Linux
Article directory
- Linux
- 1. Introduction to authority
- 2. Authority management command
- 2.1 command chmod to modify permissions
- 2.2 modify command chown of file owner and group
- 2.3 modify file group command chgrp
- 3. mask code
- 4. linux security context and special permissions
- 5. File system access control list
- 6. sudo
- 7. Management order
1. Introduction to authority
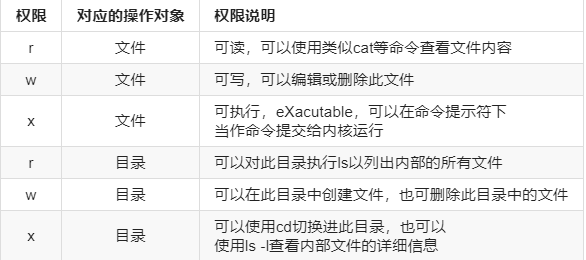
File permissions are mainly defined for three types of objects:
- : owner, u
- Group: genus group, g
- Other: other, o
Bold style each file defines three permissions for each visitor:
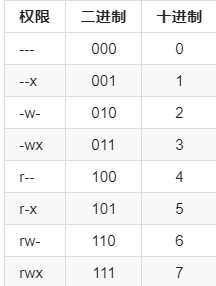
Binary to decimal conversion of permissions:
2. Authority management command
2.1 command chmod to modify permissions
//Modify the permissions of three types of users:
//Syntax: chmod MODE file
-R //Recursively modify permissions
//To modify a user or some user permissions:
//u. G, O, a (user category)
//chmod user category = MODE file
//chmod user class = MODE, user class = MODE file
//Modify one or some permissions of a certain type of user:
//u. G, O, a (user category)
//chmod user category + | - MODE file
//chmod user category + | - MODE, user category + | - MODE file
//chmod +|-MODE file,.....
2.2 modify command chown of file owner and group
The chown command is available only to administrators.
//chown USERNAME file,...
-R //Modify the owner of the directory and its internal files
//chown USERNAME:GROUPNAME file,...
//chown USERNAME.GROUPNAME file,...
2.3 modify file group command chgrp
//Syntax: chgrp [OPTION]... GROUP FILE
-R //Recursive modification
3. mask code
Why is the default permission 644 after file creation?
Why is the default permission 755 after directory creation?
This is controlled by mask code umask.
As you can see from the name, the mask code umask is used to hide some permissions. For example: what would you do if you didn't want to be recognized?
The final permissions of the file are:
-
666-umask
The final permissions of the directory are: -
777-umask
By default, a file cannot have execution permission. If the calculated result has execution permission, its permission will be increased by 1.
4. linux security context and special permissions
4.1 linux security context
Premise: process has owner and group; document has owner and group
Whether any executable program file can be started as a process depends on whether the initiator has executable rights to the program file;
After starting as a process, the owner of the process is the initiator and the group of the initiator is the group of the initiator
- The permissions for a process to access a file depend on the initiator of the process:
- When the initiator of the process is the owner of the file, the application file belongs to the owner
- When the initiator of the process is the file's group, the file group permission is applied
- Application file "other" permission
4.2 special authority
linux default permissions are controlled according to the way of linux security context, and the existence of special permissions breaks the rules of linux security context.
SUID(4) //When running a program, the owner of the process started by the program is the owner of the program file itself, not the owner of the initiator
chmod u+s file
chmod u-s file
//If the file itself has execution permission, the SUID is displayed as s; otherwise, it is displayed as S
SGID(2) //When running a program, the process started by the program belongs to the group of the program file itself, not the basic group of the initiator
//By default, when a user creates a file, its group is the basic group to which the user belongs;
//Once a directory is set with SGID, the files or directories created in this directory by users with write permission belong to the group\
//Group of directories for which SGID is set
chmod g+s DIR
chmod g-s DIR
//If the file itself has execution permission, the SGID will be displayed as s, otherwise it will be displayed as S
Sticky(1) //In a public directory, everyone can create files, delete their own files, but not delete files created by others
chmod o+t DIR
chmod o-t DIR
//If DIR itself has execution permission, Sticky will be displayed as t, otherwise it will be displayed as t
4755 //With SUID and file permission of 755
2755 //With SGID and file permission of 755
1755 //Sticky, 755
7755 //With SUID, SGID, Sticky, and file permission of 755
//The first 4, 2 and 1 represent SUID, SGID and Sticky respectively
5. File system access control list
facl (Filesystem Access Control List), using file extension to save additional access control permissions.
//Syntax: setfacl [- bkndrlp] {- m| - m| - x| - x...} file
-m //Set up
u:UID:perm
g:GID:perm
//setfacl -m u:test:rw file
//setfacl -m g:test:rw file
//If you want to set the default access control list for a directory, just add d before u or g when setting. Such as:
//setfacl -m d:u:test:rw file. The files created in this directory inherit the permissions set in this access control list
-x //cancel
u:UID
g:GID
//setfacl -x u:test file
//setfacl -x g:test file
-b //Remove all
//Syntax: getfacl [-aceEsRLPtpndvh] file
//getfacl file
//File permission application order:
//By default:
Owner --> Group --> Other
//With facl set:
Owner --> facl,user --> Group --> facl,group --> Other
6. sudo
sudo can realize what commands a user can execute through which hosts as another user
sudo's configuration file / etc/sudoers
Use the visudo command to configure sudo. Each line is a sudo entry. The entry format is as follows:
- who which_hosts=(runas) command
- Who: user? Alias, indicating the identity of the person who runs the command
- Which hosts: host alias, through which hosts
- Runas: runas? Alias, as which user
- command: cmnd? Alias, which commands to run
Aliases must be all and can only use the combination of uppercase letters. You can use exclamation mark to reverse
Alias classification:
- User alias:
- User_Alias NETWORKADMIN =
- User name of the user
- Group name, using% boot
- You can also define other user aliases
- User_Alias NETWORKADMIN =
- Host alias:
- Host_Alias =
- host name
- IP address
- network address
- Host_Alias =
- Other host aliases
- Runas alias:
- Runas_Alias =
- User name
- % group name
- Other Runas aliases
- Runas alias:
- Command alias:
- Cmnd_Alias =
- Command path
- Directory (all commands in this directory)
- Other command aliases defined
- Cmnd_Alias =
//Sudo command syntax: sudo [options] COMMAND
-V //Show version number
-h //The version number and instruction instructions will be displayed
-l //List all sudo class commands available to the current user
-v //Because sudo does not execute at the first time or within N minutes (N defaults to 5), the password will be asked. This parameter\
//It is to make a new confirmation. If it is more than N minutes, you will also ask for the password
-k //Invalidate the authentication information. If - k is not specified, the default authentication information will expire after 5 minutes
-b //Put the instructions to be executed in the background
-u USERNAME //Execute the command with the specified user name, which is root by default
7. Management order
w //Displays who are currently logged in to the system and what they are doing
sleep //Sleep, write a script to prevent sleep from being added when the previous command starts executing before the next command finishes executing\
//It means to pause for several seconds before executing the following command
sleep NUMBER[SUFFIX]...
SUFFIX:
s:Seconds, default
m: branch
h: hour
d: day
last //Display / var/log/wtmp file, display user login history and system restart history
-n # //Display the latest related information
lastb //Display the / var/log/btmp file to display the user's wrong login attempt
-n # //Display the latest related information
lastlog //Display the last successful login information of each user
-u username //Show recent login information for a specific user
basename //Show path base name

