXJwVXpVclc5WTgrNVdLZ1BZWVB0UlkreGIxUlIwVHdCazc1CnJ2NkVlTEFYSld6RlZZU0tteWxYWjN6dlZGcTk0Sm96VFNpWFRXRXJGanp5S2FoV3ZuQXV2T1R5QXFOcUpnNlIKSHhJeDAvZ1pQa1pRdjNRQ0h2cFVBc0ZBMzBrUjlqWEFRU1FSeW42NGh1em8wcXM2UG9VcExWR0ZHbTFEQlRlbQpPQ2haTXUydlRGTXFBUWsxQjlIOWRIb2xKYzVSNnRjOThEK00KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBN1ZXS2Y1dFp4VWV5OGN0ajhiV2FSQ0x4RmJHWmV3K1VGMmozRWFybzVOM2JYSWIzClVyUlVrL3B4anZaQTBHaERTMUVGYWRSWDU4UlBReURhRDNRbEdIem4ycnhlUi9jYnpBTEhFaGFJRnhxYmw2UTcKQnpGeEhEVHJzU2hIdG9VVFVXUkVKOGRPeXpSeklQcjdGTjV6K2dIY1gxam53cEpZTGp5c3ZBRUwreUhjbENnNgpHNU9xN2phOVhKaFdycVBSMXRCMU55aWFwWkpVRTdHdWNEeXM2Nnd2UDhnVlljSk4rejdjTlJCaEpBS1ZzcFF4CmFqdHlBb3gwajB0dVRKU09oTW95QU05bzV6SUtWUjdKaTRPaEdoSUZuSnVGZzg5ZGxGQnJwdkxGMm9sMGJWdmIKa1llRCtSWm9DRUFRWjFvd2hzQ2l5Um1RekxlQnNvbk56a1prdXdJREFRQUJBb0lCQUJacmdVVGl1UTFBNDYraAp4aFE4VXBGak42RVVBT3EySXdnL0d5L3BGRTBpaENsdWVvaXVqbHJZU3NmMWpWUGl0WkMwMjYwT3FTczB5VVFQCkkycFlUM1RMdjk5Uzhoa2NSOXp5Mmpsa05ZRHhPNGVNdFNMTjBlQ1hRemllRklBeWZBdXhUQnJ4NGdpaU1Nb0oKeTVSQ0czU2ZubURIZGtWVUs4NWFYdnIzb2xrYndEZC9NU2VRem1jUHo0VFpVZldGKzh6TXBQekZtNExiWmJDdgpmMXkvZHVpVGcvcTFpT1d0U0Q2Rk8xYk1PdUhLakVUU0cwMXJRU0RCSnVCaEZ2QkxKYTlLZlBFY215Sm90WThGCjZLWll2QWxhRG9PU3ZhL1NGUEw5a3F1REhsZmNzcjRxNlJQQnBrVTMvYUZidENpVTl6K3RaTWlyVXNqcGg4M3cKR21mcGdKa0NnWUVBOVludXAwOXpFRU1zMlNLbVZVcldIaWxBLzhuN0l2aW9qTmxVcklyWExsTHUzTzMvRUdPTgo2OVZvVjh4bmZUcklIUWZPampHUFV1MktRR0IrTFJMcDA1NWZhMmRHek9tQSsyczZJT0UxS0NOL2VZY1dPT3NSCldEamZjeUtyUk0wOWc5dGhXazh5MWdyOVpodmJCSWx2b1VaTFErTkhlN1QwU0VINGU3elFSamNDZ1lFQTkzSWYKRlErYzNQL2hkOXgxZDFQWU81c0VYVzBSLzhnVmk2NFlYU1ZwK1h6NTFlTVJzRGROVWlkRCtqYjVkRGtPNHJjcApYcGx6VXlSTDhsOVpObXEvQ0xRTGsrRWhPU204ZU9mWkF2YS9WOWFGcHNVMU1WMXFBYXlNa01QaWlGU1ZPcGZJCksrSm94a3AyckJ0bGNFRHg5K0lIY1VFelVkT2xRZENCR05hMDA1MENnWUFEMEdLdW9xTk02MTQwK1Q3UU1GdG4KR0lqejhEVkFjOUJhYjczSytGVWpXUkp3eUJtZ0xZdTAwQm5RMDFJQU5mdUp4K2REZWkyWndpclZtU29jbFNDZwpzdU1VamdRaGhyY0VNTVEwWW9zcTFuSlNkdkMzYlo5VldYelBFd2pLQnM0ZjBEYVE2bzRGbVNJYWhmQSsvOHVHCkc4dHJnSXBKdDZQYnczcVNvWG95dlFLQmdDSzhjb0NTWUlMbHFORWFzYUsrc213cnBzRTJ2b0FacG15bFUrWS8KaWxEcnFtYk1LWCtEUStkMGU2WjBjVEJQa2pkaFh2MVlyVWZPb0pxMXArQnJ1OFdOQU5NUmw0aGV3NFoxaFpGVQo4aWR5aGZDVFhwUS9lTklqVnRnN3AyRmIvbGJyVjc1UldrUDcwQXo1QzVSbWlaRXl1Ymk4WG1mdVBoU3ZJSEJNCk03WkJBb0dCQUpEemlKTXlkODE2OC9qZStleWtZWDExMENDZFF4WkJZYmZOWFBuckdaK1pjWkYrNEc3eDJpUHYKYVQ2Unp3Rk9lYnhCSVdRTmRWWE5lUlBUelZZT2NCUCsyc2tGa1BCMjRIWGcwRWpielQ0OHQ5SDBweVk0ZTZNdQpGSnRyS1E3Z0lhK3V3R1ZSK2F3d0xQMmNldXJKSkFWNkt2NVpkZmJLUkwzc2doMU1RMERMCi0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==