1.1 operating system
Operating System (OS) is a computer program that manages and controls computer hardware and software resources. It is the most basic system software that runs directly on the "bare metal". Any other software can run only with the support of the Operating System.
Operating system classification:
Windows operating system:
Microsoft's windows operating system, such as Windows XP, Windows Vista, Windows 8, Windows 10, etc. commonly used in personal computers. Windows Server2003, Windows Server 2008, etc. used on the server side.
Unix and Unix like (Linux) operating systems:
SUN Solaris, IBM-AIX, HP-UX, FreeBSD, etc. of Unix series, Red Hat Linux, CentOS, Debian, Ubuntu, etc. of Unix (Linux) like
Mac operating system:
Apple designs, develops and sells. Apple not only produces most of the hardware of the Mac, but also develops its own operating system. Have their own processor, their own display, etc. MAC system is the core system based on Unix, which enhances the stability, performance and response ability of the system.
Linux: there are broad and narrow senses:
- In a narrow sense, Linux refers to the linux kernel
- Linux in a broad sense refers to the Linux kernel + package
1-2-1 release
The distribution version of Linux is to package the Linux kernel and application software.
At present, the well-known distribution versions in the market include:
RedHat, CentOS, Fedora, Debian, Ubuntu, SuSE, OpenSUSE, TurboLinux, etc.
1-2-2 application fields
Server field: Internet applications, java applications and PHP applications all use linux servers
Embedded devices: such as Android
Some government agencies: Brazil, Russia, Spain, Portugal, Germany, France, etc
1-3 virtual machines
1-3-1 introduction to virtual machine
Virtual machine( Virtual Machine)It refers to a complete computer system with complete hardware system functions and running in a completely isolated environment through software simulation. The virtual system generates a new virtual image of the operating system, which has exactly the same functions as the real operating system, In the virtual machine, all operations are carried out in this new independent virtual system, which can be installed and run independently Line software, save data, have their own independent desktop, will not have any impact on other systems, and can Enough to switch with the existing operating system. Multiple different operating systems can run simultaneously on a physical computer.
1-3-2 what is cenos
CenOS, full name: Community Enterprise Operating System, Chinese Name: Community Enterprise Operating System. Is a freely available source code version of Enterprise Linux based on Red Hat Linux.
ISO format description: ISO is a kind of optical disk image file. Generally, the optical disk file is made into a file
CentOS: Version Description:
Standard Version: with graphical interface
Minimum version: no graphical interface
Full version: it contains the most abundant software and occupies a large space.
1-4 Linux directory description
- Bin - > usr / bin: this directory stores the most frequently used commands
- boot: this directory stores some core files used when starting Linux, including some connection files and image files
- Dev: dev is the abbreviation of Device. The external devices of Linux are stored in this directory, and the devices in Linux also exist in the form of files
- etc: this directory stores all configuration files required for system management
- Home: the user's home directory. In Linux, each user has its own directory. Generally, the directory name is named after the user's account
- Lib - > user / lib: this directory stores the most basic dynamic connection shared libraries of the system. Its function is similar to DLL files in Windows. Almost all applications need these shared libraries.
- mnt: the system provides this directory to allow users to temporarily mount other file systems. We can mount the optical drive on / mnt /, and then enter this directory to view the contents of the optical drive
- opt: This is the directory where the additional installation software for Linux is stored. For example, if you install an Oracle database, you can put it in this directory. It is empty by default.
- root: this directory is the system administrator directory. root is a user with super permissions
- tmp: this directory is used to store some temporary files.
- usr: This is a very important directory. Many applications and files of users are placed in this directory, which is similar to the program files directory under windows.
- var: this directory stores things that are constantly expanding. We are used to storing those frequently modified files in this directory, such as various running log files.
1-5 remote tools
In actual work, the Linux system will not be on our own computer. The Linux system is installed on the server of the computer room. It is impossible for us to run to the computer room when operating Linux, so we need a tool to remotely connect to the Linux server of the computer room through the network.
XShell/Xftp: download from the official website: https://www.netsarang.com
SecureCRT: download from the official website: https://www.vandyke.com
putty: Download Link:
https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html
WinSCP: Download Link: https://winscp.net/eng/download.php
XShell, SecureCRT and putty are remote tools
Xftp and WinSCP are file management tools
Chapter 2 Linux commands
The Linux server is generally a command line interface, which interacts with the Linux system through commands.
Various operations are carried out through commands.
Learning command address, refer to The website
It mainly includes: disk management; Document management; System settings; Compression / decompression; Network communication; Network access; Authority management; Pipeline and redirection; vi/vim edit command; Install software commands.
2-1 disk management
- Switch Directory: cd directory name
1. Switch from the current directory to / usr/local
For example: cd /usr/local
2. Go back to the root directory (similar to my computer)
For example: cd/ - List the current directory and files: ll, LS
-RW RW RW - represents a file
DRW RW RW D represents a directory folder - Displays the current directory location: pwd
For example, execute pwd in the current directory
2-2 document management
- Create directory: mkdir directory name
For example: mkdir test
View the created directory ls - Delete file or directory rm, rm -rf
1.use rm Delete file For example: rm my.txt stay test01 Directory execution echo "ok" > my.txt Create a my.txt File In execution rm mytxt.txt After pressing enter, you will be prompted to confirm deletion 2.Delete directly without confirmation For example: rm -f my.txt 3.Delete directory: rm catalogue For example: rm -rf test01 rm Directory cannot be deleted without parameters rm -rf test01 remove folders r Indicates recursive deletion, f No confirmation prompt
-
Copy file command cp, cp -rf
1. Copy file: AA Txt is the new file name
Syntax: cp assigned file name new file name
For example: CP Anaconda ks cfg aa. txt2. Copy folder
Syntax: cp -rf folder new folder name
For example, cp -rf myfolder newfolder -
View all contents of the file: file path
For example: cat / root / Anaconda KS cfg -
Paging view file content: more file path
Output screen by screen (press the blank key space to the next page) and Enter line by line
For example: more / root / Anaconda KS CFG (press Enter after command input) -
View n lines of data at the beginning of the file: head -n number
For example: head / root / Anaconda KS CFG (default is 10 lines) -
Display n lines of data tail -n numbers at the end of the file. The default is 10 lines
For example: tail / root / Anaconda KS cfg -
Search within files: grep
To search for a string in a file (multiple files can be used at the same time), you can use the regular expression syntax: grep [parameters] string content searched file name 1 [file n]
Prepare a file AA Txt, as follows. test.txt content is the same as AA txt
1.Search text“ java ": grep java aa.txt Not capitalized“ JAVA",The default is case sensitive search 2.Search text“ java "Case sensitive: grep -i java aaa.txt -i: Case insensitive 3.There are spaces in the search text, enclosed in quotation marks for example grep "java is" aa.txt 4.Search the whole word, which is part of other strings and does not meet the conditions -w : Search for words Search for words java : grep -w java aa.txt 5.Use regular to java First line ^ [0-9][a-z][A-Z]$ regular for example grep "^java" aa.txt 6.Search in multiple files grep java aa.txt bb.txt **7.Use pipe“|"** For example: cat aa.txt | grep java
2-3 system commands
-
Display system date and time: Date
Displays the current system time For example: date
-
Switch user: su user name
-
Clear screen: clear
Shortcut key ctrl+L -
Restart the system: reboot
-
Shutdown: shutdown -h now
-
View system process: ps -ef
ps [command parameter]
Common parameters:
-e: Show all current processes -f : display UID,PPID,C And STIME Field information UID: The user who owns the program PID: Process of program id PPID: Parent process id C: CPU Percentage of resources used STIME: System startup time TTY: Terminal location of login system (identification of client) TIME: Used CPU time CMD: What programs start the process
- kill process: kill
For example:
kill pid: kill the process
kill -9 pid: force kill process
It can't be used at will. It will be killed by the system process, and the program can't be used.
2-4 compression / decompression
- tar compression (archive)
tar is used to compress and decompress files. tar compressed files are also called archive files.
Syntax: tar parameter the file or directory to be compressed or decompressed
Common parameters:
z: Using compression, the generated file name is xxx.tar.gz This is linux Compression format commonly used in. c: Create a compressed document v: Displays the file names processed during compression and decompression f: Specify the archive file name, tar The parameter is followed by the archive file name x: To release a file from the archive is to unzip it t: List the contents of archived files and view the contents of files C: Unzip it to the specified directory. How to use it -C catalogue C It's capitalized
-
Create Archive (compressed)
Syntax: tar -zcvf archive file name list of files to be archived
For example: tar - zcvf txtfile tar. gz aa. txt -
Archive multiple files
For example: tar -zcvf TXT tar. gz aa. txt test. txt
-
Compressed directory
Syntax: tar -zcvf archive file name directory
For example: tar - zcvf file tar. gz mytest
2. View archived (compressed) files
Displays the contents of the compressed file.
Syntax: tar -tf archive file name
t: Lists the contents of archived (compressed) files
f: Archive file name
For example: tar - TF File2 tar. gz
3 .tar decompression
Decompression: release the compressed file contents
Syntax: tar -zxvf archived file name
Parameter: x: decompress, release the file from the archive,
decompression file.tar.gz Syntax: tar -zxvf file.tar.gz
2-5 network communication
(1) View ip information: ifconfig
grammar ifconfig For example: enter anywhere ifconfig
(2) Test network connectivity: ping
Syntax: ping ip Or domain name For example: ping www.baidu.com
After viewing, ctrl+C to exit the view and return to the Linux command line
2-6 network access
(1) C url: a file transfer tool that uses URLs to access the network.
curl Is to use URL Open source file transfer tool with syntax working in command line mode Commonly used to 1: test network access; 2: Simulate user access Grab Baidu's home page content For example: curl www.baidu.com
(2) wget: Download
WGet is a tool for downloading resources on Linux, such as downloading software installation packages. General software will give a download address
Syntax: resource address of wget Download
2-7 permission management
2-7-1 introduction:
Permission refers to the operations that users or programs can perform on directories and files.
Execute ll or ls -l to display file and directory details

The Linux permission mechanism adopts UGO mode. Where u (user) represents the user, g (Group) represents the group, and o (other) represents situations other than the user and group.
A. Read permission: read the contents of the file, execute cat, more, less and other viewing commands on the file, and read the list of files in the directory for the directory
r – read privilege 4
B. Write permission: edit, add, and modify file content
w – write permission 2
C. Execution permission: enter the directory and access the file contents in the directory
x – execute permission 1

D. Common permission settings
rwx = 4 + 2 + 1 = 7
There are three common permissions: 644, 755 and 777
The user who creates the file is the owner of the file, and the group of the user is the group of the file. All users except the one who created the file are other users. root has the highest permissions
E. Permission attempt
2-7-2 permission setting
(1) Modify file permissions chmod
Syntax: chmod UGO permission file / directory
For example, first create the file AA. As root Txt, the permission to view the file. Other users only have r read permission. centos vs AA Txt is other users
(2) Modify file owner chown
Syntax: chown new owner user modified file
For example, modify the original root owned file AA Txt is changed to centos, and the owner has read and write permission to operate
Pipes and Redirection
(1) Redirect output override: >
Output content to the file. If the file does not exist, create a new file and then output it; The file exists. Empty the file before writing the content.
For example: echo "write some" > T1 txt
(2) Redirect output append: > >
Output content to the file. If the file does not exist, create a new file and then output it; If the file exists, the new content is appended to the back of the file.
For example: echo "hello new word" > > T1 txt
(3) Pipeline|
The pipeline connects two commands with "|" and takes the output of the previous command as the input of the following command. It is used to take the output on the left of the pipeline as the input on the right.
For example: echo "hello linux" | grep "linux"
Check whether a process exists
For example: ps -ef | grep "cat"
2-9 vi and vim editors
vi is a standard text editor with a pure character interface under Linux. Because it is not a graphical interface, relevant operations should be completed through keyboard output commands. It is necessary to remember some common operation commands
vim is an upgraded version of vi, which is fully compatible with vi. vim can also be used as vi. vim adds some functions on the basis of vi, such as syntax coloring
2-9-1 launch vi editor
Syntax: vi file name
2-9-2 vi common operations
vi operation is divided into command mode and edit mode
Command mode: press esc to enter the command mode, which cannot be edited
Edit mode: press the a or i letter key to enter the edit mode (at this time, insert will appear at the bottom). In the command mode, press: wq (colon key, w key, Q key) to save and exit, and press: q! To exit without saving.
Enter the editing mode from the command mode and press the a or i letter key.
Enter command mode from edit mode and press Esc
Edit file commands
1) dd: delete the line where the cursor is located
2) yy: copy the cursor line to
3) p: paste the contents of the buffer
4) gg: the cursor returns to the first line of the file
5) GG: the cursor returns to the last line of the file
6) ^: move the cursor to the beginning of the current line
7) $: the cursor moves to the end of the current line
8) / keyword: press the slash / key to enter the character you want to search, and then confirm to search,
2-10 install software command
(1) Introduction to yum command
Yum: Yum (full name: yellow dog updater, modified): it is a software package manager in RedHat, Fedora and CentOS. It can automatically download and install software packages from specified servers. It can automatically handle the dependencies between software packages and install all dependent software packages at one time without cumbersome downloading and installing again and again.
(2) yum using:
Find package command: yum search some keywords in the package name
For example: yum search java
1.Install the specified software command: yum install Installation package name install openJdk ,GPl java Virtual machine. For example: yum install java-1.7.0-openjdk 2.Delete package command: yum remove Installation package name 3.List all installed package commands: yum list installed 4.Clear downloaded files for installed packages command: yum clean all(yum The installation packages downloaded by the command are placed in/var/cache/yum Table of contents)
2-11 shortcut keys
shift + insert is paste
tab is the completion code
y: Agree
n: Negation
Chapter III development related
3-1 JDK download and installation
(1) Download JDK
Linux can be connected to the Internet and downloaded using wget. The jdk of Linux version is downloaded.
For example: wget
(2) Unzip to the specified directory
tar -zxvf jdk-8u161-linux-x64.tar.gz -C /usr/local/
(3) Configure environment variables
1.Default environment variable java -version 2./etc Under directory profile Add at the end of the document: export JAVA_HOME=/usr/local/jdk1.8.0_161 export PATH=$JAVA_HOME/bin:$PATH export CLASSPATH=.:$JAVA_HOME/lib/dt.jar:$JAVA_HOME/lib/tools.jar:$JAVA_HOME/jre/lib/rt.jar 3.profile The document is modified to and executed source /etc/profile Make the above configuration effective source The command is usually used to re execute the newly modified initialization file to take effect immediately without Log out and log back in Syntax: source file name For example: source /etc/profile 4.implement java -version Check whether the configuration is successful
3-2 Tomcat download and installation
1.Tomcat Download:
tomcat Official website: http://tomcat.apache.org/ It can be downloaded through Alibaba open source image station
2. Unzip to the specified directory
3. Start / stop Tomcat
After extracting tomcat, you can use it. Use the cd command to switch to the bin directory under the Tomcat home directory
1.Startup mode, execution tomcat Installation directory/bin/startup.sh
stay tomcat Installation directory/bin Next execution
For example:./startup.sh
After startup, it will be tomcat Installation directory/logs Generate log file under
A,catalian.out
Log file output from console (in eclipse Medium console Window), view this article
Pieces. have access to cat,more,less,grep,Common view log tail -f catalian.out
B,localhost_access_log.2021-02-20.txt
tomcat Received http Request log. tomcat Running on server web Requests received by the application,
Request mode( get,post),Request address( get Request), whether the processing is successful
All recorded in this file.
File name: localhost_access_log_yyyy-MM-dd.log
4. Check whether the mariadb database is installed in the system
inspect Linux Is it installed mariadb database mariadb Database is mysql Branch of. Yes, No Fee is open source. mariadb and mysql There will be conflict. First check the installation mariadb Uninstall. Check command: yum list installed | grep mariadb
5. Uninstall mariadb
if Linux Installed in mariadb Database, uninstall it first, maridb The database may be different from the installation mysql Conflict. Execute command: yum -y remove mariadb-libs.x86_64
6. Modify the unzipped file name
The extracted mysql-5.7.0 31-linux-glibc2. 5-x86_ 64 renamed mysql-5.7 18 or mysql. In order to specify the version of MySQL, it is recommended to rename it mysql-5.7 eighteen
Modify the folder name: mv Original folder name new folder name
7. Create data folder data
data Folder is mysql Used to store database files. The table data of the database are placed in data catalogue Default no data Directory, which can be created manually data Directory, in mysql-5.7.31 file Create a folder under folder directory data Folders, switching to mysql-5.7.18 Directory, execute create file Clip command For example: mkdir data
8. Create a user and execute the mysqld command
establish mysql User, used to execute MySQL Command of mysqld,This command is used to initialize mysql Basics Information. Execute command: useradd mysql
9. Initialize MySQL
use mysql of mysqld Command initializes the basic information of the database. Switch to mysql-5.7.18/bin Execute under directory. Command (note that the following commands are executed on one line): ./mysqld --initialize --user=mysql --datadir=/usr/local/mysql-5.7.31/data --basedir=/usr/local/mysql-5.7.31 The above command is executed on one line
Password: b+3H)dBrt=sp
10. Enable the security function
All data transmitted back and forth between the server and the client is encrypted. Identity provided by certificate Verification mechanism, mysql Command program, mysql_ssl_rsa_setup Data encryption is enabled Function to generate digital certificate. stay mysql-5.7.18/bin Execute command under Directory: ./mysql_ssl_rsa_setup --datadir=/usr/local/mysql-5.7.31/data
11. Modify the permission of mysql installation directory
mysql Changes are required after installation mysql-5.7.31 Access to the entire folder directory, and change the user to which it belongs And groups, which were created earlier mysql User. stay mysql Parent of the installation directory(/usr/local/)position Set, execute command chown For example: chown -R mysql:mysql /usr/local/mysql-5.7.31/ mysql:mysql Indicates the user and group of the folder Parameter Description: R: Represents recursion to change the permissions of all subfolders in the directory View original directory owner
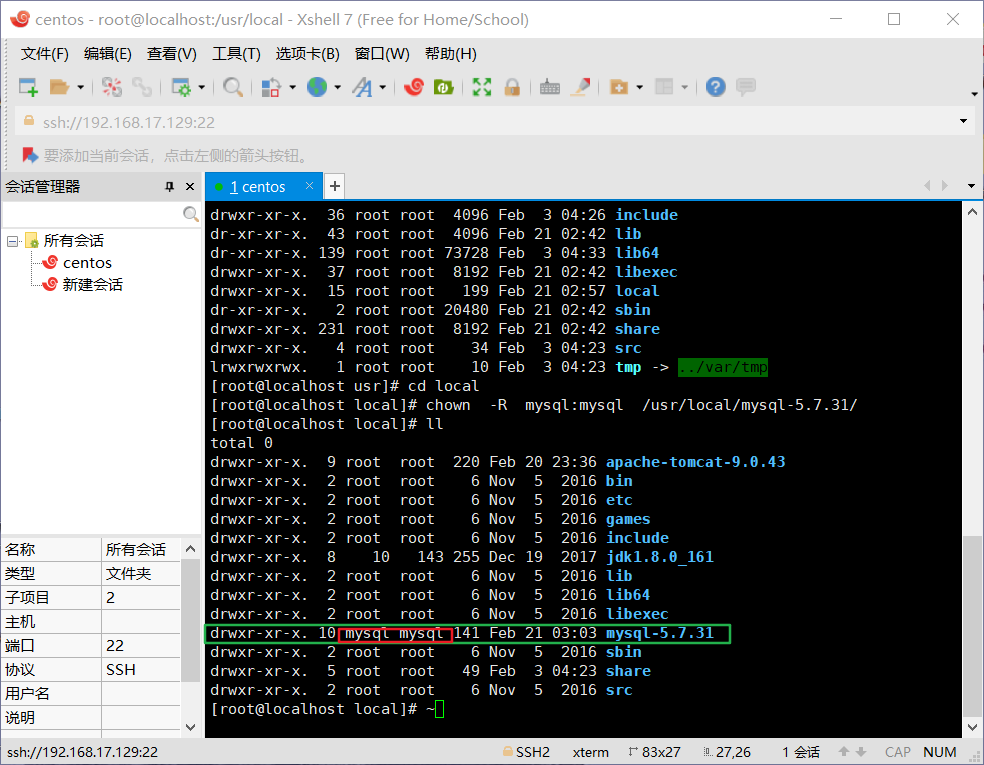
Make mysql belong to mysql and mysql user group.
12. Start MySQL
start-up MySQL Services, mysql-5.7.31/bin Execute command under Directory: ./mysqld_safe &(among & Symbol indicates background startup), enter a command and press Enter mysqld_safe The program will start at MySQL After the server, continue to monitor its operation and Restart it when it crashes mysql_safe Program to start MySQL The approach of the server is unix/linux Common on the system confirm mysql Whether to start, view the process, and use ps-ef | grep mysql
13. Use the MySQL client to enter mysql
Log in mysql,mysql-5.7.31/bin Execute command under Directory: ./mysql -uroot -p -u Indicates use root The user logs into the system and uses the password generated in step 9
14. Change the root password
Of step 9 root The user password is temporary and can only be used after being modified. implement SQL sentence show databases;The first time you use it, you will be prompted to modify it mysql of root User password modify mysql Password, command syntax: alter user 'user name'@'Host domain name or ip' identified by 'New password' For example: alter user 'root'@'localhost' identified by '123456';
15. Authorize remote access
Authorize remote access. Before authorization, it can only be accessed locally mysql,Remote authorization Is to let other computers access through the network mysql(So that remote clients can access) Authorization command: grant Syntax: grant all privileges on *.* to root@'%' identified by '123456'; Parameters: among*.*The first one*Represents all database names, the second*Represents all database tables; root@'%'Medium root Indicates the user name,%express ip Address,%You can also specify a specific ip Address, For example: root@localhost,root@192.168.10.129 1.Execute authorization command For example: grant all privileges on *.* to root@'%' identified by '123456'; 2.Update permission information and execute flush Refresh permissions For example: flush privileges;
16. Test mysql client access to mysql
Connection error, possibly Linux The firewall works. You can turn off the firewall first Commands to operate the firewall: View firewall status: systemctl status firewalld Make firewall available: systemctl enable firewalld Make firewall unavailable: systemctl disable firewalld Turn on the firewall: systemctl start firewalld Disable firewall: systemctl stop firewalld View firewall status: in Linux Command line execution
3-3 deployment of Web project to Linux system
. war mode deployment
hold web App packaged as .war File with extension. hold xxx.war File deployment to tomcat of webapps Directory, you can tomcat Medium operation web Application.