catalogue
1. Basic information of Openssh service
1) Experiment: asymmetric encryption is set between two virtual machines
2) Experiment: authentication change test
3) Experiment: Port change test
linux remote login service
1. Basic information of Openssh service
When managing the server, you need to log in to the remote host through the network and open the shell. The remote host must provide such a way to open the shell. It is almost impossible for the enssh service to provide the above.
Client: Secure SHell (ssh)
Server: Secure SHell daemon (sshd)
ssh [-l remote host user] < IP | hostname >
ssh -l root 172.25.254.120 # start a remote shell as root in host 120 through ssh command
Ask (yes/no/[fingerprint]? The identity certificate is generated. When you enter yes, host 120 will send the identity public key to the current host and save it to ~ / ssh/know_ In the hosts directory, if this authentication is changed, the next connection will be rejected
Solution:
vim ~/.ssh/know_hosts delete the corresponding error line in this file
: set nu display row d delete row
ssh common parameters:
-l # specify the login user
-i # specifies the private key
-X # open drawing
-f # background operation
-o # specify connection parameters
#ssh -l root 172.25.254.120 -o "StrictHostKeyChecking=no" you do not need to enter yes for the first connection
-t # specifies the connection springboard
#ssh -l root 172.25.254.120 -t ssh -l root 172.25.254.220
# the current user first connects to host 120 and then connects to host 220 from host 120
2. sshd key authentication
Symmetric encryption: encryption and decryption are unsafe for the same string of characters
Asymmetric encryption: public key encryption (lock) private key decryption (key) can be created anywhere. Give the created public key to XX host. Another host connects XX host with the private key (unable to log in to the server without a key)
Asymmetric encryption key generation: [root@westosb .ssh]# SSH keygen create key Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Enter the saved key file (enter to generate the default key) Enter passphrase (empty for no passphrase): Key password Enter same passphrase again: Confirm password Your identification has been saved in /root/.ssh/id_rsa. Private key Your public key has been saved in /root/.ssh/id_rsa.pub. Public key The key fingerprint is: SHA256:VFvnfu0oyLT5MHhsRAxg58p5rQ7I6ttL0RGTNpAekEk root@westosa.westos.org The key's randomart image is: +---[RSA 3072]----+ | .E+.o=oo . . . | | o o.+= + o o | | . o..o + . | | .o = o . .| | . = S + . o| | . o . B + + | | + . o @ . . .| | + o o + . | | .+.o. . . | +----[SHA256]-----+ The generated key file is stored in ~/.ssh Folder
1) Experiment: asymmetric encryption is set between two virtual machines
ssh-keygen -f /root/.ssh/id_rsa -p "" -f Specify file directory -P The specified key password is empty ssh-copy-id -i /root/.ssh/id_rsa.pub root@172.25.254.120 -i Specify public key id_rsa.pub To 120 main engine ssh -i /root/.ssh/id_rsa -l root 172.25.254.120 -i Specify key id_rsa To connect host 120
When a host with only one key is connected to the corresponding public key host, the key is used by default and does not need to be specified. If the configuration file parameters are not modified, the host can still be connected by symmetric encryption
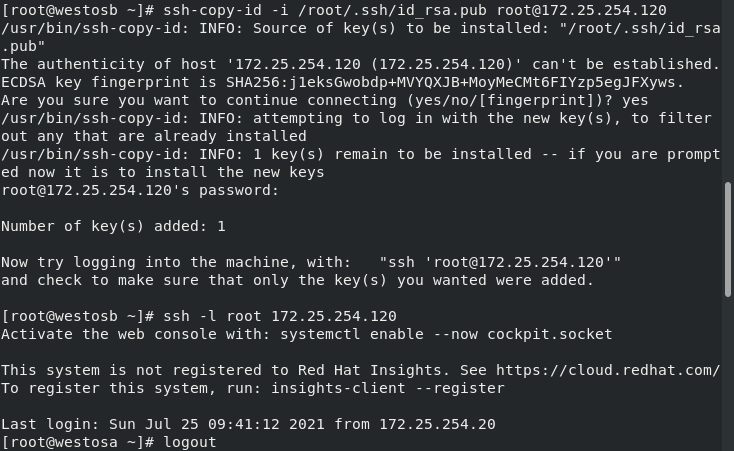
Settings cannot be connected through symmetric encryption
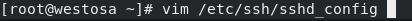
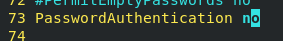
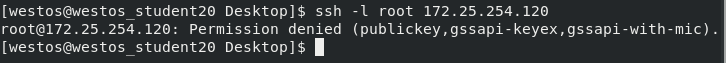
2) Experiment: authentication change test
[root@westoslinux ssh]# rm *key* -rf #Delete all files with key s in the / etc/ssh directory. [root@westoslinux ssh]# systemctl restart sshd #Restart the sshd service and the remote host generates a new public key file [root@westosb]# ssh -l root 172.25.254.120 #When connecting to the remote host again with the original key, the following error will occur ---------------- @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that a host key has just been changed. The fingerprint for the ECDSA key sent by the remote host is SHA256:j1eksGwobdp+MVYQXJB+MoyMeCMt6FIYzp5egJFXyws. Please contact your system administrator. Add correct host key in /home/westos/.ssh/known_hosts to get rid of this message. Offending ECDSA key in /home/westos/.ssh/known_hosts:4 ECDSA host key for 172.25.254.120 has changed and you have requested strict checking. Host key verification failed. ---------------- vim /home/westos/.ssh/known_hosts #Open the corresponding file according to the prompt, delete the corresponding line, and connect again without error
3) Experiment: Port change test
setenforce 0 #selinux firewall configuration 0 means shutdown (so that the port can be changed) systemctl disable --now firewalld # Turn off firewall vim /etc/ssh/sshd_config #Enter configuration file Port 22 -- 2021 #Change the port to 2021 key end SSH - l root 172.25.254.120 - P 2021 - P specify the port PasswordAuthentication yes/no #Set whether a remote connection can be made with a symmetric encrypted password (passwd: westos) AllowUsers user1 user2 ... #White list: only user1/2 can connect to the host remotely DenyUsera user1 user2 ... #Blacklist: user1/2 cannot connect remotely (only one blacklist is valid) systemctl restart sshd #Restart sshd after each change (SELinux(Security-Enhanced Linux) It's the national security agency( NSA)For the implementation of mandatory access control, yes Linux The most outstanding new security subsystem in history.)
 Set port
Set port
