File common commands
- create a file
touch
- Copy file
cp file1 file2 //Copy file1 in the same directory and name file2 cp file1 file2 dir //Copy file1 and File2 to dir directory cp -p //Move the file and save all the original information
- Move (rename) file
mv a b //Move to local and rename mv a b dir //Move a and b to dir directory
- Delete file
rm a b c //Delete normal files rm -f a b c //Force deletion of files
There will be no prompt for rm deletion of ordinary accounts,
The root administrator will be prompted to delete, y yes n no
Use with caution unless -f forcibly deleted
File view command
- View file information
ls //View files in the current directory ls -l //View detailed file ls -i //View document number ls -lh //View file size ls -a //Show all files ls -ld //View the directory itself
- View file types
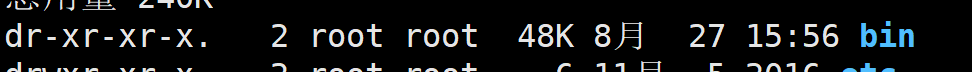
d //Represents a directory - //Representation file 1 //Represents a connection file b //Represents a device file and provides a stored interface device c //Represents a device file. Provide serial interface device - keyboard,
- view file contents
- cat
cat file //View file contents in positive order tac file //View file contents in reverse order cat -b file //The file content displays the line number cat -A file //View hidden content: line breaks, spaces, special symbols
- nl
nl -ba //List the line number whether there is an empty line or not nl -bt //If there is an empty line, the line number is not listed
- less
/ Find character :f Displays the file name and number of lines b Turn to the first page Space Turn down one page pagedown Turn down a page pageup Turn up a page q sign out
- head,tail
head file //Display the first ten lines of the file tail file //Display the last few lines of the file, and generally view the log (dynamic) parameter -n: Display several lines (ten lines by default) -f: Dynamically display the contents at the end of the file
- wc
wc -l file name //Display rows wc -c file name //Display byte
Find and replace file contents
grep can only be used to find the contents of a file
grep parameter -i : Case insensitive -v : Exclude specified string
sed can find, replace or insert the desired content
| character | Representative meaning |
|---|---|
| a | New, a can be followed by strings, and these strings will appear on a new line (the current next line) |
| d | Delete, because it is delete, so there is usually nothing after d; |
| i | Insert, i can be followed by strings, and these strings will appear on a new line (the current previous line); |
| p | Printing, that is, printing a selected data. Usually p is associated with the parameter sed |
| s | Replace, you can directly replace the work! |
- Find file find
usage:find[route][Command parameters][expression]
parameter:
-name "File name: find the file with the specified name;
-user: Find files owned by the specified user;
-group: Find files owned by the specified group;
-mtimen: Find in N Files modified days ago;
-atimen: Find in N Files accessed days ago;
-type d/t/b/1/p: Find another piece of the specified type;
-empty: Find files that are empty;
-size: Find by capacity;
-perm mode: Find files with specified properties;
-exec command{} \: Finds the specified file and executes the specified command;
-newer File name: find a file newer than the specified file
find * //All characters find ? //Single character
- Find directory which
which command
Soft connection, hard link
Hard link:
- It has the same meaning as cp -p, but the hard link can be updated synchronously
- You cannot hard link directories,
- Cannot partition
ln ln -l
Soft connection
ln -s: Soft connection
Directory common commands
- System directory
| Directory name | effect |
|---|---|
| /boot | System startup directory, files required for Linux startup, such as kernel files and boot boot boot program files |
| /dev | Device file |
| /etc | Configuration file, script file |
| /home | The root directory where all user files are stored is the base point of the user's home directory. For example, the user's home directory is / home/user, which can be represented by ~ user |
| /root | Administrator home directory |
| /proc | The virtual file system is saved to memory. Save the system's kernel, process, external device status and network status lights. For example, / proc/cpuinfo saves CPU information, / proc/devices saves the list of device drivers, / proc/filesystems saves the list of file systems, / proc/net saves the network protocol information |
| /sys | Virtual file system. Similar to the / proc directory, they are stored in memory, mainly in kernel related information |
| /srv | Service data directory. -- After some system services are started, you can save the required data in this directory |
| /tmp | Temporary directory. The directory in which the system stores temporary files, which can be accessed and written by all users |
| /usr | System software resource directory. It is the abbreviation of "UNIX software resource" and the directory where system software resources are stored. Most of the software installed in the system is saved here, |
| /var | Dynamic data storage location. It mainly saves cache, logs and files generated by software operation |
| /media | Mount directory. System recommendations are used to mount media devices, such as floppy disks and optical discs |
| /mnt | Mount directory, which was the only one in early Linux, is not subdivided. Now, the directory system recommends mounting additional devices, such as U SB flash disk, mobile hard disk and partitions of other operating systems |
| /opt | The location where the software installed by the third party is saved. This directory is the place to place and install other software. The source package software I manually installed can be installed into this directory. However, I am more used to putting the software in the / usr/loca1 / directory, which means that the / usr/local / directory can also be used to install the software |
| /run | Process file |
| /bin | The directory where system commands are stored, which can be executed by ordinary users and super users. However, the commands placed in / bin 'can also be executed in single user mode |
| / sbin | Save commands related to system environment settings. Only super users can use these commands to set the system environment, but some commands can be viewed by ordinary users |
| /usr/bin | The directory where system commands are stored, which can be executed by ordinary users and super users. These commands have nothing to do with system startup and cannot be executed in single user mode |
| /usr/sbin | Store unnecessary system management commands for the root file system, such as most service programs. Only super users can use it. In fact, you can notice that in the Linux system, only super users can use the commands saved in the "sbin" directory, and all users can use the commands saved in the "bin" directory |
| /usr/lib | 32-bit library file |
| /usr/lib64 | 64 bit library file |
- Path switching
cd
cd /: switch to the root directory
cd...: return to the previous directory
cd ~: return to your home directory
cd -: returns the directory of the previous level
- Create directory
mkdir a //Create a directory mkdir -p dir1/dir2/a //If there is no dir directory, - p automatically creates it
- duplicate catalog
cp -r dir1 dir2 //Copy dir1 in the same directory and name dir2 cp -r dir1 dir2 dir3 //Copy dir1 and dir2 to dir3 directory
- Move directory
mv dir1 dir2 //If dir2 does not exist, it is equivalent to renaming dir2 from dir1 mv dir1 dir2 dir3 //If dir3 exists, dir1 and dir2 move to dir3
- Delete directory
rm -r a //Delete a directory rm -rf a b c //Force deletion of contained files and directories
Permissions for files and directories
Query authority
ls -l query details. What does each place mean

- jurisdiction
rwx, read, write and execute, without permission-
First group rwx: permissions of the file owner
Second group rwx: permissions of the group to which the file belongs
The third group rwx: permissions for other people on the file
- file right
The owner of the file is the user. You can force writing without w permission!. The group and others can't.
r: View file contents
w: Writable
x: Can vim edit
- Permissions for directory:
Users do not have w the permission to edit files in a directory whose owner is their own
r: Check the files in the directory
w:
- You can create new files and directories in this directory
- You can delete existing files and directories
- Rename existing files and directories
- Move the location of files and directories within the directory
x: Can I enter this directory
Modify permissions
- chmod modifies the permissions of the owner and the group to which it belongs
- Numerical method: r=4, w=2, x=1
chomd 777 123 // The permissions of the owner, group and others of 123 are RWX RW RW RW-
- Addition and subtraction method
Owner / group / others, u / g / o, + / - / =, r / w / x
chomd u=rx 123// The owner permission of 123 is rx chomd u+w 123 // The owner permission of 123 is rwx
- chown modify owner
chown root abc //Modify the owner of abc to root chown -R root abc //Recursively modify the owner of abc to root //All owners contained in the abc directory are changed to root
- chgrp modify group
groupadd Group name //New group gpasswd -a User group name //Field user group chgrp root abc //Modify the group of abc to root chgrp -R root abc //Recursively modify abc to root //All groups contained in the abc directory are changed to root
Default permissions
- umask: view the default permissions of the current user to create files and directories
0022: it represents the authority taken away
The first 0 represents special permission
022: rwxr-xr-x
When creating files and directories, the x permissions of the files are taken away by default
- Temporarily modify default permissions
umask 000 //When creating files and directories, file RW RW RW RW -, directory rwxrwxrwx
- Permanently change default permissions (not recommended)
/etc/bashre / / modify the value inside
special competencies
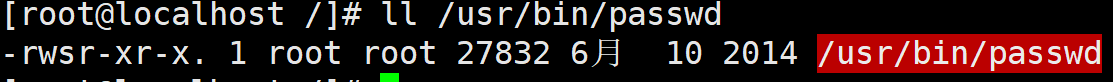
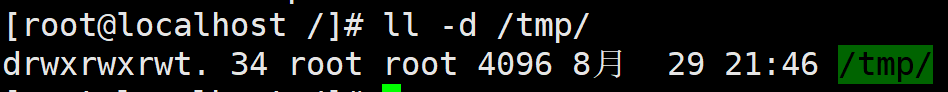
drwxrwxrwt. 14 root root 4096 10 September 23-19:32 / tmp/ rwsr- xr-x .1 root root 27832 6 October 2014 /usr/bin/ passwd
When s appears in the x permission position of the owner, it indicates that the owner has SUID permission (Set UID)
When s appears in the x permission position of the group, it indicates that the group has SGID permission (Set GID)
When t appears in the x permission position of others, it means that others have SBIT permission (Sticky Bit)
- SUID, which temporarily obtains the permission of the file owner. One can only be used for files
- SGID, even if it can act on a directory, can also act on a file
Apply to file: same as SUID
Apply to directory: inherit the instrument set directory. A directory will continue to inherit - SBIT means that only the owner of the file can delete or modify the file in the directory
Only for directories
And can only be modified in the position of others
S and T are both uppercase and lowercase
Upper case description: NO x permission
Description in lowercase: with x permission
- SUID
- Only executable binary programs can set SUID permission
- The command executor shall have x (execution) authority on the program. The command executor shall obtain the identity of the owner of the program file when executing the program (the soul attachment is the owner of the file during the execution of the program)
- SetUID permission is only valid during the execution of the program, that is, identity change is only valid during the execution of the program
When executing, temporarily have SUID permission
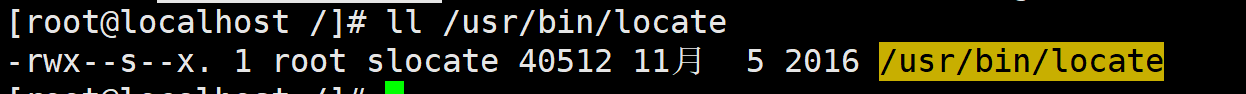
- SGID
1. For file
- Only executable binaries can set SGID permissions
- The command executor should have x Execution Authority on the program
- When executing a program, the group identity is upgraded to the group of the program file
- SetGID permission is also valid only during the execution of the program, that is, the change of group identity is valid only during the execution of the program
2. For directory
- Ordinary users must have and x permissions on this directory to enter this directory
- The valid group of ordinary users in this directory will become the subordinate group of this directory
- If ordinary users have w rights to this directory, the default group of the newly created file is the group of this directory
- SBIT
- The adhesive bit is currently only valid for directories
- Ordinary users have w and x permissions on this directory, that is, ordinary users can have write permissions in this directory
- If there is no adhesive bit, because ordinary users have w permission, they can delete all files in this directory, including files created by other users. However, the adhesive bit is given. Except for root, all files can be deleted. Even if ordinary users have w permission, they can only delete files created by themselves, but they cannot delete files created by other users
- Modify special permissions
Digital method: SUID=4 SGID=2 SBIT=1
chomd 4777 file name chomd 2777 file name chomd 1777 Directory name chmod u+s file name chmod g+s file name chmod o+t Directory name
- Delete special permissions
chmod 777 file name chmod u-s file name
ACL file permissions
If a user in the system has permission to write to a file, but the user belongs to other, he can only open the permission of other. However, once the permission of other is opened, each other can access the file,
File ACL permissions solve this problem
acl: for a single user, set a single file or directory to modify rwx permissions
- Set acl permissions for files setfacl
setfacl -m u:Account name: rwx file name/Directory name //Add acl permission to this file / directory and have a specific account setfacl -m g: Group name: rwx file name/Directory name setfacl -m m: rwx //Modify mask value parameter -m: to configure acl parameter -x: To delete a single file acl -b: delete acl Configuration of -R: Recursive configuration ac parameter
- Delete acl
setfacl -x u:Account name file name/Directory name setfacl -x g:Account name file name/Directory name setfacl -b file name/Directory name //Delete all acl permissions for this file
- Recursive ACL permissions
setfacl -m u:Account name: rwx -R Directory name
- Default ACL permissions
setfacl -m d:u:Account name: rwx Directory name
- View acl permissions of the file getfacl
getfacl file name/Directory name
- Maximum effective permission mask
mask definition, acl permission limit
1. mask is the maximum valid permission of the acl file / directory set
2. You need to set the acl permission and get the permission, which is the real acl permission of the file / directory
File system hidden properties
A lock prevents users including root from misoperating files
i: If I attribute is set for a file, it is not allowed to delete or rename the file, or add or modify data; If the I attribute is set for the directory, you can only modify the data of the files in the directory, but you are not allowed to create or delete files.
a:
If a attribute is set for a file, data can only be added to the file, but cannot be deleted or modified; If the a attribute is set on the directory, only files can be created and modified in the directory, but deletion is not allowed
- Set file hiding attribute chatr
chattr +i file name/Directory name chattr -i file name/Directory name chattr =i file name/Directory name
- lsattr hide file properties view
lsattr parameter -a: Show all files and directories -d: If the target is a directory, only the directory itself is displayed, not sub files
sudo permissions
The shutdown command can only be used by the root user, but the root user is too busy and can be given to ordinary users
- root assigns commands that can only be executed by super users
- Executed by ordinary users. The operation object of sudo is the system command, which is also a file

- View assigned permissions
sudo -l
- Set sudo
visudo //The actual modification is the / etc/sudoers file
- example
visudo SC ALL= /sbin/shutdown -r now //Give the sc user restart permission sudo /sbin/ shutdown -r now //Ordinary users perform the given permissions