1. Basic introduction
- Log file is an important system information file, which records many important system events, including user login information, system startup information, system security information, mail related information, various service related information, etc.
- Log is also very important for security. It records all kinds of things that happen in the system every day, and uses the log to check the cause of the error or the trace left by the attacker when being attacked.
- It can be understood as follows: log is a tool used to record major events
2. Common system logs
-
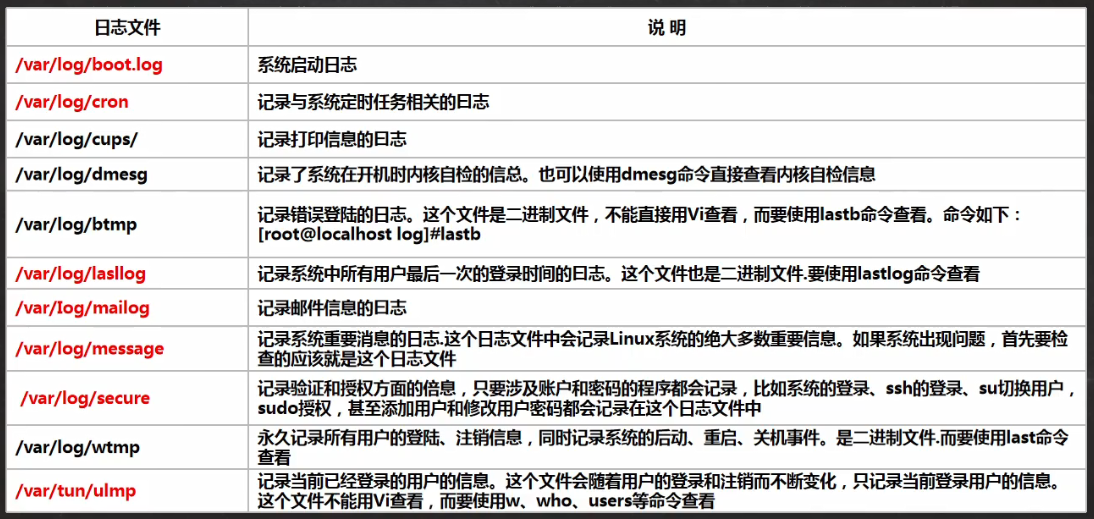
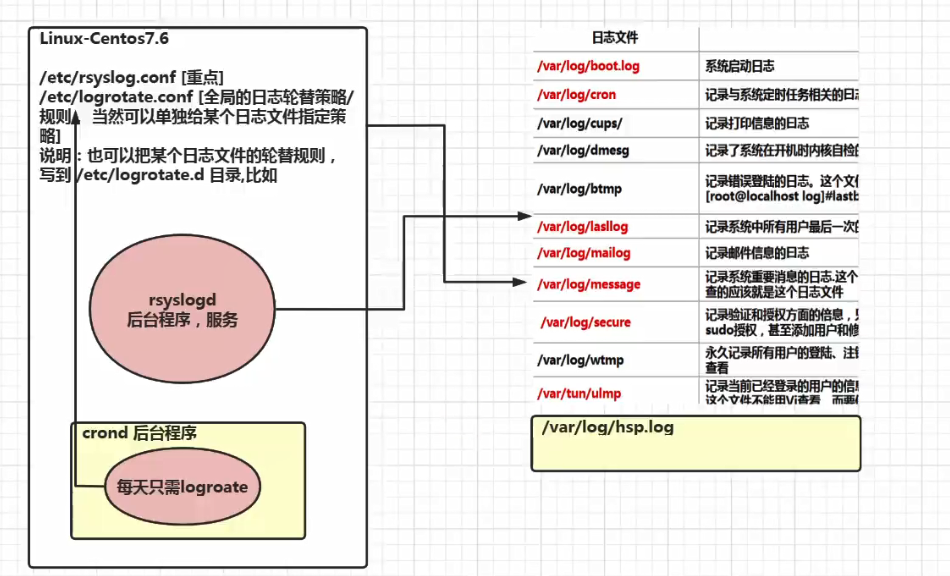
/The var/log / directory is where the system log files are saved

-
Common system logs
-
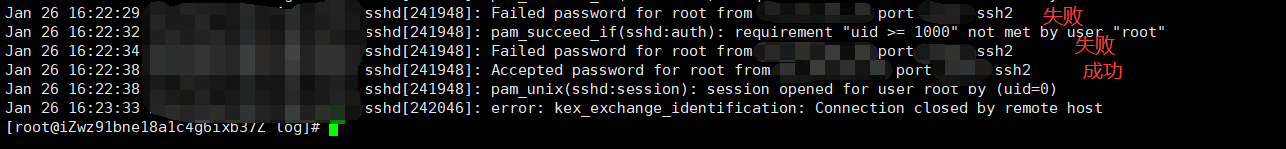
Application case
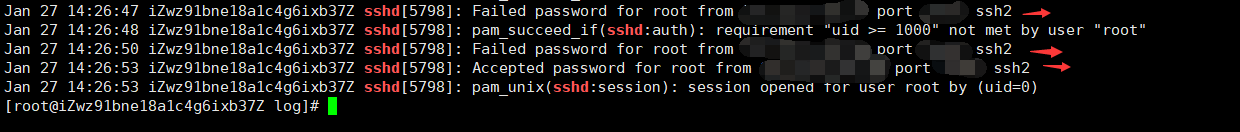
Use root to log in through xshell, use the wrong password for the first two times, and log in successfully with the correct password for the third time
Check whether relevant information is recorded in the log file / var/log/secure
3. Log management service rsyslogd
-
CentOS7.6. The log service is rsyslogd, centos6 The X log service is syslogd
-
Rsyslogd is more powerful. The use of rsyslogd and the format of log file are compatible with syslogd service.
-
Schematic diagram

-
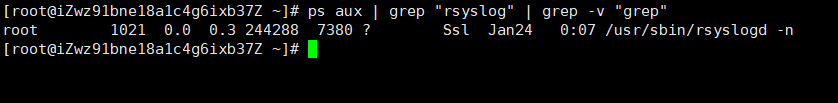
Query whether the rsyslogd service in Linux is started. grep -v indicates reverse matching. Select the process without grep from the pipeline characters
ps aux | grep "rsyslog" | grep -v "grep"
- Query the self start status of rsyslogd service
systemctl list-unit-files | grep rsyslog

- Configuration file: / etc / rsyslog conf
- Log types include:

- Log levels are divided into:
ebug ##If there is debugging information, the log communication is the most info ##General information log, most commonly used notice ##Information on the most important general conditions warning ##Warning level err ##Error level, information that prevents a function or module from working properly crit ##Severity level: information that prevents the whole system or the whole software from working normally alert ##Information requiring immediate modification emerg ##Kernel crash and other important information none ##Nothing is recorded Note: from top to bottom, from low to high, the recorded information is less and less
- The log file recorded by the log service rsyslogd. The format of the log file includes the following four columns:
- Time when the event occurred
- The hostname of the server that generated the event
- The name of the service or program that generated the event
- Specific information of the event
-
How to view instances in logs
Check the / var/log/secure log, which records user authentication and authorization information. Analyze how to view it

-
Log management service application instance
In / etc / rsyslog Add a log file / var / log / XDR. Conf Log, when an event is sent (such as events related to sshd service), the file will receive the information and save it, demonstrate the restart and login, and see if there is a log to save
*. * indicates that all types and levels of logs are recorded and written into XDR log

After restarting the server
reboot
- Reconnect to sshd. Input the wrong password twice before and input it correctly the third time. Check the log of sshd
cat xdr.log | grep sshd
4. Log rotation
4.1 basic introduction
Log rotation is to move and rename the old log file and create a new empty log file. When the old log file exceeds the scope of saving, it will be deleted.
4.2 log rotation file naming
- CentOS 7 uses logrotate for log rotation management. To change the name of the log rotation file, click / etc / logrotate "dateext" parameter in conf configuration file:
- If there is a "dateext" parameter in the configuration file, the log will use the date as the suffix of the log file, for example: "secure-20220101". In this way, the log file names will not overlap, so there is no need to change the name of the log file. Just specify the number of saved logs and delete the redundant log files.
- If there is no "dateext" parameter in the configuration file, the log file needs to be renamed. When log rotation is performed for the first time, the current "secure" log will be automatically renamed "secure.1", and then a new "secure" log will be created to save the new log. In the second log rotation, "secure.1" will be automatically renamed "secure.2", the current "secure" log will be automatically renamed "secure.1", and then a new "secure" log will be created to save the new log, and so on.
4.3 logrotate configuration file
- /etc/logrotate.conf is the global configuration file of logrotate
# rotate log files weekly to rotate the log files once a week
weekly
# keep 4 weeks worth of backlogs. A total of 4 log files are saved. When a new log file is created, the old one will be deleted
rotate 4
# create new (empty) log files after rotating old ones
create
# use date as a suffix of the rotated file
dateext
# uncomment this if you want your log files compressed. If you uncomment, the log is compressed while being dumped
#compress
#RPM packages drop log rotation information into this directory
include /etc/logrotate.d
# Contains / etc / logrotate D / all sub configuration files in the directory. That is to say, all sub configuration files in this directory will be read in,
#The following is a separate setting with higher priority.
# no packages own wtmp and btmp -- we'll rotate them here
/var/log/wtmp {
monthly # Log files are rotated once a month
create 0664 root utmp # Create a new log file with permission 0664, owner root and group utmp
minsize 1M # The minimum rotation size of log file is 1MB. That is, the log must exceed 1MB before rotation, otherwise even if the time reaches
One month, no log dump
rotate 1 # Keep only one log backup. That is, only wtmp and wtmp 1 log retention
}
/var/log/btmp {
missingok # If the log does not exist, the warning information of the log is ignored
monthly
create 0600 root utmp
rotate 1
}
- Parameter Description:

4.4 add your own log to log rotation
- The first method is directly in / etc / logrotate The rotation policy of the log is written in the conf configuration file
- The second method is in / etc / logrotate D / create a new rotation file of the log in the directory, and write the correct rotation policy in the rotation file. Because the files in the directory will be "include d" into the main configuration file, the log can also be added to the rotation.
- The second method is recommended because there are many logs that need to be rotated in the system. If all logs are written directly to / etc / logrotate Conf configuration file, the manageability of this file will be very poor, which is not conducive to the maintenance of this file.
- In / etc / logrotate D / list of configuration rotation documents

4.5 application examples
- Case, in / etc / logrotate Conf, or directly in / etc / logrotate Create the file xdrlog under D / and write the following contents. For the specific effect of rotation, please refer to boot.log under / var/log Log situation
/var/log/xdr.log
{
missingok
daily
copytruncate
rotate 7
notifempty
}
5. Principle of log rotation mechanism
- The reason why log rotation can back up logs at a specified time depends on the scheduled task of the system. In / etc / cron Daily / directory, you will find that there is a logrotate file (executable) in this directory. Logrotate is executed by relying on scheduled tasks through this file.

6. View the memory log
- journalctl can view the memory log,
- Common instructions
journalctl ##View all journalctl -n 3 ##View the latest 3 articles journalctl --since 19:00 --until 19:10:10 #View the log from the start time to the end time, and add a date journalctl -p err ##Error reporting log journalctl -o verbose ##Log details journalctl _PID=1245 _COMM=sshd ##View the log containing these parameters (view in the detailed log) perhaps journalctl | grep sshd